02 Reflective Writing Assignment Sample
Here’s the best sample of 02 Reflective Writing Assignment, written by the expert.
Introduction
The reflective report caters to evaluate the effectiveness of learning experience from the topic “cyber security challenges in business”. The digital environment is providing many benefits to businesses but at the same time, increasing the concerns of privacy and security in the organizations. The main objective of study was to understand the nature of different challenges in cybercrime, emergence of cybercrime in organizations, vulnerability of cybercrime, different forms of cybercrime, and their impact on the businesses. The study has addressed various aspects of cybercrime and security challenges in digital era. The contribution of study was significant because it has enabled better protection of information and allows businesses to take necessary actions on right time.
Effectiveness of the learning experience
The understanding of cyber security challenges have been a very useful learning experience as the takeaways have changed the perspectives, thought process and raised cybersecurity awareness. The hackers and attackers are coordinating their activities and stealing private and confidential information for malpractices. There are huge numbers of ransomware and data breaches and leading to large scale damage to the organizations. The cyber-attacks are mostly planned and staged and hackers do not leave any mark for the crime. The most feasible solution to avoid cybercrime is to take necessary precautions so that the crime does not take place and another solution to be aware of cybercrime challenges so that the prospective crime can be avoided in long term (Kaider, 2011). In the era of artificial intelligence and digital scenario, the advancements in machine learning are increasing opportunities for managing cyber security but still, the boundary between human in interaction and machine is still not clear. The machine cannot manage the parameters of security and human need to aware of potential security issues to manage the cybersecurity in well manner.
The learnings from the cybersecurity challenges have led to enhanced awareness of cybersecurity so that the professionals in business can intimate the cyber department in case of any security related issues and take necessary actions at the initial stage of cybercrime. Today, most of the data is stored in computers, laptops, mobiles and cloud based storage. The products compete against the amount of data and features. The malware vulnerabilities harm the data and overall security portfolio of companies (Branagan, 2013). The analytics and business insights are not sufficient to harvest the value from data. And it is important to consider that security is not a one-time activity but it is a continuous activity and security risks need to be managed in regular manner. The security aspects are not handled on single but it takes long term security measures to manage the cybersecurity within the business. The paradigm shift needs to be recognized and understand that cybersecurity is relevant in the cyberspace and digital environment.
The learning experience from the study enhanced the value as cybercrime need to be managed and it requires ongoing commitment in businesses. The value of cybersecurity awareness learning educate about the risks, threats and resolutions in the cyberspace. The future of cybersecurity and role of cybersecurity in business have been discussed to understand their role in current business environment (Branagan, 2013). The relevant expertise and experience in cybersecurity along with proper awareness will educate the stakeholders as well as other individuals so that relevant issues can be focussed in the organization.
Servings of learning experience
It is indicated that there are many learning experiences from the awareness of cybersecurity challenges such as avoidance of cybercrime, precautions while managing cybersecurity, management of security portfolio, protecting the private and confidential data of organization. The learning experience serves the educational program, general life as well as future career. The educational program learnings has been enhanced with the understanding of advanced cybercrime information, nature of cybercrime, different types of cybersecurity challenges faced by businesses. It has also added value to the general life because current business processes and professionals cannot deal without digital data and at the same time, the stored information need to be secured in appropriate manner (Slay, 2008). The cybersecurity is an essential part of conversation in business and also considered while making important decisions, regulatory and governance requirements, infrastructure investment etc. The general life includes conversation of cybersecurity and therefore, it is important to be aware of cybersecurity challenges to get involved in important business communication. The employees share equal responsibilities to provide best results and it require regular updated and education to manage the cybersecurity threats.
The learning experience from the study are also helpful in future development of career because the cybersecurity professionals are in high demand and certified trainings are provided to the professionals for better management of information technology as well as cybersecurity readiness. The new knowledge about cybersecurity awareness and insights will be transferred for security of data and business applications within the organization.
Learning process
The learning experiences have been very fruitful for the individuals because it have provided necessary information in stages such as emergence of cybersecurity, increasing priorities of cyber security, issues in cybersecurity, mitigating the risks of cyber-attacks in business (Gillard, 2013). The importance and security measures in cybersecurity are also explained to understand varied aspects. The learning process was built on the holistic model as indicated in below figure. The important factors such as cultural influences, values and learning community, support network, peers added to the relevance of learning. The learning process is associated with the Kolb model to evaluate the learning activities in the study. The below figure demonstrates the learning process for evaluation of study.
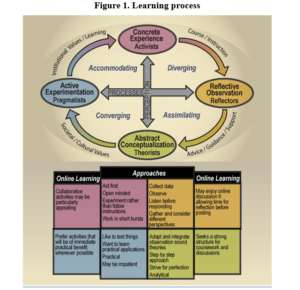
The learning process from the study of cybersecurity challenges include two different learning activities i.e. processing and perception. The processing includes dealing with information; perception includes way of taking the information. The quadrants of diagram indicate the different learning process i.e. converging, assimilating, diverging and accommodating. The converging process relates to the different perspectives for find the single answer and promotes thinking in scientific manner. The diverging process is related to the generation of different accounts of different experiences and often, they are creative processes (Philip, 2006). The assimilating process describes the consumption of new knowledge. The accommodating process explains the relatedness with the new knowledge in context to existing beliefs and experiences. The processing and perception activities of model are described as opposite factors as some individuals perceive information with the support of emotions and experiences (as indicated on the vertical axis) and some individuals perceives the information with the support of active experimentation and reflective observation (as indicated on the horizontal axis).
Evaluation of learnings
The learning gained from the cybersecurity challenges study can be interrelated with the observations made in the business research because it was very useful for the overall process of learning. The major observations in the study include measures for security of information in cyberspace and digital world. It indicates that the incidents of cybersecurity should be avoided by taking measures and at the same time, different type of potential threats are explained in detailed manner. The preparation is an essential step for managing the cybersecurity and it includes appropriate management systems, best IT policies, auditing of information technology, dedicated staff for operations and management of cyber security reasons (Kaider, 2011). The readiness of good cyber security encompasses the understanding of threats, risks to the information and assets relevant to the people and organization. The activities include detection and monitoring of cyber security threats, protecting the information and critical systems, and ensuring that organization meet the relevant compliance and standards. The contingency and response plans have to be prepared in case of any security breaches and it is also necessary to develop business continuity plans for minimization of business loss. The responsibilities of cyber security officer is to consider security measures and manage the security breaches but at the same time, other individuals, leaders and stakeholders are also responsible for management of security in cyber space. The importance of cybersecurity is equivalent to the recovery and detection practices in business. In the activity of security breach, the detection and response actions need to be conducted for minimization of loss; be it reputational, financial and others (Assante, 2010). The identification of risks needs to be quick so that the data theft can be responded properly. The loss or corruption of data can be restored with quick identification of security risks. The analysis and preservation logs can help in identification of security breach and then after, it can be closed for betterment of business. It indicates that the proactive measures are important for cybersecurity in business and therefore, awareness of cybersecurity plays vital role in improving the business activities and safeguarding the information within the business.
Reasons for conducting learning process
The new insights and other learnings of cybersecurity challenges have been conducted with specific reason of safeguarding the private and confidential information of business. In current business environment, the organizations are running business activities on the basis of data, information, facts, and figures and therefore, it is important to ensure the safety of information (Morris, 2013). The emergence of cybercrime is the major reason for conducting the activities of assignment. The collaboration of businesses with digital and information technology, internet of things security, needs of security according to customized business models, digital enterprise architecture, biometrics and advanced authentication have led to increased cybercrime. Therefore, it is important to combat cybercrime through important security measures. The learnings of cybersecurity will help in reducing the cyber threats, cybercrime and managing the business operations in efficient and effective manner.
Application of learnings in future
The application of learning is important because the understanding of learning need to be applied for better future. The clarification of research subject, course of cyber security challenges will improve general life and future profession in significant manner. The cyber security threats poses major challenges to the professionals in business across all sectors and therefore, it has to be managed in well manner to promote positives of new technology, internet of things, cognitive computing, big data analytics and influence the digital connection in seamless manner. The learnings can be applied with the sharing of threat to confidential data and investing in the infrastructure and solutions to secure the business information. The strategies will resolve the security issues such as bad password, unsolicited emails, malicious attachments, hacks. This learning will be applied in future with the consideration of step by step process in securing the private and confidential data within the digital business environment. The risks posed by the unsecured internet of things are a serious concern and emerge in the work place. The learnings of security measures and proactive security applications will help in safeguarding the data of business in new era of technology. The proactive measures in cybersecurity ensure identification of vulnerabilities and mitigations at early stage and application of security on priority.
References
Assante. (2010). Testimony on Securing Critical Infrastructure in the Age of Stuxnet. National Board of Information Security Examiners.
Branagan. (2013). A Proposed Australian Industrial Control System Security Curriculum. Hawaii International Conference on System Sciences .
Gillard, J. (2013). Cyber Centre PMC’s announcement. UK Centre for Education .
Kaider. (2011). Introducing undergraduate electrical engineering students to reflective practice. Fremantle, WA : Proceedings of the 2011 AAEE Conference.
Morris, V. (2013). Advances in the Protection of Critical Infrastructure Improvement in Industrial Control System Security. South Australia, Adelaide: Australasian Computer Science Week.
Slay, S. (2008). Developing SCADA Systems Security Course within a Systems Engineering Program. Dallas, US: Proceedings 12th Colloquium for Information Systems Security Education.
________________________________________________________________________________
Know more about UniqueSubmission’s other writing services:

