Information Security
Data protection by design and default is a technique of Information Security and it contains many policies and procedures that will also include legal activities and also physical and technical controls.
Many companies or industries use this technique to keep their data secured and helps to keep data protected from different security threats and it also provides the greater confidence to the customer or clients.
The chosen global hi tech solution is global hi tech solution to which the details of the Data protection be provided.
Implementation of Data Protection by design and default
This arrangement is for representatives, labourers and contractual workers of the Global hi tech solution.
When handling individual Regulation of General Data Protection intimates all the global hi tech solution for handling, dangers to people and expenses and so forth,) actualize fitting specialized and authoritative measures, for example, pseudonymisation, into such preparing exercises so as to meet the prerequisites of GDPR and ensure the privileges of the information concerned.
The proper measures will well modify from one handling movement to next as well as it will be significant which measures are provided thought toward the beginning of, and for the duration of, the life-pattern of the Global hi tech solution handling of individual information.
This commitment is alluded to as ‘Security by Design’. As a base, such estimates must guarantee that lone individual information which are important for each explicit reason for the handling are prepared and that the individual information isn’t made accessible to an uncertain measure of people without the information subject’s inclusion (Lodge, 2018).
This Policy gives direction on the University’s way to deal with guaranteeing that it inserts protection by plan and protection naturally over the global hi tech solution tasks. And in the occasion the ICO examines that the Global hi tech solution has not satisfied its commitments comparable to security.
The GPDR expects people to set up fitting specialized and authoritative measures to actualize the information security standards and protect singular rights. This is ‘information insurance by plan and as a matter of course’.
Fundamentally, this implies you need to coordinate or ‘heat in’ information assurance into your handling exercises and strategic policies, with the plan level directly with lifecycle.
Recently called as ‘security by structure’, this has consistently been a piece of information assurance law. And the important modification with this is that it is currently a lawful prerequisite.
Information security by configuration is tied in with thinking about information insurance and protection issues forthright in all that you do. It can assist you with guaranteeing that you follow the GDPR’s crucial standards what’s more, necessities, and structures some portion of the emphasis on responsibility.
Information assurance by configuration is eventually a methodology that guarantees you consider security and information insurance issues at the structure period of any framework, administration, item or procedure and afterward all through the entire process.
As communicated by GDPR, it expects the global hi tech solution to: set up suitable specialized as well as hierarchical estimates intended to actualize the information insurance standards; and incorporate shields into the handling with the goal that global hi tech solution meet the necessities of GDPR and ensure the rights.
Generally this implies you need to incorporate or ‘prepare in’ information security into your handling exercises and strategic approaches. Information assurance by configuration has expansive application (Suwannakit, 2019).
Models include: growing new IT frameworks, administrations, items and procedures that include handling individual information; creating authoritative arrangements, forms, strategic approaches and additionally techniques that have security suggestions; physical plan; setting out information activities; or utilizing individual information for purposes.
The fundamental ideas of information insurance by configuration are not fresh. By the term ‘security by design’ global hi tech solutions have existed for a long time. Information assurance by configuration basically embeds the protection by plan method into information law of insurance.
By the Act, ICO bolstered this methodology as it supported global hi tech solution to conform to its information assurance commitments. It is presently a legitimate necessity.
Information security as a matter of course expects global hi tech solution to guarantee that just procedure the information that is important to accomplish your particular reason.
It connects to the key information insurance standards of information minimisation reason confinement. Global hi tech solution need to process some close to home information to accomplish your purpose.
Information insurance as a matter of course implies you have to determine this information before the preparing begins, properly illuminate people and as it were process the information you requirement for your motivation.
It doesn’t expect you to receive a ‘default to off’ arrangement. What the global hi tech solution have to do relies upon the conditions of your preparing and the dangers presented to people.
By and by, global hi tech solution should consider things like: receiving a ‘security first’ method with default setting of frameworks as well as application; guaranteeing global hi tech solution don’t give a fanciful decision to people identifying with information
it will process and not handling individual information isn’t consequently made freely accessible to others except if individual chooses to done it so and giving people adequate management and alternatives to practice the privileges.
Association must setup proper specialized and hierarchical estimates intended to actualize the information insurance standards and protect singular rights. This relies upon Organization conditions (Hansen, 2016).
The important aspect is that Organization considers information insurance challenges from the beginning of handling movement, and embrace proper arrangements and steps that meets the prerequisites of information security by plan and by the default.
A few instances of how Organization can do perform include:
- Limiting handling of individual information
- Pseudonymising individual information at the earliest opportunity.
- Guaranteeing straightforwardness in regard of the capacities and handling of individual information.
- Empowering people to screen the
- Making (and improving) security highlights.
- This isn’t a comprehensive rundown. Consenting to information assurance by plan and as a matter of course may require Organization.
- To do substantially more than the above mentioned. In any case, we can’t give a total manual for all parts of information security by structure and as a matter of course
This direction recognizes the primary concerns for Organization to consider. Contingent upon the handling Organization is doing, Organization may need to acquire master exhortation that goes past the extent of this direction.
The Personal Data Protection Bill commands that associations comprehend the procedure of information stream over the frameworks, by tough information administration.
Bill additionally infers that mistaken or obsolete information be eradicated or refreshed. It is obligatory for all information guardians to agree to these guidelines (Tikkinen-Piri, 2018).
Without dim information revelation, it is difficult t o think about the sort of information an organization has gathered or put away, what the information speaks to, where it is gotten from, where it is put away, how it is being utilized, how its inclination is changing, how it travels through different frameworks, who approaches it and even the nature of the information.
Legitimate administration of dull information is basic for security consistence by all associations in India. Thus, it is suggested that associations hold onto dim information the executives as a fundamental piece of their information administration approaches.
Dim information the executives is significant for every single Indian association which are guaranteeing consistence with existing up and coming security laws in India.
Subsequently, the arrangement of the most delicate component in an information assortment will decide the information order of the whole assortment.
ACOM Data Classifications:
External:
Information expressly or certainly endorsed for dissemination to general society without limitation. It tends to be uninhibitedly circulated without potential damage to the College, associates, or people (Clarke, 2018).
Open information low affectability since by definition there is nothing of the sort as unapproved revelation, yet it despite everything warrants security since the uprightness of the information can be significant.
Internal
Information planned for inward College business utilize just with get to confined to a particular workgroup, office, gathering of people, or associates with an authentic need. Inner information are commonly not made accessible to parties outside the ACOM people group. Unapproved exposure could unfavourably affect the Colleges, subsidiaries, or people. Interior information for the most part have a low to direct affectability.
Confidential
Profoundly delicate information proposed for restricted, explicit use by a workgroup, office, or gathering of people with a genuine need-to-know. Express approval is needed to get due to legitimate, authoritative, security, or different limitations.
Unapproved exposure could have a genuine unfriendly effect on the business or research elements of the University or associates, the individual security of people, or on consistence with government or state laws and guidelines or University contracts. Classified information have an elevated level of affectability.
Exclusive Data
Classification of information gave to or made and kept up by ACOM for the benefit of an outsider, for example, an organization or government office, will differ contingent upon legally binding understandings as well as significant laws or guidelines.
The characterization and security guidelines for restrictive information claimed by the outsider will be characterized by the outsider. Restrictive information claimed by ACOM must be grouped and ensured by ACOM’s information order arrangement and security norms.
People overseeing or getting to restrictive information are liable for consenting to any extra prerequisites and security strategies and methods indicated by the outsider proprietor. Restrictive information incorporate information arranged by the central government as Classified National Security Information (private, mystery, top mystery).
Data Processing Impact evaluation
At the point when a controller gathers, stores, or uses individual information, the people whose information are handled are presented to dangers.
These dangers can go from individual information being taken or coincidentally discharged and utilized by lawbreakers to mimic the person, to stress being caused to people that their information will be utilized b for obscure purposes (Li, 2018).
A DPIA depicts a procedure intended to distinguish dangers emerging out of the handling of individual information and to limit these dangers as far and as ahead of schedule as could reasonably be expected.
DPIAs are significant apparatuses for invalidating danger, and for exhibiting consistence with the GDPR. This direction expect that a DPIA will be led for a characterized venture, instead of for an association’s tasks overall. A specific capacity of your association, or a program of changes to your association’s tasks all in all, might be seen as a venture.
Manage. Characterize venture data usage methods, report data misfortune occurrences, and fix up episode action capacity to show the activities which remediate infringement. Data misfortune avoidance is not only an creative issue but it’s additionally an approach and arrangement the executives issue.
Find. Features the affectability of large business data, make a store of touchy data, find delicate data any place but put away, and the oversee data cleanup. It incorporates examining and reviewing data very still or then again put away on the endpoint to storage, privacy, or migrate that data.
Monitor. Examine the utilization of delicate data use examples, and addition venture perceivability.
Ensure. Implement security arrangements to proactively make sure about data as well as keep it an undertaking. This security of delicate data across endpoint, the system, and the capable frameworks might to incorporate ensuring data very still with program encrypting, separate, and also expulsion.
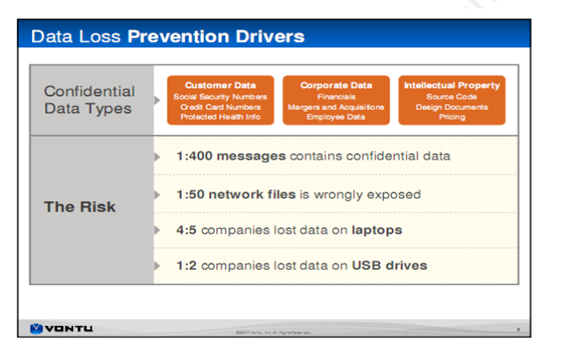
Figure 1: Data Loss Prevention (Readshaw, 2016)
Privacy Enhancing Technologies
Innovation can help information controllers’ consistence with information security standards and can go further to enable people, giving them simpler access to and command over data about them and permitting them to choose how and when these data will be uncovered to and utilized by outsiders (Harborth, 2020).
The best security for people is the point at which their own data is possibly gathered when required.
Protection improving advancements have customarily been restricted to ‘pseudonymisation apparatuses’ which are programming and frameworks that permit people to retain their actual character from those working electronic frameworks or offering types of assistance through them, and possibly uncover it when totally fundamental.
These innovations help to limit the data gathered about people and incorporate mysterious internet browsers, master email administrations, and computerized money.
Security improving innovations ought to anyway not be restricted to instruments that give a level of secrecy to living people as they ought to incorporate any innovation that ensures or upgrades a person’s protection, including encouraging people’s entrance to their privileges under the Data Protection Act.
In April 2019, UpGuard security scientists uncovered that two outsider created Facebook application datasets were presented to the open web.
One database started from Cultural Colectiva, a Mexico-based media organization, and tipped the scales at 146 gigabytes with in excess of 540 million records specifying remarks, likes, responses, account names, Facebook IDs and that’s just the beginning.
The other outsider application, “At the Pool,” was presented to the open web by means of an Amazon S3 basin, state the analysts. This database reinforcement contained sections for client data, for example, username IDs, companions, likes, music, motion pictures, books, photographs, occasions, gatherings, registration, interests, passwords and that’s just the beginning
.Information break trackers have discovered two Amazon cloud servers putting away more than 540 million Facebook-related records that host been gathered by two third-gathering organizations (Lozada, 2020).
The quantity of influenced clients is accepted to be in the scope of millions and several millions. The two servers have been found not long ago by security analysts from UpGuard, a California-based digital security firm spent significant time in recognizing information spills.
The primary server contained the vast majority of the information, and had a place with Cultural Colectiva, stage working across Spanish speaking Latin America nations.
With the size of the 146GB, AWS servers put away more than 540 million records enumerating client account names, Facebook IDs, remarks, preferences, responses, and other information utilized for breaking down online networking channels and client communications.
The second AWS server put away information recorded by the “At the Pool” Facebook game. This included subtleties, for example, the Facebook client ID, a rundown of Facebook companions, likes, photographs, gatherings, checkins, and client inclinations like motion pictures, music, books, interests, and other, alongside 22,000 passwords.
“The passwords are apparently for the ‘At the Pool’ application as opposed to for the client’s Facebook account, however would put clients in danger who have reused a similar secret word across accounts,” UpGuard said(Ayaburi, 2020).
As per this, a Mexico-based media organization called Cultura Colectiva was liable for the greatest hole. It uncovered hundred gigabytes of Facebook customer data, including account names, ID and regarding remark and responses to post. It’s hazy count of individual customers had data uncovered.
Loss to the Global hi tech solution
Individually, the application called the Pool uncovered the databases which seemed to incorporate data about customer ID, companies, images and registrations, just like unprotected Facebook password for twenty thousand customers.
The applications which were insisted to assist individual with meeting up for exercises closed in 2K14.

Making sure about the principal defective server was a bad dream, UpGuard said in an episode report distributed today. Cultura Colectiva never reacted to the specialists’ messages, and Amazon, notwithstanding getting notices from UpGuard about the cracked servers, didn’t bring the flawed AWS server down, regardless of whether the information presentation was self-evident.
It was simply after UpGuard advised a Bloomberg journalist of the issue, who thusly reached Facebook, that Amazon mediated to bring down the server – at Facebook’s solicitation, a Facebook’s representative told ZDNet.
Then again, the second Amazon server, the one putting away the At the Pool application information, was brought down even before UpGuard got an opportunity to recognize and contact the organization behind the Facebook game.
“It is obscure if this is a fortuitous event, if there was a facilitating period slip by, or if a party in question got mindful of the presentation around then. In any case, the application is not, at this point dynamic and entire signs point to the parent organization that have closed down.
These 2 new breaks exposes the significant problem that the Facebook is at present confronting. The organization has perhaps the best group of digital security specialists, adds security-related highlights to client records and its IT framework all the time, and frequently open-sources a considerable lot of its inside security apparatuses so different organizations can utilize them also.
The informational collections change in when they were last refreshed, the information focuses present, and the quantity of special people in each. What integrates them is that the two of them contain information about Facebook clients, depicting their inclinations, connections, and collaborations, that were accessible to outsider engineers.
As Facebook faces investigation over its information stewardship rehearses, they host put forth attempts to lessen third get-together access.
Be that as it may, as these exposures appear, the information genie can’t be returned in the jug. Information about Facebook clients has been spread a long ways past the limits of what Facebook can control today.
Join that abundance of individual information with capacity advances that are frequently misconfigured for free, and the outcome is a long tail of information about Facebook clients that keeps on spilling.
UpGuard Vendor can limit the measure of time the association spend evaluating relevant and outsider data security controls via mechanizing seller surveys and giving merchant poll formats. It can help persistently screen sellers’ outside security controls and give an impartial security rating. It can likewise help in a split second benchmark
present and potential merchants against their industry, so it can perceive how they stack up (Landwher, 2019).
For the appraisal of the data security controls, UpGuard Breach Sight can screen association for seventy security controls giving a straightforward, straightforward security rating and consequently recognize spilled certifications and information exposures in S3 cans, Rsync servers, GitHub repos and then some.
The significant contrast among UpGuard and other security evaluations merchants is that there is extremely open proof of our aptitude in forestalling information breaks and information spills.
Three programming blemishes in this frameworks permitted developers to break into customer accounts, that includes those of the top officials Mark Zuckerberg and Sheryl Sandberg, as indicated by 2 individuals acquainted with the examination yet not accessed to talk about it freely.
Once in, the aggressors should have accessed applications like Spotify, Instagram and many others that give clients an approach to sign into their frameworks through Facebook.
The product bugs were especially clumsy for an organization that invests heavily in its building: The initial 2 were given by an web apparatus to improve the security of clients.
The 3rd was given in 2017, july by the instrument to effortlessly change recordings. It informed it fixed the issues and told implementation authorities. Global hi tech solution authorities didn’t have the idea about the personality and the origin of the aggressors, nor they completely examined the extent of the attack or if specific customers were focused on.
Examination is in its initial stages. The global hi tech solution informed those imperfections are exacerbated by a defect in Facebook’s video-sharing program for festivities, a object highlight which was performed in 2017, July.
The defect permitted the attackers to take access tokens which is advanced keys that permits to a record. But it was not clear when the attack occurred, yet it is like to have happened after the video-sharing program was done, Facebook said.
The global hi tech solution rules was in excess of ninety million customers to log out early Friday, a security measure was handled when data have been examined. The developers additionally attempt to capture individuals’ private info, that includes names, gender and past neighbourhood, from its frameworks, Mr. Rosen said.
The organization couldn’t decide the degree of the assailants’ entrance to outsider records. Rather than going about as an individual gathering, privacy colleagues presently perform intimately with the groups over the global hi tech solution.
The move, the global hi tech solution stated, is a pressure to insert privacy over each progress of Facebook component improvement. Some portion of that exertion has been to brace Facebook against assaults on its system in anticipation of the midterm races (Brainerd, 2019).
It has gone through many days setting up fresh framework to remove such attacks, and has just controlled many parts accepted to associated with races in many countries and different nations.
All things considered, the as of late examined break is an update which it is outstandingly hard to gather that make sure about a frameworks that has more than two billion customers everywhere throughout the globe and that interfaces with a many number of administrations.
The bugs that empowered the assault have since been fixed, as per Facebook. The organization says that the aggressors could see everything in a casualty’s profile, in spite of the fact that it’s as yet hazy if that incorporates private texts or if any of the information was abused.
The a major aspect of fix, the Facebook consequently logged out ninety million Facebook clients from its records bookkeeping both for the fifty million which Facebook knows were influenced, and extra forty million that conceivably might have been. Later, it likewise affirmed the outsider destinations that those clients.
Lodge, T., Crabtree, A. and Brown, A., 2018, October. IoT App Development: Supporting Data Protection by Design and Default. In Proceedings of the 2018 ACM International Joint Conference and 2018 International Symposium on Pervasive and Ubiquitous Computing and Wearable Computers (pp. 901-910).
Suwannakit, M., 2019. Aurelia Tamò-Larrieux, Designing for Privacy and its Legal Framework: Data Protection by Design and Default for the Internet of Things. International Data Privacy Law.
Hansen, M., 2016, August. Data protection by design and by Default à la European General Data Protection Regulation. In IFIP International Summer School on Privacy and Identity Management (pp. 27-38). Springer, Cham.
Jasmontaite, L., Kamara, I., Zanfir-Fortuna, G. and Leucci, S., 2018. Data protection by design and by default: Framing guiding principles into legal obligations in the GDPR. Eur. Data Prot. L. Rev., 4, p.168.
Hoel, T., Griffiths, D. and Chen, W., 2017, March. The influence of data protection and privacy frameworks on the design of learning analytics systems. In Proceedings of the seventh international learning analytics & knowledge conference (pp. 243-252).
Tikkinen-Piri, C., Rohunen, A. and Markkula, J., 2018. EU General Data Protection Regulation: Changes and implications for personal data collecting companies. Computer Law & Security Review, 34(1), pp.134-153.
Clarke, S., 2018. The role of automated data discovery in a GDPR program. IQ: The RIM Quarterly, 34(4), p.28.
Li, P., Li, J., Huang, Z., Gao, C.Z., Chen, W.B. and Chen, K., 2018. Privacy-preserving outsourced classification in cloud computing. Cluster Computing, 21(1), pp.277-286.
Bieker, F., Friedewald, M., Hansen, M., Obersteller, H. and Rost, M., 2016, September. A process for data protection impact assessment under the european general data protection regulation. In Annual Privacy Forum (pp. 21-37). Springer, Cham.
Readshaw, N.I., Ramanathan, J. and Bray, G.G., International Business Machines Corp, 2016. Method and apparatus for associating data loss protection (DLP) policies with endpoints. U.S. Patent 9,311,495.
Harborth, D., Pape, S. and Rannenberg, K., 2020. Explaining the Technology Use Behavior of Privacy-Enhancing Technologies: The Case of Tor and JonDonym. Proceedings on Privacy Enhancing Technologies, 2, pp.111-128.
Brainerd, C., 2019. Before data breaches are discussed in detail, we first must first define what data breaches are and how they happen. In short, a data breach is a security incident in which information is accessed, and in some cases made public, without authorization. The most common ways 3 attackers get access to this data without authorization are exploiting system vulnerabilities, weak.
Venturini, T. and Rogers, R., 2019. “API-Based Research” or How can Digital Sociology and Journalism Studies Learn from the Facebook and Cambridge Analytica Data Breach. Digital Journalism, 7(4), pp.532-540.
Landwher, C., 2019. VIEW MORE ISSUES Videos Home/Magazine Archive/February 2019 (Vol. 62, No. 2)/2018: A Big Year for Privacy/Full Text. Communications of the ACM, 62(2), pp.20-22.
Ayaburi, E.W. and Treku, D.N., 2020. Effect of penitence on social media trust and privacy concerns: The case of Facebook. International Journal of Information Management, 50, pp.171-181.
Ayaburi, E., Andoh-Baidoo, F. and Lee, J.U., 2020, January. Post Data Breach Use of Protective Technologies: An Examination of Users’ Dilemma. In Proceedings of the 53rd Hawaii International Conference on System Sciences.
Lozada, L.M., 2020. The (Possibly) Injured Consumer: Standing in Data Breach Litigation. St. John’s Law Review, 93(2), p.6.


