CO4509 Digital Security Assignment Sample
Module code and Title: CO4509 Digital Security Assignment Sample
Introduction
Smart phones are becoming one of the most significant devices in human lives due to the variety of features and adaptability. Technological incorporation associated with the smart phone industry is enabling companies to make positive changes to the associated technologies such as Bluetooth, and smart phone security.
The security concerns associated with smart phone devices are major areas of concern for smart phone manufacturers. Smartphone security processes and PC security processes have distinct differences regarding their process of application and the manufacturers are trying to incorporate effective security processes to increase the operational sustainability of smart phone devices.
This report has provided a detailed analysis of the principles and theories associated with smart phone security exploits. The state of the smart phone security processes over the past five years has been discussed briefly in this report. The current state of the smart phone security industry has been analysed in this report for understanding the importance of smart phone security. The effectiveness of the smart phone security exploits is discussed inside this report as well.
The basic principle of Smart Phone Security exploits
Operating Systems (OS) is the basic principle, which is the fundamental aspect of the systems associated with smart phones across the world. Android and iOS are the two most popular operating systems, which are used for the development of smart phones across the industry. The location tracking processes are one of the common security exploits issues associated with mobile devices.
Both android and iOS operating systems are based on fundamentally different application processes. The location tracking process becomes a vulnerable option for the Android operating system due to its application signing procedures (Al-Qershi et al. 2014). The easiness associated with application signing procedures makes it a major security issue for android smart phones.
Application Programming Interfaces (API) is one of the major security concerns for the smart phone industry as well. On the contrary, the iOS operating system used within iPhones has improved security processes associated with their operating processes. One of the fundamental reasons for improved security control for iPhones is the incorporation of official networking processes.
Usage of official networking processes is one of the fundamental principles associated with iOS security processes. Apple (manufacturers of iOS-based smart phones) uses the principle of review is used for the analysis of the application before entering the market. The following are multiple stages used by Apple for conducting a comprehensive analysis of their iOS-based smart phones
- “Address Space Layer Randomisation (ASLR)”: The ASLR process is a memory-based protection process used in protecting against “buffer-overflow attacks”
- “Data Execution Prevention (DEP)”: DEP is an effective protection process used for protecting a particular section of the memory within the operating system
Furthermore, both ASLR and DEP protection process is sued for protecting the windows operating systems as well. The controlled flow of attack is stopped using these security management processes. Source codes (Used in Java Programming Language) are used for protecting Android devices. The introduction of the code protection system helps the android devices to make positive changes to security processes against malware attacks. Permission-based defence technique is one of the major principles used for providing protection against security exploits for android smart phones.
Theories of Smartphone security exploits
The introduction of multiple security models is one of the major theories associated with smart phone security exploits. Both android and iOS-based operating systems have different security models based on their architectures. Figure 1 provides a detailed analysis of the architecture used for implementing security processes for Android smart phones.
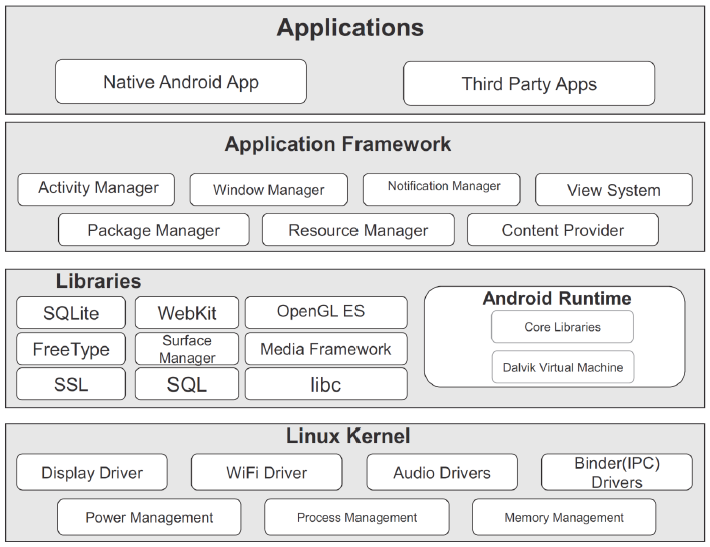 Figure 1: Architecture associated with Android operating system (Source: Ahmed and Sallow, 2017)
Figure 1: Architecture associated with Android operating system (Source: Ahmed and Sallow, 2017)
Initially, Google used the programming theories in C and JAVA for developing the Android architecture. After that, “Open Handset Alliance (OHA)” was used for developing the architecture associated with android devices. The Linux Kernel used in the development of the android architecture consists of APIs, Middleware (Based on C-programming) and libraries for increased control within the Android architecture (Ahmed and Sallow, 2017).
- 2D or 3D graphical issues are managed by OpenGL
- Managing the Sorting data related issues, the SQLite database engine is used by smart phone manufacturers (Ahmed and Sallow, 2017)
- For managing the HTML content-related issues, the “web browser engine Webkit is used” by the smart phone manufacturers
However, there are different theoretical approaches are considered for managing the security issues associated with iOS security processes. Following are the multiple theoretical models used in the development of the security processes associated with iOS operating systems.
First Model: The first model associated with the development of the iOS security processes is constructed with the following four Pillars
- Device Security: This state is developed to protect unwanted accessibility by generating pass codes and “build-in services”.
- Data Security: 256-bit AES encryption security technique is used for protecting customer data
- Network Security: The network security protocols such as “Secure Socket Layer Protocol v3 (SSL), Transport Layer Security v1.2 (TLS) and Secure/Multipurpose Internet Mail Extensions (S/MIME) protocol” are used for protecting the network issues within the iOS security processes.
- Application security: Sandboxing is a major application used for protecting the isolation of multiple applications. Code singing and Application Review are application security processes used by iOS for protecting their security systems.
Second Model: The second model associated with iOS security is enabling that multiple techniques can be used together to create a positive network for iOS operating system security. ASLR, Code Signing, “Memory Management Unit (MMU)” and Type safety are essential processes described in the second model for ensuring protection for iOS devices.
State of Smartphone security for the past five years
The recent development associated with malware is a major area of concern for smart phone manufacturers. Approximately 90% of the world population has a smart phone, which is a major indicator of the changes in technological approaches. Over 50% of the internet traffic is the smart phone users which is enabling the chances of attacks on smart phones. Both Android and smart phone users are facing issues related to apps, networks and device securities. Figure 3 is proving a detailed analysis of the number of cyber attacks on smart phones in recent times.
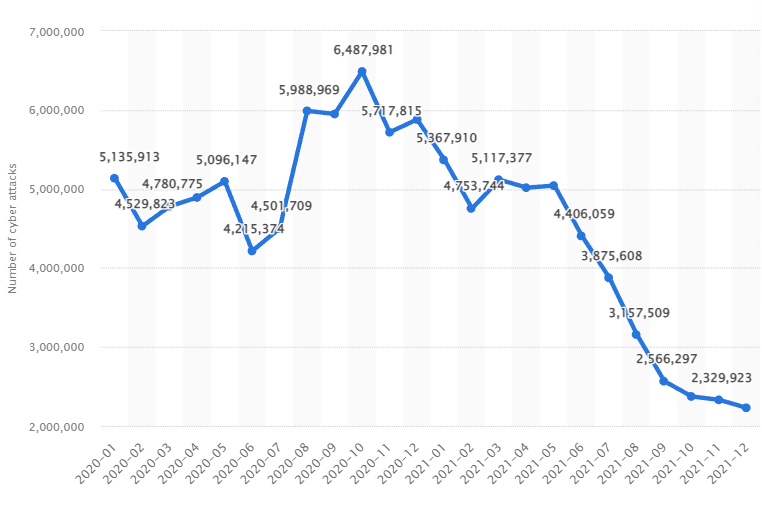 Figure 3: Number of global attacks on smart phones in recent times (Source: Ceci, 2022)
Figure 3: Number of global attacks on smart phones in recent times (Source: Ceci, 2022)
In the early stages of FY 2020, the number of monthly attacks on mobile phones surpassed 5,000,000 indicating a major concern for the smart phone manufacturers (Ceci, 2022). However, the late stages of the FY 2021 are indicating a decrease in mobile attack cases. The number has decreased to 2,329,923 in December 2021 indicating a major shift in mobile security-related issues.
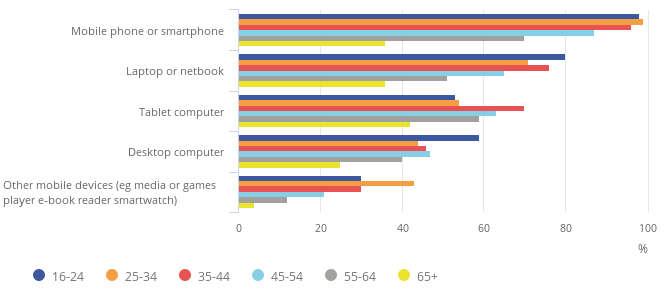 Figure 4: Number of Smartphone users accessing the Internet in 2018 (Source: Verdict.co.uk, 2018)
Figure 4: Number of Smartphone users accessing the Internet in 2018 (Source: Verdict.co.uk, 2018)
According to figure 4, the number of people associated across multiple ages (Teenagers, Adults and the Elderly) are using smart phones to access the internet in 2018. The number is gradually increasing as the availability of android or iOS-based smart phones increases across the UK. Almost 95% of the adults aged from 25 to 34 are using smart phones for accessing the internet. The increase in monetary transactions is a major change in the past five years as people are using smart phones to pay for their monthly subscriptions for different apps such as Netflix, Amazon Prime and online purchases.
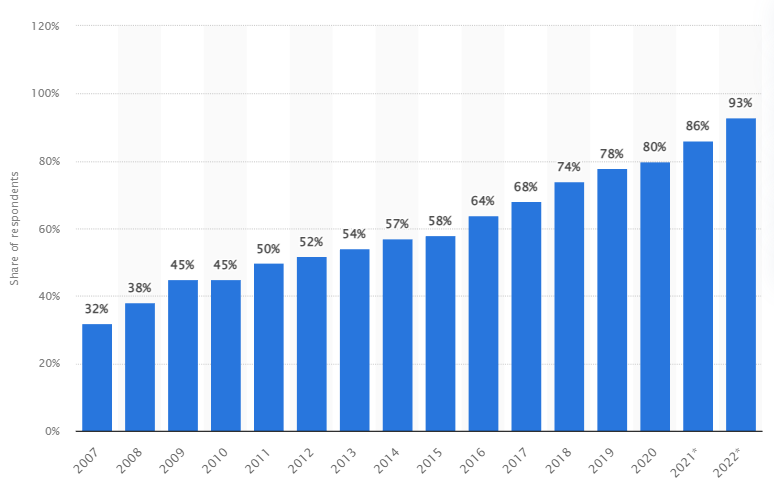 Figure 5: Increase in online banking services (Source: Statista Research Department, 2022)
Figure 5: Increase in online banking services (Source: Statista Research Department, 2022)
According to figure 5, the increase in digital banking processes is a major reason for the cyber security issues associated with smart phones. Since 2017, the number of online banking processes has increased from 68% to 93% increasing the security risks associated with smart phones (Statista Research Department, 2022). The increase in digital monetary transactions created major security concerns for the smart phone manufacturers in creating a sustainable environment for the users.
| Type of security issues | Major incidents | Process of Occurrence |
| Password issue | Pegasus spyware | The software hacked the iPhones by accessing the normal apps associated with the iOS operating systems. The spyware associated with this process targeted the iPhones for their ineffective password protection processes. Since the Pegasus spyware attacks, both Google and iOS have increased their app security systems (Marczak et al. 2020) |
| OS (Operating System) threats | Apple File
Communication (AFC) protocol
|
The encryption attack on Apple devices was significant in cresting major issues related to digital rights (Al-Qershi et al. 2017) |
Table 1: Table for examples of smart phone security issues
Real life incident on smart phone security attacks
One of the latest incident that was reportedly highlighted was T-Mobile hack, in which around 50million individuals were affected by the security attack. What happened in this attack was a bizzare experience to a large number of customers of the T-mobile company where sensitive information was exposed (zdnet, 2022). The attack was done by a youngster after finding out the gaps in the defenses of T-Mobile network and the attack was done by using an unprotected router.
A large number of malicious activities have been found in current times through the accession of different malware apps. These included stolen data, unauthorized charges and so on. These serve to be really dangerous in nature due to the disruption and hampering of potential data and in order to stay safe from these kinds of attacks one should be careful while installing applications from online platforms (bleepingcomputer, 2022).
The current state of smart phone security
The reticent development associated with smart phone security issues has been based on the development of proper education for smart phone users. The incorporation of effective Bluetooth devices is a major area of importance for the smart phone industry. Companies need to incorporate modern communication devices to increase the security of smart phones. Figure 6 is providing a detailed analysis of the Bluetooth piconet service, which can be used for improving the security of smart phones (Lonzetta et al. 2018).
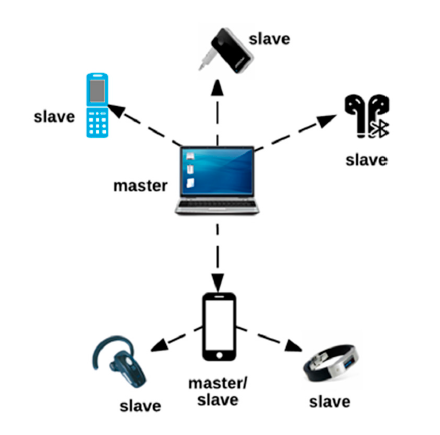 Figure 6: Bluetooth Piconet service (Source: Lonzetta et al. 2018)
Figure 6: Bluetooth Piconet service (Source: Lonzetta et al. 2018)
Implementation of effective master and slave processes will be essential for creating an improved communication process for their smart phones, which will enable the users to connect multiple devices with their associated smart phones.
Following are most significant Bluetooth attacks associated with smart phone technologies.
Mac Spoofing attacks: The Mac spoofing attack is a type of attack based on encryption issues while formation of the piconet (Lonzetta et al. 2018). In this type of Bluetooth attack process, the attackers use the process if imitation for implementing the changes associated with connections.
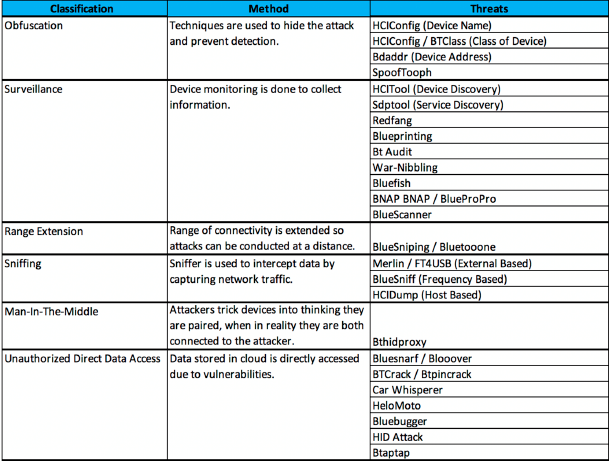 Figure 7: “Bluetooth threat taxonomies” (Source: Lonzetta et al. 2018)
Figure 7: “Bluetooth threat taxonomies” (Source: Lonzetta et al. 2018)
Figure 7 is providing a detailed analysis of the Bluetooth threats and the methods used for solving the issues associated with the threats. For example, the HCITool is used for mitigating the challenges associated with device monitoring processes (Lonzetta et al. 2018).
The implementation of effective Bluetooth connection devices is enabling manufacturers to improve security for smart phones. Approx. 24% of smart phone users do not have appropriate knowledge regarding their smart phone security issues (Verdict.co.uk, 2018). The UK government is trying to implement multiple initiatives to educate the users to adopt safer approaches to handling smart phones. Following are the major areas associated with smart phone security issues that need careful understanding by the users
- Information Leakage: Information leakage is a major source of security concern for smart phone users. The permission before accessing multiple apps needs to be monitored for avoiding the information leakage issues associated with modern smart phones (Ahmed and Sallow, 2017).
- Repackaging Apps: The repackaging of apps is a major area of concern for smart phone users due to their accessibility issues. Management of .apk files plays an effective role in creating a positive impact on the security concerns of smart phone users.
- Implementation of effective passwords: The adaptation of effective password protection across smart phones is becoming a modern trend in smart phone security processes. Organisations have started mandatory use of Alphanumeric characters for smart phone users to increase the device security system (Ico.org.uk, 2022). The multi-layer password system is another process used by multiple apps for increasing the protection associated with their devices.
- Installation of apps from trusted sources: Usage of trusted sources for app installation is a major security improvement associated with smart phone manufacturers. The incorporation of authentic sources such as the “Apple App Store”, Google Play or “BlackBerry World” is beckoning a viable solution for the smart phone manufacturers to increase security for their associated devices.
Following are other modern processes used by attackers to launch attacks on Smart phones.
Social Engineering
Bauer et al. (2020) have mentioned that the processes associated with apps downloading can create major security concerns for the Smartphone. If apps are not downloaded from a secured source, the IP addresses can be tracked for phishing and cyber attacks. Social Engineering has become one of the most common forms of attack on smart phones. Figure 8 is providing a detailed analysis of the processes associated with attacks on smart phones from social platforms.
 Figure 8: The process of cyber attacks using the social sites (Source: Gontovnikas, 2021)
Figure 8: The process of cyber attacks using the social sites (Source: Gontovnikas, 2021)
A deep search process is used for the gathering information reading the Smartphone users (Gontovnikas, 2021). The information gathered form deep search processes are used for attacking the devices for future instances.
Through public Wi-Fi
Public Wi-Fi system is becoming an effective process for attacking the Smart phones of common people. Public Wi-Fi network care connected with encrypted messages and people accessing the networks generally do not have much idea about the end users. Figure 8 is providing a detailed analysis of the processes used for attacking the smartphones through
public Wi-Fi.
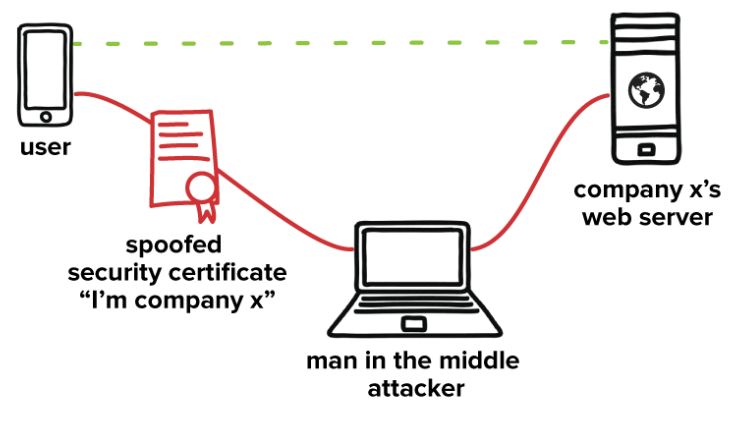 Figure 9: Processes used for attacking smart phones using the public Wi-Fi networks. (Source: Gontovnikas, 2021)
Figure 9: Processes used for attacking smart phones using the public Wi-Fi networks. (Source: Gontovnikas, 2021)
Figure 9 is showing an analysis of the process, which is used for attacking the smartphones using the public Wi-Fi networks. The fake company certificate is used to attract smart phones and after connecting to the fake Wi-Fi the customer, information is stolen by the attacker in the middle.
Future importance and effectiveness of Smartphone security exploits
Segregation of effective smart phone security approaches is essential for ensuring a sustainable operating atmosphere for smart phone users. Ahmed and Sallow (2017) have opined that static and dynamic are the two classes associated with smart phone security issues which can be used for ensuring a positive and sustainable atmosphere for smart phone users. The authors mentioned hybrid methods (A combination of static and dynamic processes) for ensuring effective protection for smart phones.
Following are several approaches, which can be used for restricting smart phone security exploitation for future instances.
- Crowdroid: Crowdriod is an effective malware detection process that is used for analysing the behaviour associated with smart phone security. The behaviour of the crowd sourcing application is managed with the help of user end and remote server end devices. The behavioural data associated with this process can be found in the form of a log file as well.
- RecDroid: RecDriod is an effective framework, which uses the crowd souring process for accessing resource permission control. The recording process helps users to segregate their choice parameters and help users to choose the appropriate option according to their requirements.
- FireDroid: FireDriod is an effective framework, which is used for managing the policies associated with security systems. This security system is enabling smart phone manufacturers to generate an application monitor for their operating systems. The FireDriod process is an essential process for detecting malware with a smart phone system irrespective of the packaging types (Ahmed and Sallow, 2017).
Conclusion
It can be concluded that this report is developed to provide an overview reading the smart phone security issues. This report has mentioned the basic principles of smart phone security exploits for understanding the major areas associated with security exploits. Android and iOS are the two most popular operating systems used for the development of smart phones.
API and the official networking process are several processes used for developing the operating systems. ASLR and DEP are two data management processes, which are used in the development of iOS-based operating systems. The incorporation of ASLR and DEP processes increases the security issues for iOS operating systems. Open Handset Alliance is an effective process used by Google to create positive changes with the Android infrastructure.
The security issues associated with the smart phone industry are creating major challenges for proving a sustainable atmosphere for the smart phone used across the UK. Approx. 90% of the users have shifted their focus on use smart phones for accessing the internet. The adults aged from 25 to 34 in the UK are relying on smart phones for managing their everyday needs. The increase in monetary transactions is creating challenges for the companies to create a sustainable atmosphere for smart phone users.
Reference
Ahmed, O.M. and Sallow, A.B., 2017. Android security: a review. Academic Journal of Nawroz University, 6(3), pp.135-140.
Al-Qershi, F., Al-Qurishi, M., Rahman, S.M.M. and Al-Amri, A., 2014, January. Android vs. iOS: The security battle. In 2014 World Congress on Computer Applications and Information Systems (WCCAIS) (pp. 1-8). IEEE.
Bauer, M., Glenn, T., Geddes, J., Gitlin, M., Grof, P., Kessing, L.V., Monteith, S., Faurholt-Jepsen, M., Severus, E. and Whybrow, P.C., 2020. Smartphones in mental health: a critical review of background issues, current status and future concerns. International journal of bipolar disorders, 8(1), pp.1-19.
bleepingcomputer (2022), https://www.bleepingcomputer.com/news/security/malicious-android-apps-with-300k-installs-found-on-google-play/ [Accessed 25 July 2022]
Ceci, L., 2022. Monthly cyber attacks on global mobile users worldwide 2020-2021.[Online].Available at: https://www.statista.com/statistics/1305965/mobile-users-cyber-attacks/.[Accessed 25 July 2022]
Gontovnikas, M., 2021. The 9 Most Common Security Threats to Mobile Devices in 2021.[Online].Available at: https://auth0.com/blog/the-9-most-common-security-threats-to-mobile-devices-in-2021/.[Accessed 25 July 2022]
Ico.org.uk, 2022. Safer Smartphones – a guide to keeping your device secure.[Online].Available at: https://ico.org.uk/media/your-data-matters/documents/1446/smartphone-securityv5.pdf.[Accessed 25 July 2022]
Lonzetta, A.M., Cope, P., Campbell, J., Mohd, B.J. and Hayajneh, T., 2018. Security vulnerabilities in Bluetooth technology as used in IoT. Journal of Sensor and Actuator Networks, 7(3), p.28.
Marczak, B., Scott-Railton, J., Al-Jizawi, N., Anstis, S. and Deibert, R., 2020. The great iPwn: Journalists hacked with suspected NSO group iMessage ‘zero-Click’Exploit.
Statista Research Department, 2022. Share of people using online banking in Great Britain 2007-2022.[Online].Available at: https://www.statista.com/statistics/286273/internet-banking-penetration-in-great-britain/.[Accessed 25 July 2022]
Verdict.co.uk, 2018. 24% of users are unaware of whether smartphone security has been installed.[Online].Available at: https://www.verdict.co.uk/smartphone-security-users-survey/.[Accessed 25 July 2022]
zdnet (2022), available at: https://www.zdnet.com/article/t-mobile-hack-everything-you-need-to-know/ [Accessed 25 July 2022]
Know more about UniqueSubmission’s other writing services:

