Management Assignment Sample
Introduction
The aim of the paper is to take into consideration the BAA’s Terminal 5 Programme at Heathrow Airport which is aiming at catering to about 30 million passengers within a span of a year and also dedicate its concern towards providing the passengers with additional capacity in terms of aircraft parking and terminal parking capacity as well. The concern is thereby towards understanding how in the process of undertaking this risk the organization is going to face and the policy or management that the organization has devised in order to put a check to the risk factors that might emerge in the concerned organization. Risk has been defined as the probability or the consequences that come on the way of reaching out to the goals.
Key Risk areas involving risk management BAA Heathrow Terminal 5
- As per the prime cost is concerned, BAA pays the actual cost in accordance with the CMA and thereby agrees on the overhead cost coming in terms with the suppliers and agrees on the ground that a level of profit on the top of that has been gathered. BAA brings into consideration considerable potential risk factors involved in its operation.
- One of the risk that lies in this respect is the risk of deliver to the T5
- The next risk that is concerned in this case is the risk from the construction of the terminal 5
- The lack of collaboration between the partners in the project and the reluctance of the clients in assuming the responsibility for the risk of the project can contribute to it effectively.
- Uncertainties in the risk in the earlier life cycle of the project information technology related risk which would go into the system
- The system of IT can be considered as the greatest source of risk
- The focus of the risk management had been towards the factor of cost as well as the constraint in terms of time (Hopkin, 2018)
Multi Risk Management Process
There might have been a failure which would have been located in the concern of the BAA in terms of identifying risk in accordance to the T5 agreement which had been concerned with the risk’s cause. Despite the fact the T5 project had been finished within the limitation of time and the budget which had been provided, the focus had been on time constraint and cost, it did not pay much attention towards other aspects and the quality involved. Though the BAA risk management process had been successful in catering to these constraints it failed to take other aspects into consideration.
The multi Risk management process should bring into consideration the monitoring of the performance. The concern of multi risk management should be dedicated towards collecting data as well as putting the risk management process in active mode in order to develop conversion in regard to the opportunities involved (Leo, Sharma & Maddulety, 2019).
Risk Breakdown Structure
The risk breakdown chart or RBS refers to the hierarchical chart that seeks to break down the risks involved in the process through the segmentation of categorization and develop sub levels of risks that might lie within.
| Level 0 | Level 1 | Level 2 | Level 3 |
| Project Risk | Environment | Statutory | ● Climate related risk |
| Industry | Market | ● Competitors | |
| Client | Fundings
Clients |
● cost coming in terms with the suppliers and agrees on the ground that a level of profit on the top of that has been gathered.
|
|
| Project | Team
IT Tasks Time Tactics |
● risk of deliver to the T5
● the risk from the construction of the terminal 5 ● risk in the earlier life cycle of the project information technology related risk which would go into the system ● system of IT can be considered as the greatest source of risk ● Timely completion of the project (Polinkevych et al., 2021) |
Identifying the risk using bow tie diagram
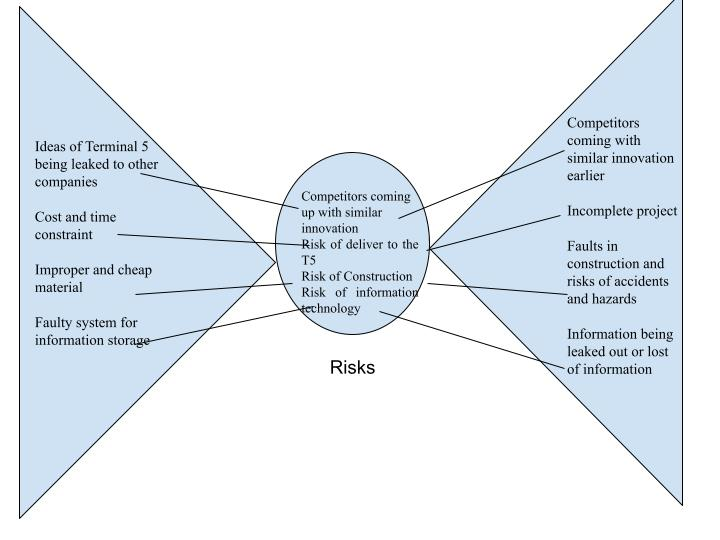
Cause
Competitors coming with similar innovation earlier
Incomplete project
Faults in construction and risks of accidents and hazards
Risks
Information being leaked out or lost of information
Ideas of Terminal 5 being leaked to other companies
Cost and time constraint
Improper and cheap material
Faulty system for information storage
Effect
Competitors coming up with similar innovation
Risk of deliver to the T5
Risk of Construction
Risk of information technology
Cause and Effect diagram using fishbone diagram
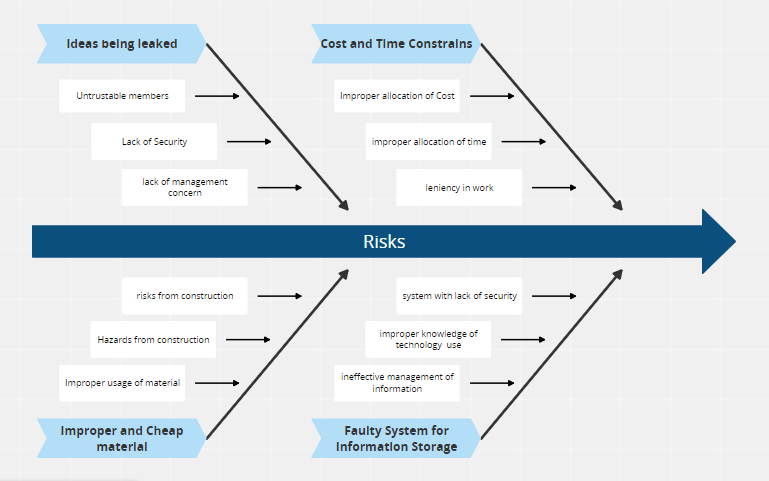
Risk Register
| Sl No | Time | Risk Description | Likelihood of Risk occurring | Impact of the Risk | Severity |
| 1 | Ideas being leaked | High | High | High | |
| 2 | Improper and cheap usage of material | Moderate | High | High | |
| 3 | Faulty system for information storage | Moderate | High | High | |
| 4 | Cost and time constraints | Low | High | High |
Probability Impact Matrix
| Sl No | Time | Risk Description | Remote not recognisable | Has occurred in the industry | Has occurred in the company | Occurred over time |
| 1 | Ideas being leaked | 1 | 2 | 3 | 4 | |
| 2 | Improper and cheap usage of material | 2 | 4 | 6 | 8 | |
| 3 | Faulty system for information storage | 3 | 6 | 9 | 12 | |
| 4 | Cost and time constraints | 4 | 8 | 12 | 16 |
Four Individual Risks
The individual risks which has been considered in this contest are
| Ideas being leaked | Competitors coming up with same ideas | Posing threats to the organization | Bring down the competitive advantages of the organization | Credibility and Authenticity of the organization has been affected |
| Improper and cheap usage of material | Creates risks of damage (Bondarenko et al., 2019) | Create risks of hazards | Creates threats of operation | Might pose risk for larger accidents (Samimi, 2020) |
| Faulty system for information storage | Leakage of information | Lost of information | Hacking | Information theft |
| Cost and time constraints | Improper timing | Improper allocation of time | Wastage of financial resources | Theft of financial resources |
Risk Mitigation Strategies
The risk mitigation strategies for the risk areas identified it can be
| Risks | Strategies |
| Ideas being leaked | Management system should be strengthened in order to prevent the ideas from being stolen or taken away
Employ core management system in order to ensure that the ideas are generated and safeguarded among the groups that are trustworthy (Araz et al., 2020)
|
| Improper and cheap usage of material | The usage of materials should be controlled and checked
The process of construction should be monitored regularly |
| Faulty system for information storage | Technical experts require to be brought under concern in order to check the process
Information system should be monitored on a regular basis in order to ensure that the information is not leaked out The storage of information requires to be taken into account |
| Cost and time constraints | The time should be managed regularly
The cost and expenditure should be monitored in order to prevent fault (Arena et al., 2017) |
Evaluation risk by qualitative and quantitative analysis
The risks as evaluated in this course are fundamental to the operation of the organization and thereby should be monitored and managed on a regular basis in order to ensure that there is no breach or leakage of information that takes place in this regard. It requires to be brought under consideration that all the risks come with equal potentiality of occurring and thereby demands that the risk management system has been implemented into place in order to check.
The BAA framework in relation to T5 requires it to be referred to in order to ensure that the operation and risk management process happens in connection to the guidelines of changes. As per the proposition of the case is concerned it has been noted that the traditional procurement should be revisited and moved towards the position from where it would be effective in controlling and managing the cause of the risk and ensure that the effect of the risk is not looked forward to (Thons 2018).
Conclusion
In order to conclude it can be stated that the management of the risk is a process that is intrinsic to the operation of the organization and requires to be taken under the consideration of the organization in order to ensure that process and operation are executed effectively. Risk management allows the organization to be more concerned with the changes that have been happening in respect to the operation.
The risk management analysis of BAA has taken into account various matrix of risk analysis which included Bow tie model, Fish bone model of cause and effect model, probability matrix of risk in order to understand the connection of one risk factor with the other and thereby devise methods in which it can be catered to effectively.
Recommendations
In this respect several recommendations can be made
- The BAA framework of T5 risk management policy requires to be followed effectively
- The T5 agreement underpinning the strategy should be adhered effectively
- Crucial monitoring and management process requires to be implemented
- Information technology management system requires to be followed as well.
- Revisit the T5 agreement in order to include the changes requires
- Look beyond the attributes of risks associated Cost and time management and bring other areas of concern into account.
References
Arena, M., Arnaboldi, M., & Palermo, T. (2017). The dynamics of (dis) integrated risk management: A comparative field study. Accounting, Organizations and Society, 62, 65-81. https://www.sciencedirect.com/science/article/pii/S0361368217300661
Araz, O. M., Choi, T. M., Olson, D. L., & Salman, F. S. (2020). Data Analytics for Operational Risk Management. Decis. Sci., 51(6), 1316-1319. https://www.researchgate.net/profile/Om-Araz/publication/339938737_Data_Analytics_for_Operational_Risk_Management/links/5e9379fa4585150839d958e3/Data-Analytics-for-Operational-Risk-Management.pdf
Bondarenko, S., Bodenchuk, L., Krynytska, O., & Gaivoronski, I. V. (2019). Modeling instruments in risk management. http://dspace.onu.edu.ua:8080/handle/123456789/27051
Hopkin, P. (2018). Fundamentals of risk management: understanding, evaluating and implementing effective risk management. Kogan Page Publishers. https://books.google.com/books?hl=en&lr=&id=bzFiDwAAQBAJ&oi=fnd&pg=PP1&dq=risk+management&ots=5RxYzP19C3&sig=KfVBlngZbLUFORe4u9EOPQtsfLg
Leo, M., Sharma, S., & Maddulety, K. (2019). Machine learning in banking risk management: A literature review. Risks, 7(1), 29. https://www.mdpi.com/422530
Polinkevych, O., Khovrak, I., Trynchuk, V., Klapkiv, Y., & Volynets, I. (2021). Business risk management in times of crises and pandemics. Montenegrin Journal of Economics, 17(3), 99-110. https://www.research-collection.ethz.ch/handle/20.500.11850/297819
Samimi, A. (2020). Risk Management in Information Technology. Progress in Chemical and Biochemical Research, 3(2), 130-134. http://www.pcbiochemres.com/article_106614.html
Thöns, S. (2018). On the value of monitoring information for structural integrity and risk management. Computer‐Aided Civil and Infrastructure Engineering, 33(1), 79-94. https://onlinelibrary.wiley.com/doi/abs/10.1111/mice.12332
………………………………………………………………………………………………………………………..
Know more about UniqueSubmission’s other writing services:

