KF7031 Wireless Network & Security
802.11 A WLAN data throughput and security overheads
Abstract
The wireless network are mainly used in security systems, television remote control, cell phones, Wi-Fi, wireless power transfer and computer interface devices. IEEE 802.11 is a part of 802 set of LAN protocols. It was a standard for transmitting data over wireless network. It uses 5 GHz frequency band and it supports data transfer up to 6.75 megabytes per second. It was released in 1999.It uses the same data link layer protocol and frame format as the original standard but as OFDM (orthogonal frequency division multiplexing) based air interface. To use the 802.11A connection each device on the wireless network should support 802.11A standard. The main advantage of using 802.11 A is less crowded because it uses 5 GHz frequency band. It has smaller interference problem andit is faster than 802.11B. It has 12 non overlapping channels. More channels can be included with more users with no performance degradation. The main disadvantage of using 802.11A standard is it won’t support many client device like PDA’S and many note book computers. These client devices will be supported by Bluetooth and 802.11B standard. It is also more expensive while comparing with other standards. The distance covered by 802.11A standard is less when compared to 802.11B due to higher operating frequency. It has error correction code also. It is widely used in all over the world. It is also mainly used in corporate office. The signals passed by 802.11A are observed by walls and other solid objects due to shorter wave length. Now a day’s wireless connections are using in our daily day to day life. In this paper we will see the architecture and how efficiently we can use the 802.11A standard and their physical structure. In this paper we are going to focus on performance of wireless network using OPNET modeler 9.1.
Introduction
Nowadays wireless technologies are emerging with new trends in daily life. Hence the security is the biggest challenge to achieve. Many intruders are coming in wireless network. There should be a strong security or encryption algorithm should be provided to secure the data in long enterprises. Wireless are used mainly nowadays because of its mobility, easy access and low cost. It is also very flexible [1](Li June, 2017).The wireless security is the security that does not allow unauthorized persons to access the data through wireless. It can be given in two ways. They are WEP and WPA. The WEP is wired equivalent privacy that the password can be easily judged in few minutes. It is weak security standard. The WPA is Wi-Fi Protected Access which is an alternative for WEP. It uses an encryption device that converts the network with 256 key. The long key will help to provide security against hackers. Even though the hackers uses new policies to access the network and uses the information. New policies should be formed to overcome the problem. In this paper we are going to secure the network by using MAC device by some security key that helps to secure the data.
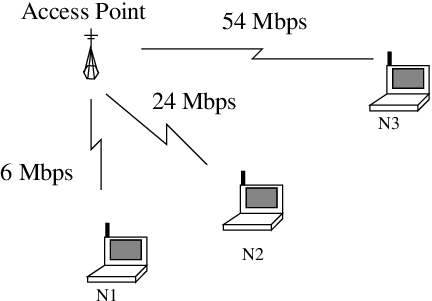
Theoretical Throughput and Development
Security mechanisms are the issue in wireless network environment. There are many algorithms development to secure our data in wireless network. The security can be given by capturing and analyzing the information of MAC device. It has lot of information for providing security. In this paper we are going to compare the existing and proposed system of protocols so that the packet delivery ratio, packets delay, throughput and packets drop are analyzed. The numerical results are depicted.
Based on the speed the ratios are changed according to the existing and proposed system. The user can design, model and simulate wireless networks using access point, wireless node, router, wired node and switch. The network simulator is set up to test the existing and proposed system. The network security is a term which helps to secure from the cybercrimes. The main components of network components are hardware, software and other services of cloud. The protocols that we are developing should be very protective. It should provide enough secure schemes. There are many tools came in market to check the protocols that provides all security to the data. Day by day new tools came into our field and hackers also using different types of techniques to capture the data.
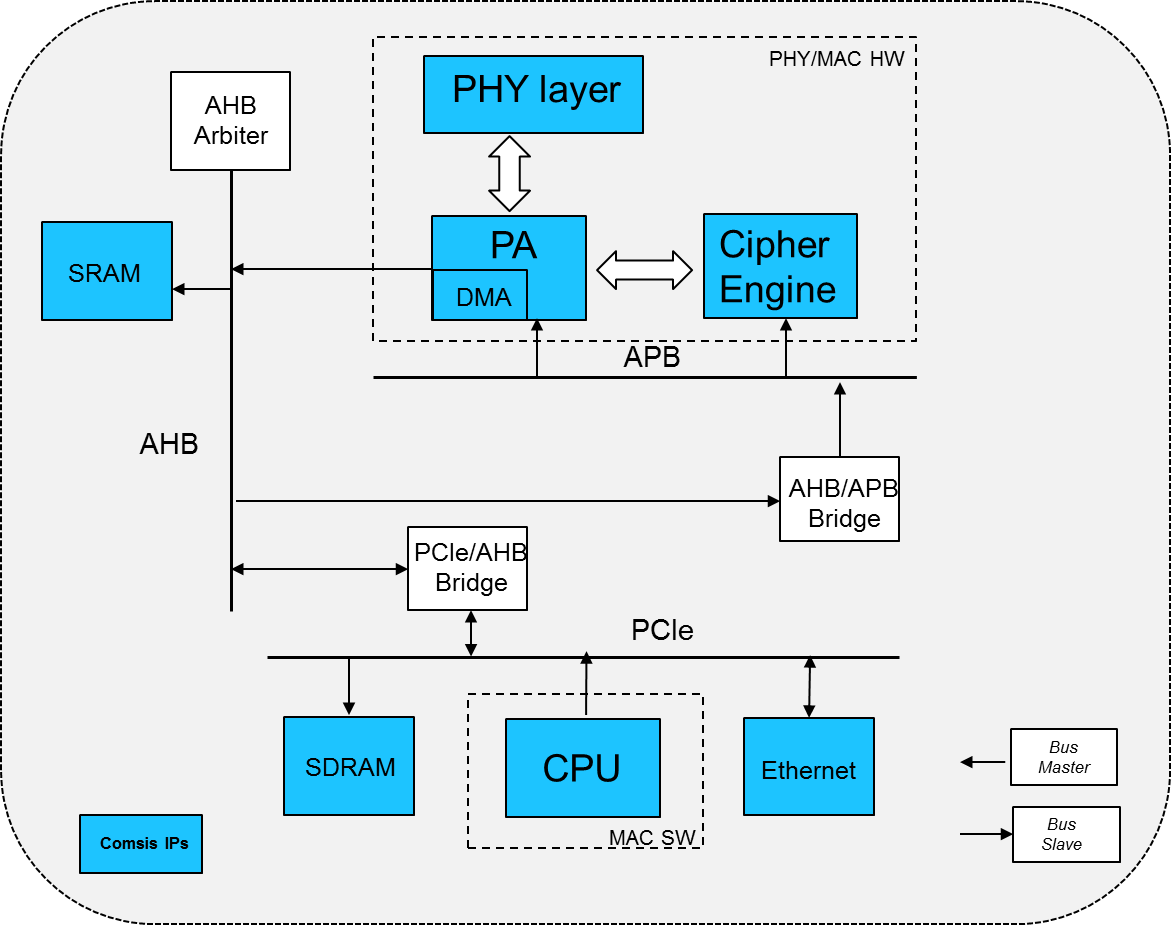
Experimental Method
The transmission type of 802.11 A is OFDM. The frequency standard band is 5GHz supporting standard channels. The base rate is 6Mbps. Many protocols are emerged to give security to the data. Now in this experimental model the packet delivery ratio analysis, packet delay analysis, throughput analysis, packet drop analysis can be analyzed by comparing the existing and proposed system. First we need to set the simulator. The graphical representation is shown below and the throughput is measured when the security is on and off stage which s depicted as before security and after security.
The throughput can be defined as the total amount of packets is passed through a link. There are some of the network tools which help to calculate throughput.
1) IPerf3
2) Net stress
3) LAN Speed test from Totusoft
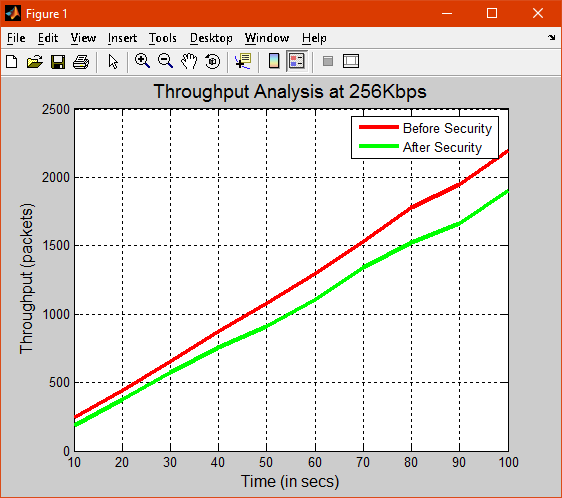
Fig 2: Throughput analysis
The protocols of existing and proposed are compared according to their delivery ratio, packet delay, throughput with upper limit and lower limit has been shown.The amount of time required to push all the bits into wire is called transmission delay.
Dt=N/R
Where dt is transmission delay
N is number of bits
R is the rate of transmission
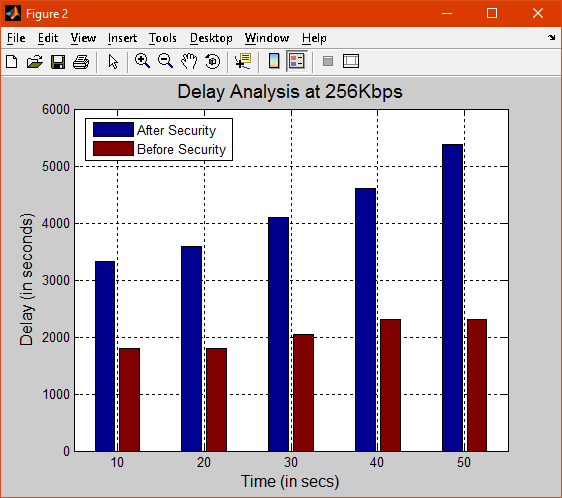
Fig 3: Delay
In this above picture the delay between the existing and proposed system is analyzed at a speed of 256kbps. The graph shows that existing sytem is more delayed than the proposed one with the security on and off state with the access point.There are different types of delay
- End to end delay
- Processing delay
- Queuing delay
- Propagation delay
- Network delay
End to End delay
It is a time taken for a packet to be broadcast across a network from resource to destination.
ETED=N*l/R
N= link of the packets
L = Packet length of a packet
R= transmission rate of a packet
Processing Delay
The time take to process the packet header that helps in detecing bit-level errors during broadcast of a packet to target.
PD=Packet header/bit-level errors
Queuing Delay
It is referred as amount of delays meet by a packet between the time of supplement into the network and the time delivery to the address.
QD= Transmit a Packet
Propagation Delay
The length of time taken to reach its destination.
PD=Input/output
Network Delay
The network specifies how elongated it takes for a bit of data to travel transversely from one message endpoint to another.
ND= Packet length* propagation speed
Result
In the packets drop analysis is shown by comparing the existing and proposed system. The packet drop occurs when one or more packets of data will travel across the network which fails to reach their destination. It is measured with percentage of packets lost with respect to packets sent. There are different types of wireless technology. They are Bluetooth, Zigbee and Wi-Fi. By comparing these three technologies the engineer can get an idea to select which protocol is the best one to suite the business. The attributes are size, power consumption, network size, bandwidth, speed and cost (Md.Abbas Ali Khan, 2016). Many wireless mesh networks are available that can automatically reconfigure it. Some security schemes should be introduced like authentication and re authentication etc(Malek Rekik, 2019).
The above diagram depicts the overall delay, load and throughput. It is used in the wireless LAN in the office room. We will find that the user association with access point increases the load also increases and the delay also increases. It represent the various delay occur in experimental results and shows the access point increases as the users association is decreases that means when network load increases the throughput decreases.
Discussions
The wireless technologies were mainly used in all areas. Many authors tried to improve the 802.11A bandwidth, size, power consumption to provide maximum flexibility. The network security also protects the data that is stored in network. It is very popular because of less error prone. It is widely used in business sector. It is license free and it is easily downloadable. It has less power consumption and more flexible and efficient. Because of its speed and quick access it is very popular. Due to its fastness it is shared both public and private. It is used in all areas like housing, industry, field sales, vending, real estate and education. The wireless network can sense light, humidity, location, sound and nature (Muwonge Ssajjabbi Bernard, 2019).
It enables the user to communicate with other without wires. The wireless is divided into four categories. They are wireless personal area network (PAN), wireless local area network (LAN), metropolitan area network (MAN), wide area network.People mainly use the wireless connection for checking the emails, browsing the internet and for any business purposes. The WEP is a secured protocol in the world. It appears first in the selection list.
The three basic services provided by IEEE standards are authentication, confidentiality and integrity. In authentication it analyzes that authorized work station is accessing the internet. If any unauthorized persons entering the network means it won’t allow accessing the data (Menal, 2017).
Confidentiality ensures that it ensures privacy. Integrity shows that any modification has not done in the information. These are the basic things provided by the standards. There are different types of attacks in security of the network. They are masquerade, passive attack, active attack and traffic analysis.Comparision table is given below
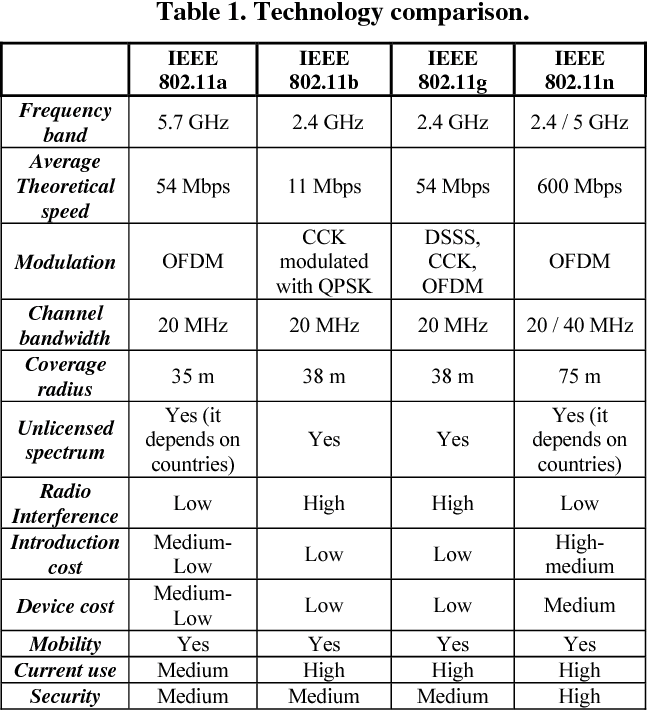
The WEP provides the biggest security in IEEE standards. With the combination of WEP and other algorithms the maximum level of security can be achieved. There are two types of authentication. They are open system and shared authentication. The WEP key is 64 bit key. When compared with WEP the WPA and WPA2 offer good results. Usually it is combined with RSA key. The OPNET modeler will support platforms like windows, Linux etc. It helps to test the technologies and also gives suggestions for further enhancements. It supports four technologies. They are discrete event simulation, flow analysis, ACE quick predict and hybrid simulation.
The main technical terms for providing network security are encryption and decryption. The encryption is changing the original text to cipher text. The decryption is changing the cipher text to original text. But with the good algorithm combinations the WPA will provide the good result. The wireless network is mainly used because of its low cost and mobility. Many industrial enterprise and companies are using only this wireless technology. Though it is wireless the problem is also very big. Many tries to access the information. Many protocols also developed. Many secure protocols also developed to meet the problems in today’s life. Protocols are a set of rules and commands that should be followed to achieve the result. The other version of WEP is WEP plus, dynamic WEB and WEP2. The wireless technology uses the spread spectrum technology for sending and receiving the information. The wireless technology uses the radio waves to connect the computers in the network. The wireless network plays an important role in global network infrastructure. The Wi-Fi provides the service at very low cost when compared to other technologies.
Conclusion
In this paper the OPNET modeler simulates the wireless network. In this we have compared the existing system with the proposed system in terms of packet delay, throughput, packet drop, and packet delivery. In future we can apply this in mobile network with good network and large. Additionally we can produce some security for the network also by using WPA and WPA2. It is the major security for the network and helps to transmit the data securely. Many attacks are coming in our networks in our daily life. Many industrial developments are implementing the WPA protocol for providing good security. So the network should be traffic free, load balanced, maximum throughput and should provide security.
References
Bibliography
J Reshma, T. K. (2019). Big Data Oriented Energy Aware Routing for Wireless Sensor Networks. Springer.
Karthika, D. N. (2017). Selfish Node Detection in Wireless Networks. International Journal of Computer Sciences and Engineering.
Li June, Y. K. (2017). A Detection Method of WLAN Security Mechanisms Based on MAC Frame Resolution. Wuhan University and Springer .
Malek Rekik, A. M.-M. (2019). OAP-WMN: Optimised and secure authentication protocol for wireless mesh networks. International Journal of Security and Networks .
Mansoor Davoodi, E. D. (2019). Algorithms for Handoff Minimization in Wireless Networks. Journal of Computer science and Technology.
Md.Abbas Ali Khan, M. K. (2016). Comparison Among Short Range Wireless Networks: Bluetooth,Zigbee& Wi-Fi. Daffodil International University Journal of Science and Technology.
Menal. (2017). Evolution of Wireless LAN in wireless networks. International Journal on Computer Science and Engineering.
Muwonge Ssajjabbi Bernard, T. P. (2019). QOS Strategies for Wireless Multimedia Sensor Networks in the Context of IOT at the MAC Layer,Application Layer and Cross Layer Algorithms. Journal of Computer Networks and Communications.
Pandian, A. C. (2019). Sustainable Mobile Networks and its Applications. Springer.
R Dutta, S. K. (2017). PER/BER Performance Evaluation of Less Complex KVD Decoding Architecture for IEEE. International Journal of Computer Sciences and Engineering.
APPENDIX
Know more about UniqueSubmission’s other writing services:

