CIS5302 Professional Skills for Business Analysis
The vision of the project called tradeshow system is to develop its own Geocaching Outings system by the Wayne in order to track the information by them. Wayne Johansen wants to develop the customised system for keeping track of own Geocaching activities and their most common activities is the uncover and searching the caches or covering its own caches.
The Wayne wanted to develop its cache because he is require to track the caches that he has not found till yet and at the same time he also have an interest on the monitoring of routes, distances and the altitudes.
The development of this system can help the Wayne to easily track all his past and future activities (Neustaedter, et. al. 2013). Moreover, with the development of this system, Wayne could locate the caches on the map and store pictures where he has finding the each caches.
Thus, from the development of the Geocachcing system, Wayne Johansen can find its all caches and able to track the information of the caches that he is desire to achieve.
Besides that, the problems that can Wayne Johansen face is that this system demands for the database to keep the track of the information related to the Geocaches. In the development of system, the Wayne requires understanding or having knowledge about the computer but he did not have that much knowledge about the computers and process of the development of software.
In that case, it is recommended that Wayne should need to take helps of the experts or developer who have a specialisation to develop the system. At the end, Wayne decides to build the system that supports his laptop (Cord, et al. 2015)
On the basis of the vision, the project of Geocaching can be divided into the two separate subsystems that are as follows:-
System capabilities and application benefits
System capabilities allow the new system should consist of the following capabilities:-
- New system should track of all the information about the caches and its locations.
- It allows to record detailed and additional information about the geo-cache locations
- It should also help the Wayne to create the new system with the aim to track new Geocaches.
- System also allow to post the information in the Geocache sites
- System also helps o track the locations of the stores where cache has find.
In case of application benefits, the system also provides the following benefits that are mention below:-
- System gives the advantage to the Wayne in order to easily track the Geocaching trips
- It also allow the Wayne to share the Geocaching interest to all their friends
- It also enables the Wayne to create and able to post new Geocaches.
- It also allows the Wayne to update the Geocaching during the travelling with his laptop.
Develop Project Management Plan is the process of documenting the actions necessary to define, prepare, integrate, and coordinate all subsidiary plans.
The project management plan defines how the project is executed, monitored and controlled, and closed (Bayad, et al. 2016). The project is started with Day 1 that is a planning day. The following core process 2 activities will be completed on Day 1:
- Determine the major components (functional areas) which are required.
- Define the iterations and allocate each functional area to iteration.
- Determine the roles and responsibilities of team members.
1.1: Components and iterations
There may be two sub-systems/ components:
- i) A first version can run on a laptop.
- ii) A second version includes mobile components for a smartphone.
The selection of the student will decide the solutions as student focused on one solution after thinking through.
The system can be divided based on functionality. Iteration 1 will be related to capturing the information about geocaches, which are completed by Wayne. Iteration 2 will be to generate and post own geocaching information.
Create WBS is the process of subdividing project deliverables and project work into smaller, more manageable components. For the first iteration, the following WBS is framed that includes different tasks and sub-tasks with time estimation on each step:
DAY 1 (PROJECT PLAN)
DAY 2 (12 HRS)
DAY 3 (14 HRS)
DAY 4 (8 HRS)
DAY 5-6 (22 HRS)
DAY 7 (12 HRS)
Based on the above WBS, it can be stated that this project can be categorized into four different tasks including identifying and analyzing Wayne’s needs to record completed geocaches, designing of the components of the solution, system programming and testing and using the system.
In discovering and analyzing the needs, Wayne and his brother will meet together to view geocaching websites and discuss Wayne’s needs. After this, information will be identified which Wayne is required to keep (Siami-Irdemoosa, et al. 2015). In addition, the use cases will be identified to keep and store the required information.
Moreover, workflows are developed for the identified use cases. In second task named as designing of components of solution, there is need to design the database tables, input and output screens, and configuration for the laptop software application.
In addition, the program details will be designed. In third task, the system will be programmed as database will be created and computer program will be written by incorporating both user interface and database updating.
In last task, the developed system will be tested and used by Wayne (Andersen, 2014). Its functionality will be tested with good data and bad data for checking validation. Further, Wayne will test it with some real data. Then the system will be handed over to Wayne to use.
Task 2: Define and understand the requirements
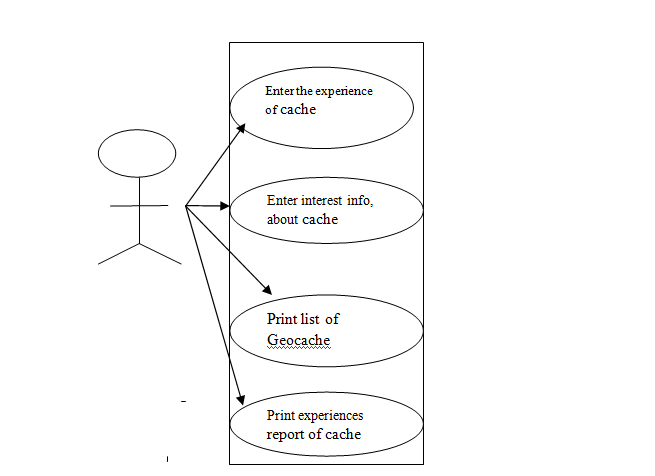
The development of the Geocaching system can provide various solutions to the Wayne regarding the tracking of information of the caches. At the same time in order to develop the system, there is needed to create the simple use case diagram from the list of the cases.
[Source: Khurana, et. al. 2016]
[Source: Isaza, et al. 2016]
Task 3 Define the User Experiences
In this part, the listed cases are defined in which it identifies that how cases will help the Wayne to track the information about their Geocaches. At the same time, it also explains the steps and options to perform the each case of the Geocache.
Steps that are require to perform the use case diagram that are as follows:-
- Firstly there is need to collect the information from the different sources.
- Identify the potential stakeholders like which partners and customers use the goods and services of the business system
- Identify the potential business use case like which goods and services are used for drawing the business system.
- Connect business use cases in which make use of goods and services of the business systems.
- Documentation of business use case
- Create model relationships between the business use case
- Monitor the use case.
In case of Geocaching, the Wayne can develop the use case diagram to systematically study about the process that needs to use in the development of the Geocaching system. The steps that are follows in each use case are mention below:-
- First step in the case of Geocaching are to collect information about the Geocache from different sources and at the same time there is need to enter Geocache information from various sources.
- Secondly, there is need to review the collected information
- Then thirdly, it is require entering the reason for interest in comments.
Thus, such steps help the Wayne to successfully formulate the Geocaching system for tracking all their past and future cache.
3.2 Workflow diagram of the use case
[Source: Hegeman, et al. 2013]

Task 4: Develop the Software Architecture Design
The high-level software architectural design of the system generally includes decisions about how the system will be built and what the database will look like. Design is a technical activity that requires experience in programming, database development, and software architecture. These activities support Core Process 4: Design system components.
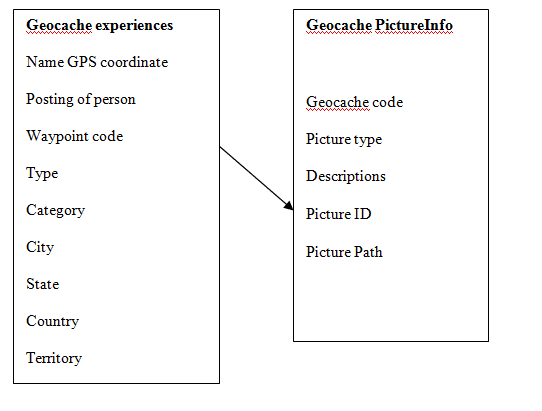
4.1 Design a preliminary database schema
| Geocaching Experience | Geocache Photo |
| Cache ID: integer, auto-increment, {key}
Cache Name: string {index} Person Name: string Gps Coord: string Waypoint Code: string {index} Date Posted: date type: string category: string city: string state: string country: string difficulty: string terrain: string description: string interest Comment: string visit Status: string visit Date: date visit Comment: string |
Image ID: integer, GUID, {key}
Cache ID: integer, {foreign key} Picture Type: string description: string directory Path: string
|
[Source: Schmidt, et al. 2013]
4.2: Desktop system or a browser-based system
Desktop system is a computer based program that runs locally on a computer system like desktop, laptop. On the other hand, in a browser-based system, a web application is delivered to a local device over the internet from a remote server.
Desktop has several advantages such as single machine with easy deployment, single database location, easy to build, secured and easier to build automated interface to download data to computer.
But at the same time, this system cannot be useful to access the data from multiple locations. In addition, it is not easy to share the data with others by using the desktop system (Malhotra, et al. 2014).
On the other hand, browser based system is useful in accessing from multiple locations and sharing the information with others. However, this system always requires internet access that increases the cost of operations. Apart from this, due to the use of browser, there may be possibility of limitation for information display (Creswell, 2013).
In addition, security is more complex due to requirement of login functionality. It is more complex to format reports via browser. But both applications are used to solve problems like electronic spreadsheets on laptop using the Microsoft Excel desktop application or a web application like Google Docs (Nathan, et al. 2013).
Both can be used to edit the basic spreadsheet but in the Google option, a live internet connection is required to work.
Desktop applications are expensive as PC and Mac platforms cause double development costs of either platform alone. However, web-based system is less expensive than the development of a desktop application for any one target platform.
Based on this comparative analysis, it can be suggested that it can be more beneficial to use browser-based system rather than desktop system.
It will be better for Wayne to use browser based system due to its cost effectiveness and more advanced features to handle the problem associated with geocaching (Anbuselvan, et al, 2015).
Task 5: develop the detailed design and program the system
In order to programming the selected system, there is need to select the most suitable programming language for developing the results. Likewise, in case of Wayne, the programming language that they could use is the complied and interpreted language.
So by studying the both the programming language advantage and issues, there is need to decide the best suited language for the Geocaches. So here are the advantage and limitation of the languages (Scheffer, et al. 2015).
Complied language:-The task of the complied language is to generate the two types of codes that is machine code and sources code and it make them compile. This complier language is the support system to interpreter language as it contributes in the developing of source and machine code.
The major advantage of the compiled language is that it takes minimum time in the translation process and this system is also supported to the newer technologies like just in time compilation.
Thus the complied language consider as a vital programming language to run the system in an appropriate manner (Severance, 2012).
In addition to this, complied programming language consider as a low-level programming language in which efficiency of the programs is the big problem or concern as in such languages, there are more one to one association between the programme code and hardware operations that is perform by the machine code.
So it becomes a complex task for the developer and in that case it is recommended that developer should use the programmers to control the use of central processing unit (CPU) and memory.
Interpreted language is the programming language that is well suited to execute something in the system. Basically, this programming language dose not compiles the program into the machine language instructions. In this, the interpreter can executes the program directly and able to translate the each statements into the sequences and systematic form.
Interpreted language is the programming language that easily considers the changes in the coding of the programs and the user interface of the programs is also simple to use (Bezanson, et al. 2012).
At the same time the main advantage that the interpreted language is provided is that it gives high security to the coding and does not allow to unauthorised access from the hackers.
This language also supports the latest versions of the programs like PHP, ASP. net etc. Moreover, the interpreted language is the user friendly language as it provides the graphic designs, image formation and coding etc.
This programming language is also flexible as for every computer it performs different programming and coding. It is also easy to learn and use and it can be perform by the less experiences user.
It allows performing the complex task in a few steps and it also edits and running of code in a fast manner (Ferreira, 2011) .
At the same time, the interpreted language is having an limited access to low level and speed optimizations code and interpreted language is also not support the changes frequently in the coding and it detecting the errors in the designing of the websites.
This programming considers as a traditional programming that does not support the advance technology. The graphic design and image formation is become a complex task under this programming language. This language also not allows making changes in the coding of the programming as JAVA system does not support it. The transition and the run time of the programs are also slow in this coding (Lucas, et al. 2010).
Besides there drawbacks, this program is widely used by the programmers as its coding is easily available and widely accepted by the users because its coding supported by both JAVA and advances JAVA.
Likewise, in the case of Wayne, the interpreted programming language could be prove to be beneficial as it supports the coding process and it also helps the user to easily change the data according to the changing technology.
So in that case, it is recommended to the Wayne to use the interpreted language for developing the Geocache system as this language provide support to developer to easily create the coding of the system.
Besides that, this programming also provides high security to the user in terms of protecting from the unauthorised access by the hackers (Fjeldstad, et al 2011). It also allow the Wayne to easily track the information about their cache pasta and present locations through the effectively use of graphic design, image formation.
At the same time, the interpreted programming language supports the latest version of the systems and programming language also assists in the development of the user-friendly system.
Task 6: Test and Deploy the System
6.1: Differences between programmer testing and user testing
There are several differences between programmer testing and user testing. Programmer testing is useful to test only good data. On the other hand, user testing is used to test in complex ways including good and bad data. In addition, artificial data is tested in programmer testing, whereas more complex data is preferred to test in user testing.
Apart from this, there is limited testing in programmer testing as it cannot be always verified that answers are correct. At the same time, this testing rends to test for crashes versus correctness while user testing tends to make mistakes (Gavalas and Kenteris, 2011).
Programmer testing cannot always test several combinations. But, user testing is used to test on the basis of work procedures. In addition, user testing is effective to assess the system against the user’s reactions and expectations. It unlike programmer testing is used to understand the solution actually solves the problem of the user or not.
This testing is not for discovering the defects but it is used to know how the customer can use it and enjoy by using the new system. On the other hand, programmer testing is effective to know the defects in the new system and helps to make the desired steps to improve the system (Blount, et al. 2010)
There are several deployment issues in both desktop system and browser-based system. In desktop system, there may be operating issues that can be related to different operational activities during the system designing.
Apart from this, there may be deployment issues related to setting up database, startup script to start database engine. In addition, it is also a deployment issues how to backup or restore data and paths and libraries for image storage. There are some deployment issues regarding compiled/linked version versus interpreted language.
On the other hand, in browser system, all the above identified deployment issues may be faced in browser-based system, but these should be decided for server. In addition, it is also challenging to deploy server (home based or hosted) (Dangl, et al. 2013).
There is need to consider virtual server for domain names and address in browser-based system. Along with this, there may be possibility of security issues due to hacking and posting the unwanted data. In the website of www.geocaching.com, issues related to browser-based system need to be addressed to deploy. In addition, it is also consider where and how the site will be hosted and how to build for multiple browsers (Lin, et al. 2011).
Apart from this, it will also be required to address the issue related to growth and scalability.
Anbuselvan, A., Oracle International Corporation, (2015) System and method for integration of browser-based thin client applications within desktop rich client architecture. U.S. Patent 8,996,658.
Andersen, E.S., (2014) Value creation using the mission breakdown structure. International Journal of Project Management, 32(5), pp.885-892.
Bayad, M., El Fenne, A. and Ferry, A. (2016) Porteurs de projet en recherche d’un nouvel emploi et entrepreneuriat: sortir de la dichotomie opportunité/nécessité. Revue de l’Entrepreneuriat, 15(3), pp.205-229.
Bezanson, J., Karpinski, S., Shah, V. B., and Edelman, A. (2012) Julia: A fast dynamic language for technical computing. arXiv preprint arXiv:1209.5145.
Blount, M., Ebling, M. R., Eklund, J. M., James, A. G., McGregor, C., Percival, N., … andSow, D. (2010) Real-time analysis for intensive care: development and deployment of the artemis analytic system. IEEE Engineering in Medicine and Biology Magazine, 29(2), pp. 110-118.
Cord, A.F., Roeßiger, F. and Schwarz, N. (2015) Geocaching data as an indicator for recreational ecosystem services in urban areas: Exploring spatial gradients, preferences and motivations. Landscape and Urban Planning, 144, pp.151-162.
Creswell, J.W., (2013) Research design: Qualitative, quantitative, and mixed methods approaches. USA: Sage publications.
Dangl, J. L., Horvath, D. M., and Staskawicz, B. J. (2013) Pivoting the plant immune system from dissection to deployment. Science, 341(6147), pp. 746-751.
Ferreira, D. F. (2011) Sisvar: a computer statistical analysis system. Ciência e agrotecnologia, 35(6), pp. 1039-1042.
Fjeldstad, B., Sannella, M. J., and Roosen, C. B. (2011) U.S. Patent No. 8,087,002. Washington, DC: U.S. Patent and Trademark Office.
Gavalas, D., and Kenteris, M. (2011) A web-based pervasive recommendation system for mobile tourist guides. Personal and Ubiquitous Computing, 15(7), pp. 759-770.
Hegeman, T., Ghit, B., Capota, M., Hidders, J., Epema, D. and Iosup, A., (2013) October. The btworld use case for big data analytics: Description, mapreduce logical workflow, and empirical evaluation. In Big Data, 2013 IEEE International Conference on. IEEE, pp. 622-630.
Isaza, F.A., Eraso, D.A.Á. and Arboleda, F.J.M., (2016) A proposal for the formalization of the class diagram in Maude Language. REVISTA POLITÉCNICA, 12(23), pp.39-50.
Khurana, N., Chhillar, R.S. and Chhillar, U., (2016) A Novel Technique for Generation and Optimization of Test Cases Using Use Case, Sequence, Activity Diagram and Genetic Algorithm. JSW, 11(3), pp.242-250.
Lin, P., Zhang, J., Chen, Y., and Zhang, Q. (2011) Macro-femto heterogeneous network deployment and management: from business models to technical solutions. IEEE Wireless Communications, 18(3).
Lucas, B. C., Bogovic, J. A., Carass, A., Bazin, P. L., Prince, J. L., Pham, D. L., and Landman, B. A. (2010) The Java Image Science Toolkit (JIST) for rapid prototyping and publishing of neuroimaging software. Neuroinformatics, 8(1), pp. 5-17.
Malhotra, K., Medhekar, S., Navathe, S.B. and Laborde, M.D. (2014) Towards a form based dynamic database schema creation and modification system. In International Conference on Advanced Information Systems Engineering, Springer International Publishing, pp. 595-609.
Nathan, A.D., Sterland, A., Leonard, M.J., Rice, T. and Montgomery, J.I., Microsoft Corporation (2013) Security system for a browser-based environment. U.S. Patent 8,543,638.
Neustaedter, C., Tang, A. and Judge, T.K. (2013) Creating scalable location-based games: lessons from Geocaching. Personal and Ubiquitous Computing, 17(2), pp.335-349.
Scheffer, L., Lavagno, L. and Martin, G. eds. (2016) EDA for IC system design, verification, and testing. USA: CRC press.
Schmidt, D.C., Stal, M., Rohnert, H. and Buschmann, F., (2013) Pattern-Oriented Software Architecture, Patterns for Concurrent and Networked Objects. USA: John Wiley & Sons.
Severance, C. (2012) Javascript: Designing a language in 10 days. Computer, 45(2), pp. 7-8.
Siami-Irdemoosa, E., Dindarloo, S.R. and Sharifzadeh, M. (2015) Work breakdown structure (WBS) development for underground construction. Automation in Construction, 58, pp.85-94.


