LD7091 Assignment Sample – Research Methods for Professional Practice 2022
Part A: Reflective CPD
1.1. Self Reflection
From my past learning outcomes through engagement with various academic assignments and projects I have achieved knowledge on professional research. The most potential skills I have achieved in my past with help of my academic activities and personal effectiveness are leadership skills, decision-making skills, problem-solving, writing and research abilities.
I had developed leadership skills by learning about major global leaders such as Sundar Pichai, Mother Teressa and others by focusing on their leadership styles. In addition, my academic engagement with classmates for completing group tasks has also contributed to the achievement of servant leadership skills. I had learned appropriate decision-making skills and assertive communication strategies for business management through my past experiences and learning outcomes.
All the academic assignment and project work associated with a business plan and business proposal development process has contributed to the achievement of advanced writing skills for representing ideas in a proper descriptive way. Engagement with professional research methodology has helped in the development of investigation skills in order to develop potential marketing plans and strategies for growth and development of business.
According to the view of Anders (2018), ability to identify research topics, identifying dependent and independent variables, review of existing literature and selection of appropriate methodology is major past achievements. During attaining lectures on professional research practices, I have learnt the art of selecting appropriate research topics by identifying a challenge or issues.
1.2. Personal SWOT
| Strength
● Active communication skill ● Decision-making skill ● Problem analysis skills ● Understanding on research methods for professional practices ● Technical knowledge |
Weakness
● Low emotional intelligence |
| Opportunity
● Improvement of personal effectiveness ● Learning business management ● Learning of advanced cyber security |
Threats
● Occupational hazards ● Taking emotional decisions |
Table 1: Personal SWOT
(Source: Student)
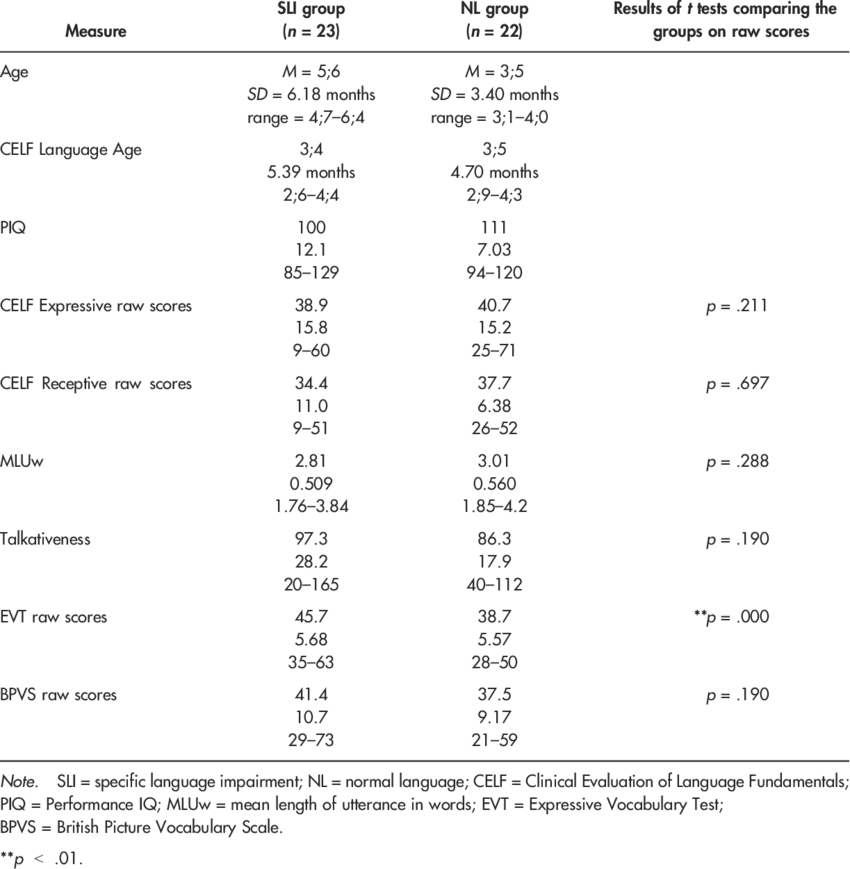
Figure 1: Result of psychometric test
(Source: Jobtestprep.co.uk)
Strength area: The areas of strength which have been developed over past years are negotiation skills, decision making, problem analysis, research methodology and technical skills. In the words of Wilson et al. (2017), the presence of assertive communication skills helps in management of the relationship with team members in business management and communication with participants during research work. A
dvanced decision-making skills are a major strength that helps in reducing problems and crises identify best alternatives for a specific problem. The presence of decision-making skills also helps in professional development for managing business and academic performance with appropriate analysis and decision.
As argued by Valiandes and Neophytou (2018), ability to solve problems through identifying root causes and developing appropriate mitigation strategies is a major strength necessary for improvement of leadership abilities.
The existence of problem-solving ability can help in managing good relationships with internal and external stakeholders for achievement of business goals and objectives in the future. It can also contribute to maintaining the standard and validity of research findings by selecting the most appropriate methodology.
According to the view of Rubens et al. (2018), having clear ideas regarding data collection and analysis methodology is a major personal advantage necessary for successful completion of the dissertation. Knowledge of computers for understanding various aspects of cyber security and information safety can help in developing aims and objectives in the dissertation.
This process can also contribute to development of appropriate research questions for demarcation of the limitations to identify potential research areas.
Weaknesses: Getting highly influenced by emotion in the decision-making process and taking occasional decisions based on an emotional level instead of logical and reasonable is one of the potential weaknesses identified in personal SWOT.
As per the view of Rubens et al. (2018), using emotions in team interaction in business or academic activities and taking emotional decisions in research work can result in a negative impact on quality standards of the potential outcome. Identification of an innovative strategy for managing self emotion in order to focus on aims and objectives of the research work is necessary (Wilson et al. 2017).
Opportunity: The most potential opportunities for development of professional skills for future improvement of personal effectiveness, developing business management skills and learning of advanced cyber security. In the words of Snyder (2019), communicating with research guides and Research participants can contribute to the development of personal effectiveness by improvement of communication and listening skills.
The utilisation of potential resources available on research methodology, books on business management and leadership has opportunities for improvement of personal skills which is necessary for personality development and succeeding in professional fields.
According to the view of Wilson et al. (2017), engagement with research work can provide the opportunities of reviewing existing literature that can help in development of business knowledge by exploding relevant theories and concepts. In addition, the development of research proposals and dissertations on topics associated with cyber security can create opportunities for learning about the importance of cyber security software for maintenance of privacy and avoiding cyber attacks.
Threats: Facing occupational hazards that can affect health and work-life balance is a potential threat identified in personal SWOT. According to the view of Abutabenjeh and Jaradat, (2018), resulting in failure in maintaining a high standard of dissertation due to influence by emotional decisions is another potential threat.
1.3. Personal Development Plan
| Activities | Duration |
| Area of interest | 2 days |
| Proposal | 1 week |
| Literature review and aim or objectives | 3 weeks |
| Research methodology selection | 1 week |
| Data collection | 2 weeks |
| Analysis of data | 1 week |
| Drafting | 2 days |
| Final Submission | 2 days |
Table 2: Timeline
(Source: Zangirolami-Raimundo et al. 2018)
For successful completion of research work, the above timeline will be followed for maintenance of sequence. According to the view of Abutabenjeh and Jaradat, (2018), the major activities associated with a personal development plan for future success of resource proposal and dissertation are analysing area of interest, proposal, literature review, methodology selection, data collection, data analysis and final submission.
Relevant sources: Google Scholar, ProQuest, and news articles will be considered as major sources of information for successful personal development plans associated with research work. PRISMA models of inclusive and exclusive criteria will be considered for the identification of potential resources from the database (Abutabenjeh and Jaradat, 2018).
Part B: Research Log
1. My research interest

2. Personal swot
3. First research interest

4. Stages of a research project

5. Personality and learning style
6. CV preparation and reflect

Part C: Project Proposal
Topic- Role of HRM in addressing cyber security challenges in modern business world
3.1. Introduction
Brief summary
The study is intended for conducting an investigation on identifying the potential role of Human Resource Management in addressing cyber security challenges in a competitive business environment. The reason for selecting the research topic on cyber security is increasing Cyberattack cases due to pandemics in 2020 and 2021. Management of organisational confidential information and privacy of employees or customers has become a major issue in business management.
Reason and justification
The major reason for intending towards conducting research on analysing the role of HRM in cyber security issues is increasing Cyberattack and cyber breaches globally. This project is worthwhile in the ability to represent professional research methods and representation of HRM in cyber security management.
According to the view of Mohajan (2018), identification of professional research methods will help in development of business management practices by conducting market research before development and implementation of a marketing plan. In addition, identification of potential role played by HRM in the cyber security process will provide proper guidelines to organisations for restructuring of Human Resource Management strategy for maintaining privacy of employees and customers, confidentiality of information and access control.
Management of cyber security challenges with innovative methodology is necessary for business survival and avoiding financial loss and damaging of brand image. This study is relevant with students for the perspective of development of professional knowledge on research methodology that can contribute to professional development (Basias and Pollalis, 2018).
In addition, the considered activities and proposed research topic are related to computing from a security perspective because a cyber attack is a major challenge in computing management that negatively affects business performance.
Aims
The aim of studies is to identify potential roles play that HRM in identifying cyber security issues for ensuring effective business management.
The project will focus on achieving a great understanding of the contribution of HRM strategies in manager information and cyber security of business organisations and their respective reflection on international market performance. Identification of innovative strategies for minimising cyber security threats for business organisations will be another potential goal of this research work.
Research scope and objective
Identification of major cyber security issues, potential challenges faced by the HRM department and contribution of services in business performances will be the major scope of the study. The study will focus on identifying potential threats in cyber security management and their potential impact for identification on business management for identifying improvement strategies of marketing performances through data protection.
Objectives:
- To understand the major role and responsibility of Human Resource Management in maintaining cyber security of company
- To evaluate major challenges of controlling data privacy and access control in companies without appropriate cyber security software
- To develop a potential solution for minimising vulnerabilities of cyber attack
SMART objective
| Specific | Measurable | Achievable | Relevant | Time bound |
| To identify contribution of HRM in addressing cyber security in business organization | To protect data and information from interfering of the third party | To achieve business goals and objectives by reducing possibilities of cyber breach and attack | To developed HRM strategy based on access control elements for proper flow of information and data | To complete understanding of research methods and importance of cyber security within 1 month. |
Table 3: SMART Objective
(Source: Zangirolami-Raimundo et al. 2018)
Research question
Q1. What are the major roles and responsibilities of Human Resource Management in maintaining the cyber security of a company?
Q2. What are the potential challenges of controlling data privacy and access control in companies without appropriate cyber security software?
Q3. What can be the capable solution for minimising vulnerabilities of a cyber attack?
3.2. Literature Review
3.2.1. Concept HRM department of the organisation
HRM stands for Human Resources Management which is a process of bringing new people within the organisation while hiring or recruiting them for the organisation. As cited by Shaban (2019), it is found from the previous studies that the effective management of employees in an organisation mainly assists to bridge the potential gap between the employee’s performances along with the organisation strategic objectives for the betterment of the organisation.
Additionally, an efficient HR management team can assist the organisation to achieve an edge over the competition in the marketplace. Besides, the role of HRM in addressing cybersecurity challenges as HRM is responsible for hiring and recruiting the professional or employee with adequate knowledge for the handling and tackling the challenges related to cybersecurity.
Cybersecurity challenges are considered threats in the modern business world because most business organisations are connected and represent their operations and functions over the internet. HRM plays a crucial role in determining and enforcing employee data permission along with providing appropriate training and enforcement of cybersecurity procedures and processes which is helpful for the organization to encounter potential cybersecurity challenges and events involved among the employees within the organisation (RAHMAN and AYDIN, 2019).
3.2.2 Emerging challenges of cybersecurity in the present business world
In the present business world, most of the business is conducted and executed over the internet where the emergence of cybersecurity arises. Cybersecurity is one of the main concerns among the business as it holds the potential for impacting the overall business operation and functions and even shutting down business for a couple of days.
As narrated by Griffy-Brown et al. (2019), various types are related to cybersecurity such as Ransomware, Phishing attacks, BYOD policies, outdated hardware and Insider attack. Additionally, ransomware attacks are considered as the most impacting cybersecurity attacks among other attacks as they severely impact the operations and functions in an organisation.
Ransomware attacks involve hacking of business data and preventing them from accessing their data until a certain ransom amount is paid to the attackers. Besides, phishing attacks are another type of attack which is associated with cyber security where the attacker utilises the social engineering attacks on the employees to steal the data related to business including credit card details, login credentials and many other data which are confidential for the business operations and function.
These attacks are considered as challenges incurred in businesses of the present era where everything is digitally stored and accessed over the internet (Hussain et al. 2020).
3.3.3. Impact of HRM on mitigating the challenges of cybersecurity
The potential impacts of HRM on mitigating the challenges of cybersecurity are huge as the HRM are responsible for enforcing and determining the employee’s data permission for the specific applications or specific areas which regular employees are unauthorised to access.
As stated by Cirnu et al. (2018), the HRM assists the organisation in mitigating the potential cybersecurity attacks beforehand while providing adequate knowledge and understanding along with proper training on cybersecurity for mitigating the possible attacks.
Moreover, HRM utilises certain strategies for mitigating the possible cybersecurity attacks within their organisation while providing enough training and enforcing specific procedures for avoiding attacks and for mitigating potential attacks which includes strategies. For example, raising awareness, leveraging trusted resources, building an economic framework, working with the invested partners and implementing response plans.
These strategies are considered crucial for the HRM to mitigate the challenges associated with cybersecurity. Moreover, raising awareness strategy includes providing enough information on the type of attacks, potential ways for executing the attacks along with implementing specific measures for avoiding attacks. Measures that are delivered and implemented by the HRM within an organisation are the use of strong passwords, applying system updates in an efficient and timely manner, securing devices while enabling firewalls and ways to avoid phishing attacks (Pham et al. 2021).
3.3.4. Theories and models
Strategic contingency theory: Strategic contingency theory focuses on the tasks which are required to solve in the form of problems or issues while de-emphasizing personality. As per the theory, it can be helpful for organisations to avoid and mitigate the potential cyber-attack within the organisation which can impact overall operation and functions.
As narrated by Steinbach et al. (2017), strategic contingency theory refers to a leader depending on their problem-solving skills along with projective personality in the centre stage. This provides the opportunities to the HRM for leading the employees based on their problem-solving skills while enforcing the possible mitigation steps, policies such as BYOD (Bring Your Device) along with procedures such as usage of a strong password, a combination of alphanumeric and symbols.
General systems theory: General systems theory refers to the skeleton of science which focuses on providing a framework and structure of systems on which flesh and blood of any stream could be hanged together for the benefit of the organisation. There are multiple key concerns of the theory which can be helpful for the HRM to mitigate and avoid cyberattacks while implementing cybersecurity within the organisation.
The concepts are open and closed systems, the significance of environment and context along stressing the role. These are considered as the concept of the theory which can assist the HRM for the handling of cyber-attacks and mitigating to minimum acceptable impact for the organisation which does not hold the potential for impacting the overall operations and functions (Chatterjee et al. 2021).
3.3.5. Literature Gap
The potential literature gap can be identified and determined as a shortage of information related to different concepts of HRM and cybersecurity due to the limitation of word count for the study. As stated by Remko (2020), the study has not evaluated the possible model on HRM and cybersecurity which can provide information on the implementation phases of cybersecurity within an organisation. Additionally, identification and reviewing of relevant authors and journals are not evaluated in this study for providing a better understanding of the topic.
3.3. Research methodology and Planning
3.3.1. Research Philosophy
In research philosophy, it is believed by the researcher to determine information related to circumstances that can be collected, analysed and utilised for conducting the study work for the betterment. As cited by Žukauskas et al. (2018), the selected and suitable research philosophy is identified and considered for conducting the entire study is positivism research philosophy approach where the researcher will determine the sources of information and its nature which can be considered for the investigation process to explore study questions and objectives.
The researcher evaluated and considered the other research philosophies like pragmatism and realism research philosophy for conducting this study work. However, due to certain limitations in other philosophies may affect the authenticity and reliability of the study therefore realism and pragmatism are not selected for this study to deliver high-quality study work with adequate information and authentic data for the readers and viewers (Hürlimann, 2019).
3.3.2. Research Approaches
The research approach which is involved with various ways for modulating the methodologies in this study work for the rechecking out to required data is essential for the study work to complete. Multiple types of research approaches assist study work for providing required information and knowledge on the topic for completing the study work with the deadline.
Amongst the multiple research approaches, the researcher has selected and determined a deductive research approach for this study work to acquire adequate information on the concept of HRM and the concept of cybersecurity along with impacts of cybersecurity challenges (Prayag et al. 2019).
3.3.3. Research Design
Research design assists study work for representing the possible ways of presenting the potential finding to the readers and viewers for their future usage along with usage of prime information related to associated fields or domains are considered. As stated by Sahin and Mete (2021), different types of research designs are used by the researchers for the research work; however, for this study, the researcher identified and considered descriptive research design amongst exploratory, conclusive and exploratory research designs.
Therefore, this entire study will be conducted while using the descriptive research designs where evaluation and determining contexts related to the study topic will be evaluated for delivering better insights on the study work. Moreover, the concept of cybersecurity for HRM, impacts of cybersecurity on HRM operations along with possible mitigation strategies which can be imposed by the HRM within an organisation for mitigating cyberattacks will be evaluated in-depth.
The selected research design will assist this study work in identifying and focusing on the multiple dimension representation while providing arguments and counter-arguments. Considering the research design can be helpful for the study work to deliver positive and negative contexts related to the study topic for providing authentic and reliable insights in this study (Aquino et al. 2018).
3.3.4. Data Collection method
Data collection methods refer to selecting, sorting and applying the appropriate information from the collected data. The method of collection of data and information is called the data collection method. As cited by Johnston (2017), there are two types of data collection methods for collecting data or information for conducting the research work that includes primary data collection methods and secondary data collection methods.
The best and suitable data collection method selected for this study will be a secondary data collection method for collecting information and data.
The secondary data collection method involves the collection of data and information related to study topics from the existing sources such as existing journals, articles, blogs and websites.
Moreover, secondary data collection methods can be helpful for the researcher to acquire benefits such as cost-saving and time management which can assist the researcher in completing this study work with the deadline. Additionally, researchers will identify and determine the appropriate resources or information based on the study topic and related keywords such as cybersecurity, HRM and cyberattacks.
The major advantage of selecting the secondary data collection method will be abundant availability of resources and information which can be useful for the researcher to conduct the study work successfully while delivering adequate information on the topic and related contexts (Garcia and Mayorga, 2018).
3.3.5. Data analysis techniques
Data analysis techniques are considered as crucial for the research work as it assists the researcher to evaluate and analyse the collected data or information to provide in-depth insights on the topic for the betterment and to develop the quality of findings.
As stated by Jackson et al. (2018), there are two types of data analysis techniques that are utilised for the analysis and interpretation of collected data and the techniques are qualitative and quantitative analysis techniques. Therefore, the researcher selected the qualitative data analysis technique for the evaluated and analysing the collected data from the existing resources.
Qualitative data analysis can be helpful for the researcher to avoid statistical information for this study work while helping to interpret the data based on observation and creating appropriate themes.
Thematic analysis can be helpful for this study work as it can provide the researcher with adequate information and knowledge for conducting the study work in a proper systematic way while delivering quality work to the readers and viewers. However, a broad discussion can be acquired by researchers for this study work which will be the potential advantage of practising qualitative analysis for this study work.
3.3.6. Timeline
3.3.7. Ethical consideration
| Deliverables | ● Project plan
● Project budget ● Project Charter |
| Resources | ● Journal
● Articles ● Blogs ● Websites |
| Skills | ● Leadership
● Communication ● Scheduling ● Risk management |
| Time | ● Data Collection 2 weeks
● Data analysis 1 week |
| Milestones | ● Improvement of HRM
● Improvement of research skills ● Professional development |
| Methods to be used | ● Secondary |
| Costs of time and resources | ● Approximately 1 month |
Table 4: Ethical consideration
(Source: Zangirolami-Raimundo et al. 2018)
3.4. Conclusion
Ethical issues
Ethical issues which can affect the project delivery are proper identification of theories and models which can align with both HRM and cybersecurity for the best possible results. Moreover, multiple ethical issues which could impact the in-progress project work are accountability, conflict of interest, and health and safety concerns along workplace environment.
As the entire project will be conducted based on the secondary data collection method their favouritism can impact the in-progress project work while delivering wrong ideas and thoughts related to the study topic for the viewer and readers (Hunter et al. 2018).
Legal issues
As the entire project work is a secondary resource therefore proper credit must be entitled to the project work along with the proper reference. However, lack of references may affect the in-progress project work as it can lead to plagiarism and copying of ideas and thoughts.
As narrated by Prabandari et al. (2020), privacy and data protection laws and regulations must be considered while conducting the project work otherwise as per the UK government it could lead to violation of the data protection act (2018) and the privacy act (1974). These are potential legal issues that can impact the progress of the project work.
Security consideration
Protection of data by following the Data Protection Act 2018 under UK legislation will be a major security consideration for the maintenance of transparency in the research findings. Identification of potential possible security issues by conducting risk analysis will help in minimising problems of managing data during the interpretation process.
In addition, effective management of transparency and research ethics during data collection and analysis will be a potential security consideration for increasing the validity and reliability of the study. The study will also focus on developing direct conclusions by highlighting major findings in the results section for contributing to existing literature.
Professional consideration
Management of timelines, sequence of research methodology, proper resource instrument and selecting of appropriate data collection and analysis method will be the major professional consideration of this study. In professional practice, consideration of a timeline by distributing different activities in an appropriate format helps in completing the research work in the estimated time.
This process contributes to the maintenance of standards and transparency of different steps of professional resources. Following the sequence in research methodology that includes development of aim and objective, review of existing literature, selection of methodologies and data collection and analysis is necessary for achieving targeted objectives.
Proper sequence management helps in identifying underlying issues and the potential mitigation strategy for the development of qualitative findings in order to justify research questions.
Identification of quality resources by following inclusive and exclusive criteria with appropriate Framework as a research instrument is another professional consideration that needs to be added in the study. This process will be in maintenance of quality in data collection and analysis identification of relevant and accurate journal articles.
Legal and social aspects of this area are not applicable in this project associated with HRM and cyber security. Legal aspects are mainly concerned with maintenance of law and order and transparency during Business expansion and entering a new marketplace.
However, social aspects are mainly associated with understanding customer buying behaviour in psychology towards product and brand image. In this research work, complete focus will be given on exploring Human Resource Management and cyber security for understanding computing conservation on business management. Therefore, it can be stated that legal and social aspects are not necessary for this research work.
References
Abutabenjeh, S. and Jaradat, R., 2018. Clarification of research design, research methods, and research methodology: A guide for public administration researchers and practitioners. Teaching Public Administration, 36(3), pp.237-258. https://journals.sagepub.com/doi/abs/10.1177/0144739418775787
Anders, A.D., 2018. Networked learning with professionals boosts students’ self-efficacy for social networking and professional development. Computers & Education, 127, pp.13-29. https://www.sciencedirect.com/science/article/pii/S0360131518302136
Aquino, E., Lee, Y.M., Spawn, N. and Bishop-Royse, J., 2018. The impact of burnout on doctorate nursing faculty’s intent to leave their academic position: A descriptive survey research design. Nurse education today, 69, pp.35-40. https://www.sciencedirect.com/science/article/pii/S0260691718302818
Basias, N. and Pollalis, Y., 2018. Quantitative and qualitative research in business & technology: Justifying a suitable research methodology. Review of Integrative Business and Economics Research, 7, pp.91-105. https://sibresearch.org/uploads/3/4/0/9/34097180/riber_7-s1_sp_h17-083_91-105.pdf
Chatterjee, S., Sarker, S., Lee, M.J., Xiao, X. and Elbanna, A., 2021. A possible conceptualization of the information systems (IS) artifact: A general systems theory perspective 1. Information Systems Journal, 31(4), pp.550-578. https://onlinelibrary.wiley.com/doi/abs/10.1111/isj.12320
Cirnu, C.E., Rotună, C.I., Vevera, A.V. and Boncea, R., 2018. Measures to mitigate cybersecurity risks and vulnerabilities in service-oriented architecture. Studies in Informatics and Control, 27(3), pp.359-368. https://www.researchgate.net/profile/Radu-Boncea/publication/328628189_Measures_to_Mitigate_Cybersecurity_Risks_and_Vulnerabilities_in_Service-Oriented_Architecture/links/5d231c57a6fdcc2462caa402/Measures-to-Mitigate-Cybersecurity-Risks-and-Vulnerabilities-in-Service-Oriented-Architecture.pdf
Garcia, N.M. and Mayorga, O.J., 2018. The threat of unexamined secondary data: A critical race transformative convergent mixed methods. Race Ethnicity and Education, 21(2), pp.231-252. https://www.tandfonline.com/doi/abs/10.1080/13613324.2017.1377415
Griffy-Brown, C., Lazarikos, D. and Chun, M., 2019. Emerging technologies and cyber risk: How do we secure the internet of things (IoT) environment. Journal of Applied Business and Economics, 21(2), pp.70-79. http://homepages.se.edu/cvonbergen/files/2019/05/Work-Non-Work-Boundaries-and-the-Right-to-Disconnect.pdf#page=71
Hunter, R.F., Gough, A., O’Kane, N., McKeown, G., Fitzpatrick, A., Walker, T., McKinley, M., Lee, M. and Kee, F., 2018. Ethical issues in social media research for public health. American journal of public health, 108(3), pp.343-348. https://ajph.aphapublications.org/doi/abs/10.2105/AJPH.2017.304249
Hürlimann, C., 2019. Research Philosophy and Ethics. In Valuation of Renewable Energy Investments (pp. 111-126). Springer Gabler, Wiesbaden. https://link.springer.com/chapter/10.1007/978-3-658-27469-6_3
Hussain, A., Mohamed, A. and Razali, S., 2020, March. A Review on Cybersecurity: Challenges & Emerging Threats. In Proceedings of the 3rd International Conference on Networking, Information Systems & Security (pp. 1-7). https://dl.acm.org/doi/abs/10.1145/3386723.3387847
Jackson, K., Paulus, T. and Woolf, N.H., 2018. The walking dead genealogy: Unsubstantiated criticisms of qualitative data analysis software (QDAS) and the failure to put them to rest. The Qualitative Report, 23(13), pp.74-91. https://nsuworks.nova.edu/tqr/vol23/iss13/6/
Jobtestprep.co.uk , 2021, Psychometric Success, Available at: https://www.jobtestprep.co.uk/how-to-prepare-for-psychometric-tests?idev_username=PsychometricSuccess [ 1st September, 2021]
Johnston, M.P., 2017. Secondary data analysis: A method of which the time has come. Qualitative and quantitative methods in libraries, 3(3), pp.619-626. http://www.qqml-journal.net/index.php/qqml/article/view/169
Mohajan, H.K., 2018. Qualitative research methodology in social sciences and related subjects. Journal of Economic Development, Environment and People, 7(1), pp.23-48. https://www.ceeol.com/search/article-detail?id=640546
Ngozwana, N., 2018. Ethical Dilemmas in Qualitative Research Methodology: Researcher’s Reflections. International Journal of Educational Methodology, 4(1), pp.19-28. https://eric.ed.gov/?id=EJ1170655
Pham, H.C., Ulhaq, I., Nguyen, M. and Nkhoma, M., 2021. An Exploratory Study of the Effects of Knowledge Sharing Methods on Cyber Security Practice. Australasian Journal of Information Systems, 25. https://journal.acs.org.au/index.php/ajis/article/view/2177
Prabandari, A.P., Hananto, P.W.H., Lestari, S.N. and Roisah, K., 2020. The legal protection of intellectual property rights toward the maritime scientific researches in Indonesian seas. AACL Bioflux, 13(3), pp.1437-1444. https://www.bioflux.com.ro/docs/2020.1437-1444.pdf
Prayag, G., Hassibi, S. and Nunkoo, R., 2019. A systematic review of consumer satisfaction studies in hospitality journals: conceptual development, research approaches and future prospects. Journal of Hospitality Marketing & Management, 28(1), pp.51-80. https://www.tandfonline.com/doi/abs/10.1080/19368623.2018.1504367
RAHMAN, M. and AYDIN, E., 2019. Organisational challenges and benefits of e-hrm implementations in governmental organisations: Theoretical shift from TOE model. Uluslararası İktisadi ve İdari İncelemeler Dergisi, pp.127-142. https://dergipark.org.tr/en/pub/ulikidince/issue/44082/516443
Remko, V.H., 2020. Research opportunities for a more resilient post-COVID-19 supply chain–closing the gap between research findings and industry practice. International Journal of Operations & Production Management, 40(4), pp.341-355. https://www.emerald.com/insight/content/doi/10.1108/IJOPM-03-2020-0165/full/html
Rubens, A., Schoenfeld, G.A., Schaffer, B.S. and Leah, J.S., 2018. Self-awareness and leadership: Developing an individual strategic professional development plan in an MBA leadership course. The International Journal of Management Education, 16(1), pp.1-13. https://www.sciencedirect.com/science/article/pii/S1472811716301732
Sahin, S. and Mete, J., 2021. A Brief Study on Descriptive Research:: Its Nature and Application in Social Science. International Journal of Research and Analysis in Humanities, 1(1), pp.11-11. https://www.iarj.in/index.php/ijrah/article/view/38
Shaban, S., 2019. Reviewing the Concept of Green HRM (GHRM) and Its Application Practices (Green Staffing) with Suggested Research Agenda: A Review from Literature Background and Testing Construction Perspective. International Business Research, 12(5), pp.86-94. https://pdfs.semanticscholar.org/e64b/53929e3314b557f4d2c10127deb042e4a596.pdf
Snyder, H., 2019. Literature review as a research methodology: An overview and guidelines. Journal of business research, 104, pp.333-339. https://www.sciencedirect.com/science/article/pii/S0148296319304564
Steinbach, A.L., Holcomb, T.R., Holmes Jr, R.M., Devers, C.E. and Cannella Jr, A.A., 2017. Top management team incentive heterogeneity, strategic investment behavior, and performance: A contingency theory of incentive alignment. Strategic Management Journal, 38(8), pp.1701-1720. https://onlinelibrary.wiley.com/doi/abs/10.1002/smj.2628
Valiandes, S. and Neophytou, L., 2018. Teachers’ professional development for differentiated instruction in mixed-ability classrooms: investigating the impact of a development program on teachers’ professional learning and on students’ achievement. Teacher Development, 22(1), pp.123-138. https://www.tandfonline.com/doi/abs/10.1080/13664530.2017.1338196
Wilson, P.H., Sztajn, P., Edgington, C., Webb, J. and Myers, M., 2017. Changes in teachers’ discourse about students in a professional development on learning trajectories. American Educational Research Journal, 54(3), pp.568-604. https://journals.sagepub.com/doi/abs/10.3102/0002831217693801
Zangirolami-Raimundo, J., Echeimberg, J.D.O. and Leone, C., 2018. Research methodology topics: Cross-sectional studies. Journal of Human Growth and Development, 28(3), pp.356-360. http://pepsic.bvsalud.org/scielo.php?pid=S0104-12822018000300017&script=sci_abstract&tlng=en
Žukauskas, P., Vveinhardt, J. and Andriukaitienė, R., 2018. Philosophy and paradigm of scientific research. Management Culture and Corporate Social Responsibility, 121. https://books.google.com/books?hl=en&lr=&id=UMaPDwAAQBAJ&oi=fnd&pg=PA121&dq=Research+Philosophy&ots=pG0GfHOoHG&sig=XonYPMzh0hS9oWfSDKttMobGxVw
Appendix
Appendix -1 Ethics form
Proposal Title
Name of Researcher (s)
| Section 1 | Yes | No | NA |
| Will you describe the primary experimental procedures to respondent in advance, so that they are informed about what to expect? | |||
| Will you tell respondent that their response is voluntary? | |||
| Will you obtain written consent for respondent? | |||
| If the research is observational, will you ask respondent for their consent to being observed? | |||
| Will you tell respondent that they may withdraw from the research at any time and for any reason? | |||
| With questionnaires, will you give participants the option of eliminating questions they do not want to answer? | |||
| Will you tell respondent that their data will be treated with full confidentiality and that, if published, it will not be identifiable as theirs? |
If you have ticked ‘NO’ to any of the questions above, please give an explanation in the box below:
| Section 2 | Yes | No | NA |
| Will subjects/respondent be paid? | |||
| Is there any contact with potentially harmful items or substances? | |||
| Are there any financial or other interests to the researcher(s) or department arising from this study? | |||
| Will project involve deliberately misleading subjects/respondent in any way? | |||
| Is there any realistic risk of any subjects/respondent experiencing either physical or psychological distress or discomfort? | |||
| Is there any realistic risk of researchers experiencing either physical or psychological distress or discomfort? |
If you have ticked ‘NO’ to any of the questions above, please give an explanation in the box below:
Know more about UniqueSubmission’s other writing services:


Наша команда профессиональных исполнителей проштудирована подать вам передовые системы утепления, которые не только предоставят надежную защиту от холодных воздействий, но и подарят вашему жилищу стильный вид.
Мы работаем с современными составами, утверждая долгий термин эксплуатации и отличные итоги. Изоляция облицовки – это не только экономия тепла на обогреве, но и ухаживание о экологической обстановке. Энергоэффективные технические средства, которые мы претворяем в жизнь, способствуют не только жилищу, но и сохранению природных богатств.
Самое ключевое: Утепление стен снаружи цена у нас начинается всего от 1250 рублей за м²! Это доступное решение, которое превратит ваш жилище в настоящий уютный локал с скромными затратами.
Наши работы – это не только изолирование, это составление поля, в где все член показывает ваш личный модель. Мы возьмем во внимание все ваши запросы, чтобы воплотить ваш дом еще больше теплым и привлекательным.
Подробнее на http://ppu-prof.ru
Не откладывайте труды о своем квартире на потом! Обращайтесь к квалифицированным работникам, и мы сделаем ваш обиталище не только тепличным, но и стильнее. Заинтересовались? Подробнее о наших услугах вы можете узнать на веб-ресурсе. Добро пожаловать в обитель удобства и уровня.