STATISTICAL ANALYSIS AND EQUIVALENT BANDWIDTH ESTIMATION IN IP NETWORKS USING REAL NETWORK TRAFFIC DATA
Introduction
The close monetarization of the incoming and the outgoing data speeds, in the IP based networking traffic data with the help of the Real time traffic tools has been done in this project. Here the statistical analysis of the equivalent bandwidth by the estimation of the IP based networks are done using the traffic data. That will be accessed by the network traffic analysis which will help in the detection of the malware, or any other vulnerabilities using the different clippers and protocols. This process has involved the troubleshooting of the slow networks and also helps to collect the historical and the real-time records by which the functions of the networks also can be detected. It works by eliminating the blind spots and by improving the visibility of networking technology. There are several network traffic analyzers but among them here in this project the developer has used the Wireshark software for the analysis of the networking tools. Here the estimation of the different bandwidths will be done by capturing the packet interfaces, from the statistical dataset and then the wide range of the networking statistics data output will be created. Thus after the creation of the statistical range of the information the statistical analysis of the loaded captured file will be done using the process of response capturing. Here in this manner the traffic data requests and the responses have been captured. Generally in the Wireshark the TCPdump is a commonly used packet analyzer. By allowing the users to display the TCP/IP packets with the other network packets, the transmission and the receiving process of the networks has been estimated. Thus the developer has also tried to show the sorting and the filtering process of the various functions by the graphical representations and also has tried to show how all the traffic will pass through the estimated network.
Aim
Here the main aim of this project is to collect the historical data records along with the real time data using the real time network analyzer. Here the developer has tried to implement the method of the network traffic analysis to monitor the activity and the availability of the identified network malwares. Here also the issues of the security and the functionality of the monetarization occurs in the time of the network analysis process. So here the developer has tried to show the common functionality of the network traffic analysis process by implementing it into the statistical data. Also here the estimation of the equivalent bandwidth in the IP networking protocols using the real time network analysis process has been done in the proposed software model. So it can be said that the detection of the ransomware activities and the malwares in the network traffic is the main aim of this project. More than that the traffic analysis process also involved the deduction of the unused information from the patterns of the network communication.
Objective
- To estimate the equivalent bandwidth in the IP networks using the real time networking analysis process.
- To do the statistical analysis of the given data for the packet tracing using the real time network analyzer.
- To examine the security problems in the IP networking packet tracer.
- To implement the network security in the process of the real time network analysis.
- To allow the users to observe all the traffic passing through the networks.
- To troubleshoot the network issues occur in the packet transmission.
- To oppose the latency issues held in the network traffic.
- To troubleshoot the malicious activities by debugging the implementation of the protocols.
Research Question
- How can bandwidth create an effect on the traffic network data?
- What will be the maximum measurement of the achieved bandwidth data on an IP address?
- What are the main factors which affect the bandwidth of an IP address?
- What are the differences which will be helpful to improve the bandwidth of an IP address?
- What will be the best value for the bandwidth network data?
- What is the unit of the measurement of the bandwidth data?
- What are the three different types of measurement used for the bandwidth networking data?
- How can a data rate can be dependent on a bandwidth network data?
- Is bandwidth directly proportional to the speed of the networking data?
- Which particular device is used to reduce the traffic networking data?
- Which particular signal has the maximum bandwidth of the networking data?
- What is the main difference between the throughput and the bandwidth?
Research Rationale
Estimation of the bandwidth on a network traffic data improves visibility for the devices which are directly connected to the network. There are various types of examples such as, health care visitors and the IoT devices. They help to troubleshoot the security issues and the operational issues of the devices. The statistical analysis helps to normalize the behavior of the traffic data on a network. It is very important to maintain the normal traffic patterns as per the application. It also helps to detect the negative activity of the traffic network data for a particular protocol. It also helps to provide the volume for the estimation of the complex patterns of the relationships and the structure of the network which can be used to disclose the main feature of the network. Real time traffic network is a monitoring tool which is used to check continuously the traffic of the networking signal.
There are lots of disadvantages or the drawbacks of the statistical analysis of the traffic data also. It is a very challenging process to collect the historical record and the real time data of the activities of the data of a particular network. They can’t properly detect malware activities or the ransomware activities in a system. They also can’t properly analyze the use of the vulnerable ciphers and the protocols. They also can’t troubleshoot a slow networking data of a system. They can’t eliminate the blind spots and can’t improve the internal visibility of the network of the system. They use high CPUs or the processor data. They can only transmit data with maximum bandwidth on a particular given time period over an internet connection network. They have issues in the physical connectivity of the devices. Malfunction of the equipment and the devices can be a cause of slow networking data.
Research Significance
Statistical analysis of the prediction of the network traffic data can be very useful as it is a very important tool for the control and the management of the IoT devices. For improving the service quality of the IoT devices, it is very important that the network data should be predicted accurately and timely. In the intelligent traffic network, the degree of the burstiness is very high. Sometimes, it can create problems during the time of the prediction. It also helps to provide the volume for the estimation of the complex patterns of the relationships and the structure of the network which can be used to disclose the main feature of the network. “Network Traffic Analysis (NTA)” is a measurement tool which can be used for analyzing the activities of anomalies, used to analyze the availability of the network, including the operational issues as well as for the security issues of the system (Pinheiro, A.M., et al 2020). They are very important as it is used to maintain the normal traffic patterns as per the application. They help to estimate the bandwidth on a network traffic data improves visibility for the devices which are directly connected to the network. It also helps to detect the negative activity of the traffic network data for a particular protocol. They help to troubleshoot the security issues and the operational issues of the devices. Real time traffic network is a monitoring tool which is used to check continuously the traffic of the networking signal. Traffic analysis are very important as it useful during the time of the trouble shooting and resolving the network issues of the system.
Research Framework
Figure 1: Research framework
(Source: self-created in draw.io)
Literature Review
According to Parisis, G., et al 2021, the characteristic of the internet traffic is a serious issue for every network vendor and the researchers. Previously, network vendors and the researchers discovered that the correlation structure of the traffic data implements the similarity and it also shows the duration of the individual flow for the packets which have heavy tails. During the comparison of this packet data, the amount of the distribution of the packets which are present on that particular link within a given time period, this topic is the least interesting topic research for the networking vendors and the researchers.
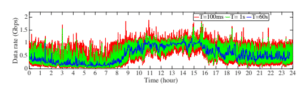
Figure 2: Data rate plot
(Source: arxiv.org)
Correct traffic data of the internet is very important because this data is used during the time of network planning. The researcher will use the meticulous statistical approach which is used to fit the statistical distribution to its traffic networking data within a time period. The researcher will choose first a timescale which will be denoted with T. Then the researcher will choose the amount of traffic data which can be seen within a time period. The researcher will analyze the distribution of the random variable as compared to the wide range of values. There are various types of tools which are used to help the administrators during the time of analysis and the monitoring of traffic network data. Classification of the traffic network data with proper accuracy is very important in the data of network activities which can be further used during the time of traffic engineering, monitoring the security issues, accounting the usage of network in the system, detection of fault in a system, etc. It also provides distribution in the Quality of Service (QoS) for the various parameters of the network services.
According to Queiroz et al. 2019 , the limitations of the traditional networks can be overcome by the use of the splitting control over the plane data. The main objective of the logic of the network is to move the components over the various managing network devices. Here in this report the author has mentioned several counter management over the network analysis. Here in this context the utilization of the network bandwidths with the estimation of the monitoring the different parameters for the network management has been analyzed using the network traffic analysis methods. The management of the network analysis involves the capacity planning, the network provisioning of the data, the load balancing and the detection of the various anomalies has been done in this process. Here at first the networks are flown through each packet then this crosses the switches, after that the data has been retrieved from the streamline of the data.
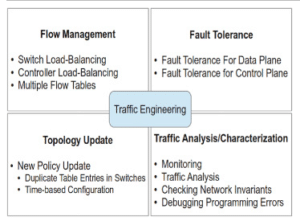
Figure 3: The traffic engineering process.
(Source: https://www.sciencedirect.com/science/article/pii/S1084804519300244)
Here in this report paper the author gets information about the traffic engineering and the open flow of the data. Here in the process of the open flow of the data, software defined networking has been implemented. It is the process by which the deployment of the controlled and traditional data networks can be established.
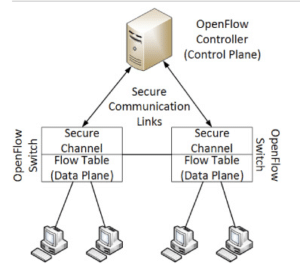
Figure 4: The open flow architecture.
(Source: https://www.sciencedirect.com/science/article/pii/S1084804519300244)
The open flow data communication fulfills the requirements of the various protocols and also provides the control over the traffic, by managing the equipment in the open networking foundation. And by applying the SDN the characteristics of the real time traffic analysis, with the flow of the designing, and routing techniques in the improvement of the utilized network resources has been depicted in the applied dataset. Thus the fault tolerance and the fast recovery from the failures of the applied network topology has been done using the critical analysis of the predicted data models.
Theories and Models
By analyzing the various methodologies and the various techniques from the different reports the implementation of those methods has been done within this project. Here in that context the developer has implemented various processes. Mainly the open model simulation structure has been followed in this project.
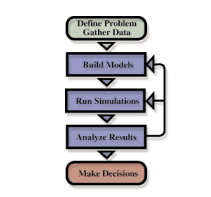
Figure 5: The open modeling and simulation structure.
(Source: https://arxiv.org/)
Here in the method of the model building the developer has to define the changes in the topology model of the applied network. Then after the node editing process has been done. Here in the process of the system architecture the changes and the defining process of the various network topologies has been done. After the node editor the process editor has been done. Here using the various behavioral logic in the control flow of the networks and the simulation process occurs. Here the developer has used the wireshark software for the simulation and then the interactive debugging of the interactions between the client and the server has been done.
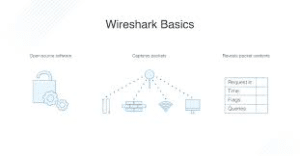
Figure 6: The basic network traffic structure in the wireshark.
(Source: data:image)
Here in this project the developer has applied the wireshark software for analyzing the packets and to capture the packet from the given dataset. To implement the networking analysis process it involves the selection of the interfaces. After the selection of the interfaces, the actual data which will be analyzed is estimated, then determining the proper dataset packets, the actual packet tracing process starts. Then after starting the recreation process of the data the running and the capturing of the packets has been done using the internet protocols. Now after the analysis of the problems in the application of the data, the problems can be avoided by avoiding the other browsers, and the other instant messengers. After this process it involves stopping the packet tracing process. Then the packet can be captured, and it can be saved in the wireshark in a lib cap format. Thus in that way the developer has implemented the packet tracing process in the proposed model.
Literature gap
Here from the above analysis of the different reports and by researching on the various research papers the developer gets the idea of the implementation of the different theories in the proposed model. But here the developer has not got the direct simulation virtual devices and there is a gap between the proposed structural models designing of the different models (Altunay, M., et al 2022). So here the developer has tried to implement the various developments in the approachable dataset structure and here also the developer has not got the estimation of the Gaussian application of the dataset in the network traffic analysis process.
Methodology
The Network traffic analysis method generally involves the packet tracing process by analyzing the type of the attacks occurring in the packet tracing process. Here the process involved two distinctive methods, like the passive method and the active method. In the passive method of the packet tracing the attackers try to extract the features of the sent traffic in the particular flow of the data transmission. Thus in that case the comparison between the networks upon the two sides has been done. And in the active method of the network traffic analysis the attackers do the alteration in the timing of the flow of the packet. Thus it involves the flow of the packets in accordance with looking at the patterns of the network streamline. In that way the attacker gets the link to combine the two different network flows for the breaking of the anonymity (Jurcut, A., et al 2022). Although in that method it adds the noise timing with the packets, it also helps in the active packet analysis. Thus the active packet analysis process has been done which is robust against such a noise. Thus it can be said that the packet tracing process is very helpful in the packet capturing which involves the analysis of the individual data sets by the optimization of the packets. Here in this project the developer has tried to use the wireshark software to analyze and estimate the equivalent bandwidth for the quicker use of the packet capturing using the capturing tools like the tcp dump and the wireshark. In the wireshark the data has been captured from the incoming and also from the going through data. After that the NICs have been analyzed to use the underlying packet capture tools. In general the wireshark considers the on-device data, which are captured from the local area network and those are run in the promiscuous mode. Here by using the NMAP’s packet capturing library the packets are captured. Here the three way handshake of the TCP communication has been done between the clients and the server. Thus by analyzing the SYN and the ACK the exchange of the information happened here (Dantas, M., et al 2019). Then After capturing the filters in the packets the capturing of the packets is done to the destination address. In this way by completing the three way TCP handshake among the client and the servers the checking has been done for the lost packets. In that part the statistics of the estimated data can be evaluated. This statistical data has been found with regards to the captured data, and after the capturing of the packets it involves analyzing the actual output of the dataset. Hence it can be said in this way the actual analysis of the packets can be done for the filtering of the TCP traffic networks by the analysis of the real time networking in the stipulated equivalent bandwidth.
Research Philosophy
In this project the developer has involved the analysis of the network monitoring process applying which the performance of the capabilities of the networks with the accumulation of the speed of the networks, can be evaluated. More than that here in this context the developer has enabled the network traffic analysis process with the estimation of the Gaussian methods , which helps to influence the performance degradation , slowness and many other issues occurring in the data transmission (Mukasheva, A.K., et al 2021). This project has been built to detect the IP networking process to analyze the probability distributions in the applied networking flow data set and also by applying the Gaussian approach the security of the traffic flow has been achieved against the various threats in the data flow. So here the application of the different data packet flow and by the estimation of the equivalent bandwidth has been done for the real time traffic analysis method.
Research Approach
In this project the developer has tried to do the qualitative analysis of the approached data. Here the project is involving the various project tools which are helpful in the detection of the malwares from the data model. It is also involved in the packet tracing process, and moreover in this way the analysis of the useless data and the negation of that data has been done (Hoppe, C., et al 2020). Among the various approaches of the network analysis the developer has chosen the Gaussian approach for the analysis of the wave packets. In that method the probability distribution for the actual statistical data with the accumulation of the packet waves in the frequency vs wavenumbers in ir rounded to the clustered data by analyzing the single data has occurred. Thus this means to create the most appropriate data application process within the wave packet communication for the statistical data.
Research Method
The network traffic analysis process is one of the processes in which the analysis of the various network packets can be done using the real time networking tools. Here the developer has applied the qualitative and quantitative analysis of the applied data model. Here the research method follows the statistical dataset to implement the monetarization of the network packets (Zakhleniu, N., et al 2019). Moreover the activity and the availability of the network protocols can be analyzed. Here also the anomalies or the various malwares can be identified by opposing the various operational issues in the stipulated network streamline. Here the network security has been included by the collection of the various historical data and also from the real time recorded data. Thus it involves the estimation of the IP networks in the equivalent bandwidth for the real time network analysis.
Data Collection Method
The data collection process of the network components also implements the packets, logs, and the flows, which are widely used in the flow of the mainstream line of the data collection mechanisms. Thus by assisting the network components and the controllers the monetarization of the flow of the data from the recorded available information has been done in the data collection method. Moreover it implements the mechanisms to estimate the equivalent bandwidth for the measurement of the quality of the network and to give the protection from the various malware attacks. Here the data collection process can be subdivided into the flow based data collection, the packet based data collection and the log based data collection. In the flow based network transmission it involves the flow of the packets and the characteristics of the packet flow has been analyzed by the observation of the period of timing. It is also determined by monitoring the location of the data and also depends on the nodes which contain the important dataset. By monitoring the flow collection of the network edged hosts and nodes, the network flow inside the switches, nodes, and the gateways can be analyzed. Thus it is the contribution of the inbound and the outbound data flow of the local area networking data streamline. Thus by applying this process the qualitative analysis and measurement can be done in the distributed data and in the cloud based data storage system. The log based data collection method is another method which is mostly applied to the recorded data system for the various network events. From the recorded data at first the data traces, status of the events and the most important is the diagnosis of the failures can be utilized (Parisis, G., et al 2021). This method of the data collection doesn’t involve any specific type of the file format , and in the log flow data collection each of the lines of the log can be written from the recorded data within the exact date and time, also the action and the operators can be taken in the appropriate place. Thus this method is mainly applicable to the deep packet inspection method for the statistical data and also it helps to detect the protocols by filtering the useless data. And here in this project the developer has implemented the packet based data collection that helps to carry the data using the TCP/IP protocols. Here the packets are transmitted from the source to destination to acquire the packets, and to aggregation, decoding is done to get the stipulated data. Here the classification of the packets has been done using the IP addresses, protocols and the ports as a header and the exchange of the data in between two communicating parties has been done through the encryption of the payloads. Here to extract the data and to classify the data it also involves the sampling method of the data collection for the real-time data.
Future Implementation
The real time data analysis using the various tools and data models has been analyzed in the above context. Here the developer has tried to give the light on the estimation of the equivalent bandwidth for the IP networks using the statistical data set with the real time network analyzer. In this project the developer has tried to build a clear concept by which the network monitoring process for the early detection of the links and the routing, designing and the implementation of the real time traffic solution has been drawn. In the time of doing this project the developer has faced many problems like the solution of the statistical analysis depends on the calculations and it also depends upon the amount of the data it contains. So it can be said that the optimal method of the data sources can be applied, by the implementation of the continuous monitoring system. And the data can occur according to the gathered data, which provides the proper notification regarding the data model applied to which industry. Thus by applying those changes in the proposed data model the developer can build a more developed structural implementation of the network traffic analysis process.
Gantt chart

Figure 7: Gantt chart
(Source: self-created in Project Libre)
Reference list
Journals
Alasmar, M., Clegg, R., Zakhleniuk, N. and Parisis, G., 2021. Internet traffic volumes are not Gaussian—They are log-normal: An 18-year longitudinal study with implications for modelling and prediction. IEEE/ACM Transactions on Networking, 29(3), pp.1266-1279.
Hernandez, L., Jimenez, G., Pranolo, A. and Rios, C.U., 2019, October. Comparative performance analysis between software-defined networks and conventional IP Networks. In 2019 5th International Conference on Science in Information Technology (ICSITech) (pp. 235-240). IEEE.
Alasmar, M., Parisis, G., Clegg, R. and Zakhleniu, N., 2019, April. On the Distribution of Traffic Volumes in the Internet and its Implications. In IEEE INFOCOM 2019-IEEE Conference on Computer Communications (pp. 955-963). IEEE.
Uhl, T., Klink, J. and Hoppe, C., 2020. Suitability of transport techniques for video transmission in IP networks. International Journal of Electronics and Telecommunications, 66(1).
Manankova, O.A., Yakubov, B.M., Serikov, T.G., Yakubova, M.Z. and Mukasheva, A.K., 2021. Analysis and research of the security of a wireless telecommunications network based on the IP PBX Asterisk in an Opnet environment. Journal of Theoretical and Applied Information Technology, 99(14), pp.3617-3630.
Queiroz, W., Capretz, M.A. and Dantas, M., 2019. An approach for SDN traffic monitoring based on big data techniques. Journal of Network and Computer Applications, 131, pp.28-39.
Lohrasbinasab, I., Shahraki, A., Taherkordi, A. and Delia Jurcut, A., 2022. From statistical‐to machine learning‐based network traffic prediction. Transactions on Emerging Telecommunications Technologies, 33(4), p.e4394.
Gong, Q., DeMar, P. and Altunay, M., 2022. ThunderSecure: deploying real-time intrusion detection for 100G research networks by leveraging stream-based features and one-class classification network. International Journal of Information Security, 21(4), pp.799-812.
Rodrigues, R., Pocta, P., Melvin, H., Bernardo, M.V., Pereira, M. and Pinheiro, A.M., 2020. Audiovisual quality of live music streaming over mobile networks using MPEG-DASH. Multimedia Tools and Applications, 79, pp.24595-24619.
Chen, A., Law, J. and Aibin, M., 2021, December. A survey on traffic prediction techniques using artificial intelligence for communication networks. In Telecom (Vol. 2, No. 4, pp. 518-535). Multidisciplinary Digital Publishing Institute.
Dong, S. and Xia, Y., 2022. Network traffic identification in packet sampling environment. Digital Communications and Networks.
Ganesan, E., Hwang, I.S., Liem, A.T. and Ab-Rahman, M.S., 2021, June. SDN-enabled FiWi-IoT smart environment network traffic classification using supervised ML models. In Photonics (Vol. 8, No. 6, p. 201). MDPI.
Damasevicius, R., Venckauskas, A., Grigaliunas, S., Toldinas, J., Morkevicius, N., Aleliunas, T. and Smuikys, P., 2020. LITNET-2020: An annotated real-world network flow dataset for network intrusion detection. Electronics, 9(5), p.800.
Schwarzmann, S., Marquezan, C.C., Trivisonno, R., Nakajima, S., Barriac, V. and Zinner, T., 2022. ML-based QoE estimation in 5G networks using different regression techniques. IEEE Transactions on Network and Service Management, 19(3), pp.3516-3532.
Mahajan, S., HariKrishnan, R. and Kotecha, K., 2022. Prediction of network traffic in wireless mesh networks using hybrid deep learning model. IEEE Access, 10, pp.7003-7015.
Pal, P., Tripathi, S. and Kumar, C., 2019. Bandwidth estimation in high mobility scenarios of IEEE 802.11 infrastructure‐less mobile ad hoc networks. International Journal of Communication Systems, 32(15), p.e4080.
Bebortta, S. and Senapati, D., 2021. Empirical characterization of network traffic for reliable communication in IoT devices. Security in cyber-physical systems: foundations and applications, pp.67-90.
Tan, L., Su, W., Zhang, W., Lv, J., Zhang, Z., Miao, J., Liu, X. and Li, N., 2021. In-band network telemetry: A survey. Computer Networks, 186, p.107763.
Ageyev, D., Mohsin, A., Radivilova, T. and Kirichenko, L., 2019, February. Infocommunication networks design with self-similar traffic. In 2019 IEEE 15th international conference on the experience of designing and application of CAD systems (CADSM) (pp. 24-27). IEEE.
Kakkavas, G., Stamou, A., Karyotis, V. and Papavassiliou, S., 2021. Network tomography for efficient monitoring in SDN-enabled 5G networks and beyond: Challenges and opportunities. IEEE Communications Magazine, 59(3), pp.70-76.
Su, H.M. and Maw, A.H., 2020, November. Comparative Analysis of Video Streaming in Software Defined Networking. In 2020 International Conference on Advanced Information Technologies (ICAIT) (pp. 12-17). IEEE.
Queiroz, W.J., Capretz, M.A. and Dantas, M.A., 2020. A MapReduce Approach for Traffic Matrix Estimation in SDN. IEEE Access, 8, pp.149065-149076.
Prokopovych, I., Lopakov, O., Kosmachevskiy, V., Babych, Y., Shvahirev, P. and Denysova, O., 2021. MATHEMATICAL MODELING OF INTERNET OF THINGS TRAFFIC IN AD-HOC NETWORKS WITH HYBRID ROUTING. Odes’ kyi Politechnichnyi Universytet. Pratsi, 2021(2), pp.36-46.
Dias, K.L., Pongelupe, M.A., Caminhas, W.M. and de Errico, L., 2019. An innovative approach for real-time network traffic classification. Computer Networks, 158, pp.143-157.
Know more about UniqueSubmission’s other writing services:

