Intrusion Detection And Prevention Systems Assignment Sample Through Experimental Research
Slide 1: INTRUSION DETECTION AND PREVENTION SYSTEMS THROUGH EXPERIMENTAL RESEARCH
Slide 2: Outline
- The experimental research can also be accomplished with the help of used data which can describe the “network environment” in great and possible extent.
- The concept of network security monitoring system is the concept of collection of escalation, analysis and collection of the warnings and indications.
SN: The concept of network security monitoring system is the concept of collection of escalation, analysis and collection of the warnings and indications that can detect and respond to the intrusions or vulnerable in the computing system. Here in this research an intrusion detection and also a prevention system is implemented with the help of an experimental research. The experimental research can also be accomplished with the help of used data which can describe the “network environment” in great and possible extent. This project basically involves the comparison and evaluation of the “two Intrusion Detection and prevention Systems” with the help of conducting the experimental work which involves the testing procedure of at least two IDPS and the performance are evaluated and compared on the basis of security monitoring techniques.
Slide 3: Introduction
- Secure information transmission is very important in the present scenario for healthy reputation and financial status.
- Risks and chances of malicious involvement are increasing.
SN: In various organizations the process of securing information and transmission is considered as one of the important tasks in the present era to maintain a healthy reputation and financial status. The main chances and risks to the malicious involvements are also increasing that can have a potential possibilities to the deliberate unauthorized structure. It can help to access the information, manipulate the information and also render the specific system in the form of unusable and unreliable data sources.
Slide 4: Introduction
- Detects attacks as soon as possible and takes appropriate action.
- It is a reactive rather than a pro-active agent.
SN: IDS or Intrusion detection system can also detect some specific attacks and also helps to take the appropriate actions. It does not take the preventive measures when the malicious attacks are detected. IDs are mostly reactive than proactive agents. This also plays an important role in the platform of suspicion and investigation. In various reports it can be found that this is considered as the most popular way for detecting intrusions with the help of auditing data which is generated with the help of the operating system.
Slide 5: Project Goals
- This total project is done on the basis of an experimental research where computer fraud and the importance of telecom systems is measured.
- The main aim of this project is to design, evaluate and compare the “two Intrusion Detection and prevention Systems” with the help of conducting the experimental work.
- Discussion on proposed hybrid IDS
SN: The main aim of this project is to design, evaluate and compare the “two Intrusion Detection and prevention Systems” with the help of conducting the experimental work which involves the testing procedure of at least two IDPS and the performance are evaluated and compared on the basis of security monitoring techniques. This total project is done on the basis of an experimental research where computer fraud and the importance of telecom systems is measured. Basically, here in this research an intrusion detection and also a prevention system is implemented with the help of an experimental research.
Slide 6: Implementation system and technology
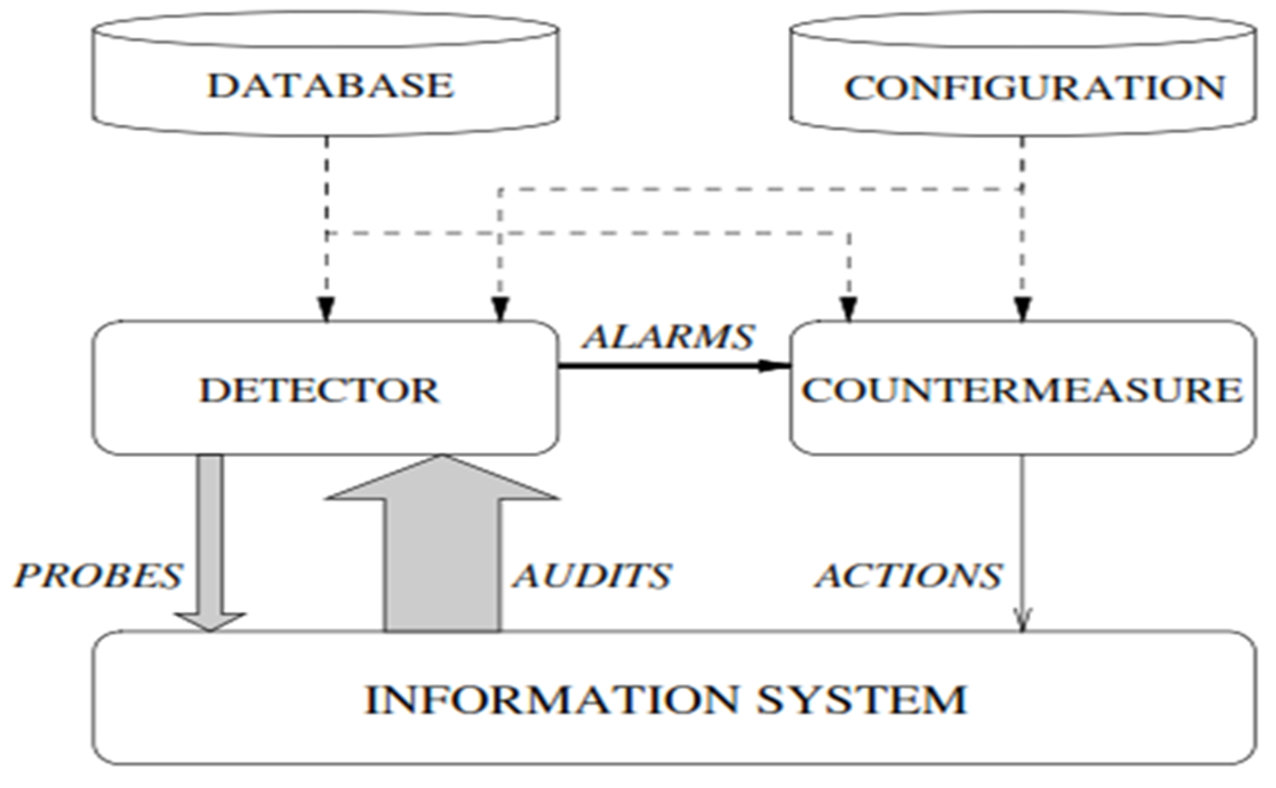
SN: This above image basically shows the implementation process of the intrusion detection system with the help of database management system. From various reports it has been found that the database system is used to analyze the actions and countermeasures are done on the basis of the action. The problems generated here can load as the input and the detectors can also investigate the data and show the vulnerability in the operating or information system. Proposed hybrid IDS mainly implemented here which use the “signature and anomaly information together” and can offer a better detection.
Slide 7: Design method
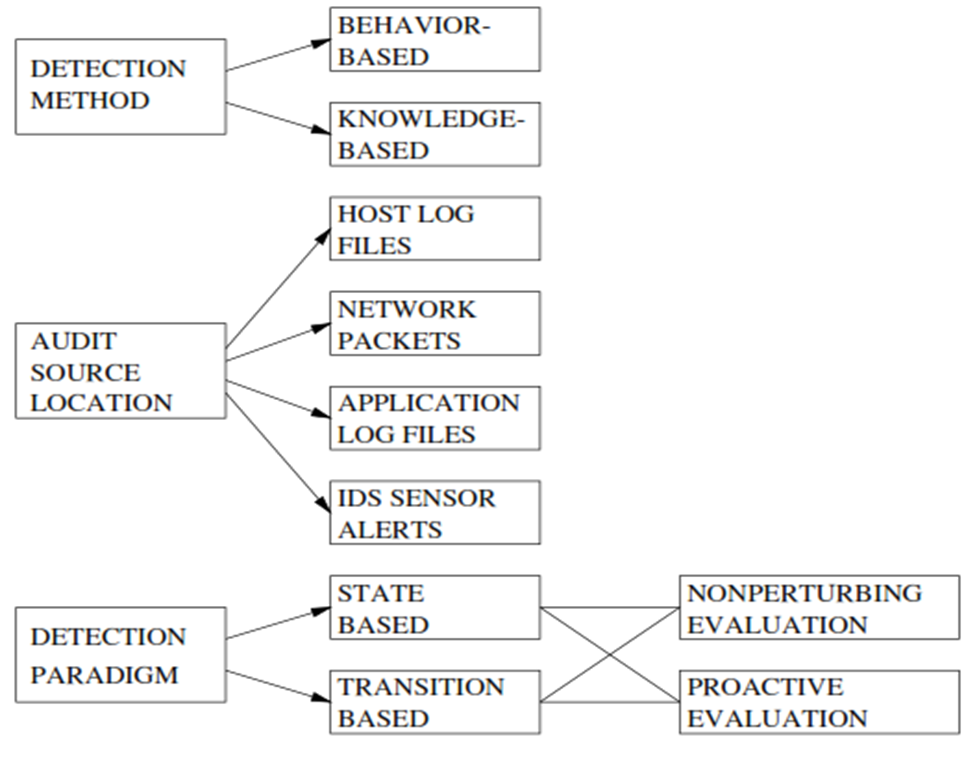
SN: Above image shows the designing method or the taxonomy of the system. In this image it can be seen that the detection method mainly involves two important characteristics which is knowledge-based and behavior-based analysis. Various files are taken for selecting the audit source location and the application log files are taken to detect the paradigm. This picture mainly helps to understand the main concept of IPS and IDS and the important category which are measured here is based on the signature information which can generate the false detection system. Various models and features are used here to show the system activities and system architecture.
Slide 8: Requirements of the implementation
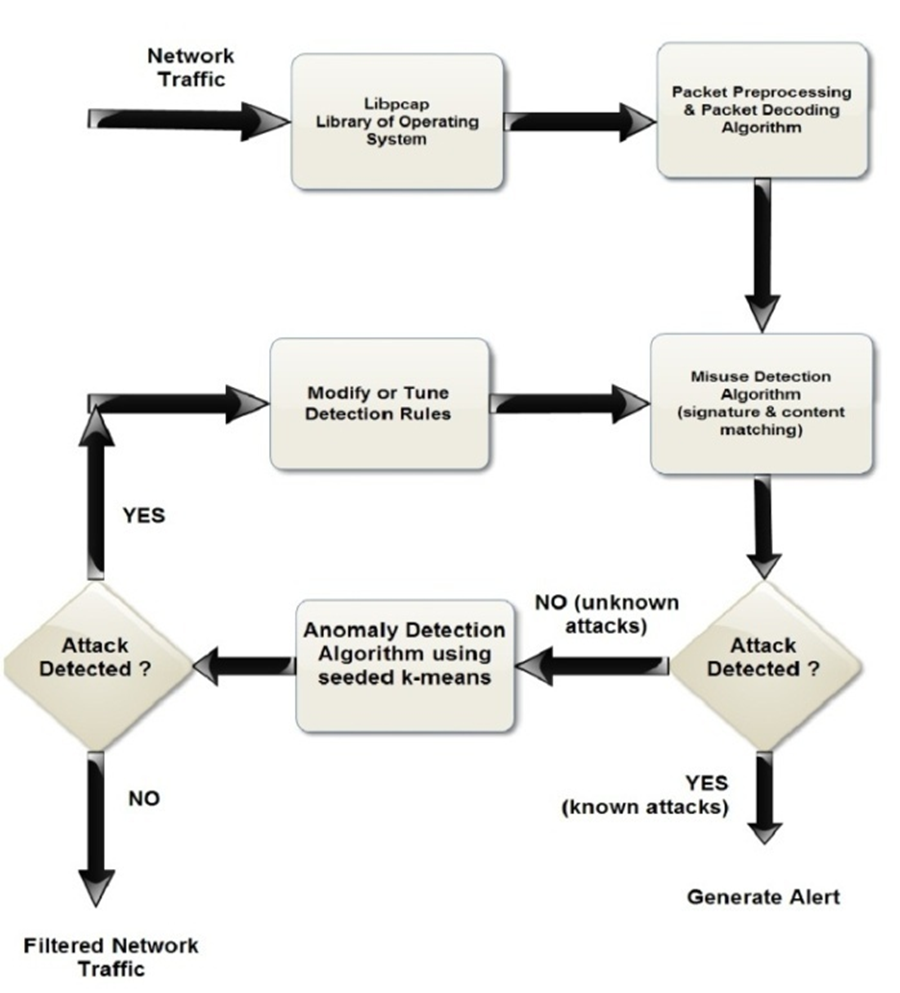
- Perspective of an algorithm
- Perspective from system architecture
- Perspective from modelling
- Perspective from deployment
SN: The main components of the intrusion detection system are considered as the two important perspectives which are considered as:
- Perspective of an algorithm: Models and features are used here to take and capture the intrusion evidence.
- Perspective from system architecture: Various components like responses, alarm generations, decision engines, knowledge-based and audit data processors are taken to analyze the system.
- Perspective from modelling: Misuse detection which is used in signature-based modeling and anomaly detection which is used in statistical-based modeling are srf as deployment.
- Perspective from deployment: Host-based and network-based modelling are used to control and monitor the network traffic and computer process system and technology.
Slide 9: Advantage
- Declarative Specification
- Multiple event streams
- Portability
- Real-time capabilities
- Pattern Matching
SN: The main advantage of the detection system is that the main network can also be used as the unprotected state in the time of building the system profile. On the other hand, if the main method or malicious activity is seen in the normal traffic analysis the system will never send an anonymous alarm. Addition to this the false positive structure can also become cumbersome with the setup. Normal usage to the process of checking an email after a specific meeting and sending a potential signal to the alarm.
Slide 10: Types of Detection system
SN: Several systems are present for detecting anonym’s behavior of the client server such as Expert system, Keystroke monitoring, Model based intrusion detection, State transition system analysis and pattern matching. Most advanced technology and antonym detection is model based intrusion detection system.
Slide 11: Intrusion Detection Approaches
SN: In order to detect intrusion aspects, some approaches are taken in consideration such as features, analysis and deployment.
Features: Required depositions are being extracted from audit data.
Analysis approach: Quantifying all the required information from the audit.
- Detection of data misuse
- Detection of anomaly
Deployment: Deployments are two types in this case.
- Network based: Monitoring the traffic of the network.
- Hot based: Monitoring the process of the computer.
In this detection system a particular algorithm is used for detecting anonymous activity. This algorithm focuses on traffic data and finds similarity in the traffic source addresses. But the fact is in this algorithm the traffic address is mentioned initially and the algorithm is unable to detect any new address. Therefore manual observation is required in such cases.
Slide 12: Used Algorithms
SN: Several algorithm models are present to prepare an instruction detection system. For developing the IDS software and preventing all the required information from anonym’s behavior, few nearest combinations are present such as K-nearest neighbor (KNN), K- Mean Clustering, Support vector machine (SVM), Ensemble Methods, Artificial Neural Network (ANN), and Fast Learning Network etc.
Slide 13: Conclusion
SN: The detection algorithm for hybrid solution can be developed with the combination of signature based attribute and detection algorithm based on anomaly. For accessing all the required information and performance development for a better detection system, Snort and seeded k-means are the best algorithms.
Slide 14: References
Journals
Panigrahi, R. and Borah, S., 2018. A detailed analysis of CICIDS2017 dataset for designing Intrusion Detection Systems. International Journal of Engineering & Technology, 7(3.24), pp.479-482.
Tama, B.A., Comuzzi, M. and Rhee, K.H., 2019. TSE-IDS: A two-stage classifier ensemble for intelligent anomaly-based intrusion detection system. IEEE Access, 7, pp.94497-94507.
Yan, B. and Han, G., 2018. Effective feature extraction via stacked sparse autoencoder to improve intrusion detection system. IEEE Access, 6, pp.41238-41248.
Yin, C., Zhu, Y., Fei, J. and He, X., 2017. A deep learning approach for intrusion detection using recurrent neural networks. Ieee Access, 5, pp.21954-21961.
Naik, N., Diao, R. and Shen, Q., 2017. Dynamic fuzzy rule interpolation and its application to intrusion detection. IEEE Transactions on Fuzzy Systems, 26(4), pp.1878-1892.
Vinayakumar, R., Alazab, M., Soman, K.P., Poornachandran, P., Al-Nemrat, A. and Venkatraman, S., 2019. Deep learning approach for intelligent intrusion detection system. IEEE Access, 7, pp.41525-41550.
Kasongo, S.M. and Sun, Y., 2019. A deep learning method with filter based feature engineering for wireless intrusion detection system. IEEE Access, 7, pp.38597-38607.
Slide 15: Thank You
………………………………………………………………………………………………………………………..
Know more about Unique Submission’s other writing services:

