CN7026 Cloud Computing Assignment Sample
HERE IS SAMPLE OF CN7026 Cloud Computing Assignment
Introduction
“Cloud computing” is defined as the common usage of software and hardware for delivering services in a network, especially with the help of the Internet. This comprises networking, databases, software, servers, intelligence and analytics. The cloud is defined as the Internet. It offers flexible resources and faster innovation. “Cloud Service Provider” management system is defined as a model for operation in which storage users use SaaS offerings for the proper management of tasks. This model is very much advanced as it does not include any installation of software, simple in use, cheap and no modification in infrastructure required.
Project planning
The purpose of the project is to understand the different ways that are being adopted by cloud “service” providers for the proper management of the data. The three types of services that are being such providers are platforms that are being used for service (PaaS), infrastructure which is being used for service (IaaS) and software that is being used for providing service (SaaS). The significant planning is that with the help of Azure, AWS and Google, which can be used for software services and thereby using these providers for the better management of the data (Almorsy, et al., 2016).
The main goal is to enhance the business procedures by increasing the flexibility and scalability by reducing the dependency on physical constraints. These service providers will help in the storage of data on a large scale by business organizations. These service providers provide backup data as and when required by the organization.
Body: Implementation and solution of cloud architecture
Gathering of requirements
The functional requirements that are involved with the use of “cloud service” provider are as follows:
- Customer support and security: Security is considered to be the most critical option while making a selection for the use of providers for cloud hosting (Ferris,et al., 2018). It is mandatory because the service provider will deal with the vital data of the company. There must be an implementation of antivirus software backup storage and firewalls for ensuring security.
- The service provider must provide excellent customer support by providing technical support to the customers with the help of a third-party source. The problems must be mitigated within time.
- Ease of problems in administration: The service that is being provided by the provider must be easy to understand, learn and implement.
- Storage, Backup and Retrieval: The service providers must provide data backup, which is essential during data loss due to corruption and during an emergency.
- Scalability: These factors are mandatory as it enhances the flexibility of the business by including price, system expansion, storage, system retraction and functionality.
- Reliability: The system that is being provided by the service provider must be operational, capable and functional for making this user-friendly.
- Other issues: the other issues that need to be kept in concern are the price of the software and smooth functioning of it.
Non-functional needs are as follows:
- Interoperability: The service provider must use open standards for managing the workloads.
- Usability: The service provider must use well-defined software and interface depending on the clients.
- Integration: The service provider must keep note that there is no interchange of data centres while there is an integration between two clouds.
The risks that are involved are in cloud computing are:
- Unauthorized access: this type of risk arises whenever there is unauthorized access to the third party.
- Vendor security risks: this risk is caused by the transfer of data to the vendors.
- Legal risks: this risk occurs when there are illegal steps taken by the company.
- Control risks: whenever the software becomes uncontrollable then it causes problems
.
Cloud platform selection
There has been the availability of several types of service providers that are being used for the better management of data. Amongst all the “cloud” service providers, AWS proves to be more beneficial (Di Spaltro,et al., 2016). “Amazon Web Services” (AWS) has a wide range of benefits which makes it advantageous while using it. These are as follows:
- User-friendly: The design of AWS is such that it allows ISVs, vendors and application providers for hosting applications securely and quickly.
- Flexible: AWS provides options for the selection of database, programming language, the platform for web application and operating system to the users.
- Cost-effective: AWS only charges for useful resources, storage and computing power. There are no further charges for up-front commitments and long-term contracts.
- Reliable: Just because of the reliability of AWS, it serves as Amazon.com’s virtual backbone by providing an infrastructure for global computing.
- High performance and Scalable: The application of AWS can increase or decrease its scaling level depending on the demand with the help of “Elastic load balancing”, AWS tools and Auto Scaling
- Secure: The approach that is being provided by AWS is end-to-end, which will harden and secure the infrastructure, including software, operational and physical measures.
Selection standards and data-centre
The various types of information are being stored in AWS. The backup files, store data for business are being stored in the AWS software (Moustafa,et al., 2017). The data centre that is being used by AWS for cloud service is TIER-4. This proves very efficient while handling various types of risks that are involved and thereby provides efficiency and security (Kratzke,et al., 2017). These standards for this type of data-centre are as follows:
- Perimeter layer: This layer provides security at the beginning phase.
- Data layer: This layer deals with customer data and thereby protecting with devices having threat detection qualities.
- Infrastructure layer: This layer is concerned with the building of the data-centre and thereby keeping the systems running (Amin,et al., 2018). This layer includes backup storage qualities.
- Environmental layer: this layer is concerned with the environmental issues regarding hazards that are caused due to environmental hazards.
The architecture of the Cloud system
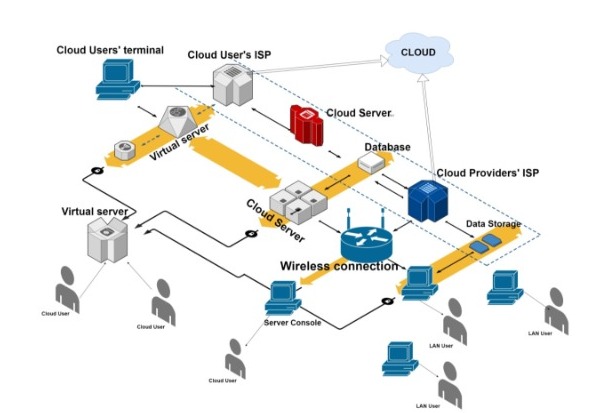
Figure 1: AWS architecture
Source:Draw.io
The architecture of AWS is very efficient, and it will be helpful in the proper management of data. There is the availability of wireless connection which helps in the transfer of data to the various servers (Aikat,et al., 2017). There is the availability of ISP terminals for cloud providers which acts as the cloud and thereby transfers data to the storage devices from where the data is being delivered to different LAN and cloud users.
All the cloud servers are being connected to the virtual servers from which information is directly transferred to the other cloud users. There is an availability of databases between two ISP terminals through which data is being delivered to the cloud servers. Then the information is transferred to the wireless connection for further transmission of data to the users. [Referred to Appendix 1]
Cloud platform implementation
AWS provides a suitable cloud platform for the quick transfer of data to various LAN users. This software helps in the storage of the information of different users on a large scale and also provides security to the stored data during emergencies. The software is flexible and thereby adapts to the changes in the cloud structures very quickly (Kaushik,et al., 2016).
The availability of high traffic that is involved in the process due to the usage of the software by multiple users are managed in a very efficient way and thereby avoiding a breakdown. There is no interruption of data due to any kind of hazards and thus not hampering the satisfaction level of the users.
Reflection and analysis
In my view, the system maintenance for AWS software can be done by the following methods:
Optimization of AWS: I would suggest that by providing observation on AWS software, the problems that are raised while using it can be omitted by adopting suitable measures like software transition and preparation activities.
Error correction: I suggest that the errors that are being generated while using AWS can be omitted and rectified immediately for offering smooth functioning.
Elimination useless features: there are many unnecessary features which includes residual files, cache, agreement receipts of customers which are available in AWS software which creates a lot of junk in the software and therefore these junks are needed to be cleaned immediately for the smooth functioning of the software in the long run.
Development of modern features: The features that are available in the software are needed to be updated regularly for enhancing the performance.
In my opinion, the update of AWS software with the help of new innovative technologies will help in the better management of its evolution and thereby providing support to the customers in the future (Kumar,et al., 2018). I would suggest that abiding by the government rules and regulation while developing the software and also proper clearance of taxes will help in the development of the software.
Conclusion
The report concludes the usage of cloud computing. The report provides an idea about the benefit of “cloud service” providers for proper management of data. The report highlights the planning of this project. The report states the non-functional and functional requirements of service providers for cloud computing. The report says the benefit of taking AWS for getting the service of cloud computing and also states the reason for its advantage over different software. The report states the data centre selection and its different standards. The report gives a clear image of the AWS architecture and also provides a good reflection of the author regarding the update of AWS.
Reference list
Journals
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security problem. arXiv preprint arXiv:1609.01107.
Ferris, J.M., Red Hat Inc, 2018. On-demand cloud computing environments. U.S. Patent 10,025,627.
Di Spaltro, D., Polvi, A. and Welliver, L., RACKSPACE US Inc, 2016. Methods and systems for cloud computing management. U.S. Patent 9,501,329.
Moustafa, N., Creech, G., Sitnikova, E. and Keshk, M., 2017, November. Collaborative anomaly detection framework for handling big data of cloud computing. In 2017 Military Communications and Information Systems Conference (MilCIS) (pp. 1-6). IEEE.
Kratzke, N. and Quint, P.C., 2017. Understanding cloud-native applications after 10 years of cloud computing-a systematic mapping study. Journal of Systems and Software, 126, pp.1-16.
Aikat, J., Akella, A., Chase, J.S., Juels, A., Reiter, M., Ristenpart, T., Sekar, V. and Swift, M., 2017. Rethinking security in the era of cloud computing. IEEE Security & Privacy.
Kaushik, A. and Kumar, A., 2016. Application of cloud computing in libraries. International Journal of Information Dissemination and Technology, 3(4), pp.270-273.
Kumar, P.R., Raj, P.H. and Jelciana, P., 2018. Exploring data security issues and solutions in cloud computing. Procedia Computer Science, 125, pp.691-697.
Amin, R., Kumar, N., Biswas, G.P., Iqbal, R. and Chang, V., 2018. A light weight authentication protocol for IoT-enabled devices in distributed Cloud Computing environment. Future Generation Computer Systems, 78, pp.1005-1019.
24/7 Chat Support | Get A+ Grade | Written by Top-Notch Subject Experts | 20% Off 1st Order |
Know more about UniqueSubmission’s other writing services:

