HI6008 Research Project Assignment Sample
Here’s the best sample of HI6008 Research Project Assignment, written by the expert.
CHALLENGES IN CYBER SECURITY FOR BUSINESS
Introduction:
In this present era while the rapid development of technology is supporting the organisations to enhance the operations and activities, then the number of cyber security terrorisations handled by the organisations is also increasing in a substantial way. It has been viewed that cyber security has become a significant issue for the entire business world across the globe.
According to Mednieks et al. (2012), the cyber security threats with the reputational and financial cost of data breaches is creating a considerable headache for the spontaneous business units. It is a proven fact that eliminating the issue is impossible for the business developers, thus, making a robust protection against the threats without hampering the business growth and innovation process is the foremost intention to the leading business organisations (Khouzani et al. 2014).
In this regards, the US government specified that cybersecurity is one of the most severe national and financial safety challenges for every business and country as well (www.mckinsey.com, 2017). Thus, most of the companies are trying to reinforce the cybersecurity competences for developing mitigation strategies against this issue.
In this particular researcher the challenges of the cyber security in business has been critically analysed to aware the board members, so that the developers could protect the firms from this significant issue. Moreover, the proposal is going to address some suitable solutions for protecting the organisations from the cyber security threats.
Project Objective:
• To identify the existing cyber security challenges in the business world
• To analyse the impact of the cyber security challenges on the business environment
• To evaluate the relationship between the current cyber security threat types and the business environment
• To recommend suitable alternatives to resolve the challenges and security issues for protecting the business environment
Project Scope:
The current study intends to investigate the cyber security challenges for the business world. In this regards, a critical analysis has been conducted to scrutinise the importance of technology and its innovative means. On the other hand, the researcher has measured the security threats in the software application, electronic external gadget, hardware devices and the other essential data storage devices used by the companies to store the unique and important data.
Thus, the current study has a scope for the business leaders to be aware from the cyber security threats in the respective organisations. Furthermore, the study has strained to provide some suitable alternatives so that the developers and business leader could fix the security issues. It is expected that the scope of the project could enable the business entrepreneurs in comprehending the security risks and threats comes from cyber security challenges in this digital age.
Literature Review:
The existing cyber security challenges in the business world
Ransomware
Ransomware usually prevents the users from retrieving vital information and data from the computer and network system until an unethical payment is being made. Supporting the fact Kennedy (2015) asserted that unlike the malware, ransomware does not steal information or data. It actually holds its confined by encrypting the data, files and then showing a ransom note on the screen of the victim. In order to cyber-extortion and threat eradication, it demands for a payment from the victim.
Barrera et al. (2012) cited that this specific cyber threat is existed for last 20 years, but now it has been evolved to create severe threats for the business world. In 2017, the global attack of ransomware has been faced by the companies from Europe, India and Russia (www.hindustantimes.com, 2017).
Hacktivism
The threat of hacktivism reflects that a huge number of public are trying to break into the computer systems for the charge of administrative or social based reasons. Considering the opinion of Khouzani et al. (2014), these types of attacks are even more destructive than as the attack of hacktivists try to make a negative statement against the firm. As a result, the reputation or brand value of the firm is smashed in front of the public.
In addition, there is another significant security concern if the hacktivists can override security system mechanism by any chance (Powar and Meshram, 2015). Consequently, the published documents by the hacktivists may create the national security risks for a country as well.
The impact of the cyber security challenges on the business environment
Financial Loss
A successful cyber-attack can be a major cause of financial loss for an organisation. The theft of corporate information and financial information like bank details, card details, account details can make adverse impact on the smooth operation of a firm. Adding to this, Mednieks et al. (2012) defined that the theft of money of the customers, suppliers, client and organisation itself made the situation more crucial for the surviving of the organisations.
Holla and Katti (2012) cited that the trading disruption such as inability to carry out the online transaction can be a loss for the business persons. Furthermore, the businesses which have faced cybersecurity breaches could need to invest more money for repairing the affected system, devices and network.
Reputational Damage
It is known to all that a cyber-attack can damage the business reputation and grind down the faith of the customers from the affected brand. The reputational damage can also lead to loss of sales, profitability, and loyal customers as well (Gajjar and Parmar, 2009). It has been viewed that reputational damage from cyber-attack can make a negative impact on the suppliers and affect the good relationship with the investors, partners, clients, stakeholders and the other business entities.
Legal consequences
The Data Protection Act needs to manage the security of the business data. If this data is inadvertently or intentionally conceded, then, it proves that the organisation is failed to provide suitable security measures to protect the data (Bernik and Prislan, 2011). As a consequence, the management of the firm needs to face penalties and governing consents to start the operations again.
The relationship between the current cyber security threat types and the business environment
It has been evident that most of the intentional leakages has been occurred from the discontented employees’ side. According to the view of Broadhurst (2013), the blunders including misplaced data, files, portable storage devices and laptops is the main reason of escaping information from the inside of the organizations. As per the 2010 Verizon Data Breach Investigations report found that almost 60% of data breaches have been occurred from the organisation’s inside (Holla and Katti, 2012). Therefore, the companies need to be more attentive about the person who has permission to access the data.
Recommended suitable alternatives to resolve the challenges and security issues for protecting the business environment
Cyber Incident Response Plan and Employee Reporting Mechanisms
The organisation has to adopt a reporting mechanisms so that the CCO (cyber security officer) is quickly guided all the defending person to take a rapid action (Kennedy, 2015). Hence, all employees of the firm could require to be conscious about the possibility of cyber-attacks. Thus, a Cyber Incident Response Plan is essential for every organisation to prevent this kind of attack.
Employing a new business-driven cybersecurity model
As per the analysis of the past scholars, inadequate protections would result in the damage of acute data, but excessively rigorous controls can get in the means of doing business or have additional contrary possessions. In this regards, Khouzani (2014) mentioned that the organisation need to use some intelligent constraints to protect the corporate data by employees, customers and also business partners working in the network system. Thus, a business-driven cybersecurity model is required to offer resiliency (Powar and Meshram, 2015). In order to increase flexibility, a highly proficient and resolute security system model is required to alert all the concerned personnel before the attack.
Research Questions/ Hypothesis:
• What is the existing security threats found in the business world?
• What is the impact of the cyber security challenges on the business environment?
• How the relationship between the current cyber security threat types and the business environment can be evaluated?
• What are the suitable alternatives to resolve the challenges and security issues for protecting the business environment?
Hypothesis:
H0: Cybersecurity challenges is a bigger issue for the business world
H1: Cybersecurity challenges is not a bigger issue for the business world
Research Design and Methodology:
Qualitative research:
In order to accomplish the project, face to face interview need to be used. To do so, 4 IT managers of the organization need to be considered. However, these samples are selected with the help of purposive sampling. Therefore, probability sampling is taken into consideration by the examiner while completing this research. Apart from this, the collected data is attained through open end questionnaire framed as per the objectives and then it is linked with the pre-mentioned literatures.
However, such a method is used in order to attain objective related as well as unbiased results. Only then, it would be extremely reliable and authentic in all regards. And the researcher would also become able to analyse the challenges of utilising cyber while maintaining the business functions. And in which ways, the challenges present a negative impact over the prosperity and image of the firm.
But, these information needs to be restored and preserved in an effective way so as to reduce its detrimental impact. Contrary to this, Kumar (2013) denoted that failure to attain accurate facts might reduce the exactness of the project and it would hamper its success effectively.
Quantitative research
Along with qualitative method, quantitative approach is also utilised. Here, a sample size of 60 employees of the business organization is to be taken. However, the sample size may not be less than 35, then it would result in an ethical issue. This is because, the responses would be entirely biased in nature and it would be extremely problematic for the examiner.
On the other, probability sampling is used. With the help of simple random sampling, the users of the project are selected for the accomplishment of the responses. Then, the obtained answers are evaluated with the use of MS excel and percentage value system.
Then the responses are presented through graphs and charts so as to analyse its essence. In what ways the challenges of cyber security effect the prospects of the business firms in the coming age may be determined with face to face interview system. Closed ended questionnaire is designed as per the objectives so as to scrutinise the views and ideas regarding cyber security.
Then these are examined with the help of data triangulation method. Moreover, the data and facts obtained need to be reliable and valid so that it would be utilised for the future comparative study. And unbiased facts may prove useful for the proper identification of varied aspects of cyber security challenges within firms working in this current scenario.
In contrast, it is determined that inadequate attainment of data might prove problematic and disturbing for the examiner and the project may not prove advantageous for the future (Kothari, 2014).
Other than this, to complete the project, positivism philosophy, deductive approach and descriptive design need to be utilized. Since, the topic is based on evaluation of the challenges from the pre-published articles. Therefore, no inventive exploration of information is useful for the achievement of the study (Bhattacharya, 2015).
Against the latter point, it is stated that use of inductive or interpretivism would be effected while scrutinising any sort of innovative topic. But, it would be relevant for the present research topic.
Research Limitations:
The current research aims to scrutinised the challenges of cyber security faced by the business world. In this regards, the impact of security challenges over the business industry has also been evaluated. Thus, the relevancy of the research outcomes cannot be appropriate for the other industries. In addition, the findings from the cyber security threats are also not applicable to mitigate other terrors of the business. On the other hand, the discussion of general cyber security issues and research findings from it can also be questionable while taking some specific business organisation into consideration. Along with this, as there is no comparative analysis with the other business issues, thus this can be itself a research limitation.
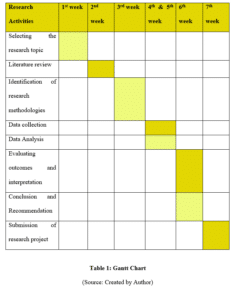
Time Schedule (Research Plan):
A timescale has been provided to portray the time schedule for conducting every activity of the research. In order to demonstrate each procedure uniquely within a stipulated time period, this specific method of Gantt Chart representation has been taken as most appropriate for the current study.
Conclusion:
The current study has assessed the security challenges of cyber system in the business environment. In order to do this, the current security threats like Ransomware, Hacktivism and its effect on the business world has been reported. The impact of cyber security challenges on the firm and its relationship with the organisation has also been analysed. Moreover, a suitable recommendation has been provided by the researcher so that the organisations could resolve the issues of cyber security challenges to protect the respective organisation.
References:
Barrera, D., Clark, J., McCarney, D. and Van Oorschot, P. C. (2012) “Understanding and improving app installation security mechanisms through empirical analysis of android”, in Proc. of the 2nd ACM workshop on Security and privacy in smartphones and mobile devices, 27(3), pp. 80–92.
Bernik, I. and Prislan, K. (2011) “Information Security in Risk Management Systems”: Slovenian Perspective. B. Dobovšek and A.Sotlar (edit.), Varstvoslovje, 13(2), pp. 208-222.
Bhattacharya, D.K. (2015). Research Methodology. Usa: Routledge.
Broadhurst, C.L. (2013), ‘Cybercrime in Asia: trends and challenges’, Springer, New York.
Companies that were hit by global ransomware attack in Europe, Russia and India (15 September 2017) Available at: http://www.hindustantimes.com/world-news/all-the-companies-hit-by-global-ransomware-attack-on-june-27/story KaiWDG64Qqj3I0Sqsl7ULL.html [Accessed: 15 September 2017].
Gajjar, K. and Parmar, A. (2009) “A study of challenges and solutions for cyber security”, Emerging Research in Computing, Information, Communication and Applications, 25(5), pp. 326–334.
Holla, S. and Katti, M.M., (2012) “Software development and its Security”, International Journal of Computer Trends and Technology, 3(3), pp. 486-490.
Kennedy, (2015) “Best practices for wireless network security”. Information Systems Control Journal 2(3), pp. 75-90.
Khouzani, M. H. R., Sarkar, S. and Altman, E. (2014) “A dynamic game solution to malware attack”, 2011 Proceedings IEEE INFOCOM, 33(7), pp. 40-80.
Kothari, C. K. (2014). Research Methodology: Methods and Techniques. Usa: sage.
Kumar, R. (2013). Research Methodology. Usa: Routledge.
McKinsey & Company. (2017). Meeting the cybersecurity challenge. [online] Available at: http://www.mckinsey.com/business-functions/digital-mckinsey/our-insights/meeting-the-cybersecurity-challenge [Accessed 15 Sep. 2017].
Mednieks, Z., Dornin, L., Meike, B. G. and Nakamura, M. (2012) Programming Android: Java programming for the new generation of mobile devices. 2nd edn. United States: O’Reilly Media, Inc, USA.
Powar, S., and Meshram, B. B., (2015) “Survey on Security Framework”, International Journal of Engineering Research and Applications, 3(2), pp. 20-32.
________________________________________________________________________________
Know more about UniqueSubmission’s other writing services:

