Cyber Security Application Portfolio
Cyber security is principally regarding individual, procedure, and innovation supporting to the full scope of danger reduction, weakness reduction, discouragements, universal commitments, occurrence reactions, and some strategies and exercise,
including computers arranges activities, information affirmation, law authentication, and some others.” Cyber security is assurance of Web-associated framework, including equipment, program, and data from digital assault.
It is gathered of 2 words one is digitals and another is privacy. Digital is identified with the innovations that contain framework, systems and project or data. But privacy identified with the assurance that incorporates framework privacy.
It is the gathering of advancements, procedure, and practice intended to protect system, gadget, project, and data from assaults, robbery, and others TESCO is the organisation to which all the below factors of Cyber Security has been provided.
Threat and vulnerability modelling, risk prioritisation
- Include a complete partner point of view. Partners incorporate the entrepreneurs just as representatives, clients, and even merchants. These players can possibly adversely affect the association (potential dangers) and yet they can be resources in assisting with moderating danger (Norman, 2017).
- Designate a focal gathering of workers who are answerable for chance administration and decide the fitting financing level for this action.
- Implement fitting arrangements and related controls and guarantee that the suitable end clients are educated regarding all changes.
- Strategies are developed for recording the information and then processing it in an accurate manner, and this would be useful in handling the data processing and information recording process. A proper strategy is needed as this would be useful in handling different challenges where the information are supposed to be recorded and corrective actions are supposed to be introduced.
- Decide the time that is needed for recording the facts.
- Monitor and assess strategy and control adequacy. The wellsprings of hazard are ever-changing, which implies your group must be set up to make any vital acclimations to the system.
Anticipation of emerging threats
It audits receptive ways to deal with digital assaults where current activities depend on past conduct, and proactive methodologies guided by expectations about what’s to come. The methods in this area permit us to choose activities dependent on their foreseen results.
They besides empower us to work in a persistently advancing condition. This capacity separates expectant methods from prescient strategies. Procedures in this segment incorporate ill-disposed reasoning, situation displaying, and expectation of disappointment.
They are encapsulated in a portion of the later ways to deal with managing digital assaults. Care is the capacity to find and oversee startling conduct. It consolidates the idea of expectation with that of versatility. Expectation contains distraction with disappointment, hesitance to disentangle, and affectability to activity.
At the point when we apply those procedures to digital security, they suggest that we should give close consideration to indications of anomalous conduct in our systems and frameworks, question what we underestimate and consistently scan for an intelligible clarification of our perceptions (i.e., keep up numerous contending theories about the condition of the world).
Expectant Failure Determination is a methodology for imagining disappointment situations. Its attention isn’t on gaining from what disappointments have happened previously, however on finding what disappointments may happen and how they can be achieved.
AFD has as of late been applied to show disappointment situations in digital security (Turner, 2018). The objective of the methodology is to manufacture a stock of assets (pointers, apparatuses, individuals, vulnerabilities, and data) that have empowered disappointments previously.
A significant objective of MAC is to implement data stream arrangements to guarantee privacy and trustworthiness. This should be possible by increasing the optional access control with the obligatory access control.
To allow the availability, MAC adopts a two-advance strategy. To begin with, each subject’s entrance benefits put away in the optional access control lattice are checked. In any case, having approvals put away in the entrance control lattice isn’t adequate to play out the activity.
This process helps in –
- Collecting the sources and using the information in an accurate manner
- Applying the information for making the right decisions
- Protecting the relevant information
- Collecting the sources that would be used for the collective conduct of the works.
These are the necessary factors where the changes are implemented for handling the business based issues where the relevant changes are implemented for getting the better results. They are important for the collectively analysing the relevance of the information and then processing it in a proper manner.
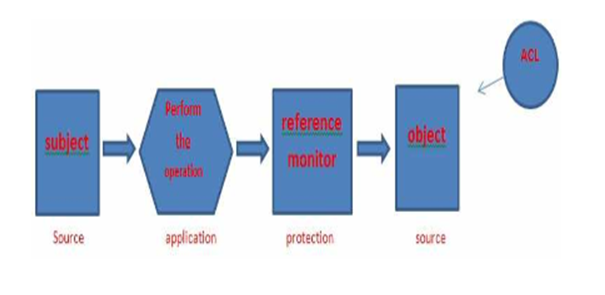
Figure 2: Access Control List
Likewise, the activity must be approved by the MAC strategy, over which subjects have no control. Macintosh approaches oversee access based on grouping of subjects and articles in the framework. With respect to this model, security levels are allotted to subjects and items.
The security level related with an item, likewise called security order, mirrors the affectability of the data contained in the article, i.e., the potential harm which could result from unapproved exposure of the data. The security level related with a subject, additionally called exceptional status, mirrors the subject’s reliability.
Defensive system design principles, in depth and breadth
As far as data security, a manager layers their advantages in cautious estimates that will dissuade easygoing aggressors trying to increase unapproved get to. Layers of guard regularly cover so as to guarantee that traffic is handled on numerous occasions by heterogeneous security advances with the expectation that the inadequacies of one security control are secured by another.
A very much tuned barrier inside and out design will forestall a greater part of assaults and alarm a head to interruptions that go through.
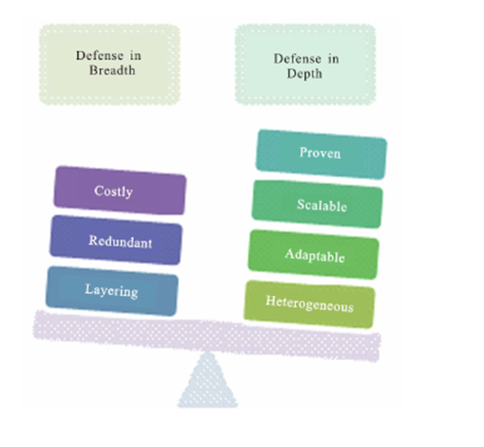
Figure 2: Defence in Breadth and Depth
Assessing the Defence in Depth system as far as present dangers will give extra understanding into the key parts of the procedure. Computerized assaults happen continually against any open confronting administration; be that as it may, these assaults need modernity as they regularly are completed by a program as opposed to a live, talented individual(Hegde, 2018).
Protection in Depth is a magnificent technique for limiting and forestalling computerized assaults, considering robotized assaults search out the most powerless resources confronting the open Internet.
A functioning assailant situation wherein a live aggressor is endeavouring to abuse a data resource is progressively hard to dissect. Contingent upon the wellspring of the assault (inner or outside), the Defence in Depth engineering may give differential assurance.
Each of the previously mentioned security gadgets gives an impediment that an assailant must explore; even talented aggressors who need inspiration will be stopped by a plenty of security controls.
Conversely, systems saw a huge increment in assaults from inside a system when assailants discovered that infiltration from within was altogether simpler since it circumvents a dominant part of the border safeguards. While the resistance top to bottom system ought to be applied to all advantages similarly, numerous professionals grouped guards at the edge.
Scope, lifecycle, maintenance and sustainability
Simulate
It is over the top expensive to (re)design, test and introduce a keen framework, in light of the fact that the force framework in activity should consistently be accessible, so bringing it down so as to perform tests is beyond the realm of imagination Therefore, two choices can be utilized.
One elective comprises of setting up a physical PC organize missing of any basic information, performing digital assaults on the system, and gathering information from interruption recognition frameworks. The subsequent option is to create manufactured information using reproduction. A re-enactment model would then be able to be utilized to break down security dangers and other system perspectives.
Analyse
In many systems, the examination of reproduction results is a test in light of the fact that the watched framework might be enormous and complex.
Numerous parts are in this manner associated, and changes in a single segment may cause unexpected consequences for different segments in the framework a deliberate and comprehensive way to deal with examination is consequently required. From the outset, each article in the demonstrated topology is broke down in disconnection.
Plan
This stage is basic when structuring needed security level. Achievability study will be directed to evaluate the methodology, diagram the discoveries from past two stages and characterize financial aspects (Newhouse, 2017). Arranging will incorporate all partners and recognized dangers will be managed moderation procedures.
Clear archive with financial matters and in any event three situations will be arranged and talked about with leaders. Prudent and specialized proficiency of situations will be surveyed by applying a multi-rules model supporting deficient or fluffy data, and different inclination structures and styles in a collective choice creation setting.
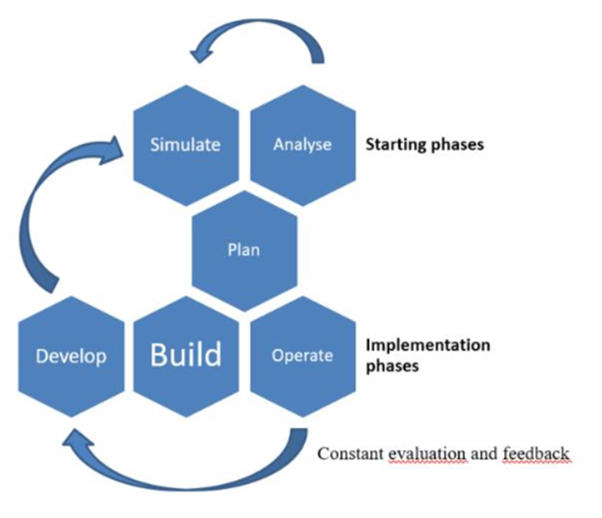
Figure 3: Life Cycle
The life cycle analyses are conducted so that the best information is collected and it is processed for increasing the business conduct. Here the ways the information would e collected and the processed for making the best use of the data are plane and implemented.
This is a crucial factor that would need a proper planning and task execution process, where the relevant data would be analysed and corrective processes are adopted and introduced.
Develop
Creating stage is initial step of execution process. Creating process will be acted in all territories: HR, equipment parts and programming segments. Characterizing of the key components for security activity focus is significant piece of this stage, just as profundity and method of activity.
Hierarchical effects will be evaluated and tended to, authoritative changes conceived and imparted. The association must grasp the procedure in this stage.
Build
Building stage is the second piece of usage procedure and comprises of buying and introducing components of Security Operation Centre. A security activities focus regularly, a SOC is prepared for get to observing, and controlling of lighting, alerts, and vehicle boundaries.
They give ongoing investigation of security alarms produced by applications and system equipment. Last phase of this stage is pre creation activity and go-live technique.
Operate
Activity stage begins with charging of the framework and placing the SOC into creation. Not just the operational issues must be tended to; hierarchical and social issues will be tended to also.
Endeavours to improve the proficiency of security activity focuses (SOCs) have accentuated fabricating instruments for investigators or understanding the human and hierarchical variables included (armakiewicz, 2017).
This may require more exertion and require longer progress period. Preliminary activity must framework potential holes and security dangers. Activity stage will continually assess execution and criticism to improvement stage built up to connect potential holes.
Stress that last three stages will continually be rehashed to manage changes in digital condition and keep up and improve digital security level (Trappey, 2018).
Technologies, options for technical implementation
Digital security assaults are currently genuine, present, and expanding in both their recurrence and advancement.
While it is some of the time recommended that basic ventures can’t hazard interfering with activities to retrofit suitable security, governments are currently resolved to force administrative controls so as to ensure national basic foundation.
Confronted with obligatory necessities to make sure about their modern resources, interchanges arrange administrators must be sure they have played it safe to shield their systems from assault. Every IC is extraordinary and has exceptional necessities, so the unpredictability of security arranging ought not to be thought little of.
Experienced security experts are required at each stage, from prerequisites catch, to plan, usage, testing and past, incorporating including them in intermittent surveys and normal reviews of all security approaches, practices, the executives and revealing.
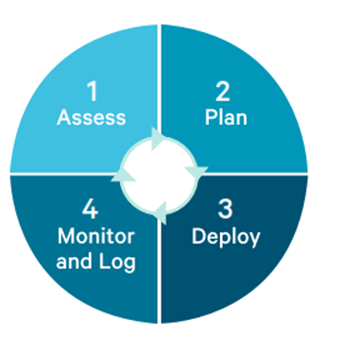
Figure 4: Implementation Process
Assess
Report the security prerequisites for your ICS. These are to a great extent driven by the norms and guidelines that apply to your industry, just as by the special arrangement of your ICS. We should
- Recognize which digital security guidelines and principles are pertinent,
- recognize all equipment, programming and system segments just as the entirety of their interconnections that can give get to,
- Locate every single potential purpose of access,
- Determine all the authentic clients and applications and the entrance benefits they require
Plan
There will be an assortment of alternatives to consider for tending to the vulnerabilities recognized by your evaluation. Every IC has its own unique prerequisites that are revealed during the Assessment stage. Proficient aptitude during the arranging stage will organize which choices to remember for your arrangement. In any case, it is conceivable to diagram a few methodologies that administrators regularly use to alleviate the vulnerabilities of an ICS.
Deploy
Execute your ICS security plan, handling the most pressing vulnerabilities first the most widely recognized dangers which could cause the most serious harm (Tselios, 2018). Organizing vulnerabilities and dangers can assist with making a staged sending plan. Making sure about a modern control framework definitely includes upsetting its day in and day out activities.
Controllers and all degrees of interior administration must get tied up with the arrangement task and bargain on approaches and punishments that will bring on any disturbance.
It involves cost versus hazard. Guarantee that you have included preliminaries of all your security strategies and your preparation plan before going live. Progressively, national and provincial controllers are requiring compulsory consistence with security gauges and accreditation under consistence programs.
Monitor and Log
It is anything but a matter of if, however when a digital security break will happen. The one suspicion you can securely make is that your system isn’t sheltered. You can hope to endure a penetrate of security and ought to along these lines have your reaction arranged ahead of time.
Indeed, even with the best procedures, apparatuses and committed security work force, another structure assault can get past. A decent beginning stage is to gather, store and normally report information on all sudden traffic or abnormal gets to over your ICS, and keep narratives so you can spot inclines in security penetrates.
And keeping in mind that it might appear glaringly evident, an imperative part of relief is to abstain from rehashing similar slip-ups — cautious assessment of the review logs can be valuable to set up what occurred. To guarantee the most ideal result, numerous associations keep up a Computer Security Incident
Encryption for communications and storage
Encryption alludes to set of calculations, which are utilized to change over the plain content to code or the confused type of content, and gives protection. To unscramble the content the recipient utilizes the “key” for the encoded content. It has been the old technique for making sure about the information, which is significant for the military and the administration activities. Presently it has ventured into the non military personnel’s everyday life as well.
Figure 5: Encryption Process
The web exchange of bank, the data move through systems, trade of crucial individual data and so on that requires the usage of encryption for privacy reasons. Greater part of the business totally relied on the online for the purchase, sell, move cash over e-banking framework, sort out, video chat, offer different types of assistance all required the encryption for association and privacy.
Prior PCs don’t have the system administrations office. As the development of systems administration industry the product’s all the more promptly accessible for the people. The upside of the business over the web is acknowledged and to get the unapproved individuals
Policies, monitoring, response plans
In the event that it alludes to other security approach records; or it very well may be amazingly point by point. A few firms think that it’s simpler to fold up every single individual approach into one WISP.
For instance, you may think that its simpler to drill down the entirety of the strategies for making sure about your association’s IT assets, for example, passwords, cell phone the executives, email, and so on and just compose a passage of rules that firm part should follow. The key parts of a WISP include:
- Asset Inventory – This is a hierarchical assessment of every single instructive resource the firm keeps up including touchy customer and worker information
- Threat Assessment – This is an assessment of what dangers exists to those advantages
- Disaster Recovery Plan – This is a specialized arrangement that is created for explicit gatherings to permit them to recuperate a specific business application; i.e., organize share drives, practice the executive’s arrangements, and so on.
- Breach Notification Plan – This is a rule for every single basic gathering if the association’s system is penetrated. It ought to incorporate warning plans and contact data for specialists and customer contacts and potentially credit checking administrations (Remesnik, 2020).
- Security Awareness Plan – This is a preparation and the board plan the frameworks strategies for distinguishing obscure assets in the structure, email security, required encryption, advanced mobile phone rules and safe Internet perusing.
- Guidelines for refreshing and testing the WISP all the time
Cost, roles, skills and human resources
On the off chance that there is any expectation in moderating the harms identified with a penetrate, quick activity is central. The jobs and duties arrangement has one sole reason – to plot who will affirm the data security strategy, appoint security jobs, facilitate and survey the execution of security over the association.
The strategy ought to characterize incorporate a chief and a delegate from the IT gathering. Obligations, for example, those for inside control responsibility, review of frameworks the executives and counteraction, and episode reaction ought to be relegated and worked out.
Among the most critical dangers to security and protection are pernicious access, forswearing of administration and robbery of administrations, particularly information.
Assailants are progressively utilizing Iota hacks to organize different sorts of disturbances. This implies tainting associated gadgets with malware and planning them to release a deluge of Internet traffic to cut down sites and other online assets in what’s known as a circulated refusal of administration (DDoS) assault.
Mobile phones are turning into a technique to give a proficient and advantageous approach to access, find and offer data; be that as it may, the accessibility of this data has caused an expansion in digital assaults.
Presently, digital dangers run from Trojans and infections to botnets and toolboxs. This need security and arrangement driven frameworks is an open door for malignant digital assailants to hack into the different famous gadgets. Conventional security programming found in work area figuring stages, for example, firewalls, antivirus, and encryption, is broadly utilized by the overall population in cell phones
Chaisse, J. and Bauer, C., 2018. Cybersecurity and the Protection of Digital Assets: Assessing the Role of International Investment Law and Arbitration. Vand. J. Ent. & Tech. L., 21, p.549.
Hegde, V., 2018, January. Cybersecurity for medical devices. In 2018 Annual Reliability and Maintainability Symposium (RAMS) (pp. 1-6).
Jarmakiewicz, J., Parobczak, K. and Maślanka, K., 2017. Cybersecurity protection for power grid control infrastructures. International Journal of Critical Infrastructure Protection, 18, pp.20-33.
Newhouse, W., Keith, S., Scribner, B. and Witte, G., 2017. National initiative for cyber security education (NICE) cyber security workforce framework. NIST Special Publication, 800, p.181.
Norman, M.D. and Koehler, M.T., 2017, October. Cyber Defence as a Complex Adaptive System: A model-based approach to strategic policy design. In Proceedings of the 2017 International Conference of the Computational Social Science Society of the Americas (pp. 1-1).
Remesnik, E.S. and Sigal, A.V., 2020, March. Application of Fishburn Sequences in Economic and Mathematical Modeling. In International Scientific Conference” Far East Con”(ISCFEC 2020) (pp. 2733-2737).
Rouse, T., Levine, D.N., Itami, A. and Taylor, B., 2019. Benefit Plan Cybersecurity Considerations: A Recordkeeper and Plan Perspective. The Disruptive Impact of FinTech on Retirement Systems, p.86.
Sawik, T., 2018. Selection of Cybersecurity Safequards Portfolio. In Supply Chain Disruption Management Using Stochastic Mixed Integer Programming (pp. 315-335). Springer, Cham.
Svilicic, B., Kamahara, J., Celic, J. and Bolmsten, J., 2019. Assessing ship cyber risks: a framework and case study of ECDIS security. WMU Journal of Maritime Affairs, 18(3), pp.509-520.
Trappey, A.J., Trappey, C.V., Govindarajan, U.H., Sun, J.J. and Chuang, A.C., 2016. A review of technology standards and patent portfolios for enabling cyber-physical systems in advanced manufacturing. IEEE Access, 4, pp.7356-7382.
Tselios, C., Tsolis, G. and Athanatos, M., 2019. A Comprehensive Technical Survey of Contemporary Cybersecurity Products and Solutions. In Computer Security (pp. 3-18).
Turner, A.J. and Mossman, S., 2018. Applying the cyber security game to a point-of-sale system. In Disciplinary Convergence in Systems Engineering Research (pp. 129-144).
Vargas, W., 2017. Cybersecurity Standards Are Standing Up to the Bad Actors. Biomedical instrumentation & technology, 51(s6), pp.7-8.



What’s up, just wanted to tell you, I loved this article. It was funny. Keep on posting!
https://suba.me/
I think this is a real great blog article.Much thanks again. Keep writing.
https://yuzuryn.tumblr.com/
Really appreciate you sharing this blog.Much thanks again.
https://augustaseoweb.com/bankruptcy-attorney-augusta
I loved your blog post.Really looking forward to read more. Cool.
https://augustaseoweb.com/therapist-columbia
A round of applause for your post.Much thanks again. Awesome.
https://www.lplastic.com
I appreciate you sharing this blog.Much thanks again.
https://www.mingdeplastic.com/plastic-sheet/pvc-sheet
My brother suggested I might like this blog. He used to be entirely right. This submit actually made my day. You cann’t believe simply how a lot time I had spent for this info! Thank you!
http://sqworl.com/vwfklr
Genuinely no matter if someone doesn’t understand afterward its up to other viewers that they will assist, so here it takes place.
https://www.siatex.com/promotional-t-shirt-suppliers-manufacturers-in-bangladesh/
Great blog post. Much obliged.
https://idiaphragm.com/page-16.html
F*ckin’ tremendous issues here. I’m very happy to peer your post. Thank you so much and i am having a look forward to contact you. Will you kindly drop me a mail?
https://www.siatex.com/blank-t-shirt-suppliers-and-manufacturers-in-bangladesh/
I really like reading a post that can make men and women think. Also, many thanks for allowing for me to comment!
https://www.thecriticalobserver.com/critical-observations/1305090_worst-types-of-injuries-in-boxing
Wow that was strange. I just wrote an incredibly long comment but after I clicked submit my comment didn’t show up. Grrrr… well I’m not writing all that over again. Regardless, just wanted to say excellent blog!
https://grindanddesign.com/members/lawsecure32/activity/327969/
anti fungal canadian pharmacy coupon code 2016
https://telegra.ph/Facts-You-Need-To-Be-Informed-About-Online-Casino-Games-05-12
Thank you ever so for you blog post.Really thank you! Cool.
https://grindanddesign.com/members/hipbucket73/activity/327763/
Now I am ready to do my breakfast, once having my breakfast coming yet again to read other news.
I really like and appreciate your blog article.Much thanks again. Really Cool.
http://www.bizholi.com/m/shop/index.php?no=253
That is a good tip particularly to those fresh to the blogosphere. Brief but very precise info Appreciate your sharing this one. A must read post!
https://www.housetohomepros.com/business-business-goods-services/carbonclick
Hi, I do think this is an excellent blog. I stumbledupon it 😉 I may come back yet again since I book markedit. Money and freedom is the greatest way to change, may yoube rich and continue to help others.
https://instapages.stream/story.php?title=financial-institution-4#discuss
Boxvhe – graduate school personal statement Srgtpc jmjubq
https://www.instapaper.com/p/plainflavor03
Major thanks for the blog. Want more.
https://store.smoktech.com/product/details/solus-2-kit
Highly energetic article, I loved that bit. Will there be apart 2?
https://k12.instructure.com/eportfolios/400292/Home/Soccer_Sports_Betting__Tips_To_Keep_In_Mind_When_Betting_Online_
Nicely put. With thanks!essays on community service all college essays medical school personal statement writing service
https://www.amazon.fr/gp/product/B08WK63YDH
I dont leave lots of comments on a great deal of blogs each week but i felt i had to here. A hard-hitting post.
https://gpsites.win/story.php?title=deposit-canadian#discuss
Major thanks for the blog.
https://ttrebags.com/
I really liked your article.Really looking forward to read more. Will read on…
https://www.marcellusmatters.psu.edu/?URL=https://www.monmall.ph/diapers-price
I would like to thank you for the efforts you have made in writing this article.Greetings! Very helpful advice in this particular article!토토It is the little changes that make the greatest changes.Thanks a lot for sharing!
https://penzu.com/p/2b2246d2
ivermectin 4 ivermectin pills – ivermectin over the counter
https://mcconnell-villumsen.mdwrite.net/order-the-most-beneficial-dashboard-camera-get-some-tips
Members achieve access our premium sources, written and curated by market professionals.
http://languagelearningbase.com/contributor/masschance1
Hey there! I simply wish to offer you a big thumbs up for the great info you have right here on this post. I’ll be returning to your blog for more soon.
http://qooh.me/beggarniece6
Do you have a spam problem on this blog; I also am a blogger, and I was curious about your situation; many of us have created some nice practices and we are looking to swap strategies with other folks, why not shoot me an e-mail if interested.
https://justpin.date/story.php?title=agb99-link-alternatif#discuss
I’m gone to say to my little brother, that he should also pay a visit this blog on regular basis totake updated from most up-to-date news.
http://grablead.site/story.php?id=26477
Amazing! Its really remarkable post, I have got much clear idea regarding from this paragraph.
https://www.kawalnews.id/prediksi/hk
A round of applause for your article.Really thank you! Cool.
https://www.nide-international.com/pro-86-Car-Windshield-wiper-motor-commutator.html
I cannot thank you enough for the blog article.Much thanks again. Awesome.
https://www.elt-holdings.com/en/product/24/3D-Metal-Printing
Appreciate you sharing, great article post.Thanks Again. Really Cool.
https://www.elt-holdings.com/sp/product_show/3k7d3z73jbgg4/Moldura-de-inserciЁ®n-de-clip-de-par
Thank you for the good writeup. It in fact was a amusementaccount it. Look advanced to far added agreeable from you!However, how could we communicate? asmr 0mniartist
https://www.articlemarket.org/
Heya i am for the first time here. I found this board and I find It truly helpful & it helped me out a lot. I hope to offer something back and help others like you aided me.
https://jobs.asoprs.org/employers/2003568-tyrone4587
Wow that was strange. I just wrote an extremely long comment but after I clicked submit my comment didn’t appear.Grrrr… well I’m not writing all that over again. Regardless, just wanted to say fantastic blog!
https://driantpace.mystrikingly.com/
I really liked your article post.Much thanks again. Really Cool.
https://earthloveandmagic.com/activity/p/252595/
efectos secundarios de lisinopril hydrochlorothiazide weight loss
https://www.complaintsboard.com/noel-meza-attorney-san-diego-unethical-attorney-services-c1583489
Hi! I’ve been following your blog for some time now and finally got the bravery to go ahead and give you a shout out from Atascocita Texas! Just wanted to say keep up the good job!
stromectol covid ivermectin – ivermectin ebay
https://www.nexusarcana.com/forums/memberlist.php?&page=12&pp=30&order=asc&sort=joindate
ivermectin pills amazon ivermectin pills for humans for sale Dtvhlue
https://soapufa.ru/
queen creek apartments york creek apartments apartments in lehi utah
https://twitter.com/BenitoCarpente8/status/1666276007412920325
These are really great ideas in on the topic of blogging.You have touched some nice factors here. Any way keep up wrinting.
https://permitdeutsch.com/service/fuhrerschein-kaufen/
After reading your article I was amazed. I know that you explain it very well. And I hope that other readers will also experience how I feel after reading your article.파워볼게임
https://permitdeutsch.com/service/fuhrerschein-kaufen/
I am so grateful for your blog article.Much thanks again. Fantastic.
https://www.vsol-xgspon.com/en/page/Why-PON-is-called-Passive-Optical-Network
Wow, great article.Really thank you! Want more.
https://www.injection-moldingg.com
Very neat blog article.Much thanks again. Really Great.
https://www.plc-wholesale.com/New-sealed-1769-L27ERM-QBFC1B-Allen-Bradley-CompactLogix-5370-L2-Ethernet-p181729.html
male erectile dysfunction best otc ed pills – best online pharmacy india
https://weeklycasinos.com
Heya just wanted to give you a brief heads up and let you know a few of the images aren’t loading correctly. I’m not sure why but I think its a linking issue. I’ve tried it in two different internet browsers and both show the same outcome.
https://forum.tvfool.com/member.php?u=1388588
chloroquine india aralen – aralen phosphate
https://eubd.edu.ba/
zion market darknet liberty darknet market
https://onearchersplace.net/
Essay writing service discount best medical school essay editing service top essay writing services
https://tonpepite.com/
I always was concerned in this subject and still am, thanks for putting up.
http://hotcoffeedeals.com/2023/06/17/ways-to-buy-stocks-eliminate-your-method-into-the-course-of-action/
zwrot podatku z zagranicy bielsko biala says:F*ckin’ awesome things here. I’m very satisfied to see your post. Thanks so much and i am looking ahead to touch you. Will you please drop me a e-mail?Reply 05/14/2020 at 3:28 am
https://www.google.co.ck/url?q=https://sites.google.com/view/dichvuhuthamcautoancau
Decimal odds quote possible return where as fractional odds quote potential earnings.
http://test.vnushator.ru/members/karatecare25/activity/2272669/
hydroxychloroquine and zinc hydroxychloroquine dosage
There is certainly a great deal to know about this topic. I like all of the points you made.
https://issuu.com/orangefir6
Very good postings, Regards. essaywriting4you.com heading for college essay
http://klusbedrijfpascalpak.online/story.php?id=29908
The North Carolina Education Lottery reported that sales of Powerball tickets through the16 drawings major to the jackpot resulted in $44.three million in sales.
http://qooh.me/coughfear3
Hi, this weekend is fastidious for me, for the reason that thistime i am reading this fantastic informative piece of writing here at my home.
https://iheartplacer.com/members/juneslice93/activity/358156/
Great, thanks for sharing this blog article. Really Cool.
https://rush-one.net/products/Kamagra7CE58DB0E5BAA6E6B6B2E6858BE5A8817CE69E9CE5878DE5A8817C7E585A5-605073ac9843d8f1.html
I have read so many articles on the topic of theblogger lovers except this paragraph isgenuinely a good article, keep it up.
Aw, this was an extremely nice post. Finding the time and actual effort to create a very good articleÖ but what can I sayÖ I hesitate a whole lot and never manage to get nearly anything done.
https://www.google.com.ai/url?q=http://eukallos.edu.ba/
I really loved this blog post. I’ll return for more to enjoy. Thank you!
https://lighttwist1.bloggersdelight.dk/2023/06/24/high-quality-education-is-today-possible-along-with-us/
wow, awesome article.Really thank you!
https://chennai-airport-to-pondic80098.educationalimpactblog.com/40984339/the-smart-trick-of-india-visa-that-no-one-is-discussing
Wow that was unusual. I just wrote an extremely long comment but after I clicked submit my comment didn’t appear. Grrrr… well I’m not writing all that over again. Regardless, just wanted to say excellent blog! see details
https://www.goodreads.com/user/show/167046018-mattiemeyers
Aw, this was a very nice post. Finding the time and actual effort to make a really good articleÖ but what can I sayÖ I put things off a whole lot and never seem to get anything done.
http://lamulher.online/story.php?id=26640
Looking forward to reading more. Great blog.Really looking forward to read more. Keep writing.
https://angelooetg31098.blogproducer.com/23822877/neotokyo-en-sosial-kombinasjon-av-japansk-mat-håndverk-og-mainstream-samfunnet
Hello there, just became alert to your blog through Google, and found that it is truly informative.I am gonna watch out for brussels. I’ll be grateful if you continue this in future.A lot of people will be benefited from your writing.Cheers!
https://ctxt.io/2/AACQT-cAFA
This is one awesome article.Really looking forward to read more. Will read on…
https://mylesoqwls.blogdemls.com/824683/not-known-facts-about-lungeklinikken-i-lillestrøm
Thanks for one’s marvelous posting! I truly enjoyed reading it, youmay be a great author.I will remember to bookmark your blog and definitelywill come back in the future. I want to encourage yourself to continue your great work,have a nice weekend!
http://meclizinex.com/
No matter if some one searches for his necessary thing, so he/she wishes to be available that in detail, so that thing is maintained over here.
https://github.com/phpboiler
Heya i’m for the primary time here. I found this board and Ito find It truly helpful & it helped me out much. I’m hoping to provide one thing again and aid others like you aided me.
https://fosterestateplanning.com/members/drygallon8/activity/440662/
Thanks a lot for the blog article.Really thank you! Really Cool.
https://www.marklifeprinter.com/
antivert
This is one awesome article post.Thanks Again. Fantastic.
https://www.medlonchina.com
top ed pills indian pharmacies without an rx – best ed pill
https://0.gp/awQDJ
Valuable advice. Many thanks!writing literature essays find phd thesis technical writing service
https://te.legra.ph/Most-Appropriate-Betting-Chance-Of-Your-Spare-Time-07-03
There as certainly a lot to know about this issue. I like all of the points you have made.
http://thebakestop.site/story.php?id=30595
Hello there! I could have sworn I’ve been to your blog before but after looking at a few of the posts I realized it’s new to me. Anyways, I’m definitely pleased I discovered it and I’ll be book-marking it and checking back frequently!
https://nyborg-tierney-2.technetbloggers.de/ants-in-the-bathing-room-eliminate-them
Hi there, I do believe your blog might be having internet
https://canvas.instructure.com/eportfolios/2252727/Home/Pest_Control_Management_Boise_Stay_away_from_the_Infestation_
Say, you got a nice article.Really thank you! Cool.
https://www.beautychemical.com/Products/Sodium-dichloroisocyanurate_07.html
Whoa many of awesome facts! cbd oil legal states
https://socialbookmarknew.win/story.php?title=the-hoi-an-spa#discuss
is chloroquine phosphate over the counter renaud muselier heart rate watch walmart
I want to to thank you for this fantastic read!! I definitely enjoyed every little bit of it. I have you saved as a favorite to look at new stuff you post…
Gerçek Aşk İçin Aşk Duası
I cannot thank you enough for the blog.Thanks Again. Keep writing.
https://www.chinatopmarketing.com/douyin-marketing-service.html
Thank you ever so for you article.Much thanks again. Much obliged.
https://yttomp333232.blog-kids.com/21001701/ytmp3-audio-the-ideal-youtube-to-mp3-converter
Hmm is anyone else encountering problems with the pictures on thisblog loading? I’m trying to find out if its a problem on myend or if it’s the blog. Any suggestions would be greatly appreciated.
http://poetical.site/story.php?id=28578
It’s enormous that you are getting thoughts fromthis piece of writing as well as from our discussion made here.
https://gfycat.com/@destinynolan
generic stromectol for humans – stromectol over the counter ivermectin australia
http://upapparel.art/story.php?id=23529
Good post. I learn something totally new and challenging on blogs I stumbleupon on a daily basis. It will always be useful to read through articles from other writers and practice a little something from their sites.
https://setan2020.blogspot.com/2023/07/ytmp3-ultimate-online-tool-for.html
Great blog.Really thank you! Keep writing.
https://www.anclighting.com/table-lamps/
Hi there mates, how is all, and what you wish for to say on the topic of thisarticle, in my view its genuinely awesome in favor of me.
https://lostmypet.ca/members/forksharon1/activity/868147/?q=2Factivity2Fp2F8681472F
Thanks for the auspicious writeup. It actually was aleisure account it. Look advanced to more brought agreeable from you!By the way, how can we keep in touch?
https://k12.instructure.com/eportfolios/450373/Home/Information_You_Have_To_Be_Informed_On_Advantages_Of_Customised_TShirts_
Hi, I read your new stuff on a regular basis. Your humoristic style is awesome, keep doing what you’re doing!
Really enjoyed this post. Want more.
https://www.arktechcn.com/5mm-Purple-Round-Shape-LED-p.html
I really like and appreciate your blog post.Really thank you! Fantastic.
https://www.senmobrew.com/Product/Fermentation-system_09.html
pretty practical material, overall I feel this is well worth a bookmark, thanks
https://listophile.com/
I like the valuable information you provide in your articles.I will bookmark your blog and check again here regularly.I am quite certain I will learn plenty of new stuff right here!Best of luck for the next!
https://worldfitforkids.org/members/pantrypantry78/activity/785725/
I just like the helpful info you supply on your articles.I’ll bookmark your blog and test again right here frequently.I am moderately certain I’ll be told lots of new stuff properhere! Best of luck for the next!
http://www.mmoutreachinc.com/links.html
Hi, I do think this is an excellent blog. I stumbledupon it 😉 I may come back once again since I bookmarked it. Money and freedom is the greatest way to change, may you be rich and continue to guide other people.
https://pagan.com.ua/privitannya/garni-privitannia-z-pershim-dnem-vesni-ykrainskou-movou/
What a data of un-ambiguity and preserveness ofvaluable know-how regarding unexpected feelings.
Thanks a lot for the blog post.Thanks Again. Really Great.
https://texasfinancial.blob.core.windows.net/financing/mortgage.html
Minimize stress to maintain clear, healthy skin.
https://anotepad.com/notes/x55pfaiw
A round of applause for your post.Much thanks again. Will read on…
https://yiyuanzhengming.com/
I really like and appreciate your post.Really looking forward to read more. Awesome.
http://budtrader.com/arcade/members/drawstream8/activity/3329978/
Nice response in return of this question with firm arguments and describing the whole thing about that.
https://www.jaguarsofficialnflprostore.com/health/uncover-the-pressure-right-behind-a-binaural-beats-obtain/
Hey there! Do you know if they make any plugins to assist with Search Engine Optimization? I’m trying to get my blog to rank for some targeted keywords but I’m not seeing very good success. If you know of any please share. Thanks!
https://about.me/todd.karamian
Very informative blog post.Much thanks again. Will read on…
https://www.arixlash.com/PRODUCTS/Eyelash-Extension_013.html
What is your most noted accomplishment. They may want good listeners rather than good talkers.
https://qr.ae/pyWJy8
Very good post! We will be linking to this great post on our site. Keep up the good writing.
https://tubidy.id
Can you tell us more about this? I’d loveto find out more details.
Well I truly enjoyed reading it. This information provided by you is very practical for correct planning.
https://qr.ae/pyWJy8
I loved your article.Really looking forward to read more.
http://www.wssu.pl/
lumen apartments arbors apartments foothills apartments
Thank you for sharing your thoughts. I truly appreciate your efforts andI am waiting for your further write ups thankyou once again.
https://maps.google.com.lb/url?q=https://www.onlymyhealth.com/prosolution-plus-pills-and-gel-reviews-1689659938
scoliosisI’m curious to find out what blog system you are using?I’m experiencing some small security problems with my latestblog and I’d like to find something more safeguarded.Do you have any suggestions? scoliosis
https://trendingpool.com/male-disney-characters/
tadalafil online with out prescription http://tadalafilise.cyou/# tadalafil order online no prescription
ferma a fuardare testo alışveriş bağımlılığı testi market agent alışveriş bağımlılığı testi a101 aktüel ürünler kataloğu 8 nisan a bimbo meaning
https://owningsprint.blog
Binaural beats meditation is a technique that utilizes rhythmic auditory stimuli to induce a state of relaxation and focus. By presenting slightly different frequencies to each ear, the brain perceives a third “beat” which promotes synchronization of brainwaves, fostering a meditative state. This practice aids in reducing stress and enhancing mental clarity.
https://binauralbeatsprogram.gumroad.com/p/binaural-beats-what-are-they-and-how-do-they-work
Hello, I do think your web site could be having internet browser compatibility problems. Whenever I take a look at your blog in Safari, it looks fine however, if opening in IE, it has some overlapping issues. I simply wanted to give you a quick heads up! Apart from that, wonderful site!
https://judahak574.full-design.com/key-snaptik-tactics-and-techniques-63426087
You are so interesting! I don’t believe I have read through a single thing like this before. So good to discover another person with some genuine thoughts on this topic. Really.. many thanks for starting this up. This site is something that is needed on the internet, someone with some originality.
https://mixbookmark.com/story588358/tubidy-mp3-download-release-the-melodic-market-of-music
Thanks for sharing your thoughts about marijuana cannabis seeds exist.Regards
https://timberdeckmaintenance.com.au/
Hi there, of course this paragraph is in fact fastidious and I havelearned lot of things from it on the topic of blogging.thanks.
http://jelly-life.com/2023/07/27/transforming-areas-the-pros-of-motorized-access/
I’m impressed, I must say. Rarely do I come across a blog that’s both educative and entertaining, and without a doubt, you have hit the nail on the head. The issue is something which too few people are speaking intelligently about. I am very happy that I found this in my hunt for something concerning this.
http://tzdh66.xyz
Really informative blog post.Really looking forward to read more. Fantastic.
https://whey-protein73727.bloginwi.com/54134557/tattoo-aftercare-cream-secrets
Right here is the right site for anyone who really wants to find out about this topic. You know a whole lot its almost tough to argue with you (not that I actually will need to…HaHa). You certainly put a brand new spin on a topic that’s been discussed for decades. Wonderful stuff, just excellent.
https://ask.godotengine.org/user/egyptbadge48
I really enjoy the blog post.Really looking forward to read more. Want more.
https://nutrition05049.blogpayz.com/20976089/the-birla-villament-whitefield-diaries
Cómo ver el golf en los Juegos Olímpicos de 2020: día clave, río en vivo gratis y más
https://www.malagainlive.com
Really enjoyed this blog.Really looking forward to read more. Will read on…
https://nutrition44938.ampblogs.com/the-smart-trick-of-windows-11-activation-key-price-that-nobody-is-discussing-57037442
A round of applause for your blog post. Awesome.
https://coldbrewcoffee18482.like-blogs.com/20328883/everything-about-stenhuset
Awesome article post. Fantastic.
https://www.upupergrow.com/product/advantage.html
Appreciate you sharing, great blog post.Much thanks again. Much obliged.
https://www.creatingway.com/guide-to-designing-sheet-metal-parts/
Good post! We are linking to this great content on our website. Keep up the great writing.
http://tdxclub.com/home.php?mod=space&uid=180176
Thanks again for the article post.Really looking forward to read more. Awesome.
https://www.panda-admission.com
Appreciate you sharing, great article.Thanks Again. Really Great.
https://iptvgithubm3u.com
Thanks for the article.Really looking forward to read more. Keep writing.
https://fishgamego.com
Good day! I could have sworn I’ve been to this blog before but after going through some of the articles I realized it’s new to me. Anyways, I’m certainly happy I came across it and I’ll be book-marking it and checking back often.
https://institutocrecer.edu.co/profile/mp3-juices-vc
Awesome article. Keep writing.
https://www.greenpetcare.com.cn/Pet-Products/Pet-Toilet_015.html
Awesome blog post.Much thanks again. Will read on…
http://www.minoo-cn.com
Some truly interesting information, well written and broadly speaking user genial.
https://www.shiningoven.ie/service/house-cleaning/
An interesting discussion is definitely worth comment. I do think that you ought to publish more about this subject matter, it might not be a taboo subject but generally people don’t talk about such issues. To the next! Best wishes!!
https://rudee11.com/
I value the post. Will read on…
https://telegramim.com
Say, you got a nice article post.Thanks Again. Want more.
https://www.speed-doors.com
Thank you ever so for you blog article.Much thanks again. Much obliged.
https://en.tongwei.com.cn
Very informative blog. Really Great.
https://www.greenpetcare.com.cn/Pet-Products/Pet-Toilet_015.html
I enjoy reading through a post that can make men and women think. Also, many thanks for allowing for me to comment!
https://apps.apple.com/us/app/sunglow-pier-tides/id6456524113
Appreciate you sharing, great blog.Really looking forward to read more. Will read on…
https://telegramim.com
Im grateful for the blog article.Really thank you! Great.
https://gamedesignreviews.org/members/bustongue84/activity/2668/
Hey, thanks for the blog.Thanks Again. Much obliged.
https://4dpick.co/live-casino
I really enjoy the blog post.Really looking forward to read more. Will read on…
https://www.sdtiles.cn/products_detail/Matte_Terrazzo_Series_tiles_for_living_room.html
An interesting discussion is definitely worth comment. I believe that you ought to publish more about this subject, it might not be a taboo matter but generally people do not speak about such issues. To the next! Kind regards!!
http://timeofthedead.com/activity/p/148257/
I cannot thank you enough for the blog.Thanks Again. Awesome.
https://stephenjorvw.fare-blog.com/21022886/everything-about-cd-ielts-centre
wow, awesome blog article.Really thank you! Cool.
https://keeganostrp.free-blogz.com/67934183/the-smart-trick-of-coimbatore-car-rental-that-no-one-is-discussing
Im grateful for the blog.Really thank you! Fantastic.
https://collagen49493.post-blogs.com/42705815/examine-this-report-on-one-day-trip-to-agra
200 mg cialis safe tadalafilise.cyou/#
Really enjoyed this article post.Much thanks again. Will read on…
https://collagen83838.blogolize.com/canadian-visas-no-further-a-mystery-60428253
Hi, I do believe this is an excellent website. I stumbledupon it 😉 I may come back once again since I book marked it. Money and freedom is the greatest way to change, may you be rich and continue to help others.
https://penzu.com/p/e7b3ef3fff845717
Excellent article! We are linking to this great post on our website. Keep up the great writing.
https://mozillabd.science/wiki/Tubidy_Your_Best_Offer_for_Music_and_Video_Search
A round of applause for your article post.Really thank you! Really Great.
https://meatking.hk/
Thank you ever so for you blog article.Thanks Again. Great.
https://whey-protein62727.oblogation.com/23693345/spices-shop-can-be-fun-for-anyone
Thanks-a-mundo for the blog article.Really looking forward to read more. Want more.
https://www.irontechdoll.com
A round of applause for your article. Fantastic.
https://rafaelafikl.idblogmaker.com/22106938/the-best-side-of-satta-matka-dpboss
wow, awesome blog article.Really looking forward to read more. Really Cool.
https://mariorenwe.vblogetin.com/27192461/details-fiction-and-luxury-bus
Im obliged for the article.Really thank you! Much obliged.
http://foxsheets.statfoxsports.com/UserProfile/tabid/57/userId/146332/Default.aspx
wow, awesome blog article.Thanks Again. Really Cool.
https://lorenzoyumew.theisblog.com/22473906/helping-the-others-realize-the-advantages-of-navelpiercing
Thanks for sharing, this is a fantastic article.Really thank you! Cool.
https://shengbenzhejiangchina.com/
I really liked your blog.Really thank you! Great.
https://www.josenart.com/products/modern-minimalist-clear-glass-lampshade-wall-light
Major thankies for the blog.Really thank you! Much obliged.
https://www.hdconnectorstore.com/productdetail/2886.html
wow, awesome blog post.Really looking forward to read more. Keep writing.
https://www.rntico.com/k/productDetails.php?id=99
I loved your article post.Much thanks again. Fantastic.
https://bonito-packaging.com/
Thanks so much for the article.Really looking forward to read more. Will read on…
https://pre-workout72716.loginblogin.com/26601135/char-dham-yatra-package-by-bus-can-be-fun-for-anyone
I am so grateful for your post.Thanks Again. Fantastic.
http://www.lftdzd.com/en/scg/504.html
Great blog post.Really looking forward to read more. Really Cool.
https://www.fjstat.com/Beer-Brewing-refractometer.html
wow, awesome blog.Thanks Again. Really Cool.
https://www.fastech-pcb.com/en/news_show/7ih8brhokbcwo/Process-Flow-Diagram-of-Aluminum-PCB
Appreciate you sharing, great blog post. Keep writing.
https://www.epicmilling.com
I appreciate you sharing this blog post.Really thank you! Really Cool.
https://wheyprotein27261.dailyhitblog.com/27713886/product-key-for-windows-11-fundamentals-explained
Looking forward to reading more. Great post.Much thanks again. Great.
https://messiahrwadg.smblogsites.com/22573181/5-tips-about-carbon-offset-through-methane-avoidance-method-you-can-use-today
A round of applause for your blog article. Cool.
https://connerxxtog.jts-blog.com/22874980/the-smart-trick-of-hop-over-to-this-web-site-that-nobody-is-discussing
Thanks for the blog. Awesome.
https://nutrition49504.webbuzzfeed.com/23150439/indicators-on-my-review-here-you-should-know
I cannot thank you enough for the post.Really thank you! Really Great.
https://wholesalenutrition94838.thelateblog.com/23133048/5-easy-facts-about-mathura-vrindavan-haridwar-tour-packages-described
Thanks again for the article post. Keep writing.
https://www.yqwakan.com/product_4339_HessmannBMWConnectorPlugOxygenSensorConnector805122541.html
Thanks again for the article post.Really thank you! Awesome.
https://rotontek.com/
I loved your blog. Want more.
https://honeylovedoll.com/
I really like and appreciate your article.Much thanks again. Will read on…
https://www.jcanatomy.com/en/product_show/fuvnk4vqzgg08/88cm–Human-Skeleton-Model—Standard
I truly appreciate this blog post.Really thank you! Want more.
https://okmusi.com/get-music
Im grateful for the blog post.Really looking forward to read more. Fantastic.
https://www.bityard.com
I truly appreciate this blog article.Really thank you! Really Cool.
https://7tdmjpf5yuwu.jobboard.io/employers/2482512-aspireapplianceservices
Great, thanks for sharing this blog post. Keep writing.
https://www.fjstat.com/
Great, thanks for sharing this blog article. Great.
http://www.fno.org.br/cro-ms-o-conselho-diretoria-legislacoes-profissionais-cd-tpd-tsb-asb-apd-cfo-contesta-decisao-de-que-somente-medicos-podem-exercer-a-acupuntura/#comment-3079943
Thank you ever so for you post.
https://janitoraichat.com/
Thanks so much for the blog.Much thanks again. Will read on…
https://apps.apple.com/us/app/hmall/id6465174760
I think this is a real great blog article.Really looking forward to read more. Want more.
https://josuevkxk43109.evawiki.com/8468614/simplify_school_fee_management_with_school_fee_software_a_comprehensive_guide
Great, thanks for sharing this blog article.Much thanks again. Fantastic.
https://sergioftgt76532.vigilwiki.com/5806229/future_choice_hospitality_tips
Looking forward to reading more. Great article.Really looking forward to read more. Fantastic.
http://www.fossil.ipt.pw/News/business-supply/
Very neat blog article.Much thanks again. Want more.
https://kapills.net/man-erection-not-hard/
This is one awesome blog article.Really thank you! Really Great.
http://www.alistsites.com/Business/
Thanks for the blog article.Much thanks again.
https://www.kubetworld.com
Major thanks for the post.Really thank you! Really Great.
https://moreabouttheauthor72614.vidublog.com/23543437/detailed-notes-on-kids-dentist-near-me
This is one awesome article. Really Cool.
https://arcade.stanford.edu/users/greihpad75cr
Very informative blog article.Much thanks again. Cool.
https://fouadmods.net/gb-whatsapp/
Thank you ever so for you post.Thanks Again. Will read on…
https://inzvod.com
I appreciate you sharing this blog.Much thanks again. Want more.
http://www.addlistdirect.com/en.php?advert/advertise_yourself/3856985.html
Im thankful for the post.Really thank you!
http://www.activewin.com/user.asp?Action=Read&UserIndex=4243772
Major thankies for the post.Really looking forward to read more. Much obliged.
https://net7722127.bloggerswise.com/29788636/fresh-vegetables-home-delivery-can-be-fun-for-anyone
Major thankies for the blog post.Thanks Again. Cool.
https://sergiomu6kq.activablog.com/23893914/not-known-factual-statements-about-kudremukha-trekking
Major thanks for the blog post.Much thanks again. Keep writing.
https://mbti55320.ka-blogs.com/76991090/indicators-on-residential-architects-in-hyderabad-you-should-know
Great article.Much thanks again. Great.
https://mbti40467.is-blog.com/29544350/the-single-best-strategy-to-use-for-cab-in-chennai
Thanks again for the blog post.Really looking forward to read more. Really Cool.
https://www.uniquehairextension.com/product/u-tip.html
I really enjoy the blog post.Really thank you! Keep writing.
https://dallasolhhx.theblogfairy.com/24149505/top-guidelines-of-pawna-lake-camping-pune
A round of applause for your blog post.Thanks Again. Want more.
https://mbti89763.bloggadores.com/24130808/the-best-side-of-termite-solutions-pest-control
I really enjoy the blog. Much obliged.
https://public.sitejot.com/shoeresidenc.html
I really enjoy the article.Thanks Again. Great.
https://simplecodingstudio.com/service/
На онлайн-сайте https://amurplanet.ru/, посвященном женской тематике, вы сможете обнаружить огромному количеству интересных материалов. Мы постоянно обновляем полезные рекомендации в разнообразных сферах, таких как здоровье и множество других областей.
Ознакомьтесь всю тайны женской красоты и физического и душевного благополучия, следите за последними трендами в мире моды и стиля. Мы предлагаем статьи о психологии и межличностных отношениях, семейных вопросах, компании и карьере, собственном росте и развитии. Вы также обнаружите советы по готовке, рецепты блюд, советы по воспитанию и множество других полезных материалов.
Наши материалы помогут сформировать уютный дом, ознакомиться с загородном хозяйстве, позаботиться о своем внешнем виде, поддерживать свой здоровьем и активным образом жизни. Мы также предоставляем информацию о здоровом образе жизни, финансовой грамотности и многом другом.
Присоединьтесь к обществу наших читателей среди женщин на AmurPlanet.ru – и смотрите полезную информацию каждый день. Не упустите возможность подписаться на наши новости, чтобы быть в курсе всех актуальных событий. Посетите наш сайт и получите доступ к миру женской тематики во полной мере!
Не забудьте добавить сайт https://amurplanet.ru/ в закладки!
Definitely, what a great blog and revealing posts, I definitely will bookmark your site. Best Regards!
My website: голые пьяные
This is one awesome post.Really looking forward to read more. Fantastic.
https://bestwondercloset.com/collections/replica-adidas-yeezy/
Семейные викторины: Раскройте веселье в вашем отношении (https://testy-pro-lyubov-i-semyu.blogspot.com/2023/12/blog-post.html) – это интерактивные опросы, созданные с целью доставлять удовольствие и развлечение. Они поднимают перед участниками разные вопросы и задачи, которые часто связаны с захватывающими темами, личными предпочтениями или веселыми событиями. Основная цель таких тестов – предоставить пользователю возможность получить удовольствие, проверить свои знания или узнать что-то новое о себе или мире вокруг них. Такие тесты широко известны в онлайн-среде и социальных медиа, где они стали признанными формами интерактивного развлечения и делиться информацией.
Не забудьте добавить наш сайт в закладки: https://testy-pro-lyubov-i-semyu.blogspot.com/2023/12/blog-post.html
Thanks-a-mundo for the blog. Great.
https://fouadmods.net/gb-whatsapp/
Great, thanks for sharing this post.Really looking forward to read more. Much obliged.
https://www.favcomic.com/picture
Проникновенные тесты для женщин: Исследуйте скрытую силу (https://zhenskie-testy.blogspot.com/2023/12/blog-post.html) – это привлекательные опросы, предназначенные для изучения женской сущности. Они задают перед участницами разнообразные вопросы для саморефлексии, часто связанные с гармонии в жизни. Основная задача этих тестов – дать перспективу приятного времяпрепровождения, а также способствовать разгадыванию эмоциональные грани. Эти тесты получили признание среди женской аудитории онлайн как метод самопознания.
Не забудьте сохранить ссылку на наш ресурс: https://zhenskie-testy.blogspot.com/2023/12/blog-post.html
I really liked your blog article.Thanks Again. Really Great.
https://titussjory.blog2freedom.com/24804074/the-2-minute-rule-for-builder-in-nagpur
Im thankful for the blog article.Much thanks again. Really Great.
https://johnnylznvf.blogoxo.com/24868251/the-smart-trick-of-construction-company-in-nagpur-that-no-one-is-discussing
Thanks for the blog.Much thanks again. Fantastic.
https://archerzprzx.link4blogs.com/46937300/an-unbiased-view-of-current-technology-news
Thank you ever so for you post. Want more.
https://trekking-near-bangalore80146.thekatyblog.com/24471193/the-ultimate-guide-to-trekking-near-bangalore
Very good blog article.Really thank you! Awesome.
https://juliusfsfs65421.blogkoo.com/down-under-dreams-unveiling-the-wonders-of-australia-for-tourists-44357192
A round of applause for your blog post. Great.
https://homeshiftingservices68056.gynoblog.com/24656000/new-step-by-step-map-for-home-shifting-services
wow, awesome article post.Much thanks again. Fantastic.
https://m.casinoplus.net.ph/
Looking forward to reading more. Great post.Really thank you! Cool.
https://dungeonborne.com
Great post. Much obliged.
https://liveplayclub.com/
Hey, thanks for the article post.Thanks Again.
https://casinoplus.net.ph/
Great, thanks for sharing this article post. Will read on…
https://www.3chlorine.com/
Im obliged for the blog post.Really thank you! Really Great.
https://blog.huddles.app/
Appreciate you sharing, great blog post.
https://crushon.ai/trends/ai_chat
Thanks for the post.Thanks Again. Really Cool.
https://www.algaecidetechnologies.com/
Thank you for your article.Thanks Again. Much obliged.
https://aspireapplianceservices.in/repair-service-centre-jyothi-nagar-mysore/
Major thankies for the blog.Really looking forward to read more. Will read on…
https://www.dolphmicrowave.com
A round of applause for your post.Really looking forward to read more. Fantastic.
https://www.rs-fastener.com
Im obliged for the blog post. Great.
https://www.lianindustrial.com
I appreciate you sharing this article post.Really thank you! Really Cool.
https://gunnertkan54321.wikifiltraciones.com/2809328/rishikesh_camping_package_tips
Thank you ever so for you article. Keep writing.
https://free-chatgpt.ai/
Really appreciate you sharing this article post.Thanks Again.
http://ezproxy.cityu.edu.hk/login?url=https://remoteiot.com/
I loved your blog post.Thanks Again. Really Cool.
https://nationaldppcsc.cdc.gov/s/profile/0053d0000049lPpAAI
Thanks for the complete information. You helped me.
Советую прочитать эту статью про афоризмы и статусы https://frag-x.ru/aforizmy-i-sovremennye-vyzovy-primenenie-mudryx-slov-v-sovremennom-mire/.
Также не забудьте добавить сайт в закладки: https://frag-x.ru/aforizmy-i-sovremennye-vyzovy-primenenie-mudryx-slov-v-sovremennom-mire/
Советую прочитать эту статью про афоризмы и статусы http://www.cydak.ru/digest/2009.html.
Также не забудьте добавить сайт в закладки: http://www.cydak.ru/digest/2009.html
Consider the intersection of personal and societal ethics and the challenges that arise when conflicting values come into play.
Советуем посетить сайт про астрологию https://astrologiyanauka.blogspot.com/
Также не забудьте добавить сайт в закладки: https://astrologiyanauka.blogspot.com/
Советуем посетить сайт про диких животных https://telegra.ph/Tainstvennyj-mir-dikih-zhivotnyh-putevoditel-po-neizvedannym-tropam-prirody-12-23
Также не забудьте добавить сайт в закладки: https://telegra.ph/Tainstvennyj-mir-dikih-zhivotnyh-putevoditel-po-neizvedannym-tropam-prirody-12-23
Really appreciate you sharing this article post. Awesome.
https://daxtromn-power.com/products/special-offer-daxtromn-power-6.2kw-solar-inverter-24vdc-48vdc-hybrid-mppt-6200w-pure-sine-wave-hybrid-charge-controller-120a-off-grid-on-grid
Thank you ever so for you article post.Really thank you! Really Great.
https://www.us-machines.com/
Appreciate you sharing, great post. Cool.
https://daxtromn-power.com/products/special-offer-daxtromn-power-mppt-4.2kw-hybrid-solar-inverter-24vdc-batteryless-working-pv-input-90-450v-grid-tie-hybrid-solar-inverter-48v-220v-120-450vdc-140a-mppt-solar-controller-dual-ouput-photovoltaic-inverter
Very informative blog.Much thanks again. Really Great.
https://daxtromn-power.com/products/special-offer-daxtromn-power-6.2kw-solar-inverter-24vdc-48vdc-hybrid-mppt-6200w-pure-sine-wave-hybrid-charge-controller-120a-off-grid-on-grid
I am so grateful for your post.Thanks Again. Cool.
https://www.us-machines.com/
I value the blog post.Much thanks again.
https://bingoplus.net.ph
Very neat blog. Keep writing.
https://crushon.ai/trends/nsfw_ai
Советуем посетить сайт про авто https://arenda-legkovyh-pricepov.ru/
Также не забудьте добавить сайт в закладки: https://arenda-legkovyh-pricepov.ru/
Thanks-a-mundo for the blog post.
https://free-chatgpt.ai/
Im grateful for the blog article.Really thank you! Really Cool.
https://tangtoutiaosite.com/
I really enjoy the blog article.Really thank you! Much obliged.
https://www.us-machines.com/
Thanks-a-mundo for the blog article.Thanks Again. Want more.
https://www.koluse.com/
Very neat post.Thanks Again. Will read on…
https://undressai.cc
Fantastic article post. Will read on…
https://outingtribe.com
Thanks-a-mundo for the blog. Much obliged.
https://www.lunaproxy.com
Thanks a lot for the blog article. Will read on…
https://www.panmin.com
Советуем посетить сайт про птиц https://telegra.ph/Udivitelnyj-mir-ptic-12-23
Также не забудьте добавить сайт в закладки: https://telegra.ph/Udivitelnyj-mir-ptic-12-23
Советуем посетить сайт про грызунов https://telegra.ph/Mir-gryzunov-interesnye-fakty-i-vidy-melkih-zhivotnyh-na-yuge-Rossii-12-23
Также не забудьте добавить сайт в закладки: https://telegra.ph/Mir-gryzunov-interesnye-fakty-i-vidy-melkih-zhivotnyh-na-yuge-Rossii-12-23
Appreciate you sharing, great blog post.Much thanks again. Fantastic.
https://www.hospital-xg.com
Awesome blog article.Thanks Again. Cool.
https://casinoplus.net.ph
Thanks again for the blog post.Really thank you! Will read on…
https://www.birthdayblooms.com/showcase?page=1
Major thanks for the article. Great.
https://overseastudentloan.com
Советуем посетить сайт про рептилий https://telegra.ph/Reptilii-Udivitelnyj-mir-cheshujchatyh-12-23
Также не забудьте добавить сайт в закладки: https://telegra.ph/Reptilii-Udivitelnyj-mir-cheshujchatyh-12-23
Thank you for your article post.Much thanks again.
https://cncmachining-custom.com
Советуем посетить сайт про домашних животных https://telegra.ph/Kak-uhazhivat-za-domashnimi-zhivotnymi-sovety-i-rekomendacii-12-23
Также не забудьте добавить сайт в закладки: https://telegra.ph/Kak-uhazhivat-za-domashnimi-zhivotnymi-sovety-i-rekomendacii-12-23
wow, awesome post.Really looking forward to read more. Really Cool.
https://crushon.ai/
Советуем посетить сайт о кино https://kinokabra.ru/
Также не забудьте добавить сайт в закладки: https://kinokabra.ru/
Fantastic blog post.Really looking forward to read more. Much obliged.
https://crushon.ai/
wow, awesome blog.Really looking forward to read more. Really Great.
https://gpt-free.ai/
Very good article post. Will read on…
https://aichatting.ai/
Советуем посетить сайт конструктора кухни онлайн https://40-ka.ru/news/page/konstruktor-kuhni-online-besplatno
Также не забудьте добавить сайт в закладки: https://40-ka.ru/news/page/konstruktor-kuhni-online-besplatno
Советуем посетить сайт, чтобы прочитать о цветах в картинах https://daibob.ru/himiya-tsveta-kak-nauka-ozhivlyaet-iskusstvo/
Также не забудьте добавить сайт в закладки: https://daibob.ru/himiya-tsveta-kak-nauka-ozhivlyaet-iskusstvo/
Im thankful for the post.Much thanks again. Really Great.
https://crushon.ai/character/19133f53-77e1-4a1f-a44d-9d6fbb5d62d3/chat
This is one awesome post.Much thanks again. Want more.
https://cncmachining-custom.com
Советуем посетить сайт https://allkigurumi.ru/products
Также не забудьте добавить сайт в закладки: https://allkigurumi.ru/products
Thanks a lot for the blog article.Really looking forward to read more. Cool.
https://creatiodesign.net
Thanks so much for the article.Really looking forward to read more. Really Cool.
https://www.wikitrade.com/en/news-forex/1.html
Very good blog post.Much thanks again.
https://www.findalocallawyer.com
Советуем посетить сайт https://a-so.ru/
Также не забудьте добавить сайт в закладки: https://a-so.ru/
Thanks a lot for the blog.Thanks Again. Will read on…
https://www.kubet.fyi/
Советуем посетить сайт https://togliatti24.ru/svadebnye-tosty-chto-pozhelat-i-kakim-dolzhen-byt-tost/
Также не забудьте добавить сайт в закладки: https://togliatti24.ru/svadebnye-tosty-chto-pozhelat-i-kakim-dolzhen-byt-tost/
Say, you got a nice blog.Thanks Again. Really Cool.
https://bonitocase.com/
Really enjoyed this article post.Really looking forward to read more. Keep writing.
https://www.oneuedu.com/visa
Советуем посетить сайт http://www.obzh.ru/mix/samye-smeshnye-sluchai-na-bolshix-press-konferenciyax-vladimira-putina.html
Также не забудьте добавить сайт в закладки: http://www.obzh.ru/mix/samye-smeshnye-sluchai-na-bolshix-press-konferenciyax-vladimira-putina.html
Советуем посетить сайт https://style.sq.com.ua/2021/10/25/kakim-dolzhen-byt-tost-na-svadbu-kak-vybrat/
Также не забудьте добавить сайт в закладки: https://style.sq.com.ua/2021/10/25/kakim-dolzhen-byt-tost-na-svadbu-kak-vybrat/
Советуем посетить сайт https://samaraonline24.ru/narodnyje-primjety-o-pogodje
Также не забудьте добавить сайт в закладки: https://samaraonline24.ru/narodnyje-primjety-o-pogodje
Советуем посетить сайт https://invest.kr.ua/igor-mamenko-i-ego-zhena.html
Также не забудьте добавить сайт в закладки: https://invest.kr.ua/igor-mamenko-i-ego-zhena.html
Советуем посетить сайт https://pfo.volga.news/594544/article/obrazy-russkogo-nemca-i-amerikanca-v-anekdotah.html
Также не забудьте добавить сайт в закладки: https://pfo.volga.news/594544/article/obrazy-russkogo-nemca-i-amerikanca-v-anekdotah.html
Советуем посетить сайт https://podveski-remont.ru/
Также не забудьте добавить сайт в закладки: https://podveski-remont.ru/
Советуем посетить сайт https://mari-eparhia.ru/useful/?id=12206
Также не забудьте добавить сайт в закладки: https://mari-eparhia.ru/useful/?id=12206
Great blog.Thanks Again. Really Great.
https://www.oneuedu.com/visa
We recommend visiting the website https://etc.bdir.in/dialogue/movies/A
Also, don’t forget to add the site to your bookmarks: https://etc.bdir.in/dialogue/movies/A
Советуем посетить сайт https://back2russia.net/index.php?/topic/2622-rvp-v-permi/
Также не забудьте добавить сайт в закладки: https://back2russia.net/index.php?/topic/2622-rvp-v-permi/
Great, thanks for sharing this post.Much thanks again. Really Great.
https://casinoplus.net.ph/
Советуем посетить сайт https://mama.ru/forums/theme/kredity/page/22/
Также не забудьте добавить сайт в закладки: https://mama.ru/forums/theme/kredity/page/22/
Советуем посетить сайт https://pravchelny.ru/useful/?id=1266
Также не забудьте добавить сайт в закладки: https://pravchelny.ru/useful/?id=1266
Советуем посетить сайт https://ancientcivs.ru/
Также не забудьте добавить сайт в закладки: https://ancientcivs.ru/
Really appreciate you sharing this blog post.Really looking forward to read more. Much obliged.
https://crushon.ai/
This is one awesome blog post.Much thanks again. Fantastic.
https://crushon.ai/
Very informative article. Cool.
https://crushon.ai/
Советуем посетить сайт https://amurplanet.ru/
Также не забудьте добавить сайт в закладки: https://amurplanet.ru/
Советуем посетить сайт http://yury-reshetnikov.elegos.ru
Также не забудьте добавить сайт в закладки: http://yury-reshetnikov.elegos.ru
Enjoyed every bit of your article post. Fantastic.
https://faceswapapp.ai/
Really informative blog.Really looking forward to read more. Really Great.
https://finewatchcare.com/products/fwc-for-rolex-226659-0002-watch-protection-film?_pos=1&_sid=4daead44a&_ss=r&variant=44666503463199
Советуем посетить сайт http://oleg-pogudin.elegos.ru/
Также не забудьте добавить сайт в закладки: http://oleg-pogudin.elegos.ru/
Say, you got a nice blog post.Thanks Again. Will read on…
https://faceswapapp.ai/
Советуем посетить сайт https://krasilovdreams.borda.ru/?1-11-0-00000014-000-30-0-1266268332
Также не забудьте добавить сайт в закладки: https://krasilovdreams.borda.ru/?1-11-0-00000014-000-30-0-1266268332
Say, you got a nice article.Really looking forward to read more. Cool.
https://zhongli998.com
Im obliged for the article post.Thanks Again. Cool.
https://callmeimei.com
Советуем посетить сайт https://anekdotitut.ru/kak-promokody-pomogayut-sekonomit-na-onlajn-pokupkah/
Также не забудьте добавить сайт в закладки: https://anekdotitut.ru/kak-promokody-pomogayut-sekonomit-na-onlajn-pokupkah/
wow, awesome article. Much obliged.
https://callmeimei.com
Major thanks for the article post.Much thanks again. Keep writing.
https://www.temporaryfencesales.ca
Советуем посетить сайт https://antipushkin.ru/preimushhestva-ispolzovaniya-promokodov-pri-onlajn-pokupkah/
Также не забудьте добавить сайт в закладки: https://antipushkin.ru/preimushhestva-ispolzovaniya-promokodov-pri-onlajn-pokupkah/
Советуем посетить сайт https://fotonons.ru/preimushhestva-ispolzovaniya-promokodov-pri-onlajn-pokupkah/
Также не забудьте добавить сайт в закладки: https://fotonons.ru/preimushhestva-ispolzovaniya-promokodov-pri-onlajn-pokupkah/
Советуем посетить сайт https://kinokabra.ru/promokody-glavnye-roli-v-mire-mody-i-kino/
Также не забудьте добавить сайт в закладки: https://kinokabra.ru/promokody-glavnye-roli-v-mire-mody-i-kino/
This is one awesome blog article.Thanks Again. Keep writing.
https://www.wiremeshfence.com
Советуем посетить сайт https://mymeizuclub.ru/polezno/ekonomiya-v-seti-kak-promokody-delayut-vashi-onlajn-pokupki-bolee-vygodnymi
Также не забудьте добавить сайт в закладки: https://mymeizuclub.ru/polezno/ekonomiya-v-seti-kak-promokody-delayut-vashi-onlajn-pokupki-bolee-vygodnymi
Appreciate you sharing, great blog article.Much thanks again. Cool.
https://www.zoomesh.us
Советуем посетить сайт https://anekdotitut.ru/srochnyj-vykup-avto-v-saratove-kak-eto-proishodit-i-kakie-preimushhestva/
Также не забудьте добавить сайт в закладки: https://anekdotitut.ru/srochnyj-vykup-avto-v-saratove-kak-eto-proishodit-i-kakie-preimushhestva/
I really enjoy the post.Really looking forward to read more.
https://animegenerator.ai/
Советуем посетить сайт https://anekdotitut.ru/pochemu-vazhna-konsultatsiya-surdologa-dlya-detej-s-problemami-sluha/
Также не забудьте добавить сайт в закладки: https://anekdotitut.ru/pochemu-vazhna-konsultatsiya-surdologa-dlya-detej-s-problemami-sluha/
Советуем посетить сайт https://zaslushaem.ru/ekonomiya-v-seti-preimushhestva-promokodov-pri-onlajn-pokupkah
Также не забудьте добавить сайт в закладки: https://zaslushaem.ru/ekonomiya-v-seti-preimushhestva-promokodov-pri-onlajn-pokupkah
Wow, great article.Really looking forward to read more. Really Cool.
https://fouadmods.net/
Советуем посетить сайт https://zhiloy-komplex.ru/promokody-vash-nadezhnyj-sputnik-v-mire-onlajn-shopinga/
Также не забудьте добавить сайт в закладки: https://zhiloy-komplex.ru/promokody-vash-nadezhnyj-sputnik-v-mire-onlajn-shopinga/
Советуем посетить сайт https://artcet.ru/mastera-ekonomii-promokody-kak-klyuch-k-bolee-vygodnym-onlajn-pokupkam/
Также не забудьте добавить сайт в закладки: https://artcet.ru/mastera-ekonomii-promokody-kak-klyuch-k-bolee-vygodnym-onlajn-pokupkam/
Wow, great article post. Cool.
https://nsfwgenerator.ai/
Советуем посетить сайт https://admlihoslavl.ru/promokody-sekretnyj-instrument-ekonomii-v-mire-onlajn-shopinga/
Также не забудьте добавить сайт в закладки: https://admlihoslavl.ru/promokody-sekretnyj-instrument-ekonomii-v-mire-onlajn-shopinga/
Советуем посетить сайт https://elegos.ru/promokody-vash-put-k-ekonomii-i-udovolstviyu-v-mire-onlajn-shopinga/
Также не забудьте добавить сайт в закладки: https://elegos.ru/promokody-vash-put-k-ekonomii-i-udovolstviyu-v-mire-onlajn-shopinga/
Enjoyed every bit of your blog article.Much thanks again. Awesome.
https://devinai.ai
Советуем посетить сайт https://avtomaxi22.ru/
Также не забудьте добавить сайт в закладки: https://avtomaxi22.ru/
Советуем посетить сайт https://med-like.ru/
Также не забудьте добавить сайт в закладки: https://med-like.ru/
Thanks for the post.Really looking forward to read more. Much obliged.
https://www.yinraohair.com/cosplay/shop-by-color/silver
Советуем посетить сайт https://metal82.ru/
Также не забудьте добавить сайт в закладки: https://metal82.ru/
Советуем посетить сайт https://kryshi-remont.ru/
Также не забудьте добавить сайт в закладки: https://kryshi-remont.ru/
I really enjoy the blog.Much thanks again. Cool.
https://www.yinraohair.com/wigs/shop-by-colour/highlight-wig
Major thankies for the blog article. Really Cool.
https://www.isin-wheel.com/post/top-20-electric-scooter-manufacturers-in-the-world/
Советуем посетить сайт https://balkonnaya-dver.ru/
Также не забудьте добавить сайт в закладки: https://balkonnaya-dver.ru/
Looking forward to reading more. Great blog article. Much obliged.
https://bestanimationacademyinraj54134.jiliblog.com/83197114/everything-about-best-animation-academy-in-rajasthan
Very informative article post.Really thank you! Will read on…
https://www.onthebanks.com/users/vastuconsultantnearme
I really like and appreciate your article.Really looking forward to read more. Awesome.
https://rivergwna09976.thecomputerwiki.com/4671566/occupational_english_test
Great post.Really looking forward to read more. Want more.
https://juliusixkx87643.uzblog.net/pvc-o-pipe-manufacturers-in-india-39711923
Say, you got a nice article.Really looking forward to read more. Awesome.
https://lincoln6g32sfr6.bloguerosa.com/25177791/canada-118-105-115-97-requirements
Major thanks for the post.Really thank you! Awesome.
https://donovansvzsc.blogoscience.com/31777509/little-known-facts-about-indian-masala-company
I love making hottest sex chat for free, please and enjoy . wanna have fun with me
Советуем посетить сайт https://admlihoslavl.ru/
Также не забудьте добавить сайт в закладки: https://admlihoslavl.ru/
Major thanks for the article.Really looking forward to read more.
https://dantedpcn42197.blogproducer.com/31350625/the-advantage-of-market-trading-course
Советуем посетить сайт https://elegos.ru/
Также не забудьте добавить сайт в закладки: https://elegos.ru/
Appreciate you sharing, great article post.Really looking forward to read more. Really Great.
https://sethvjxk32198.eqnextwiki.com/4078332/home_appliances_products
I truly appreciate this blog.Really thank you! Will read on…
https://mydirectorys.com/listings12674413/helping-the-others-realize-the-advantages-of-satta-king-result
physician cv writing service best paper writing service
https://suba.me/
Major thanks for the blog.Really thank you! Great.
https://hectorrvbyw.wikidirective.com/6594307/the_smart_trick_of_industrial_flanges_manufacturer_that_nobody_is_discussing
I really enjoy the post.Really thank you! Great.
https://real-directory.com/listings12676824/examine-this-report-on-canada-pr-visa-process
Appreciate you sharing, great article.Much thanks again. Awesome.
https://trentonkzna09865.wonderkingwiki.com/539942/the_benefit_of_custom_plastic_parts
Советуем посетить сайт https://100sm.ru/
Также не забудьте добавить сайт в закладки: https://100sm.ru/
Im thankful for the article post.Much thanks again. Fantastic.
https://crushon.ai/
Thanks a lot for the blog.Really looking forward to read more. Awesome.
https://nsfws.ai/
Советуем посетить сайт https://club-columb.ru/
Также не забудьте добавить сайт в закладки: https://club-columb.ru/
Im grateful for the post.Really looking forward to read more. Fantastic.
https://www.laifentech.com/
I loved your blog post.Much thanks again. Want more.
https://www.aidevin.ai
Really enjoyed this blog article.Much thanks again. Really Cool.
https://www.chaguanersite.com/
I think this is a real great blog article. Fantastic.
https://www.helmsmancrystal.com/
Thanks a lot for the blog post.Really thank you! Cool.
https://www.orangenews.hk
Советуем посетить сайт https://softnewsportal.ru/
Также не забудьте добавить сайт в закладки: https://softnewsportal.ru/
This is one awesome post. Much obliged.
https://inspro2.com/
Thanks for the blog post.Thanks Again. Keep writing.
https://inspro2.com/
Советуем посетить сайт https://gulliverauto.ru/
Также не забудьте добавить сайт в закладки: https://gulliverauto.ru/
A round of applause for your blog article.Much thanks again. Fantastic.
https://talkietalkie.ai/
Советуем посетить сайт https://doutuapse.ru/
Также не забудьте добавить сайт в закладки: https://doutuapse.ru/
Советуем посетить сайт https://russkiy-spaniel.ru/
Также не забудьте добавить сайт в закладки: https://russkiy-spaniel.ru/
Very good blog.Much thanks again. Really Great.
https://atop-education.degree
I really like and appreciate your article.Really thank you!
https://crushon.ai/
Советуем посетить сайт https://stroydvor89.ru/
Также не забудьте добавить сайт в закладки: https://stroydvor89.ru/
Советуем посетить сайт https://magic-magnit.ru//
Также не забудьте добавить сайт в закладки: https://magic-magnit.ru/
We recommend visiting the website https://mywebsitegirl.com/.
Also, don’t forget to bookmark the site: https://mywebsitegirl.com/
I think this is a real great article post. Will read on…
https://nsfws.ai/
Looking forward to reading more. Great article. Will read on…
https://crushon.ai/
We recommend visiting the website https://villa-sunsetlady.com/.
Also, don’t forget to bookmark the site: https://villa-sunsetlady.com/
We recommend visiting the website https://realskinbeauty.com/.
Also, don’t forget to bookmark the site: https://realskinbeauty.com/
We recommend visiting the website https://talksoffashion.com/.
Also, don’t forget to bookmark the site: https://talksoffashion.com/
I really like and appreciate your blog article.Really looking forward to read more. Cool.
https://www.kjin-stationery.com/products.html
We recommend visiting the website https://skinsoulbeauty.com/.
Also, don’t forget to bookmark the site: https://skinsoulbeauty.com/
I really like and appreciate your blog.Really looking forward to read more. Great.
https://summerseasiren.com/collections/period-underwear
We recommend visiting the website https://powerofquotes12.blogspot.com/2024/03/the-power-of-quotes-inspiration-for.html.
Also, don’t forget to bookmark the site: https://powerofquotes12.blogspot.com/2024/03/the-power-of-quotes-inspiration-for.html
We recommend visiting the website https://quotes-status1.blogspot.com/2024/03/the-power-of-quotes-inspiration-for.html.
Also, don’t forget to bookmark the site: https://quotes-status1.blogspot.com/2024/03/the-power-of-quotes-inspiration-for.html
Say, you got a nice blog article.Thanks Again. Fantastic.
https://felixbpdr65421.wikienlightenment.com/6759948/revolutionize_your_99_114_121_112_116_111_trading_with_the_best_copy_trading_bots
We recommend visiting the website https://quotablemoments1.blogspot.com/2024/03/embracing-lifes-wisdom-how-quotes-can.html.
Also, don’t forget to bookmark the site: [url=https://quotablemoments1.blogspot.com/2024/03/embracing-lifes-wisdom-how-quotes-can.html]https://quotablemoments1.blogspot.com/2024/03/embracing-lifes-wisdom-how-quotes-can.html[/url]
I value the post.Much thanks again. Much obliged.
https://creatine49472.mdkblog.com/31245658/5-simple-techniques-for-mitchell-fishing-rod
We recommend visiting the website https://wisdominwords123.blogspot.com/2024/03/unlocking-lifes-treasures-timeless.html.
Also, don’t forget to bookmark the site: https://wisdominwords123.blogspot.com/2024/03/unlocking-lifes-treasures-timeless.html
Say, you got a nice blog post. Really Great.
https://www.hogshaven.com/users/BestDuctCleaningServices
We recommend visiting the website https://wisdominwords123.blogspot.com/2024/03/echoes-of-wisdom.html.
Also, don’t forget to bookmark the site: https://wisdominwords123.blogspot.com/2024/03/echoes-of-wisdom.html
Thanks for the article post. Really Great.
https://beauqiap77655.mysticwiki.com/538661/what_is_osha_courses_online
We recommend visiting the website https://telegra.ph/The-Radiance-of-Positivity-Exploring-the-Power-of-Positive-Quotes-03-31.
Also, don’t forget to bookmark the site: https://telegra.ph/The-Radiance-of-Positivity-Exploring-the-Power-of-Positive-Quotes-03-31
Awesome blog.Really looking forward to read more. Much obliged.
https://ericktjym54220.wikicorrespondence.com/3397704/your_gateway_to_best_nift_coaching_classes_in_delhi
A round of applause for your blog article.Thanks Again. Great.
https://wheyprotein72727.blog5star.com/26074771/experience-the-ultimate-romance-with-maldives-honeymoon-packages
We recommend visiting the website https://telegra.ph/The-Craft-of-Achievement-Finding-Inspiration-in-Work-Quotes-03-31.
Also, don’t forget to bookmark the site: https://telegra.ph/The-Craft-of-Achievement-Finding-Inspiration-in-Work-Quotes-03-31
We recommend visiting the website https://telegra.ph/Sculpting-Success-How-Quotes-Can-Shape-Our-Aspirations-03-31.
Also, don’t forget to bookmark the site: https://telegra.ph/Sculpting-Success-How-Quotes-Can-Shape-Our-Aspirations-03-31
I really liked your blog post. Awesome.
https://https-jun88online-co26789.blogsmine.com/25107849/rumored-buzz-on-nebosh-general-certificate-courses
We recommend visiting the website https://telegra.ph/The-Bonds-We-Cherish-Celebrating-Connections-Through-Friendship-Quotes-03-31.
Also, don’t forget to bookmark the site: https://telegra.ph/The-Bonds-We-Cherish-Celebrating-Connections-Through-Friendship-Quotes-03-31
Wow, great post.Thanks Again. Cool.
https://mbti59912.blogitright.com/24875693/the-2-minute-rule-for-best-iema-courses-online
We recommend visiting the website https://telegra.ph/Lifes-Mosaic-Understanding-the-Big-Picture-Through-Quotes-03-31.
Also, don’t forget to bookmark the site: https://telegra.ph/Lifes-Mosaic-Understanding-the-Big-Picture-Through-Quotes-03-31
Awesome blog.Much thanks again. Want more.
https://arenaplus.ph/
We recommend visiting the website https://telegra.ph/The-Drive-Within-Unlocking-Potential-with-Motivational-Quotes-03-31.
Also, don’t forget to bookmark the site: https://telegra.ph/The-Drive-Within-Unlocking-Potential-with-Motivational-Quotes-03-31
Major thankies for the article post.Really looking forward to read more. Really Cool.
https://www.sonhungbac.com/
Awesome article post. Fantastic.
https://atop-education.degree/
Awesome blog article.Much thanks again. Awesome.
https://gbdownload.cc/
Fantastic blog.
https://fouadmods.net/
I really liked your article.Much thanks again. Great.
https://gbdownload.cc/
Мы рекомендуем посетить веб-сайт https://telegra.ph/Luchshie-prikormki-dlya-lovli-shchuki-v-2024-godu-03-31.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Luchshie-prikormki-dlya-lovli-shchuki-v-2024-godu-03-31
I cannot thank you enough for the post.Thanks Again. Really Great.
https://fouadmods.net/
Мы рекомендуем посетить веб-сайт https://telegra.ph/Luchshie-internet-magaziny-rybolovnyh-snastej-03-31.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Luchshie-internet-magaziny-rybolovnyh-snastej-03-31
Im grateful for the blog.Really thank you!
https://nsfwgenerator.ai/
Мы рекомендуем посетить веб-сайт https://telegra.ph/Uspeh-na-konce-udochki-kak-vybrat-i-ispolzovat-kachestvennoe-rybolovnoe-oborudovanie-03-31.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Uspeh-na-konce-udochki-kak-vybrat-i-ispolzovat-kachestvennoe-rybolovnoe-oborudovanie-03-31
Мы рекомендуем посетить веб-сайт https://telegra.ph/Instrumenty-dlya-udovolstviya-pochemu-kachestvennoe-rybolovnoe-oborudovanie—zalog-uspeshnoj-i-komfortnoj-rybalki-03-31.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Instrumenty-dlya-udovolstviya-pochemu-kachestvennoe-rybolovnoe-oborudovanie—zalog-uspeshnoj-i-komfortnoj-rybalki-03-31
Very good post. Really Cool.
http://animegenerator.ai/
Мы рекомендуем посетить веб-сайт https://telegra.ph/Sekrety-uspeshnogo-ulova-znachenie-pravilnogo-vybora-i-ispolzovaniya-oborudovaniya-pri-rybalke-03-31.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Sekrety-uspeshnogo-ulova-znachenie-pravilnogo-vybora-i-ispolzovaniya-oborudovaniya-pri-rybalke-03-31
Really appreciate you sharing this article.Really looking forward to read more. Awesome.
https://zanderqnfv88765.prublogger.com/25585346/trip-package-tips
Bonjour ! Cet article ne pouvait pas être mieux écrit ! En le lisant, je me souviens de mon ancien colocataire qui en parlait tout le temps. Je lui transmettrai cet article. Je suis sûr qu’il l’appréciera. Merci de le partager !
https://www.contre-les-douleurs.fr/la-bandane-proprietes-medicinales/
Мы рекомендуем посетить веб-сайт https://telegra.ph/Na-rybalku-s-uverennostyu-kak-vybrat-kachestvennoe-oborudovanie-dlya-uspeshnoj-rybalki-03-31.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Na-rybalku-s-uverennostyu-kak-vybrat-kachestvennoe-oborudovanie-dlya-uspeshnoj-rybalki-03-31
Мы рекомендуем посетить веб-сайт https://telegra.ph/Rybachok-vsyo-neobhodimoe-dlya-rybolova-03-31.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Rybachok-vsyo-neobhodimoe-dlya-rybolova-03-31
Excellente sélection. Nous allons mettre un lien vers cet excellent article sur notre site. Continuez le bon travail.
https://www.contre-les-douleurs.fr/blog/page/2/
Мы рекомендуем посетить веб-сайт https://telegra.ph/Osnovnye-principy-udachnoj-rybalki-03-31.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Osnovnye-principy-udachnoj-rybalki-03-31
Thanks for sharing, this is a fantastic article.Really thank you! Cool.
https://mbti89857.blogozz.com/24998643/stay-updated-with-live-cricket-scores-on-myfinal11-in
Thanks-a-mundo for the blog post.Really looking forward to read more. Awesome.
https://trevorcjos03680.pages10.com/trip-package-tips-61392775
Мы рекомендуем посетить веб-сайт https://telegra.ph/CHto-neobhodimo-vzyat-s-soboj-na-rybalku-03-31.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/CHto-neobhodimo-vzyat-s-soboj-na-rybalku-03-31
Im obliged for the post.Thanks Again. Really Cool.
https://fernandosxbf68146.qowap.com/85338896/the-advantage-of-satta-matka
Мы рекомендуем посетить веб-сайт https://telegra.ph/Obzor-populyarnyh-pnevmaticheskih-pistoletov-sovety-po-vyboru-03-31.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Obzor-populyarnyh-pnevmaticheskih-pistoletov-sovety-po-vyboru-03-31
This is one awesome blog.Thanks Again. Want more.
https://andersonzknwe.pages10.com/elevate-your-brand-visibility-with-the-best-billboard-advertisement-and-fm-promotion-services-in-surat-gujarat-61314348
Мы рекомендуем посетить веб-сайт https://softnewsportal.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://softnewsportal.ru/
Мы рекомендуем посетить веб-сайт https://doutuapse.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://doutuapse.ru/
Appreciate you sharing, great post.Thanks Again. Cool.
https://bestaccountingsoftwarefor29406.verybigblog.com/25060943/experience-luxury-travel-with-bharat-benz-coach-bus-rentals-in-gurgaon
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-Vash-provodnik-v-mire-rybolovstva-04-09-2.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-Vash-provodnik-v-mire-rybolovstva-04-09-2
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-Vash-nadezhnyj-pomoshchnik-v-mire-rybolovstva-04-09.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-Vash-nadezhnyj-pomoshchnik-v-mire-rybolovstva-04-09
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-Mesto-gde-rybalka-nachinaetsya-s-vybora-snaryazheniya-04-09.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-Mesto-gde-rybalka-nachinaetsya-s-vybora-snaryazheniya-04-09
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-Vash-provodnik-v-mire-rybolovstva-04-09.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-Vash-provodnik-v-mire-rybolovstva-04-09
Thanks-a-mundo for the post. Cool.
https://blog.huddles.app
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-Vash-nadezhnyj-pomoshchnik-v-mire-rybolovstva-04-09-2.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-Vash-nadezhnyj-pomoshchnik-v-mire-rybolovstva-04-09-2
Great, thanks for sharing this post. Fantastic.
https://blog.huddles.app
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-Vash-vernyj-sputnik-v-mire-rybnoj-lovli-04-09.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-Vash-vernyj-sputnik-v-mire-rybnoj-lovli-04-09
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-Vash-nadezhnyj-pomoshchnik-v-mire-rybolovstva-04-09-3.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-Vash-nadezhnyj-pomoshchnik-v-mire-rybolovstva-04-09-3
A round of applause for your article post.Thanks Again. Really Cool.
https://crushon.ai/
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-Vash-vernyj-sputnik-v-mire-rybnoj-lovli-04-09-2.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-Vash-vernyj-sputnik-v-mire-rybnoj-lovli-04-09-2
Very good post. Will read on…
https://www.hommar.com/video/products-detail-4541552
Мы рекомендуем посетить веб-сайт https://vektor-meh.ru//.
Кроме того, не забудьте добавить сайт в закладки: https://vektor-meh.ru/
Мы рекомендуем посетить веб-сайт https://russkiy-spaniel.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://russkiy-spaniel.ru/
Мы рекомендуем посетить веб-сайт https://stroydvor89.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://stroydvor89.ru/
Im obliged for the post.Really looking forward to read more. Much obliged.
https://aihentai.fun/
Мы рекомендуем посетить веб-сайт https://magic-magnit.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://magic-magnit.ru/
Выбираете совершенный подарок или хотите оформить свой праздник волшебными впечатлениями?
Советуем вам: Купить шарики Москва
Рекомендуем добавить сайт http://carstvo-sharov.ru в закладки.
Мы рекомендуем посетить веб-сайт https://kvest4x4.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://kvest4x4.ru/
Мы рекомендуем посетить веб-сайт https://photo-res.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://photo-res.ru/
Выбираете идеальный подарок или хотите оформить свой мероприятие неповторимыми впечатлениями?
Советуем вам: Надувные шары доставка
Рекомендуем добавить сайт http://carstvo-sharov.ru в закладки.
Very informative blog post.Thanks Again. Really Great.
https://crushon.ai/
Мы рекомендуем посетить веб-сайт https://90sad.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://90sad.ru/
Мы рекомендуем посетить веб-сайт https://kmc-ia.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://kmc-ia.ru/
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-vash-nadezhnyj-partner-v-mire-rybalki-04-15.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-vash-nadezhnyj-partner-v-mire-rybalki-04-15
Мы рекомендуем посетить веб-сайт https://thebachelor.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://thebachelor.ru/
Мы рекомендуем посетить веб-сайт https://kreativ-didaktika.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://kreativ-didaktika.ru/
Im thankful for the blog article.Thanks Again. Really Great.
https://www.yinraohair.com/wigs/shop-by-wig-length/pixie-wigs-under-6
Мы рекомендуем посетить веб-сайт https://cultureinthecity.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://cultureinthecity.ru/
Мы рекомендуем посетить веб-сайт http://vanillarp.ru/.
Кроме того, не забудьте добавить сайт в закладки: http://vanillarp.ru/
Мы рекомендуем посетить веб-сайт https://core-rpg.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://core-rpg.ru/
Мы рекомендуем посетить веб-сайт https://urkarl.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://urkarl.ru/
Great, thanks for sharing this article.Much thanks again. Really Great.
https://umhom13.com
I really enjoy the article.Thanks Again. Awesome.
https://umhom13.com
Мы рекомендуем посетить веб-сайт https://yarus-kkt.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://yarus-kkt.ru/
Мы рекомендуем посетить веб-сайт https://imgtube.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://imgtube.ru/
Мы рекомендуем посетить веб-сайт https://svetnadegda.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://svetnadegda.ru/
Thanks-a-mundo for the blog. Fantastic.
https://girl-friend.ai/
Мы рекомендуем посетить веб-сайт https://tione.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://tione.ru/
Thanks for the blog.Really looking forward to read more. Great.
https://girl-friend.ai/
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-vash-vybor-dlya-uspeshnoj-rybalki-04-15.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-vash-vybor-dlya-uspeshnoj-rybalki-04-15
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-vash-put-k-uspeshnoj-rybalke-04-15.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-vash-put-k-uspeshnoj-rybalke-04-15
Major thanks for the blog article.Really thank you! Will read on…
https://aura-circle.com/collections/aura-sleep-mask-collection
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-vash-partner-v-mire-rybnoj-lovli-04-15.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-vash-partner-v-mire-rybnoj-lovli-04-15
I truly appreciate this blog.Much thanks again. Cool.
https://aura-circle.com/
Im obliged for the article. Will read on…
https://lennyfactory.x.yupoo.com/categories/3822886
I value the post.Thanks Again. Cool.
https://x.yupoo.com/photos/lennyfactory2/albums
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-vash-nadezhnyj-partner-v-mire-rybalki-04-15-2.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-vash-nadezhnyj-partner-v-mire-rybalki-04-15-2
Great article.Really looking forward to read more. Much obliged.
https://www.piaproxy.com
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-vash-vybor-dlya-uspeshnoj-rybalki-04-15-2.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-vash-vybor-dlya-uspeshnoj-rybalki-04-15-2
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-vash-put-k-udachnoj-rybalke-04-15.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-vash-put-k-udachnoj-rybalke-04-15
Appreciate you sharing, great article post. Really Great.
https://www.piaproxy.com
Im grateful for the article.Much thanks again.
https://telagrnm.org
Мы рекомендуем посетить веб-сайт https://telegra.ph/O-magazine-Rybachok-04-15.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/O-magazine-Rybachok-04-15
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-vash-put-k-uspeshnoj-rybalke-04-15-2.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-vash-put-k-uspeshnoj-rybalke-04-15-2
Hey, thanks for the blog article.Thanks Again. Much obliged.
https://telcgrnm.org/
Мы рекомендуем посетить веб-сайт https://telegra.ph/Internet-magazin-Rybachok-vash-nadezhnyj-partner-v-mire-rybnoj-lovli-04-15.
Кроме того, не забудьте добавить сайт в закладки: https://telegra.ph/Internet-magazin-Rybachok-vash-nadezhnyj-partner-v-mire-rybnoj-lovli-04-15
Мы рекомендуем посетить веб-сайт https://burger-kings.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://burger-kings.ru/
Hey, thanks for the blog article.Really thank you! Want more.
https://cncmachining-custom.com
Мы рекомендуем посетить веб-сайт http://voenoboz.ru/.
Кроме того, не забудьте добавить сайт в закладки: http://voenoboz.ru/
Мы рекомендуем посетить веб-сайт https://remonttermexov.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://remonttermexov.ru/
Thanks for sharing, this is a fantastic blog post.Thanks Again. Great.
https://www.haijiao.cn
Мы рекомендуем посетить веб-сайт https://lostfiilmtv.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://lostfiilmtv.ru/
Мы рекомендуем посетить веб-сайт https://my-caffe.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://my-caffe.ru/
Мы рекомендуем посетить веб-сайт https://adventime.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://adventime.ru/
Im grateful for the blog article.Really thank you! Will read on…
https://www.slsmachinery.com
Мы рекомендуем посетить веб-сайт https://ipodtouch3g.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://ipodtouch3g.ru/
Мы рекомендуем посетить веб-сайт https://kaizen-tmz.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://kaizen-tmz.ru/
Enjoyed every bit of your blog post.Really looking forward to read more. Really Great.
https://www.glass-lids.com
Im grateful for the blog article. Keep writing.
https://crushon.ai/
I loved your article.Thanks Again. Will read on…
https://crushon.ai/
wow, awesome article. Will read on…
https://crushon.ai/
Very informative blog article.Thanks Again. Will read on…
https://crushon.ai/
Muchos Gracias for your article. Want more.
https://crushon.ai/
Im obliged for the article. Fantastic.
https://crushon.ai/
Мы рекомендуем посетить веб-сайт https://mehelper.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://mehelper.ru/
Мы рекомендуем посетить веб-сайт https://useit2.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://useit2.ru/
Great, thanks for sharing this blog article.Much thanks again. Cool.
https://crushon.ai/character/f5757531-9a53-4c38-85ef-cd5ae51cdc13/details
Мы рекомендуем посетить веб-сайт https://orenbash.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://orenbash.ru/
Wow, great post.Thanks Again. Cool.
https://crushon.ai/character/503eeebe-1626-45bf-89e9-8614106dc5ab/details
Im obliged for the blog post.Thanks Again. Really Great.
https://crushon.ai/character/0370eef1-b4fb-4c24-b4e5-8f66b79d401d/details
Мы рекомендуем посетить веб-сайт https://center-esm.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://center-esm.ru/
Muchos Gracias for your blog.Much thanks again. Fantastic.
https://crushon.ai/character/b2e7751b-b890-4697-ab6b-09b273d08cc2/details
Wow, great blog article.Thanks Again. Fantastic.
https://crushon.ai/character/188bda39-a5d0-40c4-a1a5-33e26408927c/details
Мы рекомендуем посетить веб-сайт https://stalker-land.ru/.
Кроме того, не забудьте добавить сайт в закладки: https://stalker-land.ru/
Im grateful for the blog.Much thanks again. Fantastic.
https://smashorpass.app/
Wow, great blog article.Much thanks again. Much obliged.
https://smashorpass.app/
Really enjoyed this post.Really looking forward to read more. Much obliged.
http://ai-gf.top/
Awesome blog. Great.
https://spicychat-ai.online/
wow, awesome blog post.Thanks Again. Great.
https://rizzgptapp.ai/
Great, thanks for sharing this article.Thanks Again. Really Cool.
https://janitorai.chat/
Looking forward to reading more. Great article. Keep writing.
https://faceswapapp.ai/
Мы рекомендуем посетить веб-сайт http://skatertsamobranka.ru/.
Кроме того, не забудьте добавить сайт в закладки: http://skatertsamobranka.ru/
Really informative article post.Thanks Again. Really Cool.
https://www.pyproxy.com
Awesome blog.Really thank you! Really Cool.
https://vapzvape.com/
Appreciate you sharing, great post.Really looking forward to read more. Great.
https://vapzvape.com/
Really appreciate you sharing this blog article.Really looking forward to read more. Cool.
https://www.vibratorfactory.com
This is one awesome post.Really thank you! Will read on…
https://www.vibratorfactory.com
I truly appreciate this blog post.Really thank you! Want more.
https://honista.io/
Im obliged for the article post. Cool.
https://spotigeek.com/
Обязательно посетите этот сайт – скачать вавада
Ознакомьтесь с лучшими предложениями на 1win, перейдя по ссылке – 1win зеркало
Актуальные бонусы и зеркала на 1win ждут вас по ссылке – https://vk.com/1wincasinotoday
Получите актуальные промокоды и бонусы в лекс казино по ссылке – lex casino no deposit bonus code
лекс казино официальный сайт
Читайте отзывы о lex casino и активируйте бонусы по ссылке лекс казино промокод фриспины
Читайте отзывы о lex casino и активируйте бонусы по ссылке лекс казино скачать на андроид
Читайте отзывы о lex casino и активируйте бонусы по ссылке lex casino review
Ознакомьтесь с топ слотов в онлайн казино 2024 и найдите для себя лучшие игры.
Ищете экзотические игры? Попробуйте casino slots animals и получите незабываемые эмоции.