KF7028 Assignment Sample
Cloud Cryptography
Introduction
Cloud computing has proved to be an advanced approach for providing better management of the data or different computer resources without direct control over the data by the users. The suitable management of the resources for computer application is done through the strategic management of the information and data for different business organizations and also helping in the significant increase in the efficiency for computing power. This proposal is designed by focusing on the benefits developed through the application of cloud cryptography that insists on managing the valuable data for different business firms. Cloud cryptography plays an important role in the suitable management of resources by enhancing data security by implementing models for data security to enhance the safety of the data that is available within the cloud architecture.
Due to the advancement in technology that led to gearing up the methods for data flow through the implementation of wireless resources, the benefits have been faced through the application of cloud computing through the suitable increase in the rise of scalability and flexibility for the effective transfer of data. Through the application of wireless sensors or IoT devices that led to the effective tracking of data within the clouds of different organizations and helping in the decrease in the manual control over data through the use of automation for delivering the data to the user as per the requirements made from time to time. However, the demerits have been faced by the development of cyber attacks done by hackers intentionally by trapping the valuable data for the users present within the cloud architecture and reducing the safety and security of important data on a large scale. This factor is eliminated through the implementation of the approach for cloud cryptography through the application of encryption techniques for securing the user’s data effectively that is available with the cloud for enhancing the data authentication and privacy on a large scale. This proposal develops an aim for the perfect implementation of cloud cryptography through the identification of risks for performing risk management and also identifies different issues linked with its application.
Research Question
- What are the necessities and assumptions for providing data security through cloud cryptography for minimizing cyber risks?
Aim
This project takes a mission for the implementation of the methods for cloud cryptography through the effective identification of the cyber risks that reduce the data security within the clouds (Stergiou et al. 2018). The necessities are being spotted through the recognition of different cyber risks and thereby helping in developing assumptions for better management of risks by making suitable identification of activities.
Relevance, Motivation and Background – Literature Review
Performance enhancement through the effective management of the available data within the cloud architecture has been considered the prime focus for developing this project. The performance for cloud computing is greatly enhanced by implementing the techniques for cloud cryptography that will help increase the trust level of the users through the use of passwords for increasing privacy and security for valuable data on a large scale.
According to Yan and Varadharajan 2017, the presence of different types of cyber attacks has been identified that intends to create havoc by disrupting the security and privacy of the data of the users through the implementation of honey traps for getting access to the data present within the cloud leading to the loss of the information accordingly. The presence of different cyber attacks like malware, DDoS attacks, SQL injection, phishing and weaker passwords often lead to the significant increase in the loss of the valuable information of the users and thereby leading to the decrease in the trust level of the users through the increase in the concerns for data privacy and security on a large scale. The authors highlight the fact that as the data that is present within the cloud architecture of different business sectors are out of control for the users, therefore, it proves to be of an utmost requirement for reducing the possibility for data leakage through the development of unauthorized access by the hackers for stealing user data. The three significant factors have been identified by the authors that are demonstrated below.
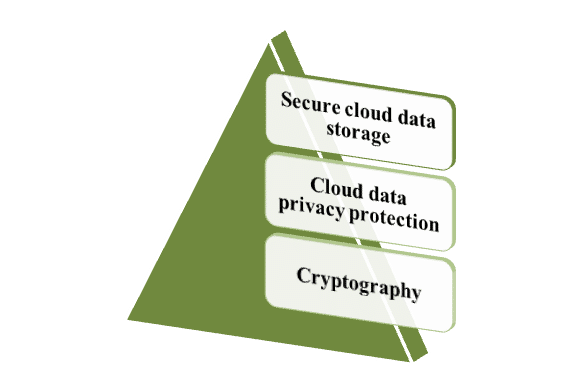
Figure 1: Factors for cloud computing
(Source: Self-created)
-
Securing storage for cloud data:
The authors have mentioned the SICAC scheme or “Secure Independent-update Concise-expression Access Control” that mostly makes use of the approach for “Attribute-Based Encryption” for giving efficient and flexible authorization and authentication for the user data available in the clouds for maintaining the services for “Video on Demand” (Abdel-Basset et al. 2018). The effective implementation of Key policy ABE algorithm helps in the suitable development of keys and passwords that will enhance the levels of data encryption through the implementation for limitation of the data flow within the servers accordingly.
-
Privacy protection for cloud data:
The authors have stressed on the suitable implementation for privacy protection through the “Attribute-Keyword based data Publish-Subscribe (AKPS) scheme” that will entail in the development of decryption and encryption methods for securing the data accordingly. The approximation of k-Nearest Neighbors helps in the generation of queries for decrypting the encrypted data through the suitable identification of the data patterns, thereby enhancing the authentication of the data for the users seeking the permission in order to give access to the data to third parties.
-
Cryptography:
The author mentions developing the level of data security through the implementation of RSA algorithms that encrypt the data through the use of 110 factoring integers that are required to be decoded for getting access to the valuable data of the users (AbdElminaam, 2018). The codes that are generated through the implementation of SOPE algorithms help in maintaining balance within the ciphertext equation and thereby helping in increasing the data feasibility on a large scale (ieeexplore.ieee.org 2020).
The researchers have previously made the approach for the effective implementation of encryption techniques through the use of cloud cryptography for enhancing the data feasibility on a large scale. Previously, the approaches have been made in the fields for cloud computing to better manage big data and enhance cloud security. The efforts have been made previously for the suitable implantation of the models for cloud deployment that mostly include hybrid, public and private models and thereby helping in the accessibility range for different users within a particular cloud architecture. The researches have been done previously for increasing the flow of data through the use of wireless devices that will help in the effective management of data within different server points and also increasing the user relying on the data through the effective reduction in the malpractices of the hackers for stealing data on a large scale. The reasons that have been specified through the development of this proposal for the suitable implementation of clouds cryptography are as follows:
-
Data authorization:
The consideration for the attempt for data authorization helps in understanding the reliability of the data that is being transferred by different users and thereby helping in increasing the user trust on a large scale on the received data (Al-Samarraie and Saeed, 2018). The implementation of wireless networks through the implementation of cloud architecture and IoT devices increases the possibility for heaving the presence of third parties or hackers in the intermediary zones for data transfer and thereby might affect the data of the users by making changes within the data. This proves to be dangerous as the user is unable to detect the originality of the data that is being received and might get trapped or cheated by the hackers resulting in the loss of personal data on a large scale. Therefore, the implementation of the cryptographic approach will help understand the relevance of the data sent by the sender and accept the receiver that, in turn, reduces the chances for data leakage considerably.
-
Data authentication:
The authenticity of the data is required to be focused on understanding the data contents accurately, thereby reducing misunderstanding amongst business organizations through the modification done within the data by hackers (Chatterjee et al. 2017). As the cloud data is out of direct control for the users, there developed chances for making modification in the data by the third party users. As a result, there occurs the possibility of increasing data loss of the users on a large scale.
-
Data encryption:
For developing security and safety of the data for the users, the authentication and authorization of the data are done through the implementation of the passwords designed through the use of digits for encrypting the valuable resources from the sender terminals. On receiving the data by the receiver, the server makes the request for decrypting the codes and generates a query request to the sender for giving access to the authorized users for getting the contents of the valuable data.
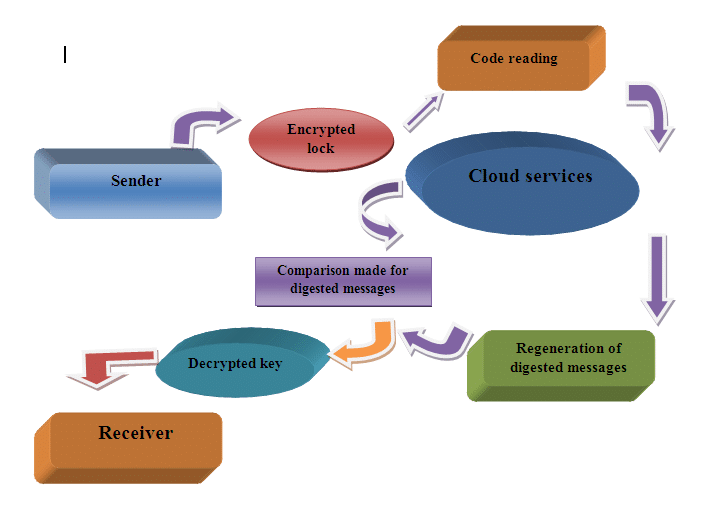
Figure 2: Mind map diagram for cloud cryptography
(Source: Self-created)
For the suitable increase in the development of the proposal for this research, the activities are being listed in order to accomplish and the benefits of cloud cryptography in a suitable manner. The activities are listed below:
-
Identification of cyber threats:
The action has been taken for the suitable identification of cyber risks that majorly affects the data that is present in the cloud leading to the increase in the range of data and economic loss up to a certain extent (Ghahramani et al. 2017). These threats are analyzed for understanding the patterns developed within them that are being imposed by the hackers and thereby facilitation in the suitable implementation of the protective measures for safeguarding of the users through decryption and encryption.
-
Authorizing and authenticating the data:
This action will help in the suitable recognition of the data that the users access, thereby enhancing transparency within the process of data transmission on a large scale. These actions will not help in the suitable recognition of the users and will assist in the development of the limitations for resisting the wrong flow of data to the users accordingly.
-
Implementation of passwords:
Passwords are implemented through the use of encryption algorithms that make use of numerical digits that are required to be cracked by the users for getting access to the data (Ghomi et al. 2017). This will help in maintaining the safety and authenticity of the data on a large scale.
-
Motivating users for using cloud computing:
The application of the approach through the use of cloud cryptography will assist in making use of digital platforms and cloud applications in order to store their data without any worries. This approach will also motivate and satisfy the users on a large scale by entering the data security level with the use of passwords and thereby avoiding data leakage.
In the future, the application of data mining models will make use of artificial intelligence, thereby assisting in understanding patterns developed within the data to understand the deformation developed in the data by the hackers in the intermediate zone.
For performing this research, the consideration of online portals for different business firms are considered and collecting the secondary data for the suitable accomplishment of the qualitative research (Kumar et al. 2018). The various protection protocols implemented by different firms for safeguarding the valuable data in the cloud architecture and thereby helping in the development of judgmental skills for identifying the best encryption algorithms for increasing the security of the data on a large scale (d1wqtxts1xzle7.cloudfront.net 2018).
Risks, Objectives and Scope
Project scope is designed through the implementation of the techniques for cloud cryptography and thereby helping in getting a suitable achievement through the development of the network security for the cloud data effectively. The vision that has been developed in this research is to develop the authenticity of the data through the implementation of encrypted codes and thereby limiting the accessibility of the unauthorized users up to a significant extent (Li et al. 2017). The research helps in increasing focus on the existence of cyber attacks affecting the cloud data and thereby helping in the application of coding languages for enhancing the safeguarding rates of the data on a large scale. This research excludes the importance of data mining models for increasing the efficiency of data encryption on a large scale through the suitable prediction of the attacks and thereby helping in the generation of alerts to the users more efficiently. In future, the implementation of the concept for AI will assist in developing the scope for this research massively and thereby helping in increasing the security level for data in a more modified approach (researchgate.net 2018).
| Specific | Measurements | Attainable | Realistic | Time-Bound |
| The application of cloud cryptography helps in increasing data authenticity through the application of passwords. Focus is majorly given for enhancing the data safety. | For the implementation of cloud cryptography, efforts must be made for measuring the entire data that is present in the cloud or server. The application of this approach could be done through the effective measurement of the cyber risks present in the system and thereby providing protection based on the priority developed for a particular cyber attack. | Suitable identification of the risks that might be encountered in the cloud data can prove to be a challenging attempt but could be achieved through the implementation of passwords that will help in generation of queries for opening the encrypted data by the users. | The focus must be made to be realistic for making use of the cryptographic techniques for mitigating the developed risks in the cloud data and thereby helping in enhancing the trust level for the users (Mollah et al. 2017). Use of secondary resources for different firms will help in improving the quality of the research on a large scale. | The accumulation of assumptions for the research must be completed within a specific time and also help in a suitable reduction in the cyber risks on a large scale. This will help in getting desired results within a specified time and will assist in motivating and increasing the satisfaction level of the users on a large scale. |
Table 1: SMART objectives
(Source: MS-Word)
| Objectives | Measurement of deliverables |
| Specific | Through the implementation of secondary resources, the measurement is done through the achievement of the safety of the user data. |
| Measurable | Taking into account the websites for different business firms for measuring the risk effects for taking immediate actions through the implementation of strong passwords. |
| Attainable | Risks are measured through the use of qualitative data and thereby taking opinions from users for understanding the success range for the approach made through the use of cryptographic algorithms for developing network security (Ramachandra et al. 2017). |
| Realistic | The secondary data are collected from the previous research for developing the quality of the research on a large scale and thereby measuring success through the accomplishment of project goals efficiently. |
| Time-bound | The success rate is measured through the completion of project goals on time. |
Table 2: Deliverables measurement
(Source: MS-Word)
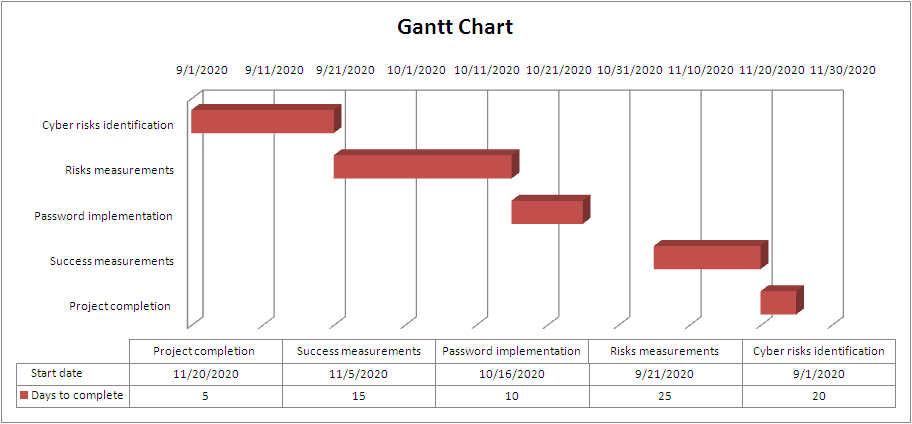
Figure 3: Gantt chart
(Source: MS-Excel)
| Task List | Resources | Deliverable | Skills | Time duration (days) |
| Identification of Cyber risks | Consideration of human resources that might use the skill of risk analyst for the effective tracing of risks | Effective planning through the use of secondary data and also consulting risk analyst for identifying the patterns of risks effectively | Knowledge of different cyber risks and cloud applications | 20 |
| Measurement of effects for a specific cyber risk | A costly approach through the use of machine learning for developing risk priority | Taking opinions from different employees of business firms for getting ideas regarding most prominent cyber threats (Senyo et al. 2018). | Knowledge about the cyber risk for developing strong passwords | 25 |
| Password implementation | IT developer | Security enhancement | Knowledge for developing passwords through the use of encrypted algorithms | 20 |
| Success measurement through the use of previous attempts | Researcher and quality control expert | Taking data from previous research materials for developing the quality of the research through the suitable implementation of passwords | The smart approach for understanding data relevancy and hereby helping in enhancing the motivation level of the users | 15 |
| Project completion | Feedback from the user for measuring the acceptability range of the developed password | Success measurement for completing research on time | Effective presentation and closure for the project | 5 |
Table 3: Control and Monitoring table
(Source: MS-Word)
| Task List | Risk developed | Risk rating | Mitigation |
| Cyber risk identification | Unable to detect the correct patterns for cyber threats due to technical faults | High | Implementation of AI for understanding patterns |
| Cyber risk measurement | Due to lack of proper information or resources for a particular risk, less action is developed for mitigating the most prioritized risk (Subramanian and Jeyaraj, 2018). | Very high | Hiring a skilled cyber security analyst for measuring the risk effectively. |
| Passwords | Weaker passwords | Very high | Development of suitable passwords |
| Previous research | Low budget | High | Implementation of alternatives for maintaining the budget |
| Project completion | Project delay | Medium | Implementation of skilled personnel for effective project completion |
Table 4: Risk management
(Source: MS-Word)
Professional, legal, social, ethics and security consideration
| Professional | Legal | Social | Ethics | Security |
| The issues are spotted for not being able to manage time by different skilled personalities and thereby leading to the decrease in the quality of the project with a then significant decrease in the contribution level of the employees. | The development of legal problems through the decrease in the transparency level of accumulated data resources for enhancing data security. | The issues are raised for not being able to the user identity and system parameters for the users and thereby leading to a decrease in the feasibility of research on a large scale. | The ethical issues are raised through the decrease in the rate of efforts by the human resources that will lead to the decrease in the project profitability through the decrease in the moral values for developing the research (Varghese and Buyya, 2018). | The rise of technical faults within the research will lead to an increase in the possibility for the development of the security breaches on a large scale and hence reducing the productivity of this research topic. |
Table 5: Issues
(Source: MS-Word)
Conclusion
To conclude, the consideration of the cloud cryptography has proved to be efficient in the determination of the enhancement in the network safety on a large scale and thereby helping in improving the process for cloud computing. The suitable motivation has been provided to the users by developing the security level of the data and thereby helping in developing project scope through the effective identification of the risks more efficiently.
Reference List
Book
Stergiou, C., Psannis, K.E., Kim, B.G. and Gupta, B., 2018. Secure integration of IoT and cloud computing. Future Generation Computer Systems, 78, pp.964-975.
Journals
Abdel-Basset, M., Mohamed, M. and Chang, V., 2018. NMCDA: A framework for evaluating cloud computing services. Future Generation Computer Systems, 86, pp.12-29.
AbdElminaam, D.S., 2018. Improving the security of cloud computing by building new hybrid cryptography algorithms. International Journal of Electronics and Information Engineering, 8(1), pp.40-48.
Al-Samarraie, H. and Saeed, N., 2018. A systematic review of cloud computing tools for collaborative learning: Opportunities and challenges to the blended-learning environment. Computers & Education, 124, pp.77-91.
Chatterjee, R., Roy, S. and Scholar, U.G., 2017. Cryptography in cloud computing: a basic approach to ensure security in cloud. International Journal of Engineering Science, 11818.
Ghahramani, M.H., Zhou, M. and Hon, C.T., 2017. Toward cloud computing QoS architecture: Analysis of cloud systems and cloud services. IEEE/CAA Journal of Automatica Sinica, 4(1), pp.6-18.
Ghomi, E.J., Rahmani, A.M. and Qader, N.N., 2017. Load-balancing algorithms in cloud computing: A survey. Journal of Network and Computer Applications, 88, pp.50-71.
Kumar, P.R., Raj, P.H. and Jelciana, P., 2018. Exploring data security issues and solutions in cloud computing. Procedia Computer Science, 125, pp.691-697.
Li, Y., Gai, K., Qiu, L., Qiu, M. and Zhao, H., 2017. Intelligent cryptography approach for secure distributed big data storage in cloud computing. Information Sciences, 387, pp.103-115.
Mollah, M.B., Azad, M.A.K. and Vasilakos, A., 2017. Security and privacy challenges in mobile cloud computing: Survey and way ahead. Journal of Network and Computer Applications, 84, pp.38-54.
Ramachandra, G., Iftikhar, M. and Khan, F.A., 2017. A comprehensive survey on security in cloud computing. Procedia Computer Science, 110, pp.465-472.
Senyo, P.K., Addae, E. and Boateng, R., 2018. Cloud computing research: A review of research themes, frameworks, methods and future research directions. International Journal of Information Management, 38(1), pp.128-139.
Subramanian, N. and Jeyaraj, A., 2018. Recent security challenges in cloud computing. Computers & Electrical Engineering, 71, pp.28-42.
Varghese, B. and Buyya, R., 2018. Next generation cloud computing: New trends and research directions. Future Generation Computer Systems, 79, pp.849-861.
Yan, Z., Deng, R.H. and Varadharajan, V., 2017. Cryptography and data security in cloud computing.
Online Articles
d1wqtxts1xzle7.cloudfront.net 2018, SECURE FILE STORAGE ON CLOUD USING CRYPTOGRAPHY, Available at: https://d1wqtxts1xzle7.cloudfront.net/56786053/IRJET-V5I3475.pdf?1528867980=&response-content-disposition=inline%3B+filename%3DSECURE_FILE_STORAGE_ON_CLOUD_USING_CRYPT.pdf&Expires=1610085397&Signature=HrwiiyxzW0KIM4K80PeqMIltZIraXdha3BNAHCXjbnKQ9VKXW86xn9LNxNb~N~7d7Rv53pNRcB4o0VzcOAQstzhAl4iAdZK-wmw7ti1r7~P9eBuOKiZBvV5gNWpXpd6TBGGM9M~J1Aow96Zutuda1H4UTGBLI57brwBKkjWOnRaKEtaPDOrm9TBedzwCAGDPoQwykurpV1lFCxBvDyZowDmy5eqJcdidJ17jJPbdBGuYCeofY68COHewS-PBGT~3kymxZD8aXWABocz5MKgQajIUpibnpXySK496NumeMkHBAqhZEt0zb2frV762Al6DOf80sFCGMXVDZPjjyipI7A__&Key-Pair-Id=APKAJLOHF5GGSLRBV4ZA, [Accessed on: 27.12.2020]
researchgate.net 2018, The Cryptanalysis of a Secure Authentication Scheme Based on Elliptic Curve Cryptography for IOT and Cloud Servers, Available at: https://www.researchgate.net/profile/Vinod-Kumar-5/publication/334167206_The_Cryptanalysis_of_a_Secure_Authentication_Scheme_Based_on_Elliptic_Curve_Cryptography_for_IOT_and_Cloud_Servers/links/5e136875299bf10bc392faac/The-Cryptanalysis-of-a-Secure-Authentication-Scheme-Based-on-Elliptic-Curve-Cryptography-for-IOT-and-Cloud-Servers.pdf, [Accessed on: 27.12.2020]
Website
ieeexplore.ieee.org 2020, Scalable and Secure Big Data IoT System Based on Multifactor Authentication and Lightweight Cryptography, Available at: https://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=9118946, [Accessed on: 27.12.2020]
………………………………………………………………………………………………………………………..
Know more about UniqueSubmission’s other writing services:

