Analyzing The Impact of Cybercrime on It and Telecom Industry Assignment Sample
Introduction
Cybercrime has a major impact on the IT and Telecom industry, creating huge financial loss, and data loss. There are different activities included in cybercrime such as ransomware attacks, email fraud, and internet fraud. Cybercrime indicates stealing the personal data of users and trying to get financial information to harm them by using the internet and computer system. It is important to protect computer systems and use safe network connections in IT and telecom organizations to avoid cybercrime activities. The main aim of this study is to investigate the reason for cybercrime and recognize cyber threats and strategic mechanisms to control access in the IT and telecom industry.
Describe the reason and identify the risk in the IT and telecom industry
The major reason for increasing cybercrime in IT systems and telecom organizations is widely used computer systems and unauthorized software (Christou, 2018). A large number of employees are using computer systems and software in the IT industry to share their business information, and personal information. Therefore hackers easily target IT systems to steal users’ data and get huge financial profits. Lack of internet security as well as system security, and system vulnerability are two major reasons for which cybercrime is increasing in the IT and telecom industry rapidly (Fahlevi et al. 2019). Telecom industries are the biggest target for cyber hackers as telecom industries use critical infrastructure to communicate with a large number of users and store a wide range of sensitive information in a small storage system. Some potential cyber threats in the IT and telecom industries are discussed below;
Malware attack: It is software such as ransomware, virus used by cyber hackers to steal users’ information and operate the user’s system. Malware becomes activated when users are clicked on a link that creates cyber threats for the IT and telecom industry. Around 28% of malware attacks will happen in corporate sectors through Botnets in 2020 (statista.com, 2020). It indicates that cyber attackers use Botnets to install the malware in the IT system and steal sensitive information.
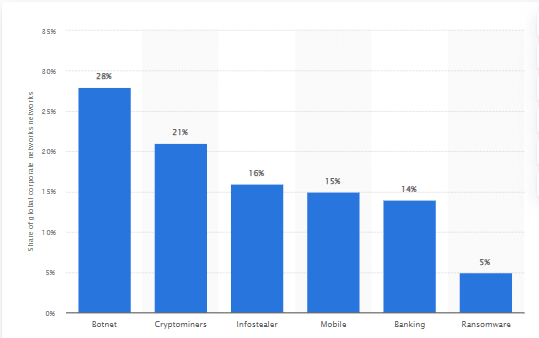
Figure 1: Malware attacks in 2020
(Source: statista.com, 2020)
Denial of service (DoS): Telecom industry is highly faced with DoS attacks and cybercriminals can easily steal information from a large number of users. Approximately 29% telecom industry in Russia faces a DoS attack in 2020 (statista.com, 2021). DoS attacks generally shut down the system and create fake traffic in internet connection so that users are unable to access online information.
Phishing attack: Phishing attacks are carried out through fake communication through email and other platforms (Alazab and Tang, 2019). Users mainly get instructions such as providing passwords and other information through which hackers can steal information in the Telecom industry. Through phishing attacks, cybercriminals can breach the financial information and organizational information of IT industries.
Explain the evidence of cybercrime activity in the IT and telecom industry
There is a huge threat for the telecom and IT industry to lose financial information and user data due to cyber threats. Cyber attackers mainly target the telecom industry to steal a large amount of users’ information from a small storage space (Schia, 2018). Many small IT companies are not using protected systems and network connectivity that create major cyber threats of cybercrimes. Virgin Media is one of the popular network providers in the UK that faces huge cyber threats that shut down the entire network system for users for one month (cybersecurity-insiders.com, 2021). The cyber threats badly hit the reputation of virgin media due to this internet blackout at Christmas time. More than 63% of users launch a report that they are faced with internet issues and on the other hand 39% of users state that they faced mobile network issues (cybersecurity-insiders.com, 2021).
Approximately 19% of business organisations in the UK stated that they are facing huge cyber security threats data breaches once in the last 12 months (statista.com, 2021). During the pandemic situation, the rate of cyber attacks is increasing gradually in the UK, creating a huge financial loss for IT as well as the telecom industry.
Strategies to achieve authentication and access control
The use of a protected system and network connection can reduce cyber attacks threats in the IT and telecom organizations. Standard password mechanisms and safe authentication can be used to improve the access control of computer systems in the IT and telecom industries. Some strategies to prevent cyber attacks in IT systems are discussed below;
2-factor authentication: It is required to protect systems in the IT and telecom industry by using two-factor authentication. It is required to set a standard password and provides physical objects to get access to a specific system as well as a network (Lallie et al. 2021). Therefore this authentication helps the telecom and IT industry to protect systems from cyber hackers.
Provide endpoint protection: It is important to protect network connections used by users however unauthorised network connections may create a path for cyber hackers to steal users’ information (Chang et al. 2018). Management of IT and telecom organisations can use protection software to detect threats on the internet by endpoint protection.
Monitor traffic on the internet: Management of IT firms can increase network monitoring processes that can help them to detect unauthorised users (Aldawood and Skinner, 2018). It boosts the access control mechanism within organisations to protect computer systems and manage organisational information systematically.
Conclusion and recommendations
From the study, it has been concluded that the IT and telecom industries are one of the main targets of cyber attackers to steal sensitive information and create a huge financial loss. There are different cyber threats such as malware, ransomware, phishing, and DoS used by cyber hackers to negatively impact IT systems. Password protection, 2-factor authentication, and monitoring network systems can reduce cyber threats in the telecom industry.
Recommendations
It has been recommended that organisations can update their system and software to detect potential cyber threats. Using updated software, the system creates difficulties for hackers to penetrate sensitive information (Schia, 2018). It is also required to give training for IT staff so that they can understand how to protect data, systems with passwords and other authentication mechanisms. Employee training helps to improve the security process of telecom firms and maintain organisational reputations. It also has been recommended that management can use AI, Machine learning, and Blockchain technology to protect systems from cyber attacks and detect unauthorised users (Kim and Park, 2020). It helps to detect cyber threats, viruses, and unauthorised users automatically from a network connection.
References
Alazab, M. and Tang, M. eds., 2019. Deep learning applications for cyber security. Springer.
Aldawood, H. and Skinner, G., 2018, December. Educating and raising awareness on cyber security social engineering: A literature review. In 2018 IEEE International Conference on Teaching, Assessment, and Learning for Engineering (TALE) (pp. 62-68). IEEE.
Chang, L.Y., Zhong, L.Y. and Grabosky, P.N., 2018. Citizen co‐production of cyber security: Self‐help, vigilantes, and cybercrime. Regulation & Governance, 12(1), pp.101-114.
Christou, G., 2018. The challenges of cybercrime governance in the European Union. European Politics and Society, 19(3), pp.355-375.
cybersecurity-insiders.com, 2021, cyber attacks to blackout virgin media internet, Available at: https://www.cybersecurity-insiders.com/cyber-attack-to-blackout-virgin-media-internet-users-for-one-month/#:~:text=Cyber%20Attack%20to%20blackout%20Virgin%20Media%20Internet%20users%20for%20one%20month,-By&text=UK’s%20most%20popular%20internet%20service,next%20month%20for%20most%20users. [Accessed on: 11th April, 2022]
Fahlevi, M., Saparudin, M., Maemunah, S., Irma, D. and Ekhsan, M., 2019. Cybercrime Business Digital in Indonesia. In E3S Web of Conferences (Vol. 125, p. 21001). EDP Sciences.
Kim, J. and Park, N., 2020. Blockchain-based data-preserving ai learning environment model for ai cybersecurity systems in iot service environments. Applied Sciences, 10(14), p.4718.
Lallie, H.S., Shepherd, L.A., Nurse, J.R., Erola, A., Epiphaniou, G., Maple, C. and Bellekens, X., 2021. Cyber security in the age of COVID-19: A timeline and analysis of cyber-crime and cyber-attacks during the pandemic. Computers & Security, 105, p.102248.
Schia, N.N., 2018. The cyber frontier and digital pitfalls in the Global South. Third World Quarterly, 39(5), pp.821-837.
statista.com, 2020, malware attacks in corporate network, Available at: https://www.statista.com/statistics/1238997/malware-attacks-corporate-networks/ [Accessed on: 11th April, 2022]
statista.com, 2021, cyber security breaches experience in business uk, Available at: https://www.statista.com/statistics/586725/frequency-of-cyber-security-breaches-experience-by-businesses-in-the-uk/[Accessed on: 11th April, 2022]
statista.com, 2021, ddos attack in Russia, Available at: https://www.statista.com/statistics/1189519/ddos-attacks-distribution-in-russia-by-industry/[Accessed on: 11th April, 2022]
………………………………………………………………………………………………………………………..
Know more about UniqueSubmission’s other writing services:

