CIS114-6 Assignment Sample – Network Systems and Administration 2022
Introduction
In a Cloud environment it is used to accumulate the data which it assures by both diminutive and great company to admission of data communication internet from wherever at any place in a cloud. Cloud computing development consists of front end and back end .
The obverse ending is used by admittance of platform represent a cloud based method. The obverse end has network servers that include tablets, chrome, and other devices to access data. Overhaul source is make use of by reverse end which is used to manage
the resources such as data, virtual machine, and refuge device. The cloud compute has structural design includes the following components such as customer component, request and services provided by cloud environment..
Fig: 1 Cloud Benefits
Consumer constituent make available client interface to cloud communications. Whichever function that a consumer cans admission to beneficiary condition the cloud environment make available request to admittance.
Cloud environment provide according to the services through a data communication which is represent to bring and imbursement based on usage in a service. It makes available stage expansion and performs various service in order to accumulate information. The cloud environment is a huge collision provides universal to bring out of big resolution of Information technology sector.
LIITERATURE SURVEY
Yigitbasiogly et al proposed why industry need cloud and don’t need cloud. The interviews were conducted on mainly at the basis of risk, acceptance and cloud computing. The research refers as involvement of abroad is data confidentiality. The risk with cloud computing the organization use hybrid solution with dedicated data centers.
Prasad,Green and Heales et al focused on cloud computing services. It represent how should manage the IT expenditure and modern resources .A study was conducted with 126 clients and 26 respondent with 110 respondent adopt cloud computing services. The result reveals that immediate cloud migration is an essential part for business.
Tchernykh et al analyzed the intention of users’ action and cloud providers. It deals with reliability, safety, privacy of information to deliver cloud under restriction in discretion, reliability and accessibility.
Theoharidou et al propose the risk in cloud and identify with measure. The application and data migrate to a cloud represent with new intimidation and vulnerabilities [2]. It examines how privacy risk are initiate when data and relevance are migrate to cloud.
CLOUD SERVICE CATEGORY
Infrastructure service provides overhaul for storeroom space, virtualization, and network as disburse on model. It gives communications on basis method so dealing client e can keep away from spend for possessions. Infrastructure as a service allows client for their contract out of Information technology transportation, fundamental equipment, storage allocate space etc. A long-established organization make available pay on model for a particular requirements of h/w arrangement with a phase of time.[3] The Infrastructure as a cloud supply with unreliable provisions for the essentially use services and pay on your own for the particular overhaul in cloud environment.
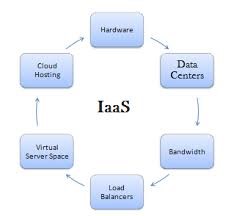
Fig:2 Infrastructure as a service
The three deployment models offer in cloud environment such as community, confidential and hybrid. A confidential be inherent in a private which imply communications. The community cloud represent data center and combination cloud of hybrid where customer select both public and private.[4]
IaaS provider has the following services and it includes
Compute overhaul
It includes primary memory as a fundamental and central dispensation for the client.
Infrastructure as a service storage space
It makes available storing data in a back -end storage space
Arrangement of connections as a overhaul
It provides set of connections such as overpass, control routers.
Consignment matching
Afford consignment balances at communications layer.
Advantages of Infrastructure Service Provider:
Communications: various customer can distribute substantial infrastructure
Possessions Web admittance: Admittance resource through the online web access.
Pay-model: users essential to compensate and pay for what are the services they have used in a cloud service.
Commerce: It makes available commerce for IT communications.
Scalability: The main advantages of infrastructure as a service communications are reliable. The problem occur in h/w or in software by customers no need to be concerned.
Disadvantage of Infrastructure service Provider:
- Protection in Infrastructure service: Protection in Infrastructure as a service
- Preservation: It is difficult to use the particular software for some of the companies.
- Services: Move around effective machine of Infrastructure as a source is hard.
Infrastructure as a service provider:
| Infrastructure as a Provider in Cloud | Infrastructure resolution | Details in Infrastructure |
|
Web- AMAZON |
Plan | Examine cloud environment , load corresponding as collection |
| Net enchantment contributor | Cloud service | centers as a Data |
| Dependence announcement | Put in the ground- in a reliable center | RIDC services based cloud |
| Provider of sify as Infrastructure | Infrastructure cloud | Offer infrastructure platform Services |
| Provider of Tata as a Infrastructure | calculate Insta | Infrastructure assistance available in Singapore and hyderabad |
Platform as a Service
It offer a programmer to position and runtime surroundings to position web request. The request can get e from a cloud on a basis of request and admittance through online association. The cloud provider manage Scalability so client don’t bother to agonize about cloud communications to handle.[5] It comprise policy interactions to hold up mesh request. It afford folder, request structure in Platform, and language
Fig3: Platform as a service
l communication: It offer for the programmer to expand request to avail programming language are Java ,Perl and Go.
Relevance structure : It provide the structure in Platform such as Word press, mechanism to comprehend the request progress in Platform.
Record in PaaS: It offer record as a database application as Mongo Database, Clear Database to converse with request.
Other Applications: It is used to deploy request
Advantage of Platform as a servicer
Expansion in Platform: It is make use of to expand without disturbing concerning transportation.
Lowe in Risk: Endow in platform such as h/w and s/w. It requires simply device to communicate and a data connection to construct submission [6].
Function commerce t
The organization purpose to avoid build from the origin and the developers start from the development phase.
Neighborhood in Platform
It provide online service provider to give information or ideas. .
Reliable request in Platform
It provides consumption for various users to transform of request.
Disadvantage of Platform as a service
- confine : The request should perform based on a platform and cloud environment provide service to move would be a problem to another user in a platform as a service.
- Isolation: The data is pubic so there is a isolate a data is a risk factor because it is visible as communal to users, so threat in information time alone as a Platform service[7].
- Classification relevance: Huge Increase convolution in data.
Cloud Platform as a service:
| Platform service contributor | Services in PLATFORM |
| Google browser | URL obtain to obtain for cloud environment storage allocation space ,overhaul |
| rummage sale power providers | Accomplishment and RELIABILITY |
Software as a service
The software as a service provide allocation where services offer accessible by a cloud administrator..The client doesn’t require to for any related software to admittance request. The cloud environment services give by Software as a service application such as:
- Commerce in S/w as a service:
The organization in a business overhaul in Software service provides Enterprise resource planning, customer association organization, and transaction in hardware and software.
- Document in Software:
The record offer other revelry to direct and pathway data automatically.
- Network providers:
A set of connections service contributor switch the data in Software as a service..
- Electronic Mail in Software service:
Many electronic mail offer the request using Software as a service.
Advantage of Software provider in cloud environment:
- The admission industry according to a minimumprice.
- on its own request and request publically shared by many users.
- extra hardware is not provided
- small preservation
- No need any communication devices to integrate hardware and software description
- overhaul e access by any machine
- It effortlessly integrates with other providers.
- No need any s/w mechanism.
Disadvantage of S/w provider:
- Safety measures is a concern for customer because information is accumulates in environment of cloud.
- Mainly depends on Data association.
- Unhurried duty to relocate documentation.
| S/w as provider | S/w as a service |
| Sales force in cloud | resolution as a CRM |
| Microsoft office | Online office |
| Google browser | Gmail |
|
GOTO meeting App |
Video
conferencing |
| Oracle storage | resolution as a CRM |
| Workday | Payroll in
Financial Management |
DEPLOYMENT MODELS IN A CLOUD
The consumption provide in a cloud service are
Public cloud Deployment
The communal cloud is available from third party through internet for arrange and create IT. The user can access the possessions such as storage, claim server in a cloud. It is mainly used for developing application.
Example:Google [8]
Private cloud Deployment
The confidential cloud in an association is used for large group. It is very expensive to use private compare to public
Hybrid cloud Deployment
The association use private and public altogether. The association use to setup IT communications deployment to provide the capacity available in a private cloud.
Community cloud
Multiple association share possessions through the community cloud environment.
SECURITY ISSUES: ANDCHALLENGES IN CLOUD RELOCATION
A company wanders or moves in cloud the application, information and commerce from tapered strategy to cloud. production faces the various challenge[9] . They are:
Confront in business:
It is one of the major confront in cloud to converse with any sytems. The enlarge of system mechanism with extra numeral of overhaul contributor in obscure concurrently. If the commerce is go approximately in a environment of cloud which it is compatible and provide other request overhaul source in organization.
Safety measures and privacy
To accept in cloud commerce in succession of a security measure according to a server basis is less classify over the data. There is a threat available of attack by hackers to obtain the information in a cloud.
Observant data
It is easily migrate data in a environment of a cloud is easily moved from one location to another location easily. It is hard for the cloud provider with individual platform in different representation [10].
Impediment
It is one of the main issues to drift data or information for company because of be deficient of reliability. If client want to move or go some other merchant in a cloud environment the numeral of hard work has to be observe [11].
Organizational challenge
In a cloud environment the expertise has lot of change and move about the secure data to cloud. So overall setup and modify and worker be supposed to attain commerce hoard on a isolated server in an organization.
- Security apprehension1: substantial security is lost with the cloud representation with no knowledge of resource to run.
- SecurityApprehension2:company desecrated the law
- Security Apprehension3: irreconcilable with vendors service so client move from one to another.
- Security Apprehension4: logically think who controls the encryption and decryption key.
- Security Apprehension5: Integrity of data to be ensure and changes occur only it should represent with endorsed transactions.
- Security Apprehension6:Data security standard must provide with security regulators[12].
7.Security Apprehension7: Application improvements must be protected Security
Security Apprehension8:The banking regulations and government regulations have strict limits and the client economic data should stay behind in their own nation.
Security Apprehension9: A virtual machines make difficult to ensure the ability of records in active and solution nature which is difficult to maintain the reliability of security.
Security Apprehension10:Cloud examination may damage their repute because consumers may be able to provide services if their solitude rights are dishonored.
DATA MIGRATION PROCESS
Cloud Managers face extreme problems in cloud migration when the company server to another server forms cloud. Cloud is an interface where organization access in a virtual environment [13]. If data passage is not done appropriately it arise a problem with data and cloud with the primarily comprise of data. Thus cloud providers manage with the skill for managing cloud effectively.
PROPOSED WORK ON CLOUD MIGRATION
The process of transmit data and applications on services represent over the internet with numerous challenges where cloud computing enable to potentially reduce operating cost with effectively allocate resource in cloud-based computing [14].
ESTIMATE BASED ON ENCRYPTION
The encryption the cipher-text with the string represents the public identity and decryption the cipher text if the identifiers with the decryption key. Decryption occurs when the attributes match with the make use of information which represent the characteristic need to decrypt and association between characteristic [15]. It consists of four operations:
- Initialize the crypto-scheme with as secure secret key which has a public parameters such as:
(SK,PK ):=setup()
KEYGEN: generate a key using decryption
DECRYPT(entity)=keygen(SK,input supplied)
Encryption: It create a plain text with encryption key
EK=Encrypt(PK, encryption entity)
Decrypt: It decrypt a original-text which is use to access policy
Decrypt((PK, decryption entity))
crypt: It create a plain text with encryption key
EK=Encrypt(PK, encryption entity)
The encrypted data and decrypt key can access with public key and endorsed particular client can access the cloud data base with the encryption process of specific parameter
SECURING A CLOUD MOVEMENT
Due to minimum passage in a cloud environment corporation features has different confront. A secure resolution in cloud migration represent as:.
Method of Encryption
The information transport commencing confined server to cloud environment by a consumer of allocating process be chop up of garbage by other gathering. The encryption plays to secure the information and is the main technique in cloud devices.
Endorsement
The association of data backup provides for their limited devices and many cloud environment providers asses a hoard in a cloud environment for customers.
Cloud proficient
The association moving to cloud and know the knowledge tradition in an efficient way. The cloud specialized should have well expertise in tradition of information in a standard method [16].
Safety measures Service in cloud
It provide available protected services to the client in arrange way of representing the information companionship to use as overhaul in a protected method [17].
Tutoring in cloud
Industry should teach the new tools to users in order to use cloud services effectively and make it a success to handle with a new techniques.
Cloud provider Requirements
The organization supposed to provide the requirements in a marketplace to know the necessities in a business level. The end-user should clarify about the cloud examination provider and ask the approach of request offer such as antivirus for system, setup firewall for securing data, security provide when consumers move to cloud environment [18].
Examination services
The cloud examination services provide safety measures and make a review plan and strategy, events for a location in prospect [19].When a user choose a to be familiar with various services offered by the cloud supplier of a particular association of a company. The client encompass and sign the service level agreement (SLA) offer services by the provider in an environment. The SLA provides a declaration mainly assist to construct confidence among customer to provide data protection in a cloud surroundings [20,21].
CONCLUSION
The enlargement in a cloud environment gives a resolution to acquire well-known techniques admittance and provide a passage connecting diminutive of great business and production. Many businesses move to the service providers offer by cloud for the elevated cost of services and they possess condensed and enlarge the income in a business.
The main confront in an association level have increased such as reliability, securely portability of data and scalability is the major advantage in a cloud.. The main concern should hub as a center in cloud to be a refuge and in order to switch in a solitude scheme.
The Main organization in a cloud such as manufactured goods, submission progress, and convention construct secretarial requirements of h/w and s/w which offer by cloud source as a overhaul. It is easy to examine a customer in a cloud and use a cloud deployment services for imbursement only custom of the particular overhaul. It offer dependable armed forces to provide enhanced excellence in an business environment .
The association effortlessly engrave downward the service cost and enlarge earnings according to the organization business requirements.
REFERENCES
[1] Gleeson, E., Computing industry set for a shocking change.RetrievedMay10,2014fromhttp://www.moneyweek.com/investment-advice/computing-industry-set-for-ashocking-change-43226.aspx,2014.
[2] Gartner ,Gartner Says Cloud Computing Will Be As Influential As E-business. Gartner press release, 26 June 2013.http://www.gartner.com/it/page.jsp?id=707508,2013
[3] Boss, G., Malladi, P., Quan, D., Legregni, L., Hall, H. ,Cloud computing.www.ibm.com/developerworks/websphere/zones/hipods/. Retrieved on 20th May, 2015.
[4] Foster I, Kesselman C,ComputationalGrids. http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.36.4939 ,2013
[5] Foster I, Kesselman, C, Tuecke S . The Anatomy of the Grid: Enabling Scalable Virtual Organization. International Journal of High Performance Computing Applications 15(3):200-222,2012.
[6] Foster I, Zhao Y, Raicu I, Lu S , Cloud Computing and Grid Computing 360-Degree Compared. In: Grid Computing Environments Workshop (GCE’08). oi:10.1109/GCE.2008.4738445 ,2015.
[7] Fellowes, W. Partly Cloudy, Blue-Sky Thinking About Cloud Computing. Whitepaper. 451 Group,2014.
[8] M. Casassa-Mont, S. Pearson and P. Bramhall, “Towards Accountable Management of Identity and Privacy: Sticky Policies and Enforceable Tracing Services”, Proc. DEXA 2014, IEEE Computer Society, pp. 377-382,2014.
[9]J. Salmon “Clouded in uncertainty – the legal pitfalls of cloud computing”, Computing, 24 Sept 2008, http://www.computing.co.uk/computing/features/2226701/clouded-uncertainty-4229153,2014.
[10] Khajeh-Hosseini, A., Greenwood, D., Sommerville, I.,. Cloud Migration: A Case Study of Migrating an Enterprise IT System to IaaS. Submitted to IEEE CLOUD 2014
[11] S. Overby, How to Negotiate a Better Cloud Computing Contract, CIO, April 21, 2014. http://www.cio.com/article/591629/How_to_Negotiate_a_Better_Cloud_Computing_Contract
[12] Krautheim FJ ,Private virtual infrastructure for cloud computing. In: Proc of HotCloud ,2013.
[13] Santos N, Gummadi K, Rodrigues R Towards trusted cloud computing. In: Proc of HotCloud ,2014.
[14] Armbrust M et al Above the clouds: a Berkeley view of cloud computing. UC Berkeley Technical Report,2014.
[15] Ghemawat S, Gobioff H, Leung S-T The Google file system. In: Proc of SOSP, October 2013 Hadoop Distributed File System, hadoop.apache.org/hdfs
[16] An article on “Predictions about the future of Cloud Computing” available at http://mediastar91.blogspot.in/2012/04/predictions-about-future-of-technology
[17] C. Schridde, T. Dornemann, E. Juhnke, B. Freisleben, M. Smith, “An Identity-Based Security Infrastructure for Cloud Environments,” 2013 IEEE International Conference on Wireless Communications, Networking and Information Security (WCNIS), pp. 644 – 649, 2013.
[18]J. Y. Sun, C. Z, Y. C. Zhang, and Y. G. Fang, “An Identity-Based Security System for User Privacy in Vehicular Ad Hoc Networks, ”IEEE Transactions on Parallel and Distributed Systems, vol. 21, no.9, pp. 1227-1239, 2013.
[19] A Lewko, T. Okamoto, A. Sahai, K. Takashima, and B. Waters. Fully secure functional encryption: Attribute-based encryption and (hierarchical) inner product encryption. In Advances in Cryptology – EUROCRYPT 2013. Springer, 2013.
[20]. M. Pirretti, P. Traynor, P. McDaniel, and B. Waters “Secure attribute-based systems,” Journal of Computer Security, vol. 18, no. 5, pp. 799–837, 2013.
[21]. S. Jahid, P. Mittal, and N. Borisov, “Easier:Encryption-based access control in social networks with efficient revocation,” in ASIACCS, Hong Kong, March 2012.
Know more about UniqueSubmission’s other writing services:


Your article gave me a lot of inspiration, I hope you can explain your point of view in more detail, because I have some doubts, thank you.