Element 010 ASSIGNMENT Sample : CASE STUDY WEB APPLICATION 2022
A1 Injection is the first injection
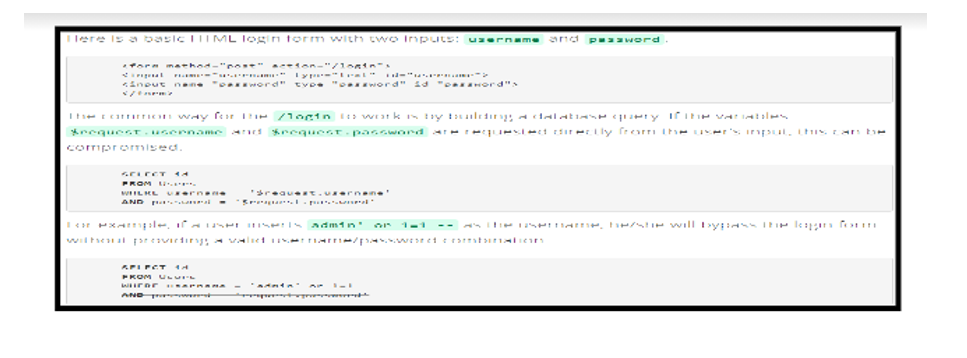
When inaccurate data is provided into a translator as part of an order or inquiry, injections errors, such as SQL, operating system, and LDAP infusions, may occur. Because of the attacker’s unwelcome information, the mediator will be forced to comply with the attacker’s unwelcome orders or to acquire information without authorization.
Agents of Risk-
The infusing vector is not often seen, particularly in asset code. Input mistakes may occur in SQL, LDAP, XPath, or NoSQL queries, operating system instructions, XML parsers, SMTP headers, Lingus headings, and object-relational mapping queries. It is not difficult to discover imbuement issues during a code review session. Attackers may employ scanning and fuzzes to aid them in their efforts to identify absco.
The danger of injection, which is particularly prevalent in older codes, is a frequent kind of safety mistake. SQL inquiries, LDAP queries, XPath queries, NoSQL queries, OS commands, XML parsers, SMTP headers, voice conversations, and ORM queries are all instances of Infusion mistakes, as are other programming languages. During code review, it is not difficult to identify and trace down infusion problems. Scanners and fuzzers are tools that attackers may use to discover charging issues.
It is possible that injecting may result in data shortfalls, downgrading or exposure, a loss of control, or an unwillingness to allow unapproved organizations. The installation will also result in the manager being completely managed as a consequence of the installation. The market outcome is decided by the needs of the system as well as the information that is made accessible to the public.
Mitigation
Use of an API that has been validated to prohibit the translator from accessing or supplying the specified interface, or the use of ORMs, are the two options available.
The stored procedures will always apply to SQL () regardless of whether the stored procedures are written in PL / SQL or T-SQL, or if they generate frightening information regarding EXECUTE IMMEDIATE, or whether they utilize non-friendly data through EXECUTE IMMEDIATE (Bermejo et al., 2020).
Valid or “white” data validation should be used. There is little question that this is not comprehensive protection, since certain programs, such as mobile devices or APIs, need characters that are different from the default. * You may get rid of various personalities by using an enticing linguistic frame as a mediator for any of the more complicated issues that arise.
SQL injection is a kind of programming error.
Several different approaches may be used to prepare for SQL rendering. Using “Structured Statements (Parameterized Questions)” as a defense strategy is one of the most effective methods. This technique enables the designer to see the full SQL code before dragging each border to the query, which is very useful.
Injection of os commands
Instead of sending the order string to a Shell mediator that supports order attachment and redirection, the software may utilize order APIs to transmit a particular cycle across its name and order line arguments. Examples of Java API Runtime include the commands exec and ASPNET, among others.
Injection of the host header
Allowing new line characters to be added to data should be avoided at all costs. When feasible, use strong authorization to protect your data.
Injection of XPath
Having pre-installed needs, such as the installation of SQL databases, is the most effective method to guard against this danger. These queries were pre-arranged before the production of the software to prevent the issue of poor characters that were executed incorrectly. To create a perplexing inquiry, make certain that the characters who should deviate from the foundation are present and well-represented.
CRLF
In addition, the guideline of not trusting consumer input is adhered to. When viruses are killed, all client information is destroyed, and HTTP headers that are frequently accessible to customers are effectively encrypted. This helps to ensure that the CRLF arrangements and their assets are not jeopardized.
Injection of email headers
It is necessary to approve a client contribution before any additional language characters in the offer may be added to another SMTP header to prevent an email header from being sent out. When it comes to approving client input, using a white list of characters that are permitted to be used in SMTP headers is generally the quickest and most efficient method of achieving effective information approval.
Other precautions should be taken.
The usage of a secure API, which prevents the translator from being completely used, offers a structured interface, or avoids the need to use Object Relational Mapping Tools in other places, is another popular approach (ORMs).
- Participate inactively or “registered” work while providing informed permission. The purpose of this is nothing more than complete monitoring, since many systems, such as content areas and flexible APIs, need uncommon characters.
The use of translator-specific software to skip distinct characters is recommended if there are any remaining unique inquiries. Take note that SQL format components include table names, category names, and other information. Business names given to a customer are dangerous since they are undetected. This is an issue that often occurs with reporting systems.
A5 Inadequate access control
Because access control permits techniques, cracked customers are unable to operate without the authorization they have already obtained. In many cases, dissatisfaction leads to the illegal exposure of data, the modification or complete loss of all information, or the prolongation of the business cycle to the greatest extent feasible. The following are some of the most often seen mistakes in access control systems:
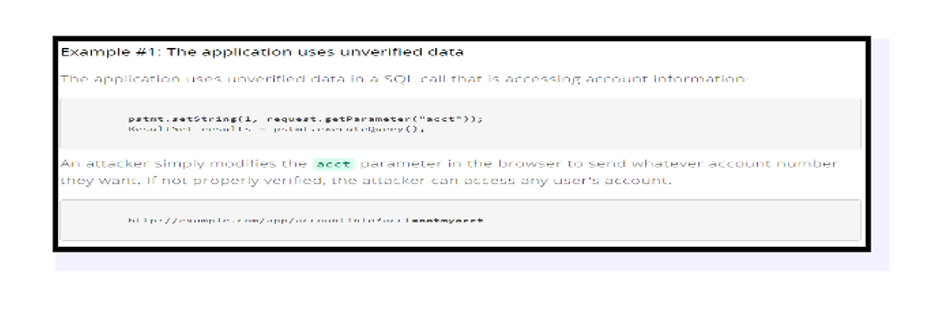
Changing the URL, internal system status, HTML page, or utilizing the custom attack API unit may all be used to prevent access to security tests from being granted.
Metadata abuse, such as re-changing or altering the JSON login access token, or manipulating an encrypted medical or secret field to provide privileges, or breaching JWT’s objection.
- Unauthorized API access is possible as a result of incorrectly formatted CORES.
- As an illegal customer or as a general client with special sites, you may demand that confirmed locations be checked once again on your behalf. With Article, Position, and Remove access restrictions enabled again after being removed earlier, you may use the API.
Danger Agents- Abusers must be able to keep track of who is gaining access. When access restrictions are not present, SAST and DAST devices can detect their absence, but they are unable to verify their functioning when they are there. In certain systems, access control may be understood by human manipulation or, in other instances, by a machine that is not programmed to understand the system.
Because of the absence of planned facilities and the failure of applicants to pass the required tests, security threats are very high in this environment. In most cases, access control IDs are not suitable for use in static or dynamic systems. To examine missing or faulty access restrictions, basic methods include manual verification, impacts such as HTTP process (GET vs PUT, etc.), controller, direct indicators, and other similar methods such as direct indicators.
Attackers who use machine effects pose as clients or managers, or clients who use unique abilities, and they can create, detect, fix, or delete any record. The market impact is defined by the requirements for application and information security, among other things.
Mitigation
When the application is complete, install and renew access to controllable resources, which may include restricting the usage of CORES. • Instead of enabling the client to combine, read, edit, or delete any data, restrict the client’s ability to do so.
- Recording may be accomplished via the use of a database and an access control mechanism.
- Depending on the kind of space, carpet requirements will be tailored to the market for particular uses.
- Disable the transmission of web envelopes to guarantee that the metadata for recording and authenticating documents does not wind up in the webroot.
- Manage log failures; chair alerts when fundamental information is missing (e.g., a rekindled sense of dissatisfaction) (Poston, 2020).
To reduce the harm caused by programmed attack tools, set the API rating and controller access restriction to the lowest possible values.
- When tagging an employee, JWT tokens should be scrutinized for authenticity. Engineers and quality assurance personnel, as well as an effective access control unit and installation inspection, should be put in place.
- Wherever feasible, use a variety of authentication methods to prevent robots, compression of authorization, animal power, and certificate recycling from taking advantage of your system.
- Avoid posting or sending any automatic certificates, particularly to customers who are administrator clients (Ferrara et al., 2019).
Use weak password tests, such as scanning for new or modified passwords in comparison to the 10,000 worst-case passwords, to identify potential security risks.
- By Section 5.1.1 of NIST 800-63 B, the length of the password and the difficulty of switching and turning should be adjusted by modern, key evidence-based techniques such as remembered or other modern, key evidence-based ways.
This was accomplished by targeting the list of accounts using the same principles for all results and therefore strengthening the authentication registration process, authorization renewal process, and API methods.
- The point of infringement or the progressive delay in logged-in login attempts after the point of infringement. Include all of your disappointments and mentors who are ready to be recognized with a diploma, animal power, or a distinct attack in your campaign.
- Use the staff side, which is secure and works for the conference master, who creates another odd meeting ID with a high degree of entropy after logging in. The URL should not include the IDs of the meetings. Ids should also be safely kept and destroyed after logging, idle time, and indirect breaks, among other things.
A7 Invasive Cross-Site Scripting
Cross-Site Scripting (XSS) is a kind of intrusion that allows malicious documents to be sent to secure sites under any conditions at all. When an attacker uses a web system to deliver malicious code to certain end customers, it is common for the attacker to get as near to the customer as possible; this is known as an XSS attack (Li, 2020).
It is typical to encounter flaws that enable these assaults to be fruitful when a web application relies on client commitment without thoroughly testing it or placing it into a lucrative harvest. In certain cases, the victim may be able to utilize XSS to send a malicious email to another client (Hamam and Derhab, 2021). Certainly, the liquid elements that will be used by the world’s first consumer finishing software are familiar to the program’s developers.
That material from downloaded sources, any administrations, contact tokens, or other personally identifiable information are deleted from the framework that maintains and runs that web page or inaccessible item, and the content is no longer accessible. They may also utilize this material to build HTML page devices by combining it with other content.
Vulnerabilities
An XSS (Cross-Site Scripting) attack occurs if the following occurs: data is received from an untrustworthy source, typically a web-based system.
Information is given with relevant information transmitted outside of the online client without any verification of potentially dangerous material to the web client.
However, a malicious item transmitted from an Internet browser may also include HTML, Flash, or any other kind of code that a product may employ in addition to JavaScript encryption. The scope of an XSS-based assault is almost limitless, although it often entails providing sensitive information to the abuser, such as the organization’s name or other data collecting information, to direct the attackers’ attention to the harm done to the web-controlled object.
Example of Coding
As long as you stick with the normal alphanumeric eid string, the code in this example will function flawlessly. When displaying an HTTP response, a web browser may make use of the eid parameter if the value comprises source code and meta-characters, as described above.
At first sight, this does not seem to be an apparent typographical error. True risk exists in the fact that a gate crasher may establish up a malicious URL and utilize emails or social media to entice people to visit the URL’s organization. When victims click to connect, malicious items appear on their computers and attempt to access them via an unstable web system. The XSS that has been deployed is believed to be a method of fooling unstable web apps.
Mitigation
The OWASP XSS Prevention Cheat Sheet is a summary of the most important XSS protections.
There is also evidence that one has weakened HTTP TRACE consistency across all website administrators. Even if the document. a cookie is disabled or rejected by the client, the victimizer may collect clinical data by using JavaScript to acquire information. A customer delivers harmful material to an organization, and another customer taps the connection and begins a low-effort HTTP Trace call, which collects client and executive information from the representative, then transmits it to the retaliator, who obtains managerial information.
This may be easily remedied by disabling HTTP TRACE support for all website administrators on the network.
Several security mechanisms, including cross-border planning and XSS implementation, have been created as part of the OWASP ESAPI project and are now accessible in a variety of languages. OWASP WebGoat project planned project (Shoel et al., 2018) includes Cross-Site Scripting courses and coding skills as well as other security-related topics.
References
Bermejo Higuera, J.R., Bermejo-Higuera, J., Sicilia, J.A., Cubo Villalba, J. and Nombela Pérez, J.J., 2020. Benchmarking Approach to Compare Web Applications Static Analysis Tools Detecting OWASP Top Ten Security Vulnerabilities.
Ferrara, P., Mandal, A., Cortesi, A. and Spoto, F., 2019. Static Analysis for the OWASP IoT Top 10 2018. Proceedings of SPIoT’19.
Hamam, H. and Derhab, A., 2021. An OWASP Top Ten Driven Survey on Web Application Protection Methods. In Risks and Security of Internet and Systems: 15th International Conference, CRiSIS 2020, Paris, France, November 4-6, 2020, Revised Selected Papers (Vol. 12528, p. 235). Springer Nature.
Li, J., 2020. Vulnerabilities mapping based on OWASP-SANS: a survey for static application security testing (SAST).
Poston, H., 2020. Mapping the OWASP Top Ten to Blockchain. Procedia Computer Science, 177, pp.613-617.
Sϕhoel, H., Jaatun, M.G. and Boyd, C., 2018, June. OWASP Top 10-Do Startups Care?. In 2018 International Conference on Cyber Security and Protection of Digital Services (Cyber Security) (pp. 1-8). IEEE.
Know more about UniqueSubmission’s other writing services:

