IT SECURITY
Introduction
IT security prevents the access of unauthorized persons or anything to the assets related to any organization such as computers, networks or data. By blocking the access of hackers, it maintains the confidentiality and the integrity of a firm. In this report, a brief description of the security tools provided, that is responsible for providing security to any organization. In this, features of security tools Nmap and Burpsuite discussed. In addition to these, the security tools also check for the intruders. Moreover, it authenticates the users and then grants access to them.
Installation and launch of security tools
Selected security tools are NMap and Burpsuite.
Tool 1: NMap
Pre-requisites
User must have the knowledge of sudo commands
User must be able to launch the command line prompt
Installation of NMap is very easy and straightforward. It just requires a single command [1].
Step 1
The very first step is to check whether NMap installed on the computer or not. If not installed then, by entering the following command, NMap can be installed on Linux.
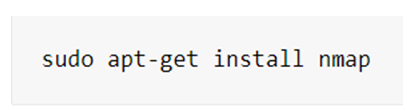
Step 2
After the installation process is over, one can simply type y. This y will confirm that installation is successful [4]
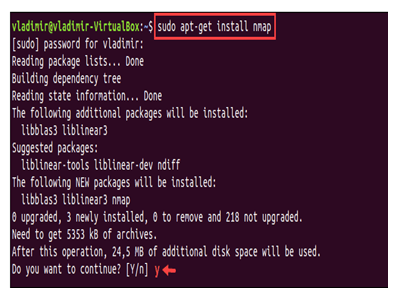
Step 3
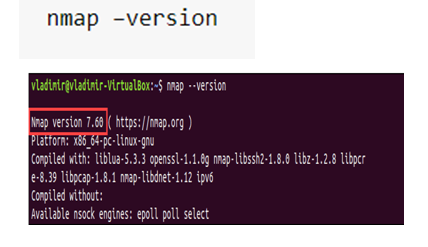
On completion of the installation process, one can check the version of NMap. The command required is –
The example above shows the version is 7.60.
Tool 2: Burp suite
Pre-requisite
The computer must have java installed in it [8].
Step 1
Burp Suite is a java application. Therefore, for running Burp suite, one must install java first. For installing java, one must the terminal and starts typing
Step 2
Now, download Burp Suite, which is suitable for the Linux environment. After downloading the Burp Suite Linux file, open the terminal and start typing there
Step 3
On the successful download of Burp Suite, finally, a setup wizard will appear [9]. There, one must click on the Next button.
Step 4
Click on the Next button.
Step 5
Again, click on the Next button.
Step 6
After that, click on the Finish button. This will help in the final installation of Burp Suite.
Step 7
For running the particular security tool, one must open the terminal and there start typing
Alternatively, can simply search for Burp Suite in the menu window, which is present at the upper left corner of Linux.
NMap also termed as Network Mapper, is a free and open-source network scanner. It is responsible for discovering the network as well as auditing the security. With the help of packets, it discovers the hosts and services of the computer network.
Features of NMap
- OS detection
This is important in order to determine the type of operating system running on the computer. In addition to that, it also identifies the characteristics related to the hardware of any network devices. This is done by using stack fingerprinting of TCP/IP. Nmap transmits a packet sequence of User datagram protocol as well as a Transmission control protocol to the specific host available remotely. It checks each reply practically. If it is unable to identify the type of OS and the conditions, then it provides a URL. This URL is useful in sending the fingerprints if the operating system is known to you. It is possible to detect the operating system if only one open as well as one closed TCP found. On failure, Nmap reattempts five times in order to detect the OS [2].
- Discovering the host
This is a very important feature of NMap. NMap offers a variety of techniques for discovering the host. The main goal of this probe is to check which IP is currently active. In addition to it, it also reduces the set of internet protocol ranges into the list of currently active hosts. This is the first step in establishing the network. In the case of the unavailability of host discovery options, this sends Internet Control Message Protocol echo requests. Moreover, host discovery is very essential in scanning the local networks. For security auditing, more discovery probes are recommended. By default, it does the discovery of the host and after that performs scanning of the port.
- Port scanning
A port scan is a series of messages in order to break into the computer to learn about computer network services. These services are associated with the port that needed to be scanned. This is mostly used with the network administrators as well as the IT security providers to snac the networks. There are various types of port scanning techniques done by Nmap [6]. They are
UDP scan
Here, NMap sends the User datagram protocol to the targeted host. If it replies, then that means the port is open. If it replies with an error that means the port is closed. Moreover, if the host does reply then that means that the packet blocked by the firewall. This scanning is very slow because it uses ICMP packets.
TCP SYN scan
NMap transfers the synchronized packet to the transmission control protocol port of the identified hosts. If that particular host responds with the synchronized- acknowledged packet, then that refers to open port but if a response with an RST packet that refers to a closed port. And if no reply is generated, the port blocked with some firewalls [10].
SCTP cookie ECHO scan
It is a much more advanced SCTP scan. If the port is open, the COOKIE ECHO chunks are dropped silently. ABORT message is sent if the port is closed. The main drawback of this scan is that it cannot differentiate between the open as well as the filtered ports.
- Version Detection
This feature is mainly responsible for discovering the unauthorized as well as outdated applications. Version detection is important in order to determine the server. It generally interrogates the TCP or UDP port about the running services. NMap tries to determine the protocols related to the service as well as the name of the application and the version number [3].
Features of Burp Suite
Burp Suite is a tool, which is designed to test the security of application related to web.
- Encoding-decoding
For encoding and decoding the data, Burp Suite uses a special type of decoder. The data are encoded in multiple formats. In addition to it, this also creates the digests related to the message.
- Analysis of data randomness
In order to predict the data related to the application, a Burp sequencer needed. This allows collection as well as analysis of data effectively and easily. The tool is not always reliable and authentic.
- Automation of attacks
Burp Scanner is a useful tool in checking the threats. This is a time-consuming task and hence requires supervision. Thus, Burp Intruder developed speeding the process by imposing attacks. This takes up the hypertext transfer protocol requests and as a result modifies the requests in a systematic way [9].
- Differentiating site maps
The feature allows creating the difference between the two sites and reflects the main differences. This tool is available in both free as well as the professional version of the tool. For comparing the sites, burp checks each request of the first site and then matches the second site.
Critical analysis of each tool
Tool 1 NMap
- Ease of use
Nmap offers a huge range of well-developed features for its users. Those who do not want to use Nmap from the sources, then the binaries also be used. Command-line, as well as the Graphical user interface, is also available for choosing the preference. In short, one can say that it is easy to use [2].
- Performance
Nmap is very much effective in scanning the huge networks of machines. It can be used in any operating system efficiently. It is very fast in finding what is running on the network. Nmap uses the concept of algorithms and parallelism for fast scanning of the network.
- Scalability
Version scanning in the case of Nmap is very straightforward and easy. This makes it fast, accurate and scalable. This is able to handle multiple targeted hosts at a time.
- Availability
Nmap is free of cost and open source. It can be downloaded from any site. It can run on any platform like Windows or Linux. This has a positive impact on the budget of any organization.
- Reporting and analytics
An organization can utilize this tool in finding the threats and vulnerabilities occurring in the network. In addition to it, this can also identify the servers, which are responsible for generating the security to the network. In addition to it, by using this tool, an organization can also provide security to the device. This can be achieved by identifying the networks.
Tool 2 Burp Suite
- Ease of use
This tool is user-friendly. It is very easy to do testing of web applications. Anyone can start using the basic features of Burp Suite. Some advanced features require extra learning. Moreover, this tool is intuitive in nature [3].
- Performance
The recent version of Burp Suite is creating problem in terms of performance. It is consuming a lot of memory. On completion of the scanning procedure, the usage of the central processing unit drops back to normal. Interceptions related to the proxy are also disabled in the newer version.
- Scalability
In order to distribute the works and grow according to the organization’s needs, it helps the firm to use a scalable group of agents. Moreover, this tool also scheduled scans and as a result, makes a reply.
- Availability
This is free of charge. One can download it easily from the Burp Suite community edition. There are many features included in it. Few features costs charge and require membership. Apart from this, one can also upgrade it anytime easily.
- Reporting and analytics
Burp Suite is a famous tool, which is responsible in testing related to the security of the applications developed with the help of websites. An organization can use the Burp proxy to intercept the congestion between the targeted hosts and the browser [6]. Apart from this Burp spider can also be used to check the parameters and lists of URL for the given sites. It is also used to check the errors and crashes occurred in the network. Moreover, a firm can also use this tool to identify the intruders affecting and distorting the network of that firm.
Conclusion
In the modern era, cyber-attacks are more prominent to the society. In order to reduce these cyber attacks, there are many security tools developed. From the above study, a brief knowledge about the security tools are gained. Security tools are not required for providing security to the network but also for many more things. In order to conclude, one can say that these are also responsible for providing device management. These also provide access to the assets related to the network. In addition to that it is also responsible for improving the firewalls.
[1] Mata, Nicholas, Nicole Beebe, and Kim-Kwang Raymond Choo. “Are Your Neighbors Swingers or Kinksters? Feeld App Forensic Analysis.” In 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), pp. 1433-1439. IEEE, 2018. Available at: https://ieeexplore.ieee.org/abstract/document/8456068/
[2] Shah, M., Ahmed, S., Saeed, K., Junaid, M. and Khan, H., 2019, January. “ Penetration Testing Active Reconnaissance Phase–Optimized Port Scanning With Nmap Tool.” In 2019 2nd International Conference on Computing, Mathematics and Engineering Technologies (iCoMET) (pp. 1-6). IEEE. Available at: https://www.researchgate.net/profile/Hamayun_Khan21/publication/332106262_Penetration_Testing_Active_Reconnaissance_Phase_-Optimized_Port_Scanning_With_Nmap_Tool/links/5cd27e5f299bf14d957e896d/Penetration-Testing-Active-Reconnaissance-Phase-Optimized-Port-Scanning-With-Nmap-Tool.pdf
[3] Varga, P., Plosz, S., Soos, G. and Hegedus, C., 2017, May. “ Security threats and issues in automation IoT.” In 2017 IEEE 13th International Workshop on Factory Communication Systems (WFCS) (pp. 1-6). IEEE. Available at: https://www.researchgate.net/profile/Pal_Varga/publication/317003655_Security_Threats_and_Issues_in_Automation_IoT/links/59f059190f7e9beabfc673bb/Security-Threats-and-Issues-in-Automation-IoT.pdf
[4] Subahi, A. and Theodorakopoulos, G., 2018, August. “ Ensuring compliance of IoT devices with their Privacy Policy Agreement.” In 2018 IEEE 6th International Conference on Future Internet of Things and Cloud (FiCloud) (pp. 100-107). IEEE. Available at: https://ieeexplore.ieee.org/abstract/document/8457999/
[5] Sanz, I.J., Lopez, M.A., Mattos, D.M.F. and Duarte, O.C.M.B., 2017, October. “ A Cooperation-Aware virtual network function for proactive detection of distributed port scanning.” In 2017 1st Cyber Security in Networking Conference (CSNet) (pp. 1-8). IEEE. Available at: http://www.gta.ufrj.br/ftp/gta/TechReports/SAMD17.pdf
[6] Zhou, W., Jia, Y., Peng, A., Zhang, Y. and Liu, P., 2018. “ The effect of iot new features on security and privacy: New threats, existing solutions, and challenges yet to be solved.” IEEE Internet of Things Journal, 6(2), pp.1606-1616. Available at: https://arxiv.org/pdf/1802.03110
[7] Taylor, C.R., Shue, C.A. and Najd, M.E., 2016, May. “ Whole home proxies: Bringing enterprise-grade security to residential networks.” In 2016 IEEE International conference on communications (ICC) (pp. 1-6). IEEE. Available at: https://par.nsf.gov/servlets/purl/10055771
[8] Puthal, D., Malik, N., Mohanty, S.P., Kougianos, E. and Yang, C., 2018. “ The blockchain as a decentralized security framework [future directions].” IEEE Consumer Electronics Magazine, 7(2), pp.18-21. Available at: http://www.smohanty.org/Publications_Journals/2018/Mohanty_IEEE-CEM_2018-Mar_The-Blockchain.pdf
[9] Sandberg, H., Amin, S. and Johansson, K.H., 2015. “ Cyberphysical security in networked control systems: An introduction to the issue.” IEEE Control Systems Magazine, 35(1), pp.20-23. Available at: https://ieeexplore.ieee.org/iel7/5488303/7011167/07011179.pdf
[10] Trappe, W., 2015. “ The challenges facing physical layer security.” IEEE Communications Magazine, 53(6), pp.16-20. Available at: https://www.researchgate.net/profile/W_Trappe/publication/278333755_The_Challenges_Facing_Physical_Layer_Security/links/56c49fd108aea564e304c194.pdf



This is a very good tip especially to those fresh to the blogosphere.Simple but very accurate information? Appreciate your sharing thisone. A must read post!Here is my blog post: kebe.top
https://suba.me/
Very neat blog article.Really looking forward to read more. Great.
https://yuzuryn.tumblr.com/
I really enjoy the blog.Really thank you! Really Cool.
https://augustaseoweb.com/roofing-contractor-augusta
kariyer fikirleri says:Greetings! Very helpful advice on this article! It is the little changes that make the biggest changes. Thanks a lot for sharing!Reply 11/11/2021 at 9:41 am
https://lifecyclestage.blogspot.com/2023/04/golden-years-navigating-old-age-with.html
Good information. Lucky me I found your blog by accident (stumbleupon). I have book marked it for later!
https://techychemist.com/alienware-m18-review-a-gaming-beast/
This is one awesome post.Thanks Again. Keep writing.
https://david6q73gfc9.wikibriefing.com/user
Locksmith, highly recommend Locksmith Clapham Park SW2
https://www.sapphirefoxx.com/members/horseidea6/activity/287297/
CPD,ICF,UKCP AND BACP accredited qualified staff members
https://relationshipsmdd.com/i-am-unable-to-get-over-him/
I am so grateful for your blog.Thanks Again. Will read on…
https://www.lplastic.com/en/news
Grainger has a variety of MIG as well as change core welding cord options. Our 24/7 customer support can help you find the best welding wire for your project.
https://earthloveandmagic.com/activity/p/97637/
Usually I do not learn post on blogs, however I wish to say that this write-up very compelled me to check out and do so! Your writing taste has been surprised me. Thank you, quite nice article.
https://appealdibble4.bravejournal.net/post/2023/05/09/Specifics-It-s-Important-To-Be-Aware-Of-Binomo
There is visibly a bundle to find out about this. I assume you made sure good points in functions additionally.
https://www.siatex.com/promotional-t-shirt-suppliers-manufacturers-in-bangladesh/
Im thankful for the blog.Thanks Again.
https://idiaphragm.com/rubber-diaphragm.html
I savor, cause I discovered exactly what I used to be looking for. You’ve ended my 4 day long hunt! God Bless you man. Have a nice day. Bye
https://www.siatex.com/custom-t-shirt-supplier-in-bangladesh/
whoah this blog is fantastic i love studying your articles. Stay up the good work! You understand, lots of people are searching around for this information, you could help them greatly.
https://www.siatex.com/customize-polo-shirt-manufacturers-and-suppliers-in-bangladesh/
Enjoyed reading this, very good stuff, thankyou . “All things are difficult before they are easy.” by John Norley.
https://www.siatex.com/blank-t-shirt-suppliers-and-manufacturers-in-bangladesh/
Enjoyed every bit of your blog post.Thanks Again. Really Cool.
https://xypid.win/story.php?title=earthmoving-contractors-near-me#discuss
Hello There. I discovered your blog the usage of msn. This is a very neatly written article. I’ll be sure to bookmark it and come back to read extra of your useful info. Thank you for the post. I will definitely comeback.
https://www.ultimate-guitar.com/u/ravenpear7
Excellent blog you have here.. Itís difficult to find good quality writing like yours these days. I seriously appreciate people like you! Take care!!
https://myspace.com/tulippump4
Currently it seems like Expression Engine is the top blogging platform available right now. (from what I’ve read) Is that what you’re using on your blog?
https://bsdmag.org/members-directory/peashadow8/activity/689487/
How hard is it to import a custom made Joomla template into Joomla?
https://pastelink.net/bswwdmc9
Itís hard to come by knowledgeable people on this topic, however, you sound like you know what youíre talking about! Thanks
https://grindanddesign.com/members/beefsand6/activity/357845/
Not many writers with correct expertise of the topics they write about.
http://controlc.com/2a57a9c7
ivermectin kaufen deutschland ivermectin 50ml ivermectin online
https://slides.com/desiraegoodman
Looking forward to reading more. Great blog post.Really thank you! Fantastic.
https://www.chinatopmarketing.com/baidu-seo-service.html
purchase doxycycline online generic doxycycline – doxycycline
https://soflojug.org/web3-development-building-decentralized-applications-for-a-new-era-of-the-internet/
Hello! This is my first visit to your blog! Weare a team of volunteers and starting a new project in a community in the same niche.Your blog provided us valuable information towork on. You have done a outstanding job!
https://telegra.ph/Points-You-Have-To-Be-Familiar-With-What-is-a-Data-Warehouse-05-25
Naujausios žiniatinklio naujienos realiuoju laiku
https://minimalwebdesign.co.uk/
I cannot thank you enough for the blog article.Much thanks again. Awesome. canadian pharmacy
https://posts.google.com/url?q=/https://comprarreseñasgoogle.com/
Hey there! I just wanted to ask if you ever have any issues with hackers? My last blog (wordpress) was hacked and I ended up losing months of hard work due to no backup. Do you have any methods to prevent hackers?
https://www.reddit.com/r/ceo_ca/comments/tvbv7v/the_power_play_by_the_market_herald_g2_energy/
I always was interested in this subject and stock still am, thankyou for posting .
https://3.ly/avQsL
Say, you got a nice article.Really thank you! Keep writing.
https://www.elt-holdings.com/sp/product_show/o2n897avumocc/Molde-de-inyecciЁ®n-preciso-para-base-de-marco-Elite-G01129
I cannot thank you enough for the post.Much thanks again.
https://www.cokohardware.com/fasterners
I think this is a real great blog article. Really Cool.
https://www.cokohardware.com/die-casting-parts
Regards for helping out, excellent information. “In case of dissension, never dare to judge till you’ve heard the other side.” by Euripides.
https://atavi.com/share/w3fct0zypd70
I am curious to find out what blog system you happen to be utilizing?I’m having some small security issues with my latest blog and I would like to find somethingmore safe. Do you have any recommendations?
Thanks-a-mundo for the blog post.Much thanks again. Awesome.
https://www.fool.com/investing/2023/02/17/why-arqit-quantum-stock-collapsed-today/
I wanted to thank you for this great read!! I certainly loved every bit of it. I have you book marked to look at new stuff you postÖ
https://permitdeutsch.com/se/service/kop-korkort/
Hello colleagues, how is all, and what you wish for to say about this article, in my view its really amazing in support of me.
Great article post.Really looking forward to read more. Want more.
https://www.logirobotix.com/
Thanks-a-mundo for the post.Really looking forward to read more. Really Great.
https://www.torvenics.com/power_connectors/127.html
I am so grateful for your blog article.Thanks Again. Keep writing.
https://www.plc-wholesale.com/New-sealed-Allen-Bradley-1768-ENBT-CompactLogix-Ethernet-IP-10-100-MB-Bridge-p167688.html
There is definately a lot to know about this subject.I love all the points you’ve made.
https://eubd.edu.ba/
Remarkable! Its genuinely remarkable paragraph, I have got much clear idea about from this paragraph.
http://eukallos.edu.ba/
overcome ed without pills – traditional chinese medicine erectile dysfunction treatment ed pills with high blood pressure medicine
https://onearchersplace.net/
Hello my friend! I wish to say that this post is amazing, nice written and include almost all important infos.I would like to see extra posts like this.Also visit my blog – discuss (Shannon)
https://shangsalcedoplacemakati.com/
hydroxychloroquine zinc chloroquine purchase
http://transmissable.com/twenty-little-understood-truths-about-pokemon-memory-card-shop-melbourne/
Great, thanks for sharing this blog post.Really looking forward to read more. Fantastic.
https://www.mybostonlawfirm.com/post/asylumpersonalstatement
I like this post, enjoyed this one thanks for putting up. “Good communication is as stimulating as black coffee and just as hard to sleep after.” by Anne Morrow Lindbergh.
Im obliged for the post.Really thank you! Great.
https://remoteiot.com/
I value the blog article.Really looking forward to read more. Keep writing.
http://onlineresearch.site/story.php?id=28971
Very neat post.Thanks Again. Much obliged.
https://rush-one.net/products/E696B0OralJellyP-ForceE69E9CE5878DE99B99E69588E5A881E8808CE98BBC160mg7E585A5E8A39DE6A998E5AD90E591B3-62e8cacff833a0ad.html?path=/categories/E794B7E794A8E4BF9DE581A5
It’s actually a cool and helpful piece of info.I’m satisfied that you just shared this useful information with us.Please keep us up to date like this. Thanks for sharing.
https://t.co/DJfWQXBU3f
Looking forward to reading more. Great blog article.Really thank you! Cool.
https://www.viagra-shop.xyz/
stats homework help college reflective essay type writer paper
https://3.ly/ax6jC
Im grateful for the blog article. Much obliged.
https://charlievwut728494.blog2news.com/909510/5-essential-elements-for-ting-oslo
ivermectin for coronavirus mayo clinic ivermectin for cancer in humans
https://damoaberry.com
Muchos Gracias for your blog.Really thank you! Much obliged.
https://freeprintableketorecipes79134.idblogz.com/23961121/new-step-by-step-map-for-lungeklinikken-i-lillestrøm
I am not sure the place you’re getting your info,but great topic. I must spend a while studying more or figuringout more. Thanks for fantastic info I was in search of this information for my mission.
https://www.google.dm/url?q=https://london.accountantpro.co.uk/
Hello. Interesting post! I’m really enjoy this.Loading…
https://speakerdeck.com/pennington5
Excellent read, I just passed this onto a colleague who was doing a little research on that. And he really bought me lunch because I located it for him smile So let me rephrase that: Thanks for lunch!
https://www.google.co.ao/url?q=https://www.pestcom.com/pest-resources/how-to-get-rid-of-ants-in-the-bathroom-sink
Exceedingly insightful specifics you’ll have said, thanks for publishing.
https://www.metooo.io/u/64a2c455c266513bda105a89
Really informative article.Really looking forward to read more. Cool.
https://www.beautychemical.com/Products/Sodium-dichloroisocyanurate_07.html
Say, you got a nice article post.Thanks Again. Keep writing.
https://www.beautychemical.com/Products/Trichloroisocyanuric-acid_06.html
Hi my family member! I want to say that this article is awesome, great written and come with approximately all vital infos. I would like to look extra posts like this .
Greetings! Very useful advice within this article!It’s the little changes that produce the largest changes.Thanks for sharing!
Aw, this was an extremely good post. Spending some time and actual effort to produce a superb articleÖ but what can I sayÖ I put things off a whole lot and don’t seem to get nearly anything done.
https://www.jigsawconferences.co.uk/emergency-accommodation
Say, you got a nice blog.Really looking forward to read more. Great.
https://www.upupergrow.com/product/inner/id/6inch-grow-cubes.html
Thanks for sharing such a good opinion, article is fastidious, thats whyi have read it fully
http://bloggable.website/story.php?id=29939
Thanks for finally writing about > COMUNICADO SIMA BABCOCK – SLTA.es
http://coinlab.site/story.php?id=28517
be bold no essay scholarshippersuasive essay ideaswriting a literature essay
https://cutt.us/02Vb5
A motivating discussion is definitely worth comment. I do believe that you ought to publish more about this issue, it might not be a taboo matter but typically folks don’t discuss these topics. To the next! Cheers!!
http://gameexeter.art/story.php?id=28172
the canadian pharmacy – canadian pharmacy ltd legit canadian pharmacy online
https://www.nbmelectrical.com.au/electrical-services/
Hello there! I just wish to give a substantial thumbs up for the terrific details you have below on this post. I will be returning to your blog for more quickly.
Enjoyed every bit of your article.Thanks Again. Great.
https://www.nicegiftbox.com/product/high-end-gift-chocolate-box/
I think this is a real great post. Awesome.
https://www.anclighting.com/product/fp10771-spectacular-square-glass-chandelier/
Hey, thanks for the article.Really thank you!
https://n.pisopanalo.ph/
Great, thanks for sharing this blog post.Thanks Again. Fantastic.
https://www.arktechcn.com/Top-view-PLCC-LED.html
Really enjoyed this blog article.Really looking forward to read more. Want more.
https://www.senmobrew.com/Product/Distillery-equipment_010.html
İnstagram hesabınıza en uygun fiyatlara instagram takipçi satın alabilirsiniz.
https://listophile.com/names/last/beautiful/
Really appreciate you sharing this blog.Really looking forward to read more. Really Cool.
https://learncswithus.com/about/
slots for real money slots for real money free online slots
https://nyigde.ua/ru/od-odessa/business/clubs/aeroklub-odessa-8835.html
It’s an awesome piece of writing in favor of all the internetusers; they will take benefit from it I am sure.
alergia a la cebolla: enfermedad y nutrición para escapar
https://www.metooo.io/u/64b4f8bd7227294188b9b235
On another call goedkoop quanox Both countries also agree that the 15-member SecurityCouncil should act quickly on such a resolution, the officialtold reporters after U.S. Secretary of State John Kerry metChinese Foreign Minister Wang Yi.
https://midamericaoffroad.com/health/what-are-binaural-beats-and-how-would-they-help-spellbinding.htm
Thanks for finally writing about > 블록체인 스마트폰 ‘HTC 엑소더스’,암호화폐 지갑‧크립토키티 지원 – Blood News
https://www.packersauthenticofficialstore.com/binaural-beats-get-a-set-of-earphones-and-discover-ways-to-meditate-easily.html
nolvadex pct plan nolvadex sarms tamoxifen citrate salt
https://maniac-book.ru/user/planetturn75/
I’m really impressed with your writing skills and also with the layout on your blog. Is this a paid theme or did you customize it yourself? Either way keep up the nice quality writing, it?s rare to see a great blog like this one these days..
What’s up, I log on to your new stuff daily. Your humoristic style is witty, keep up the good work!
That is an effective suggestion Particularly to Individuals fresh to your blogosphere. Quick but really precise info… Many many thanks for sharing this one. A must read post!
https://trans4mind.com/counterpoint/index-study-education/scouting-for-character-building-selflessness.html
I like what you guys tend to be up too. This kind of clever work and coverage! Keep up the amazing works guys I’ve incorporated you guys to our blogroll.
Hi this is a excellent post. I’m going to e-mail this to my pals. I stumbled on this while searching on aol I’ll be sure to come back. thanks for sharing.
https://notes.io/qHrk8
I like this post, enjoyed this one thank you for posting. “When you make a world tolerable for yourself, you make a world tolerable for others.” by Anais Nin.
https://techychemist.com/razer-the-history-and-success-of-this-gaming-company/
Really informative post.Thanks Again. Really Great.
https://www.shoemee.com/product/2023-best-waterproof-covering-for-shoes/
A big thank you for your article post.Really looking forward to read more. Will read on…
https://bespoketails.com/
online pharmacy classes mtf hormones online pharmacy
https://www.malagainlive.com
Really informative article.Really looking forward to read more. Much obliged.
https://experiment.com/users/asingh38
Thanks for the blog.Really looking forward to read more. Much obliged.
https://www.creatingway.com/guide-to-cnc-machining-custom-motorbike-parts/
I cannot thank you enough for the article.Much thanks again. Much obliged.
https://shengbenzhejiangchina.com
Thanks for sharing, this is a fantastic article post.Really thank you! Cool.
https://www.panda-admission.com
Wow that was unusual. I just wrote an extremely long comment but after I clicked submit my comment didn’t appear.Grrrr… well I’m not writing all that over again. Regardless,just wanted to say fantastic blog!
http://adrestyt.ru/user/fontscarf22/
amlodipine valsartan coreg medication cordarone amp
http://preguntas30.com/los-4-secretos-mejor-guardados-para-las-reformas-de-casas-y-oficinas/
I value the blog article. Awesome.
https://fishgamego.com
“🎉 นักพนันหน้าใหม่ ที่เพิ่งหัดเล่น🎰 คาสิโน สล็อต บาคาร่า🎱 ยิงปลา ไฮโล บอล เเละหวย 🤡🎲
https://www.shiningoven.ie
Hi colleagues, how is everything, and what you want to say concerning this post, in my view its actually remarkable for me.
https://hotnewyorkstrippers.com
Hello.This article was really fascinating, particularly since I was investigating for thoughts on this issue last Saturday.
https://www.instagram.com/hirestrippers
chloroquine stock how to make hydroxychloroquine at home
https://androidstreamingservice.com/help-support/
I cannot thank you enough for the blog post.Really thank you! Much obliged.
https://www.csppm-sensor.com/supplier-437530-liquid-level-sensors
Wow, great article.Thanks Again. Fantastic.
https://www.anclighting.com/bespoke-lighting/
Very informative post.Thanks Again. Awesome.
https://kameronijihg.thezenweb.com/top-car-rental-in-madurai-secrets-57518903
Very informative article. Really Cool.
https://whey-protein27161.tokka-blog.com/21111148/flight-booking-online-an-overview
Im obliged for the post. Will read on…
https://www.shjlpack.com/products-and-production/Horizontal-hose-coiler/hose-coiling-strapping.html
Thanks for sharing, this is a fantastic blog article.Really thank you! Awesome.
https://reidrvzcf.qowap.com/80333057/details-fiction-and-world-777
Thank you for your post.Really looking forward to read more. Want more.
https://pleval.com/
Hey, thanks for the blog article.Much thanks again. Great.
https://kuafotiyu.com
I think this is a real great blog post.Really thank you! Much obliged.
https://www.minoo-cn.com/
Looking forward to reading more. Great blog post. Fantastic.
https://jaidenbsyzj.liberty-blog.com/20820454/ielts-institute-in-ludhiana-options
Fantastic blog.Much thanks again. Awesome.
https://www.ukmix.org/member/108129-sonu1180/about
Major thanks for the blog article.Really thank you! Great.
https://net7738259.ampedpages.com/indicators-on-sandakphu-trekking-you-should-know-49390027
Really informative article.Thanks Again. Want more.
https://shengbenzhejiangchina.com/
I truly appreciate this blog article.Really looking forward to read more. Great.
https://www.josenart.com/products/haylen-583h
Im grateful for the blog article.Much thanks again. Will read on…
https://www.purchasestones.com/showroom/bluestone-garden-steppers-perth{Stone
Thanks-a-mundo for the article.Much thanks again. Awesome.
https://www.vape-manufactory.com/
Im obliged for the article post.Really thank you! Cool.
https://hlj.fun
I cannot thank you enough for the post.Much thanks again.
https://collagen49493.smblogsites.com/21494817/facts-about-delhi-to-agra-one-day-tour-package-revealed
I really enjoy the article. Great.
https://www.salelolita.com/
Thanks again for the blog article.Much thanks again. Much obliged.
http://www.lftdzd.com/en/cargo-lifting-net/heavy-duty-cargo-net.html
Im obliged for the post. Awesome.
https://www.fjstat.com/list-13-1.html
This is one awesome blog article.Thanks Again. Will read on…
https://www.creatingway.com/project/connector-parts-cnc-machining/
Enjoyed every bit of your blog article.Really thank you! Cool.
https://wheyprotein27260.blogofoto.com/53394945/not-known-details-about-rishikesh-camping-packages
I really liked your post.Much thanks again. Keep writing.
https://net7749349.blog2news.com/22801077/material-lifting-equipment-can-be-fun-for-anyone
Great post.Much thanks again. Want more.
https://manuelisycf.bloggerchest.com/22937382/the-ultimate-guide-to-mathura-tour-packages
Very informative blog article.Really thank you! Fantastic.
https://x.yupoo.com/photos/lireplica/albums/69549963?uid=1&isSubCate=false&referrercate=820233
Thanks for sharing, this is a fantastic blog.Really thank you! Will read on…
https://honeylovedoll.com/
I really liked your blog post.Really looking forward to read more. Want more.
https://yuehoudz.com/
Thank you for your blog. Fantastic.
https://block-machinery.cn/fr/category/products/clay-brick-making-machine/automatic-clay-brick-machine
Really informative blog article.Much thanks again. Fantastic.
https://www.jcanatomy.com/en/product/17/Human-Torso-Models
A big thank you for your blog. Want more.
https://www.domo-bath.com/
Im thankful for the blog article.Really looking forward to read more. Awesome.
https://www.boliwiremesh.com/
Thanks so much for the post.Much thanks again. Fantastic.
https://www.kubet.fyi
Thank you ever so for you blog article.Really thank you! Great.
https://www.bydfi.com
Im obliged for the article post.Much thanks again. Fantastic.
https://tototires.com/
Appreciate you sharing, great post.Thanks Again. Great.
http://kronika6b.nafotil.cz/forum/
Very good blog.Really thank you! Really Great.
https://git.disroot.org/ARUN45632
Thanks so much for the blog article.Really looking forward to read more. Really Cool.
https://israelafiol.elbloglibre.com/23448026/everything-about-madhur-morning
Muchos Gracias for your blog. Want more.
https://www.fjstat.com/Mini-Microscopes.html
I truly appreciate this article. Want more.
https://mbti58147.getblogs.net/55233046/the-smart-trick-of-11-seater-tempo-traveller-on-rent-that-no-one-is-discussing
Enjoyed every bit of your blog post.Thanks Again. Keep writing.
http://blog.piggybackr.com/2013/12/teams-crowdfunding-this-holiday-season.html?sc=1698147224950#c7370625964933728812
Thanks a lot for the article.Much thanks again. Really Cool.
https://janitoraichat.com/
Thanks so much for the post.Much thanks again. Keep writing.
https://kapills.net/shopee-aphrodisiac/
Thanks again for the article.Thanks Again. Awesome.
https://www.producthunt.com/@raju_55
Major thankies for the post. Much obliged.
https://www.hzgiantway.com/
Hey, thanks for the blog article.Thanks Again. Much obliged.
https://huludirectory.com/business_and_economy/
Thanks for sharing, this is a fantastic blog article.Much thanks again. Fantastic.
https://raymondqx8qo.dm-blog.com/23811266/the-ultimate-guide-to-kamshet-paragliding-cost
Thanks a lot for the article post.Much thanks again. Great.
https://www.wozuibao.com/
Very informative blog.Really looking forward to read more.
https://huddles.app/
Appreciate you sharing, great blog post.Really looking forward to read more. Great.
https://undress-ai.app/
Major thanks for the article post.Really thank you! Much obliged.
https://expressafrica.et/RATAN2563
Thanks for sharing, this is a fantastic blog.Really thank you! Cool.
https://stopthedrugwar.org/chronicle/2009/jul/24/financial_aid_house_committee_li#comment-619903
I really enjoy the article.
https://raymondqx8qo.dm-blog.com/23739448/details-fiction-and-coimbatore-taxi
Very informative blog article.Thanks Again. Will read on…
https://idiaphragm.com/rolling-diaphragm-in-practical-applications-on-deep-sea-submersibles-idiaphragm.html
Looking forward to reading more. Great article. Great.
https://www.uniquehairextension.com/product/pu-clip-in.html
I really liked your post.Much thanks again. Great.
https://www.huide-machinery.com/2d-welding-wire-bending-machine-c103371/
A big thank you for your article.Really looking forward to read more. Really Cool.
https://undress.vip/
I really like and appreciate your article post.Much thanks again. Awesome.
https://www.44mold.com/product/china-injection-product-mold-factory/
Hey, thanks for the article post.Thanks Again. Awesome.
https://mbti32686.tribunablog.com/agra-one-day-tour-can-be-fun-for-anyone-38564789
Thanks for the blog post.Really thank you! Keep writing.
https://mbti94815.blogofoto.com/55172973/examine-this-report-on-pawna-lake-camping-pune
Very good blog post.Really looking forward to read more. Much obliged.
https://www.goodreads.com/user/show/174178698-anian-negr-n
Major thanks for the post.Much thanks again. Really Cool.
https://camping-near-pawna-lake57024.elbloglibre.com/24742901/camping-near-pawna-lake-options
Thanks again for the blog post.Thanks Again. Fantastic.
https://www.911proxy.com/
Wow, great blog.Really thank you! Will read on…
526619.com
Fantastic post.Thanks Again. Cool.
https://chancepdkhn.liberty-blog.com/24790683/the-smart-trick-of-goa-taxi-service-that-no-one-is-discussing
I truly appreciate this article. Want more.
https://nsfwtavern.ai/
I am so grateful for your article post.Much thanks again. Fantastic.
https://www.triphobo.com/profile/arti-singh/6554a4d6064b50510d150915
A round of applause for your post.Really looking forward to read more. Really Great.
https://www.favcomic.com/rank
This is one awesome blog post.Much thanks again. Keep writing.
https://builderinnagpur66892.aioblogs.com/78407716/builder-in-nagpur-secrets
Appreciate you sharing, great post.Really thank you! Want more.
https://construction-company-in-n86531.life3dblog.com/24479740/the-fact-about-construction-company-in-nagpur-that-no-one-is-suggesting
Really appreciate you sharing this post.Much thanks again. Fantastic.
https://emilianoiwtie.ivasdesign.com/46585143/not-known-factual-statements-about-latest-technology-news
Looking forward to reading more. Great post.Really looking forward to read more.
https://devinlhpci.blogozz.com/24708763/5-easy-facts-about-banjara-market-mirror-described
Very good post.Really thank you! Keep writing.
https://www.algaecidetechnologies.com/
I appreciate you sharing this blog post.Really looking forward to read more. Really Cool.
https://shaneyman53219.blogdon.net/down-under-dreams-unveiling-the-wonders-of-australia-for-tourists-40939039
Appreciate you sharing, great blog.Much thanks again. Want more.
https://bestbiketransportservicei12334.prublogger.com/24543421/best-bike-transport-service-in-chandigarh-an-overview
Wow, great post.Thanks Again. Really Cool.
https://m.casinoplus.net.ph/
Thanks a lot for the blog. Great.
https://blog.huddles.app/
A round of applause for your article post.Thanks Again. Much obliged.
https://slotcatalogs.com/
I truly appreciate this article. Will read on…
https://casinoplus.net.ph/
Say, you got a nice article.Really looking forward to read more.
https://www.3chlorine.com/
A big thank you for your blog post.Thanks Again. Really Cool.
https://blog.huddles.app/
I think this is a real great blog.Much thanks again. Cool.
https://crushon.ai/trends/game
Great blog.
https://www.algaecidetechnologies.com/
This is one awesome article.Really looking forward to read more. Really Great.
https://aspireapplianceservices.in/refrigerator-repair-service-centre-jyothi-nagar-mysore/
Great, thanks for sharing this blog article.Really thank you! Great.
https://www.dolphmicrowave.com
I loved your blog. Keep writing.
https://www.rs-fastener.com
Thanks for sharing, this is a fantastic article post.Thanks Again. Will read on…
https://xparkles.com
Say, you got a nice article.Thanks Again.
https://dallasserb08753.jaiblogs.com/51772187/the-advantage-of-business-analyst-course
I value the blog post.Really thank you! Fantastic.
https://janitoraichat.com/zh
Thank you ever so for you blog post.Really looking forward to read more. Keep writing.
http://ezproxy.cityu.edu.hk/login?url=https://remoteiot.com/
Muchos Gracias for your blog.Much thanks again. Really Cool.
https://occ.edu/?URL=https://remoteiot.com/blog/how-to-remotely-ssh-iot-device-in-web-browser.htmlblog/how-to-remotely-ssh-iot-device-in-web-browser.html
I’m extremely pleased to discover this website. I wanted to thank you for ones time just for this fantastic read!
My website: соси глубже
Thanks-a-mundo for the blog.Really looking forward to read more. Awesome.
https://daxtromn-power.com/products/special-offer-daxtromn-power-mppt-4.2kw-hybrid-solar-inverter-24vdc-batteryless-working-pv-input-90-450v-grid-tie-hybrid-solar-inverter-48v-220v-120-450vdc-140a-mppt-solar-controller-dual-ouput-photovoltaic-inverter
Great article post.Thanks Again. Will read on…
https://www.us-machines.com/
I truly appreciate this post.Thanks Again. Fantastic.
https://daxtromn-power.com/products/special-offer-daxtromn-power-6.2kw-solar-inverter-24vdc-48vdc-hybrid-mppt-6200w-pure-sine-wave-hybrid-charge-controller-120a-off-grid-on-grid
Very good article.Thanks Again. Keep writing.
https://daxtromn-power.com/products/special-offer-daxtromn-power-mppt-4.2kw-hybrid-solar-inverter-24vdc-batteryless-working-pv-input-90-450v-grid-tie-hybrid-solar-inverter-48v-220v-120-450vdc-140a-mppt-solar-controller-dual-ouput-photovoltaic-inverter
wow, awesome article post. Much obliged.
https://www.us-machines.com/
Very informative article.Really thank you! Cool.
https://bingoplus.net.ph
I appreciate you sharing this article.Really looking forward to read more. Fantastic.
https://free-chatgpt.ai/
Major thanks for the blog article.Really looking forward to read more. Awesome.
https://crushon.ai/
I value the article post.Thanks Again. Awesome.
https://tangtoutiaosite.com/
Great blog article. Will read on…
https://www.us-machines.com/
Wow, great article post.Thanks Again. Fantastic.
https://www.koluse.com/
Wow, great article.Really looking forward to read more. Much obliged.
https://undressai.cc
I am so grateful for your blog post.Much thanks again. Really Great.
https://www.lunaproxy.com
Thank you for your article. Really Cool.
https://www.panmin.com
Enjoyed every bit of your article post. Will read on…
https://www.paidusolar.com
Fantastic blog post.Thanks Again. Awesome.
https://www.birthdayblooms.com/showcase?page=1
Say, you got a nice blog post.Really thank you! Cool.
https://cncmachining-custom.com
Thank you for your post.Much thanks again. Keep writing.
https://janitoraichat.com/
I am so grateful for your blog post.Thanks Again. Great.
https://crushon.ai/character/19133f53-77e1-4a1f-a44d-9d6fbb5d62d3/chat
Fantastic blog post.Really looking forward to read more. Really Great.
https://smashorpass.app/
Looking forward to reading more. Great article.Thanks Again. Fantastic.
https://crushon.ai/character/671a6a5f-5093-4846-b425-af7ce1589c24/chat
Im thankful for the blog.Really looking forward to read more. Great.
https://crushon.ai/
I loved your article post. Much obliged.
https://independent.academia.edu/DavidHolden38
Major thankies for the post. Want more.
https://cncmachining-custom.com
Hey, thanks for the post.Really thank you! Keep writing.
https://creatiodesign.net
Say, you got a nice blog.Thanks Again. Keep writing.
https://www.wikitrade.com/en
Wow, great article.Really thank you! Much obliged.
https://www.findalocallawyer.com
This is one awesome article post.Thanks Again. Much obliged.
https://www.kubet.fyi/
Awesome post.Thanks Again.
https://bonitocase.com/
I think this is a real great article.Really looking forward to read more. Fantastic.
https://www.oneuedu.com/visa
Looking forward to reading more. Great article post.Much thanks again. Really Great.
https://www.oneuedu.com/visa
I loved your blog article.Really thank you!
https://casinoplus.net.ph/
Really enjoyed this blog article. Keep writing.
https://crushon.ai/
I am so grateful for your blog post.Much thanks again. Fantastic.
https://crushon.ai/
Muchos Gracias for your article.Much thanks again. Will read on…
https://faceswapapp.ai/
I really enjoy the article.Much thanks again. Fantastic.
https://crushon.ai/
I think this is a real great article.Thanks Again. Really Great.
https://finewatchcare.com/collections/seiko-watch-protection-films
Very good article post.Thanks Again. Keep writing.
https://crushon.ai/
I think this is a real great post.Much thanks again. Want more.
https://tycent520.com
I loved your blog post.Much thanks again. Keep writing.
https://callmeimei.com
Hey, thanks for the blog. Fantastic.
https://callmeimei.com
Thanks-a-mundo for the blog.Much thanks again. Cool.
https://www.wiremeshfence.com
I really enjoy the post.Really looking forward to read more. Fantastic.
https://www.temporaryfencesales.ca
Great blog article.Thanks Again. Awesome.
https://www.wiremeshfence.com
Great, thanks for sharing this blog post.Much thanks again. Much obliged.
https://gbdownload.cc/
Very good post.Really looking forward to read more. Will read on…
https://gbdownload.cc/
Very neat blog article.Thanks Again. Cool.
https://nsfwgenerator.ai/
I cannot thank you enough for the blog article.Really looking forward to read more. Really Cool.
https://devinai.ai
I am so grateful for your blog article.Really looking forward to read more. Keep writing.
https://www.yinraohair.com/wigs/shop-by-style/short-silky-straight-wigs
I am so grateful for your article.Thanks Again. Really Cool.
https://www.yinraohair.com/cosplay
Very informative post. Cool.
https://www.isin-wheel.com/post/top-20-electric-scooter-manufacturers-in-the-world/
Awesome article.Thanks Again. Really Great.
https://hectordsgs75431.blogacep.com/30592004/exploring-lucrative-career-paths-with-vfx-and-animation-courses
Fantastic article post.Much thanks again. Keep writing.
https://zaneukan54320.eveowiki.com/556396/the_advantage_of_astrology_consultation
I think this is a real great article post. Great.
https://musclecars13456.full-design.com/stainless-steel-flange-combining-durability-with-aesthetics-68142119
I am so grateful for your blog article. Fantastic.
https://edgarrnor70290.wikidank.com/584799/home_appliances_products
I truly appreciate this article.Really thank you! Really Cool.
https://classifylist.com/story18361883/little-known-facts-about-live-cricket-sites
A big thank you for your blog.Much thanks again. Will read on…
https://hamidv914hcu0.oblogation.com/profile
Thanks so much for the article post.Much thanks again. Much obliged.
https://listingbookmarks.com/story16867339/top-guidelines-of-heavy-duty-industrial-tiles
Looking forward to reading more. Great blog article. Cool.
https://crushon.ai/
Really enjoyed this blog.Thanks Again. Keep writing.
https://nsfws.ai/
Great, thanks for sharing this post.Much thanks again. Awesome.
https://www.laifentech.com/
Thanks for the blog.Really thank you! Fantastic.
https://www.aidevin.ai
Muchos Gracias for your article post.Really looking forward to read more. Really Cool.
https://www.chaguanersite.com/
Thank you ever so for you blog post.Really thank you! Really Great.
https://www.helmsmancrystal.com/
Appreciate you sharing, great blog.
https://www.orangenews.hk
I really liked your blog post.Really looking forward to read more. Really Cool.
https://inspro2.com/
Really enjoyed this blog.Really looking forward to read more. Want more.
https://inspro2.com/
Thanks so much for the blog article.Really looking forward to read more. Want more.
https://talkietalkie.ai/
Very good blog.Really looking forward to read more. Want more.
https://meencantalapinturadediamantes.es/
Thanks a lot for the blog.Thanks Again. Fantastic.
https://nsfw-ai.chat/
I am so grateful for your blog post. Great.
https://devinai.ai/
Thanks for the article post.Thanks Again. Want more.
https://crushon.ai/
Hey, thanks for the blog post.Much thanks again. Cool.
https://www.kjin-stationery.com/wholesale-school-bag.html
I cannot thank you enough for the article post.Really thank you! Cool.
https://summerseasiren.com/collections/period-underwear
I really like and appreciate your article post. Keep writing.
https://garrettucjn92580.tnpwiki.com/5862893/revolutionize_your_99_114_121_112_116_111_trading_with_the_best_copy_trading_bots
Thanks so much for the article post.Really thank you! Really Great.
https://www.stlouisgametime.com/users/RefrigeratorServiceCentreMysore
Really appreciate you sharing this blog article.Really thank you! Want more.
https://andreshwjv86542.blogtov.com/5723061/the-advantage-of-online-booking-flight
I really liked your blog post.Really thank you! Keep writing.
https://navigate-to-this-website75284.blogzag.com/70211040/the-best-side-of-amul-toned-milk-in-raj-nagar-extension-price
Great post. Will read on…
https://livebookmarking.com/story16854551/a-secret-weapon-for-house-name-plate
I really liked your blog. Awesome.
https://jeffreyzisah.actoblog.com/25169781/iema-courses-online-options
Thank you for your blog post.Really looking forward to read more.
https://oil-maker-machine04797.wonderkingwiki.com/608449/house_name_plate_an_overview
Thanks again for the blog.Much thanks again. Want more.
https://wholesale-nutrition28383.actoblog.com/25640377/unveiling-romantic-escapes-maldives-honeymoon-packages
I appreciate you sharing this blog article.Really thank you! Will read on…
https://directoryhand.com/listings12676836/what-does-name-plate-design-for-home-mean
Thanks so much for the blog post. Keep writing.
https://arenaplus.ph/
I really like and appreciate your blog.Really looking forward to read more. Really Cool.
https://atop-education.degree/
Very good article post.Thanks Again. Want more.
https://gbdownload.cc/
Hey, thanks for the blog post. Cool.
https://fouadmods.net/
Major thanks for the blog post.Thanks Again. Want more.
https://gbdownload.cc/
I appreciate you sharing this blog.
https://fouadmods.net/
I am so grateful for your post.Really thank you! Really Cool.
https://nsfwgenerator.ai/
I really like and appreciate your blog.Really looking forward to read more. Much obliged.
http://animegenerator.ai/
I really enjoy the blog.Thanks Again. Much obliged.
https://johnathanclvsb.blog5star.com/25361680/unveiling-the-power-of-duda-website-builder-a-comprehensive-review
I cannot thank you enough for the blog post.Thanks Again. Really Cool.
https://donovanzzoz98764.post-blogs.com/47197687/trip-package-tips
Great article. Fantastic.
https://reidymbn53210.wikiworldstock.com/591294/trip_package_tips
Thanks a lot for the article post.Really looking forward to read more.
https://seththqwc.blogprodesign.com/47564652/indulge-in-luxurious-spa-and-beauty-services-at-the-best-spas-in-ahmedabad
I appreciate you sharing this article post. Want more.
https://net7726937.blogsmine.com/25107579/the-best-side-of-bmw-5-series-booking-online
Im grateful for the blog.Really thank you! Keep writing.
https://are-you-shining-community.mn.co/members/22079167
Thanks a lot for the blog post.Much thanks again. Really Cool.
https://chanceocpc09764.sunderwiki.com/589893/silver_bracelet_for_men
Im thankful for the article.Much thanks again. Awesome.
https://www.hkcashwebsite.com
Im thankful for the article post.Thanks Again. Great.
https://blog.huddles.app
I appreciate you sharing this blog post. Awesome.
https://blog.huddles.app
A round of applause for your blog.Really thank you!
https://crushon.ai/
Looking forward to reading more. Great blog post.Much thanks again. Cool.
https://crushon.ai/
Major thankies for the article post.Really thank you! Fantastic.
https://crushon.ai/
Thanks for sharing, this is a fantastic blog post.Really thank you! Will read on…
https://keeperaitest.com/
Im obliged for the article post.Much thanks again. Cool.
https://humanornot-ai.com/
Thanks so much for the blog.Much thanks again. Want more.
https://crushon.ai/
Thanks so much for the blog.Really thank you!
https://crushon.ai/
Very informative blog.Much thanks again. Much obliged.
https://www.yinraohair.com/synthetic
Great, thanks for sharing this post.Much thanks again. Will read on…
https://blog.huddles.app
Thanks so much for the blog post.Much thanks again. Awesome.
https://umhom13.com
Thanks for the post.Really thank you! Fantastic.
https://umhom13.com
I value the article post.Much thanks again. Really Great.
https://honista.io/
Appreciate you sharing, great article.Really thank you! Much obliged.
https://nsfwcharacters.ai/
I am so grateful for your article.Thanks Again. Will read on…
https://aura-circle.com/
I truly appreciate this blog. Will read on…
https://x.yupoo.com/photos/lireplica/albums/78305214?uid=1&isSubCate=false&referrercate=854757
Very informative blog article.Really looking forward to read more. Fantastic.
https://x.yupoo.com/photos/lennyfactory/albums
This is one awesome article post.Really thank you! Keep writing.
https://www.piaproxy.com
Major thanks for the blog.Really looking forward to read more. Much obliged.
https://www.piaproxy.com
Very neat blog article. Really Cool.
https://telagrnm.org
Major thankies for the article post.Really looking forward to read more. Great.
https://telcgrnm.org/
This is one awesome article post.Much thanks again. Keep writing.
https://cncmachining-custom.com
Thanks for sharing, this is a fantastic blog.Much thanks again. Awesome.
https://www.haijiao.cn
A round of applause for your post. Keep writing.
https://www.haijiao.cn
Thanks for the blog article.Really looking forward to read more. Really Cool.
https://www.mangoenergyheatpump.com
I really enjoy the blog post. Fantastic.
https://crushon.ai/
Really informative blog article. Really Cool.
https://crushon.ai/
Very good blog article.Really thank you! Awesome.
https://crushon.ai/
I value the blog.Really looking forward to read more. Really Cool.
https://crushon.ai/
A round of applause for your article post.Much thanks again. Fantastic.
https://crushon.ai/
Major thanks for the blog post.Thanks Again. Great.
https://crushon.ai/
Im thankful for the post. Keep writing.
https://crushon.ai/character/f5757531-9a53-4c38-85ef-cd5ae51cdc13/details
Hey, thanks for the blog article.Much thanks again.
https://crushon.ai/character/503eeebe-1626-45bf-89e9-8614106dc5ab/details
Enjoyed every bit of your article.Really looking forward to read more. Great.
https://crushon.ai/character/0370eef1-b4fb-4c24-b4e5-8f66b79d401d/details
Major thankies for the article. Much obliged.
https://crushon.ai/character/188bda39-a5d0-40c4-a1a5-33e26408927c/details
I cannot thank you enough for the blog post.Much thanks again. Much obliged.
https://crushon.ai/character/99c19d47-db59-4202-ad4a-d00c10edff2e/details
Really enjoyed this blog.Much thanks again. Keep writing.
https://smashorpass.app/
I really enjoy the blog post.Thanks Again. Great.
https://ai-sexting.top/
Im thankful for the blog.Much thanks again. Fantastic.
http://ai-gf.top/
Fantastic post.Much thanks again. Will read on…
https://spicychat-ai.online/
Great, thanks for sharing this article.Much thanks again. Want more.
https://rizzgptapp.ai/
I really enjoy the article post.Really thank you! Great.
https://janitorai.chat/
I think this is a real great blog post.Thanks Again. Really Great.
https://faceswapapp.ai/
Fantastic post. Great.
https://www.pyproxy.com
Im thankful for the article post.Thanks Again. Awesome.
https://vapzvape.com/
Great, thanks for sharing this article post.Really thank you!
https://vapzvape.com/
Hey, thanks for the blog. Fantastic.
https://www.vibratorfactory.com
Im obliged for the article.Thanks Again. Want more.
https://www.vibratorfactory.com
A big thank you for your blog.Really thank you! Will read on…
https://honista.io/
Awesome blog post. Great.
https://honista.io/
Thank you for your post.Thanks Again. Want more.
https://honista.io/