OPENSSL HEARTBLEED LOOPHOLE ASSIGNMENT 2020
i) Implementation process of OpenSSL communication tool
As the government data is sensitive, it is required to encrypted data through a secure encryption tool. In this situation Bob and Alice has decided to use OpenSSL tool for transferring data from one end to another (Fischer et al. 2015). OpenSSL is an open source tools that can be download through their website and after that data scientist of the organization needs to know about the version of the tool so that they can understand functionality of the tools.
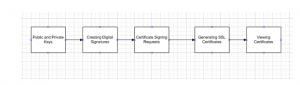
Figure 1: Process for implementing OpenSSL system
In these tools, data scientists are needed to implement encryption before sending the data. In this data encryption process should be as follow. For example if the developers want to encrypt and text “Bob and Alice” following command should be used.
| touch plain.txt
echo ” Bob and Alice ” > plain.txt openssl enc -aes-256-cbc -in plain.txt -out encrypted.bin //enter aes-256-cbc encryption password: Alice and Bob //Verifying – enter aes-256-cbc encryption password: Alice and Bob
|
After that encryption process it is needed to create private as well as public key so that user can decrypt and encrypt data (Haque, 2015). The encryption process has to be properly followed so that the security loops could be overridden and it could be brought under proper control process. A proper coding system needs to be followed as this would assists in refactoring the overall process that would be used to control the vulnerabilities that affects the quality of the security system adopted.
openssl genrsa -out key.pem 1024 command is useful for creating RSA key and this process allows the tool to create public and private key with .pem file. Digital signature is also required to create for verification purpose. openssl dgst -<hash_algorithm> -out <digest> <input_file> command is used by the data scientist for creating signature (Laskar et al. 2017). Additional security is required in the database and for that purpose database developers must generate SSL certificates. A better security measure needs to be followed so that the complex system could be analysed and standard SSL software could be adopted to control the negative impact of the vulnerabilities. This would provide a greater benefit to the members and ensure that the right things are done to control the possibilities of leakage of the facts. The industrial standard needs to be followed as this would help in coping with the requirements of the strategies that could be used for controlling the security measures.
Symmetric encryption method with security key exchange
In OpenSSL security tool secure socket layer technology has been used and developers need to create link between client and server. A proper security measure has to be followed to avoid the security related issue that causes a huge issue in securing the information. In order to increase the quality of the security measure, the members have to follow a proper coding system that is outlined by the guidelines. This would help in dealing with the challenging situations that arise at the time of implementing the security measures that are needed for the goal accomplishment. The variable factors would have to be handled in the process of introducing the changes in the coding measures.
Symmetric encryption
In symmetric encryption, pre shared key encryption process is followed by the developers. In this purpose Bob and Alice has used a single key for both encryption and decryption process (Malav, 2019). Sender encrypts as message with a key and the receiver for decrypting the message uses an identical key.
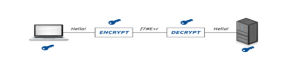
Figure 2: Symmetric encryption process and key exchange
(Source: Influenced by Malav, 2019)
In general data scientist of the concern government office has created the key with the size of 265 bits as the high key size can increase the security level of the database. Though the high number key has been used in this purpose, stronger encryption capabilities are required in the system (Pal & Chakraborty, 2017). Two types of algorithms can be used in symmetric encryption process including stream and block algorithms. In block algorithms block are used for encrypting bit length so that user can specify their key. System is programmed in a way that data in memory can be hold for future use. In stream algorithms, developers do not use memory; instead streams are used for data encryption purpose (Fischer et al. 2015). The coding process would use the proper method to control the challenges that are associated with the coding and securing measure. This is one of the basic requirements that are needed for sourcing the information and properly recording the relevant information that would be used for handing the SSL heartbleed loophole process. For implementing the change and following the security measure, the members have to properly focus on the adoption of the better security measure that would help in achieving the goals of retaining the information.
Security key exchange
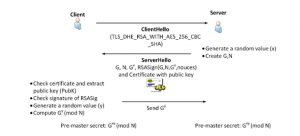
Figure 3: Security key exchange process in OpenSSL
(Source: Influenced by Pal & Chakraborty, 2017)
In a public network, key exchange operation can be performed. In this technique multiple user can access a single security key without understand the actual key. Both RSA and elliptic curve cryptography technique has been followed by the data scientists (Pal & Chakraborty, 2017). Multiple key can be produced in digital encryption process so that the users can access a specific power in the database. With a proper plan and strategy, the member would be able to introduce the changes that are needed for handling the security measures. These aspects are conducted by the quality analysis measures that would be used for retaining the information and follow a proper coding process.
ii)Challenges in key exchange process
Several types of issues can be there in key exchange process. As the ECC algorithm is depends on the finite fields and its algebraic structure, base point of the curve element can be impractical. In this situation, integer factorization in the key exchange process should be presumed and this can be responsible for large integer’s implementation in the server (Fischer et al. 2015). User of this system is allowed for creating product along with publishing it though large prime number implementation. One of the biggest challenges in this purpose is to keep the key private from other users in the same network.
Suggestion for overcoming the challenges through certificate authority
All the issue that can be happen in key exchange process may be solved by implementing certificate authority. It is recommend that the data scientist of the organization do no need to distribute the validate fingerprint as well as public key. Even at the time of updating and creating key pairs these keys are not needed to be validated. This entire technique is responsible for solving key exchange process.
Gurjar, S., Baggili, I., Breitinger, F., & Fischer, A. (2015). An empirical comparison of widely adopted hash functions in digital forensics: does the programming language and operating system make a difference? Proceedings of the Conference on Digital Forensics, Security and Law, , 57-68. Retrieved from https://search.proquest.com/docview/1791621609?accountid=188056
Haque, M. S. (2016). Web server vulnerability analysis in the context of transport layer security (TLS). International Journal of Computer Science Issues (IJCSI), 13(5), 11-19. doi:http://dx.doi.org/10.20943/01201605.1119
Shaw, N., Dey, B., Mazumder, S., & Laskar, F. M. (2017). Enhance the data security by changing the encryption technique based on data pattern in block based private key data encryption. International Journal of Advanced Research in Computer Science, 8(7) Retrieved from https://search.proquest.com/docview/1931130680?accountid=188056
Malav, A. (2019). Security improvement for realistic data using international data encryption cryptographic algorithm. I-Manager’s Journal on Computer Science, 7(2), 19-25. doi:http://dx.doi.org/10.26634/jcom.7.2.15465
Pal, S. K., & Chakraborty, N. (2017). Application of cosmos’s law of merges and split for data encryption. International Journal of Computer Network and Information Security, 9(5), 11. doi:http://dx.doi.org/10.5815/ijcnis.2017.05.02
Khalaf, E. F., & Kadi, M. M. (2017). A survey of access control and data encryption for database security. Journal of King Abdulaziz University, 28(1), 19-30. doi:http://dx.doi.org/10.4197/Eng.28-1.2