ASSIGNMENT-CRYPTOGRAPHY
Cross-Site Scripting (XXS) attack on Microsoft outlooks of android
2. System attacks by Cross-Site Scripting
The Cross-Site Scripting aims to attacks the malicious scripts of the web browser, the possible attacks can be seen in Cascading Style Sheets, Active X, Flash, Drupal, Joomla Humhub and VBScript. According to the views of Gupta & Gupta (2016), the Cross-Site Scripting attacks are most common to the JavaScript because it is the most fundamental.
The following tables have been used to represent the ranks of the attacks by the threat Cross-Site Scripting. The ranks are analysis on the basis on time analysis on the different operating system (web app).
| Web application | Attack ranks of the threat (XSS) |
| Drupal | 3rd |
| Joomla | 2nd |
| Humhub | 1st |
| Active X | 4th |
Table 1: Ranked List of XSS attack
(Source: Rodríguez et al (2019)
3. How Cross-Site Scripting perform attacks
Cross-Site Scripting attacks the web browser by adding malicious code in the legitimate web application or web page. The XSS attacks the users of android Microsoft Outlook when they try to enter in the web pages through HTML. It mostly attacks when the internet users try to send malicious code in the form of the browser script. From the views of Rodríguez et al (2019) after the attacks, the Cross-Site Scripting generates the output without validating or encoding the web page.
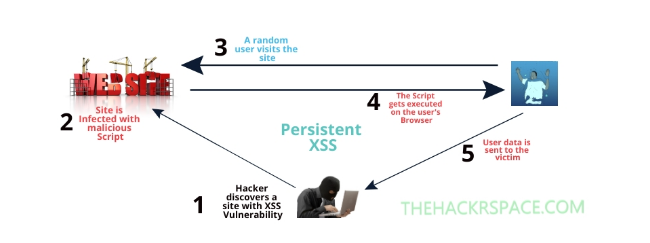
Figure 1: Process of XSS attacks
(Sources: Rodríguez et al (2019)
The below table shows the performances of the Cross-Site Scripting attack based on time calculations. The analysis is done on the basis of time in milliseconds in computer and mobile phone cloud platforms.
|
Web Application |
Response time (in ms)
Without mobile cloud platform |
Response time (in ms)
With mobile- based cloud platform (MS outlook) |
| Drupal | 2096 | 2018 |
| Joomla | 2312 | 2216 |
| Elgg | 2789 | 2676 |
| Humhub | 3126 | 2986 |
Table 2: Performance analysis of XXS using Time calculation
(Source: Rodríguez et al (2019)
4. Mitigation Strategies of Cross-Site Scripting attack
● Validating Input: Validating input is a strategies method of ensuring applications of web pages by rendering the correct data in order to avoid the interference of the malicious data in the system. The validating input in the Microsoft outlook is generally associated with the SQL injection.
- Escaping: The escaping of the user inputs is one of the easiest ways of mitigating the attack of Cross-Site Scripting. The time when the internet user removes or closes the inputs it prevents the ways of attacking to HTML, URL or Javascript by the threat Cross-Site Scripting (XSS).
- Sanitizing: The sanitizing of the system data which are used in browsing the internet or applications in the Microsoft outlook can mitigate the attack of the Cross-site scripting (XSS). Sanitizing strategy is perfect for prevention of Cross-Site Scripting attacks in the HTML of the Microsoft Outlooks.
The following are the policy introduced in order to mitigate the cyber attacks
- Cyber Security Enhancement Act (CSEA) 2002 of the United States
- National Cyber Security Policy 2013 (United States)
There are a number of organizations and institutions who give the training to mitigate the cybercrime and XXS attacks;
- Cyber Security Training for Business
- International Training Course
5. Scope of Cross-Site Scripting attack
The cybercriminals can exploit the vulnerability scope of the Cross-Site Scripting attack; through the XXS attacks, the cybercriminals can steal the data and information from various users of different regions. According to Gupta & Gupta (2017) the Cross-site scripting attacks by cybercriminals through the process of injecting malicious in the web page and applications of Microsoft outlook and steal the data of HTML, URL and JavaScript.
The following table shows an example of the code used by the cybercriminals during performing Cross-Site Scripting.
| Attack type | Code snippet of guestbook | Example attack |
| Stored | Comment: <? echo $msg;?> | <script>alert(‘xss’);</script> |
| Reflected | <? Echo $_GET(‘fname’);?> Not found. | www.guesstbook.com? Fname=<script>alert(‘xss’);</script> |
| DOM-based | var name = document.URL.indexOF (“name=”)+5; document.write (“Hello” + name); | www.guestbook.com# name=<script>alert(‘xss’);</script> |
Table 3: Table of XXS attack and example code
(Source: Gupta & Gupta (2017)
From the analysis of the Mitigations strategy of the Cross-site scripting, here I can conclude that the mitigations are necessary to protect the Microsoft Outlook from XXS attacks. The technical mitigations strategy includes three methods, Escaping, Validating Input and Sanitizing of the web page. I think the technical strategies can mitigate the cyberattack for a limited period of time and into a limited extends. In order to mitigate the cyber attack by Cross-site scripting policies and training strategy is needed. The training strategy can help in producing a trained professional to find the cybercriminal and prevent cybercrime. The policies mitigations of cybercrimes provide guidelines and laws to decrease the ratio of cybercrime.
Gupta, S., & Gupta, B. B. (2016). XSS-SAFE: a server-side approach to detect and mitigate cross-site scripting (XSS) attacks in JavaScript code. Arabian Journal for Science and Engineering, 41(3), 897-920. Retrieved from: https://link.springer.com/article/10.1007/s13369-015-1891-7 [Retrieved on: 1st December, 2019]
Gupta, S., & Gupta, B. B. (2017). Cross-Site Scripting (XSS) attacks and defense mechanisms: classification and state-of-the-art. International Journal of System Assurance Engineering and Management, 8(1), 512-530. Retrieved from: https://link.springer.com/article/10.1007/s13198-015-0376-0 [Retrieved on: 30th November 2019]
Rodríguez, G. E., Torres, J. G., Flores, P., & Benavides, D. E. (2019). Cross-Site Scripting (XSS) Attacks And Mitigation: A Survey. Computer Networks, 106960. Retrieved from: https://www.sciencedirect.com/science/article/pii/S1389128619311247 [Retrieved on: 2nd December, 2019]