Ict Network Architecture Design Assignment Sample
Introduction
The development of a communication system is referred to as network design. Standardized communication networks would govern how networking devices communicate, with networking architectural style defining which methods will be utilized as well as how networking devices will use these cloud service standards. It is indeed a paradigm for specifying the hardware elements of such a system, and also underlying functional organization including setup, operational requirements including processes, including network protocols employed. A network design in this report would define how any company connects to, utilizes, ultimately profits from the world wide web. Well with the right system architecture, the company will not only stay in touch, but will also experience consistent data rates.
Aims and Objectives
The main aim of the designing of a network will be to ensure whether the needs of the operators and the subscribers are met by the new and innovative networks or services of telecommunications. Network design also aimed to share resources to a greater extent.
The objectives of network design are as follows –
- To meet data transmission needs whilst decreasing costs.
- To predict the way of operations of new and innovative networks or services of telecommunications in the IT sector.
- To know the cost of concerning economic data.
- To recognize or analyse the details that are technical of the capabilities of networks or services of telecommunications.
- To save the money of an organisation and provide high reliability and high performance in the IT sector.
- To make all programmes, data, including equipment accessible to everybody on the system, regardless of geographical location of the client or resources.
Literature Review
Background of the study
Networks are suitable for the proposed strategy to outperform those which are haphazardly put up because the demands of such networks are accounted for (Матёкубов et al. 2020). A well-designed network will become more resilient as well as provide vastly superior productivity. Good networks are fast and reliable, giving the finest framework for any and all apps users want to utilise. Whether there will be latency or postponed reaction time, whatever job that workers strive to reach would be hampered; that’s one of the causes why it would be critical to evaluate the network architecture too before executing any modifications or commencing the initial deployment.
Past Findings
According to the author U.K. Matyokubov, in Uzbekistan, methodologies to the management of mobile phone network infrastructure that will be resistant to disaster will be designed. Natural as well as man-made calamities could have a severe impact on the operating effectiveness of every network design. In these kinds of instances, technological systems are required to endure any negative consequences (Säily et al. 2020). This article discusses numerous difficulties in developing a robust infrastructure against environmental as well as man-made calamities. This has been concluded from the study that the design of mobile communication systems that are vulnerable to environmental as well as man-made catastrophes, regarding the degree of growth of Uzbekistan’s network infrastructures, i.e. employing the capacity of current communication networks have been studied. The fundamental design and network design, which could be organised as rapidly as feasible, were primarily studied in this research.
According to the author the advancement of the networks of ICT that are distributed has been introduced. Conventional communication services, particularly the well-known 3-tier topology architecture, concentrated on centralising computer networks that employed redundancies as just a safety feature for potential malfunctions. Nevertheless, over recent times, decentralisation has evolved throughout a plethora of different strategies. Begin with customers that require genuinely isolated connections for major use (Estevan et al. 2020). The Spine Leaf architecture with Software-Defined Networking technologies followed. This research article demonstrates why decentralisation will be preferable for centralisation by employing features of probability theory. Secondly, demonstration of how Spine-Leaf as well as Software-Defined Networks have been naturally decentralised, resilient, as well as superior to typical centralised networks (Shami et al. 2019). This has been concluded from the research that, initially, the major reason for consolidation was effectiveness, but this overlooked the underlying hazards in these kinds of installations. The era of decentralisation nowadays will be changing network architecture, rendering systems increasingly robust to unforeseeable dangers. This could also observe that decentralisation will be making inroads into storage solutions. The growth of Software-Defined Storage results is seen.
According to the author and architecture of the dual network has been designed for CT of few-view. In this study, a “dual network architecture (DNA)” for dynamically recreating pictures using sinograms has been proposed. A juncture fully-connected stratum performs the backprojection procedure in the suggested DNA approach, requiring substantially fewer storage than that of the earlier techniques. The suggested methodology employs O(C N Nc) variables, wherein N as well as Nc represent the dimensionality of the rebuilt pictures and also the amount of projecting, accordingly (Xie et al. 2019, September). C is indeed a variable that may be assigned to as little as 1. These experiments showed that DNA outperforms alternative state-of-the-art technologies in terms of efficiency. Whenever the number of genuine patient photos is low, environmental photographs could be utilised for pre-training DNA to minimise fitting problems. To conclude from the study, a new DNA network for automatically recreating CT images using sinograms has been created. Although the suggested technique has been evaluated for a few-view CT research question, researchers think it could be implemented to handle a variety of other CT difficulties, such as noise removal, restricted-angled CT, and etc. It isn’t the first publication to rebuild pictures directly from data that is raw, however earlier approaches need substantially more GPU RAM for training (Rubio-Aparicio et al. 2019). It should be noted that the suggested solution tackles this memory issues by mastering the reconstruction using the juncture fully-connected stratum as well as other appropriate networking devices. Furthermore, the suggested approach may properly acquire the backprojection simply transmitting even just a focal position through into fully-connected stratum.
Linking of the findings of the past with the aims and objectives
According to the past findings, the functionality of the network will be solely reliant on a particular connection. If indeed the shared connection fails, the entire network connectivity fails. Configuration could not be spread to something like a broad region due to the requirement for just a clear connection (Zang et al. 2019). For example, if there will indeed be a multi-storied structure, computer systems might well be located far from each other. That there were only single servers or users, therefore if either fails, then the entire system will cease to function. Users are unable to use the networking clusters. It was not a positive idea for almost any database system. This applies whenever the two or more devices stand close to one another, as when attaching printers. The past findings could not meet the aims or objectives of the project. The operators and the users are no doubt benefitted but are lacking some problems in it. Findings could not meet data transmission needs by decreasing the cost. All the programs were not accessible to all the customers and all users of the network designs.
Proposed Methodology and Data
Diagram
The main concept of the network design will follow the following design of the network with the client and the servers.
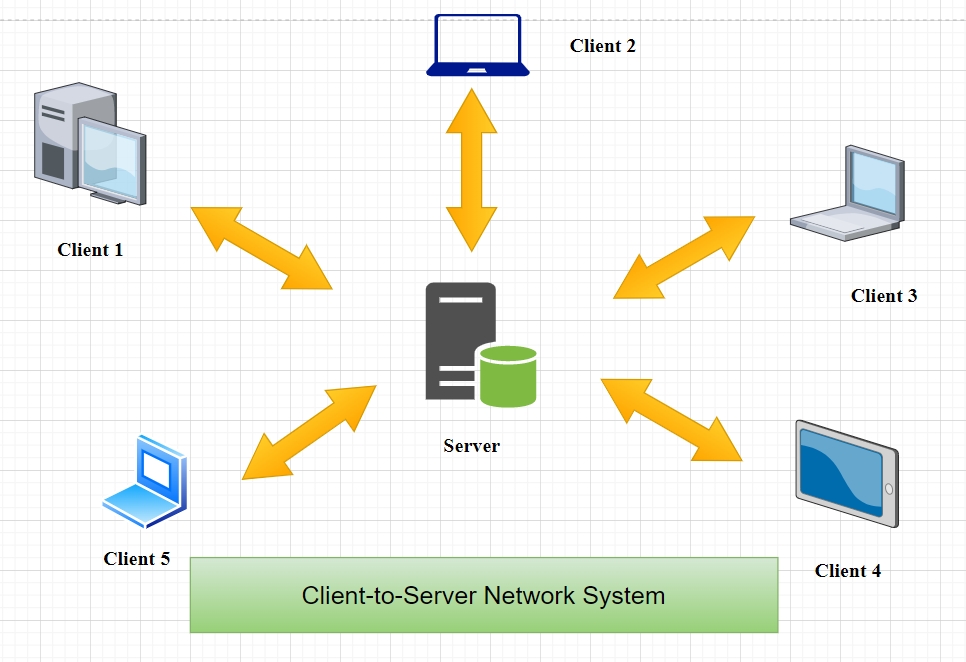
Figure 1: Client-to-Server System
(Source: draw.io)
In the earlier days, the networking was done using the point to point topology of networking. It had many disadvantages. The network’s operation will be entirely dependent on a single link. If the global connection breaks, the network security will be rendered inoperable. Due to the ability for even just a direct relationship, reconfiguration could not be dispersed over a large area (You et al. 2020). For example, if there will be a multi-story structure, computer networks may be positioned far apart from one another. Because there was just a database computer or user, if somehow fails, the entire machine eventually stops working. The connectivity clusters are inaccessible to users. It was a bad concept for practically any database management system. This will be true anytime two or more users are in close proximity to each other in the, such as when connecting computers.
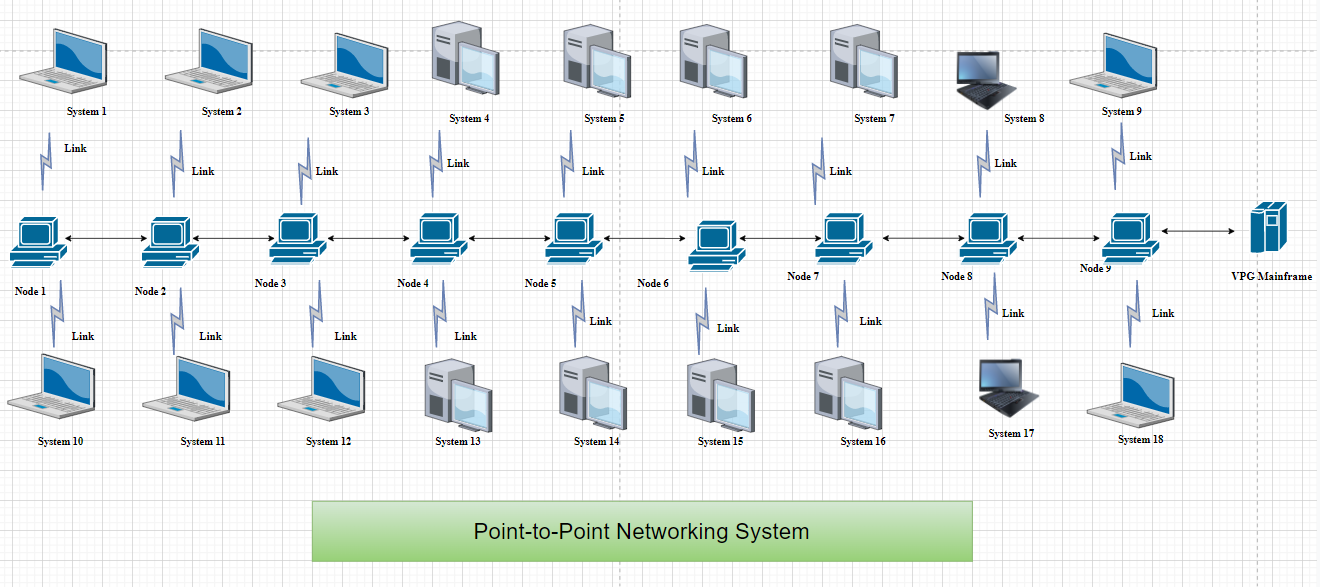
Figure 2: Point-to-Point System as Current network
(Source: draw.io)
A multiple network connection will have several features over a moment in time connection, including simplicity of installation, cheap cost, and dependability (Kopsidas et al. 2021). A moment in time connection connects two devices, whereas a multiple network connection connects more than multiple technologies to the same transmission medium.
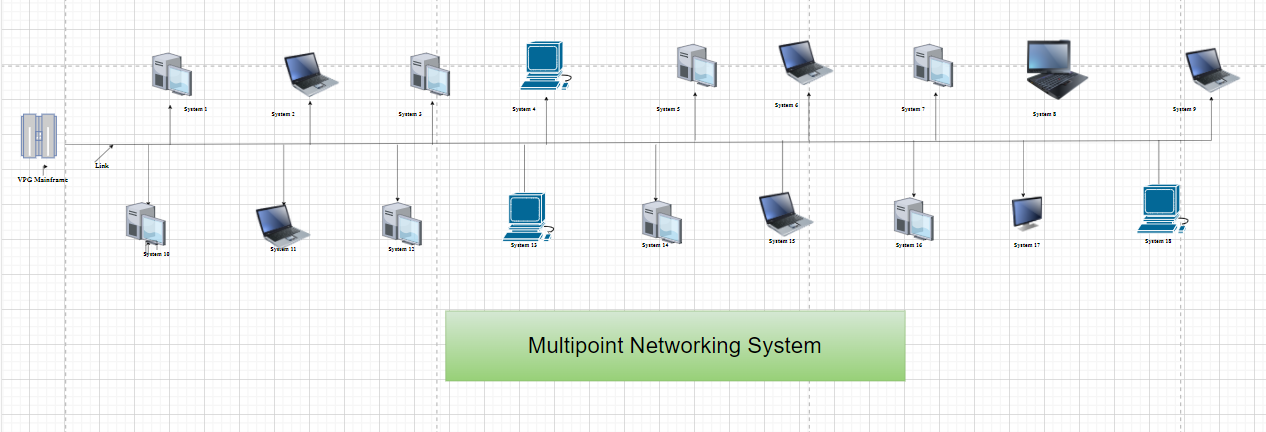
Figure 3: Multipoint System as future network
(Source: draw.io)
Hardware Software and Network Elements
Network device components include both physical as well as software equipment that are needed to set up communications systems in businesses and homes (Casellas et al. 2021). The server, consumer, peer, network segments, and connected devices are the physical components. The computer system & protocols are computational models. A total estimation of 300 pound sterling is required for establishing a new network system in an IT sector.
Hardware Elements
The hardware elements required for the designing of the networks are as follows –
- A router consisting of the access of high-speed internet. A router will indeed be a type of networking equipment which routes packets of data. Routers are responsible for traffic direction just on the Web (Gago et al. 2021). Data packets are used to represent transmitted data over the web, including a website page or perhaps a mail. A router will indeed be a networking device that connects multiple data channels across distinct internet protocols. Four antenna routers are required with N600 rate with a cost of 19.72 pound sterling.
- A modem – The modem will indeed be a hardware device which allows computers to communicate and exchange information through telephones or broadband connections. The modem’s primary role will be really to turn digital signals to analogue signals as well as vise-versa. The modem will be made up of two components: a modulator as well as a demodulator. Digital modem with 8000/8000 baud and 56.0/48.0 bit rate will be required which costs 110.53 pound sterling.
- Switches that are single or multiple – This helps in enabling the computers for linking one to the other over a network that will be internal. Switches seem to be networking devices that operate just at the access layer and data connection layer of the OSI model (Zeb et al. 2019). These link devices of networking and employ packet switching to deliver, collect, as well as forward packets of data across the system. A switch would have a port number into whatever PCs can be connected. Switch size 1.72*17.25*9.02 in inches and weight 6.83lb which costs 69.01 pound sterling will be required.
- Hubs of Ethernet – A network device will be a component that transmits data to all computer systems and Multimode fibre devices. A switch, on the other hand, may isolate data flows to network equipment and will be more advanced than a hub. Compact, basic local area networks (LANs) are best served by network hubs. 8 device connector hubs are required costing 6.90 pound sterling.
- Wired or Wireless linking of fibre optics or lines of telephone or cables – They are defined as a long, high information transmission as well as telecommunications. Optical fibre lines would have a wider throughput than conventional connections and therefore can carry data across greater distances. 10baseT cable will be required costing 6.60 pound sterling.
Software Elements
The software elements required for the designing of the networks are as follows –
- “CisCo Packet Tracer” – This will be a communication network learning & teaching application that will provide a unique blend of computer simulation as well as visualisation experiences, evaluation, activity composition capabilities, multiple access collaboration & competitive opportunities.
Network Elements
Regarding company owners, a proper small biz networking design will be vital. Due to technical flaws, a core router will be frequently more prone to viruses including malware than that of a bigger network. It would be just as critical to have up-to-date technology designed to handle such hazards as it will be to have elevated transportation technologies as well as equipment (Ah-Lian et al. 2019). It will be not really simple to always understand how to create a communications system. The dissemination of data inside an organisation will be affected by anything from the positioning of such routers inside a given circuit towards the numbers of devices in the network. Building up a chain circuit for the business necessitates the proper procedures:
- A connection to the internet that will be protected from the “Internet Service Provider (ISP)”. ISPs connect its clients here to the Web; simple providers of access merely traffic are managed here between people and also the Web overall. However, based just on the client’s premises as well as accessibility, additional products might well be packaged together. Among such offerings are:
– Services for sending emails
– Services for web hosting
– Browsers as well as technology applications for registration of domains.
- Capabilities of firewall – Firewalls are just the first line of defence for just an organisation from unauthorised users as well as inbound dangers. Every data packet which passes through the firewalls being checked for specified security needs, and everything which does not fulfil these requirements are instantly banned. This provides a decent foundation of protection, however businesses today must further defend themselves from advanced attacks.
Impact
A reliable internet design must acknowledge that a customer’s objectives encompass a variety of technological and organisational goals, such as availability, adaptability, cost, security & management (Gjøsæter et al. 2018). Many clients also wish to designate a necessary degree of system performance, which will commonly be referred to as a quality service. A successful network architecture will be even more resilient therefore allow for greater performance. Functionality will be cheap and effective, giving the finest framework for all of the apps people want to utilise.
Traffic Demands
Network security shall be considered always, with the purpose of preventing unwanted assaults from reoccurring across the firm. Any network architecture should provide a vulnerability management program, as well as facilities for backup generators when necessary (Li et al. 2019). Apart from that, and then in relation to the protection of just a company’s data, information should indeed be stored up on a regular basis to reduce the chance of destruction if something goes wrong with the networks caused by fire or even other security breaches. The security will be much better in the case of a multi-point network since it will be a shared network. The following things should be maintained within the IT sector for preventing the network from security breaches.
- Encrypt network communication using wireless cryptographic primitives with complicated passwords (WEPs).
- Programming can be used to grant authorisation access & limits to certain personnel.
- To cloud computing network connectivity, use a VPN.
- Create a “guest” wifi network for other unlicensed networks.
- Check that the communication, protection, and antivirus software equipment will be up to date.
- Restriction on access privileges to the modem.
Assessment
A multiple access connection will have several advantages over a moment in time connection, including simplicity of installation, cheap cost, and dependability. A moment in time connection connects two devices, even though a multiple network connection connects more than two devices to the same communication channel (Gagin et al. 2021). As a result, multipoint connections are more reliable. It would be simpler to make more individuals to a multiple network relationship than it would be to create individual interconnections between all users. This also results in lower connectivity & production process. A network interface will be made up of a single wire that connects all connected devices. The same will be true for a star configuration, which uses a single ring connector to interconnect all devices simultaneously. The gadgets communicate with one another through a common connection. Target data rate will be higher for the multipoint network hence created and designed than that of the point-to-point networking system. The multipoint networking system also avoids interferences in a better way than that of the point-to-point networking system.
Support and Training
A well designer of the network design will be required for the building and implementation of new and innovative network designs (Alharbi et al. 2020). The multipoint networking system will be implemented instead of the old fashioned point-to-point networking system since it provides shared networks between all the systems and provides a better and efficient network in an IT sector.
Data Analytical Tool
Cisco Packet Tracer will be the data analytical tool used. Cisco’s simulation software is called Cisco Packet Transporter. It will be used to design complex network conceptualizations as well as test & simulate conceptual networking ideas. It will serve as a learning environment for networking and indeed the encounter will be extremely similar to that of communications networks. They will also provide services in Spanish, Russian, French and German among other languages (Lin et al. 2021). Network Switch will allow students to build complex & large connections, which would sometimes be impossible to do with actual gear owing to cost constraints. Linux, Microsoft, MacOS, Mobile & iOS will all be supported by Network Simulator. Users will be able to drag & drop servers, exchanges & other network equipment to construct simulated network components in Packet Tracer. With the help of tube software the followings could be done –
- Cisco Network Switch will have a multi-user platform that helps several users to join different topologies over a network. System Software may also be used by instructors to create activities for students to complete.
- Allows for feature growth through other packages that leverage an API to enhance Network Simulation Winston’s capacities in areas such as curriculum & assessment presentation, gaming, disability & communicating with project – based learning.
- Using the ‘Enhanced Practical Mode’, one may imitate cabling equipment on a cabinet in a virtual environment. Refresh important skills including rack & layer device arrangement, on-device voltage changing, device port-to-port connectivity (including connector identification and implementation) troubleshoot & more.
- Atmospheric effects account will be required to acquire it for complimentary.
- It allows users to replicate Cisco router settings and may be performed at any location worldwide.
- Whether users use its Internet GUI or its Endpoints, the Network Administrator provides a complete dashboard for viewing the network’s condition, rapidly discovering and diagnosing faults, and pushing changes to the system to all domain controllers at once. One may indeed connect the Conducted using optimising compilers on the PC and execute one’s own operational stored procedures.
- It may be downloaded through an infinite number of devices.
- Provides a personality & interactive atmosphere
Conclusion
To conclude that, a new, innovative, efficient and further more productive technology of networking system will be designed by keeping the security and other parameters in mind. Previously, the point-to-point networking system was done, but it should be converted to the multipoint networking system for better reliance, better network security and cost-effectiveness. The aims and objectives for the research have been mentioned in the report followed by the literature review and the methodology to carry on with the project has been discussed in detail. A network design in this report has been defined which would be designed on later days how any company connects to, utilises, ultimately profits from the world wide web. Well with the right system architecture, the company will not only stay in touch, but will also experience consistent data rates.
Reference List
Journals
Ah-Lian, K., Eric, R., Karl, A., Jari, P. and Georges, J.P., 2019. Education in green ICT and control of smart systems: A first hand experience from the International PERCCOM masters programme. IFAC-PapersOnLine, 52(9), pp.1-8.
Alharbi, H.A., Elgorashi, T.E. and Elmirghani, J.M., 2020. Energy efficient virtual machines placement over cloud-fog network architecture. IEEE Access, 8, pp.94697-94718.
Gagin, S., Klingert, S. and de Meer, H., 2021. ICT Design for Community-empowered Sustainable Multi-Vector Energy Islands. ComForEn 2021, p.37.
Gago, S., 2021. ICT for Rail Transport in Poland. Problemy Kolejnictwa.
Gjøsæter, T., Radianti, J. and Chen, W., 2018, July. Universal design of ICT for emergency management. In International Conference on Universal Access in Human-Computer Interaction (pp. 63-74). Springer, Cham.
Kasprowicz, G.H., Poźniak, K.T., Zabołotny, W.M., Wawrzyniak, Z.M., Wojeński, A., Tyburska, A., Kamiński, J., Struniawski, J., Iwański, J., Brawata, S. and Szymajda, W., under review Mobile Distribution Point Architecture Concept of ICT Infrastructure.
Kopsidas, K., Cruzat, C. and Ni, M., 2021. Cyber‐physical reliability of dynamic line rating ICT failures in OHL networks. IET Generation, Transmission & Distribution, pp.371-382.
Li, Y., Li, K., Zhang, C., Montoya, J. and Chen, G.H., 2019, March. Image reconstruction from fully-truncated and sparsely-sampled line integrals using iCT-Net. In Medical Imaging 2019: Physics of Medical Imaging (Vol. 10948, pp. 194-199). SPIE.
Lin, B.S.P., 2021. Toward an AI-enabled SDN-based 5G & IoT network. Network and Communication Technologies, 5(2), pp.1-7.
Rubio-Aparicio, J., Cerdan-Cartagena, F., Suardiaz-Muro, J. and Ybarra-Moreno, J., 2019. Design and implementation of a mixed IoT LPWAN network architecture. Sensors, 19(3), p.675.
Säily, M., Estevan, C.B., Gimenez, J.J., Tesema, F., Guo, W., Gomez-Barquero, D. and Mi, D., 2020. 5G radio access network architecture for terrestrial broadcast services. IEEE Transactions on broadcasting, 66(2), pp.404-415.
Shami, E., 2019. The Evolution of Decentralized ICT Networks. arXiv preprint arXiv:1909.04434.
Xie, H., Shan, H., Cong, W., Zhang, X., Liu, S., Ning, R. and Wang, G., 2019, September. Dual network architecture for few-view CT-trained on ImageNet data and transferred for medical imaging. In Developments in X-ray Tomography XII (Vol. 11113, p. 111130V). International Society for Optics and Photonics.
You, M., Zhang, X., Zheng, G., Jiang, J. and Sun, H., 2020. A versatile software defined smart grid testbed: Artificial intelligence enhanced real-time co-evaluation of ICT systems and power systems. IEEE Access, 8, pp.88651-88663.
Zeb, K., Zhang, X. and Lu, Z., 2019. High capacity mode division multiplexing based MIMO enabled all-optical analog millimeter-wave over fiber fronthaul architecture for 5G and beyond. IEEE Access, 7, pp.89522-89533.
Zhang, Q., Jiang, M., Feng, Z., Li, W., Zhang, W. and Pan, M., 2019. IoT enabled UAV: Network architecture and routing algorithm. IEEE Internet of Things Journal, 6(2), pp.3727-3742.
Матёкубов, Ў. and Давронбеков, Д., 2020. Approaches to the organization of disasterresistant mobile network architecture in uzbekistan. Acta of Turin Polytechnic University in Tashkent, 10(2), p.10.
………………………………………………………………………………………………………………………..
Know more about UniqueSubmission’s other writing services:

