LD7015 Engineering and Environment Advanced Practice
Introduction
In this present global atmosphere, the role of IoT is getting enhanced every day. There are multiple organisations around the globe developing IoT based infrastructures to support multiple systems and make sure about a future-oriented supply procedure. Here we as a group or team have developed an effective cyber security strategy to support an integrated IoT system. While completing the research-based project, I have understood and accumulated different sets of technological skills and attributes Adeani, Febriani and Syafryadin, 2020). All my identical and opportunity based evaluations and landings will be evaluated in this report. The report will be based on the Gibbs reflective cycle for better format presentation and proper identification of the learnings. Gibbs’s reflective cycle will enhance the opportunity of the report to be fact-finding and opportunistic. The critical finding associated with the security strategies and its implementation will be developed in the initial part of the research-based project. All of those are opportunistic to find out my capability or my efficiency towards effectiveness as an implementer. Even the report will critically reflect on the achievements I have been able to accomplish according to my personal learning goals set before the implementation of the project (Sekarwinahyu et al., 2019). In father evaluations, all the personal learning contracts and the portfolio-based evaluations developed for making an integral part of learning towards an opportunistic future will be developed and make sure I am relevant and, importantly, able to accomplish or acquire all the requirements. In the later part of the report, the future imposition or the future capabilities I will possess with the skills I have been able to acquire will also be demonstrated, and its implementable opportunities will also be demonstrated in brief. The report will critically follow the Gibbs reflective cycle, so all the six parts of the evaluation will be completed. The whole learning cycle of my ability enhancement will be based on those.
Gibbs reflective cycle
Gibbs reflective cycle is accounted to be the most prolific model of reflection based findings or evaluation, which has the potential of evaluating all the identical learnings coming out of study research or any type of report accomplishment. In this case, the whole report and the reflective cycle will depend on the learning switch I have been able to acute while determining effective cyber security strategies to support an integrated IoT system.
Description
As opined by Tawanwongsri and Phenwan (2019), the part of the description is quite relevant and essential to demonstrate the identical goals we have set before starting the project. The project’s initial goal is to identify effective cyber security strategies to support an integrated IoT system. The goal was relevant and important to ensure that all the research-based questions developed, like the most common cyber security strategies present in the market and its efficiency in generating awareness or mitigating all the cybersecurity-related risks over the evaluated integrated IoT system. While evaluating, one of the critical goals is to signify the most efficient cyber security strategies used by different integrated IoT systems and its efficiency in deploying proper security infrastructure to the society or the system. Another important goal associated with the task for the team is to determine the most influential and implementable benefits of cyber security development over any type of cyber threats and IoT based systems (Li et al., 2020). One of the most identical portfolios designed or developed for accomplishment is determining the effective way to implement the resources. Even the initial goal of abrupt potential generation or enhancing the ability to complete any research satisfies or signifies the opportunity of the research to be implementable. Without having critical findings associated with it, there are possibilities of facing issues within the implementation which are required to be solved within the initial phase.
Along with all the identical opportunities, it is initially attributed or ensuring that the security interface or ecosystem developed for implementation will be for a long term security provision to the integrated IoT system. To make sure about all of this, it is quite relevant and essential to create an assurance framework and ensure that the framework is relevant to the context of the research (Tanaka, Okamoto and Koide, 2018). Another critical identity of all goals set in the initial part of the research is encouraging open standards of operation. By setting reasonable goals, the chance of accomplishing those gets enhanced, and in this context, all the goals being evaluated or set are proper and implementable in a manner. The research’s implementation phase becomes relevant to identifying the most appropriate cyber security provision ability to the research path or the integrated IoT system by ensuring all these probabilities.
Feelings
Considering feelings in the initial half of the project, I was nervous about the fact findings. One of the critical reasons for this is my inability to work in a group or complete any project with the help of different individuals. At the beginning of the project, I have identified that to complete any group project, and it is imperative to be a good learner and a good leader to lead a team. Without having an apparent ability to lead a team, it is quite difficult to manage the work and make sure to upgrade the efficiency of the research by a substantial margin. Considering this research, I was not able to adopt the process through which the adoption of effective cyber security strategies is developed (Ahmed, 2020). There are multiple types of strategies available in the present global cyber security measures, but ensuring proper implementation of the strategies to support an integrated IoT system is a tough job. Another critical feeling that I have been able to accumulate while implementing the security interfaces is regarding finding the regulatory frameworks. It is tough to find out the best regulatory framework and implement those into the situation with proper measures. Even in the case of protecting critical information infrastructure, there are possibilities of facing mechanism related concerns and issues related to its proper implementation. According to the interface or the IoT system, the strategic evaluation will prove to be the best one. Another critical strategy required to fulfil the security provision of the integrated IoT system is related to the deployment of e-governance services. It is quite hectic to deploy or secure e-governance services within an IoT interface and ensure its potential output bindings (Nejabatkhah et al., 2020). But in this context, it is imperative and relevant to state that I have gathered a significant number of skills related to cyber security strategy development and my ability enhancement in tough situation handling. Without being able to acquire such skills, I might have faced different problems in the letter part of the project where I needed to deploy the strategies in an efficient measure along with ensuring the fact that this is the best set of strategies which can enhance the potential ability of the research or the integrated IoT system. While accomplishing the task, I have also faced a relevant amount of self-doubt in deploying the adopted exploratory research design (Taeihagh and Lim, 2019). The exploratory research design having the ability to adopt changes according to the research progress has made the task much easier for the researchers like me, who had very few opportunities to complete it without such an influential research design. In the potential future development, there will be coefficient abilities coming into my path where I will be able to signify the proper strategy without taking too much time.
Evaluation
According to Fielder et al. (2018), the received subject determining effective cyber security strategies to support integrated IoT systems has a large amount of resource availability in the present market. But the chance of adopting those and making a significant change within the operation procedure is a substantially important and relevant act of consideration. But from the personal learning point of view, it is relevant and important to identify the critical requirements associated with the whole progressive idea of deploying cyber security strategies within the integrated IoT system procedure of operation. Relevant aspects are coming in where the need of securing all the associated data is an essential task. It is imperative and relevant that the security measures related to the system are achieved without facing any difficulties. Another integrated evaluation suggests that critical information infrastructure development is not an easy task where critically evaluating or suggesting the methodologies are a very important aspect of the research. To provide a proper security interface, it is very important to abide by the cyber security frameworks like ISF, ISO/IEC 27001, and NIST CSF (Ghadge et al., 2019). In the context of implementing all these cyber security frameworks, it is important to earn or gather the relevant amount of information about all these. Even making sure about the IT resource management policies is a very important task to be assigned with all these frameworks and implement them properly and efficiently for natural habitat development. Apart from all these measures are one of the integral parts of the research that suggests cyber security strategy has a potential chance of being called a cyber security framework associated with the industrial standards and coefficient development policies associated with these types of standards of operation (Andrade, Ortiz-Garcés and Cazares, 2020). The most important part of these implementations or framework development is to procure or propose strategies that can secure the environment associated with the IT interface and IoT based system.
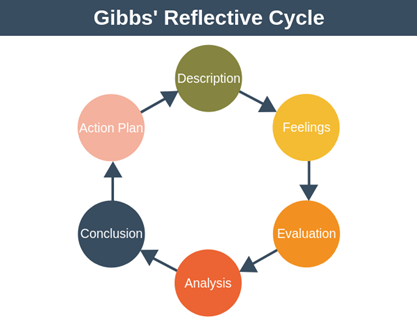
Figure 1: Gibbs reflective cycle
(Source: Boiko, Shendryk and Boiko, 2019)
Analysis
While analysing the progress of the whole scenario and the implementable face of operation associated with the aim of the project-based research to determine effective cyber security strategies to support an integrated IoT system, it can be evaluated that the whole implementation of this system interface is developed for some time between 3 to 5 years (Boiko, Shendryk and Boiko, 2019). To secure all the services and ensure proper implementation of all these measures, it is important to upgrade the security interfaces associated with the cyber security strategies and block all the efficient cyber security trades according to the time measures. Without being able to do so, the chance of getting affected by the cyber security threats and the whole data associated with the integrated IoT system getting lost is high. This also enhances the chance of data loss or male practice associated with the data. One of the most efficient identifications which I have been able to understand after completing the research clearly States the fact the inventories associated with digital measures along with personal and window based measures to ensure proper safety and IT infrastructure requires potential attention at every certain point of referring or every certain change of threats (Gunduz and Das, 2020). Any set upset coming into the path of the integrated IoT system needs to be given the proper amount of importance and add strategic evaluation or strategic direction towards the impact of the issue or threat. By strategic upgradation of the module or security standards, the chance of deploying or blocking any setup cyber security trade into the integrated IoT system gets enhanced. In context to enhance the security purposes, it has also been evaluated that the cyber security threats need to be evaluated or implemented without taking any set of time after evaluation. By every set of data integration and proper identification of all those or even by critically enhancing the infrastructural benefits, the chance of deploying security measures tends to increase by a sufficient medium. The analysis accounted for by my prior experience and the experience of working within the research-based project also helped me compose my abilities towards fact-finding and critically availability of any set of cyber security threats coming over an integrated IoT based system (Tawalbeh et al., 2020). In the future composition of the operations or deployment of any set of cybersecurity-related measures, I will be efficient enough to identify and observe any set of threats coming into the path of the system. These factors will also enhance my capability to implement and ensure critical resources to any security interface associated with the internet of things and the security protocol development of an organisation.
Conclusion
As a brief evaluation and identification, I have been able to conceptualise and adapt multiple types of eventual learnings within this present project-based research task. The first and the most important aspect of my observation and skill enhancement is to enable the opportunity to complete research within a team (Vitunskaite et al., 2019). According to my value stream and whole identification, it is very important to be a good team player for completing any Research. I have been able to sustain in different situations and adapted different skills related to teamwork, like understanding the consequences of situations and leading the team according to its requirements and many other aspects. I have been able to adapt to the good quality of cyber security threat detection. Identifying the risk associated with any type of system or procedure is an important task. With time and completion of the research, I have detected those without facing too much trouble. Being able to do those will help me enhance my potential ability towards a sustainable gain in the IT industry and secure the interfaces I will be working on. Even in the case of working on future projects, I will also be efficient and adaptable towards the situational analysis and completion of the research within a time frame. Time-bound work completion is also one of the strategic factors that I have determined and accomplished while completing the research. Having a credible amount of time adjustment ability is very important, and this can lead to proper project findings and evaluation of statistical benefits. Along with all these factors, I have also been able to identify the most critical cyber security strategies like creating a secure cyber ecosystem creating an assurance framework securing e-governance services creating mechanisms for its security, and many others. An in-depth operation and knowledge or knowledge of implementation will help me gather much greater amounts of relevant and influential abilities for my capability enhancement and IT infrastructure support development in future (Mayer et al., 2019). Mitigating the cyber security trades is not a very easy task. Still, with the adoption of all these concerns and practices, I will be able to do all the stars without facing a relatively higher amount of issues.
Action plan
Developing a proactive action plan associated with the proper identifications and opportunity enhancement in my skill base will be a great task for me to accomplish. The first impact making skill which I have been able to accurately and has the potential to implement in future is related to my team working skill. In the future, while working on any type of project, I will be efficient in adapting to the situation without taking too much time and will have the potential to lead the team if required. Team leadership is one of the aspects which I was looking to adapt according to the methodologist or my goal based identification out of the research. I am quite happy and enthusiastic about adopting the skills or being able to adopt skills which I was looking to adopt at any cost (Hermanto, 2018). The critical abilities that I have gathered related to cyber security strategies will have a substantial part in my future practices related to the adaptability of cyber concerns or to mitigate any type of cyber threats coming over any interface or IoT-based integrated system. Being able to strategise the facts or having the coefficient ability to identify the strategic requirements coming within a cyber security trade management or cyber security strategic development procedure will be easy for me. In future projects, if a task is assigned to me which requires proper adoption of cyber security strategies will become a task of my preference. With previous knowledge about cyber security strategies, deploying skills according to the requirements will be easy. The strategic implementation path associated with those will also be influential in blocking the cyber security concern or threats. Another influential way of the operation coming into my path or one of the skills I have gathered and am quite confident to implement in my future research is related to the skill of proper identification of cyber threats. Identifying these cyber threats is very important and one of the proper requirements for cyber threat strategy development or support development for integrated IoT systems or any type of IT infrastructure or digital mechanism (Tawalbeh et al., 2020). With such an influential amount of capability and a considerable amount of probabilities to deploy all these procedures, I will be one of the efficient researchers to increase the efficiency of cyber security strategies and deploy those according to its requirements. There will be possibilities or opportunities coming into my path where I will be effective and efficient towards cyber security strategy development and providing proper support to any cyber security concerns to projects, research or any medium facing concerns related to cyber security attacks.
Conclusion
In this report, a brief evaluation related to the findings and skill-based efforts or abilities that I have gathered out of the research base project determining effective cyber security strategies to support an integrated IoT system has been demonstrated with the proper use of the Gibbs reflective cycle. One of the key reasons for using the reflective cycle is to enhance the credibility of findings and skill enhancements appropriately to sustain an opportunity to implement those in future references or projects of mine. In the initial part of the project, a brief demonstration about the key goals associated with the project for me is described and made sure which are being achieved. Then the report finds out or critically reproduces the feelings I have gathered over time and implements them for coefficient ability generation within the research-based project. Even the project has given a proper evaluation of the factors relevant to the context of my skill learning or my goal accomplishment through the project. One of the critical findings associated with the project is being demonstrated through the help of proper analytical functions and analysis of the facts, which I considered to be very effective and influential in my future orientation. Even all the facts are knowledge which I have gathered along with the skills which I have been able to pursue with this research waste project are referred to in this report and make sure all the future practices or implementations which I will be able to deploy in my future learning and works are also described in it.
Reference list
Adeani, I.S., Febriani, R.B. and Syafryadin, S., (2020). USING GIBBS’REFLECTIVE CYCLE IN MAKING REFLECTIONS OF LITERARY ANALYSIS. Indonesian EFL Journal, 6(2), pp.139-148. http://journal.uniku.ac.id/index.php/IEFLJ/article/download/3382/2034
Ahmed, A.M., (2020). From reluctance to addiction: The impact of reflective journals on Qatari undergraduate students’ learning. Reflective Practice, 21(2), pp.251-270. https://www.tandfonline.com/doi/pdf/10.1080/14623943.2020.1735328
Andrade, R.O., Ortiz-Garcés, I. and Cazares, M., (2020, July). Cybersecurity attacks on Smart Home during Covid-19 pandemic. In 2020 Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4) (pp. 398-404). IEEE. https://www.researchgate.net/profile/Roberto-Andrade-7/publication/344785490_Cybersecurity_Attacks_on_Smart_Home_During_Covid-19_Pandemic/links/603e664fa6fdcc9c780c4e0b/Cybersecurity-Attacks-on-Smart-Home-During-Covid-19-Pandemic.pdf
Boiko, A., Shendryk, V. and Boiko, O., (2019). Information systems for supply chain management: uncertainties, risks and cyber security. Procedia computer science, 149, pp.65-70. https://www.sciencedirect.com/science/article/pii/S1877050919301152/pdf?md5=0d9e21d8b62a5770fcf40e27920470e4&pid=1-s2.0-S1877050919301152-main.pdf
Fielder, A., König, S., Panaousis, E., Schauer, S. and Rass, S., (2018). Risk assessment uncertainties in cybersecurity investments. Games, 9(2), p.34. https://www.mdpi.com/2073-4336/9/2/34/pdf
Ghadge, A., Weiß, M., Caldwell, N.D. and Wilding, R., (2019). Managing cyber risk in supply chains: A review and research agenda. Supply Chain Management: An International Journal. https://www.academia.edu/download/61398732/Managing_cyber_risk_in_supply_chains20191202-60324-1lqjlbj.pdf
Gunduz, M.Z. and Das, R., (2020). Cyber-security on smart grid: Threats and potential solutions. Computer networks, 169, p.107094. https://e-tarjome.com/storage/panel/fileuploads/2020-01-27/1580123093_E14222-e-tarjome.pdf
Hermanto, A., (2018). Integration of EA and IT service to improve performance at higher education organisations. In MATEC Web of Conferences (Vol. 154, p. 03008). EDP Sciences. https://www.matec-conferences.org/articles/matecconf/pdf/2018/13/matecconf_icet4sd2018_03008.pdf
Li, Y., Chen, W., Liu, C. and Deng, M., (2020). Nurses’ psychological feelings about the application of Gibbs reflective cycle of adverse events. American Journal of Nursing, 9(2), pp.74-78. https://pdfs.semanticscholar.org/deb5/86a11508fe8b5cc51f490596d98f7659bdcd.pdf
Mayer, N., Aubert, J., Grandry, E., Feltus, C., Goettelmann, E. and Wieringa, R., (2019). An integrated conceptual model for information system security risk management supported by enterprise architecture management. Software & Systems Modeling, 18(3), pp.2285-2312. http://nmayer.eu/publis/Mayer%20et%20al.%20-%20SoSyM18.pdf
Nejabatkhah, F., Li, Y.W., Liang, H. and Reza Ahrabi, R., (2020). Cyber-security of smart microgrids: A survey. Energies, 14(1), p.27. https://www.mdpi.com/1996-1073/14/1/27/pdf
Sekarwinahyu, M., Rustaman, N.Y., Widodo, A. and Riandi, R., (2019, February). Develop problem-based learning for online tutorial program in plant development using Gibbs’ reflective cycle and e-portfolio to enhance reflective thinking skills. In Journal of Physics: Conference Series (Vol. 1157, No. 2, p. 022099). IOP Publishing. https://iopscience.iop.org/article/10.1088/1742-6596/1157/2/022099/pdf
Süzen, A.A., (2020). A Risk-Assessment of Cyber Attacks and Defense Strategies in Industry 4.0 Ecosystem. International Journal of Computer Network & Information Security, 12(1). https://www.mecs-press.org/ijcnis/ijcnis-v12-n1/IJCNIS-V12-N1-1.pdf
Taeihagh, A. and Lim, H.S.M., (2019). Governing autonomous vehicles: emerging responses for safety, liability, privacy, cybersecurity, and industry risks. Transport Reviews, 39(1), pp.103-128. https://www.tandfonline.com/doi/pdf/10.1080/01441647.2018.1494640?needAccess=tr&
Tanaka, M., Okamoto, R. and Koide, K., (2018). Relationship between Reflective Practice Skills and Volume of Writing in a Reflective Journal. Health, 10(3), pp.283-288. https://www.scirp.org/journal/paperinformation.aspx?paperid=83028
Tawalbeh, L.A., Muheidat, F., Tawalbeh, M. and Quwaider, M., (2020). IoT Privacy and security: Challenges and solutions. Applied Sciences, 10(12), p.4102. https://www.mdpi.com/2076-3417/10/12/4102/pdf
Tawanwongsri, W. and Phenwan, T., (2019). Reflective and feedback performances on Thai medical students’ patient history-taking skills. BMC medical education, 19(1), pp.1-8. https://link.springer.com/article/10.1186/s12909-019-1585-z
Vitunskaite, M., He, Y., Brandstetter, T. and Janicke, H., (2019). Smart cities and cyber security: Are we there yet? A comparative study on the role of standards, third party risk management and security ownership. Computers & Security, 83, pp.313-331. https://dora.dmu.ac.uk/bitstream/handle/2086/17616/SmartCitiesV3.pdf?sequence=1&isAllowed=n
Know more about UniqueSubmission’s other writing services: