CETM30 Fundamentals of Cybersecurity Sample
Part 2
Proposed diagram with modified building planning
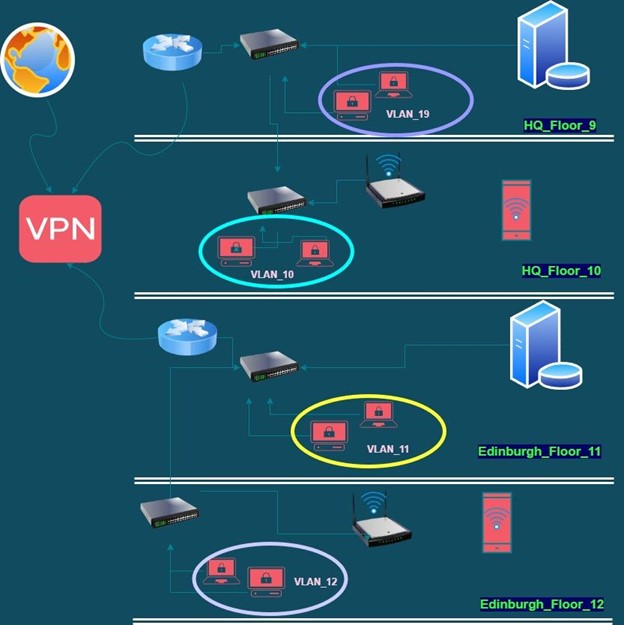
Figure: Complete network architecture as per building plan
(Source: Generated by the learner)
The proposed network architecture has been proposed in terms of visualizing a layout diagram of the proposer scenario. As per the requirements, it has been viewed that the prime intention is to secure both the network intended to implement on both building on 9th, 10th and 11th and 12th respectively.
Question 1
A link is established between two sites which have the FTTP connectivity maintaining all the protocol to secure the data from theft. As per the view of Sarker et al. (2020), a VPN is created to ensure that all the sensitive data is safe. This VPN is connected with the network in different floor and providing encrypted conncetion over the internet, so the traffic remains secure while travelling.
So the network cab be connected securely with corporate network from anywhere.VPN changes the normal texting into code,which is unreadable and a decryptor helps to unscrambles that text so that it can return into the readable information. It is providing maximum security cause the decryption key can be accessed only by VPN provider and the device.
This is for sharing the confidential information through a more secure network. VPN ensures that the information or any data cannot vbe transferred without theb authentication of the user. Floor 9 of Edinburg containing a router connected with a switch , maintaining the conncetion between the devices and internet. It is acting as dispatcher, to choose the best secure path of travelling for the information and protecting it from any security threat.
Router connects devices with internet and with other devices, which allows secure sharing of information and software tools.This rotwCC In LAN , a network hub acts as the central point of connection for the devices and it also limits the number of connection for a network that is hub- based .Here for avoiding all these limitation a switch is used. Every floor used different switches for connecting the devices together. These switches are connected with routers for the smooth access of internet.
This network plan is applied for all the floors for a secure travelling of data. Two database are provided for the collection of information in the devices for keeping all the tracks of information ,business processes and other confidential data. VCHere two databases are provided , in the 9th and 11 th floor, and the other network structure are same for all the floor.
Here a logical grouping for all the devices have done in the same domain. VLAN helps in increasing the broadcast domain by decreasing the size. This reduces the security risk , as it it reducing the host number and also keeps the hosts consisting of sensitive data into a VLAN which is separate for improving the security. Uses of VLAN also increase the flexibility of network. All this technologies are used to maintain a secure network when the data flowing through the sites.
Question 2
There can be several weaknesses of the following physical security. The respected private systems can necessitate the specialized hardware as well as the multiple boxes of the control. This also can be location specific. The overall arrangement of the following control boxes can indicate the every design for that respected area precisely.
This can need a lot for the procedure of the installation as well as this can be self contained. The vulnerability of the following network is a sort of weakness or the flaw in the respected processes of the following organization. The following networking may increase the higher potential for the issues of the security like the data loss, respected security breaches, and several malicious attacks.
There are several preventive measures for assisting the following network security involves-
several security devices like the firewalls as well as the software of the anti-malware. The setting of the security in the following operating system, encryption of the following data system for the sensitive data.
The following networking can raise a higher potential for the issues of the following security like data loss, security breaches as well as the malicious attacks. The respective measures can be implemented for reducing the vulnerability of the following network to unauthorized access or the following damage.
For securing the following network some of the procedures can be taken-
Restrict the access to the following wireless network, the firmware of the following router of this particular router have to be modified, the remote access is to be disabled, and the following firewall of the router has to be turned on. The respected data has to be encrypted for both transits as well as reset. For decreasing the risk of the following organization by encrypting the data that is sensitive.
This can make it more difficult for the respected attackers to access the data for managing the breach of the following network.The information on the security, as well as the solution of the event management, has to be considered. This can provide the several capabilities to any response team to the following incident,
The alerts can be based on the analytics that can match a certain set of rules which can indicate the issue of the security. A huge amount of data can be collected from the following finished environment of the network, which can make humans for getting the access. The departments of the following organization can be unable to draw the required data that can allow for detecting the several cyber threads properly.
The respective security audits have to be conducted on a regular basis. Security audits are a crucial part of decreasing the security risk of the network of the following organization. The assessment of the cyber risk can be needed when evaluating the requirements of the following program of the security. The latest threats of the security has to be updated as well as trends. The further way of decreasing the network security of the following organization has to be aware of the current trends as well as the cyber threads.
The security risk of the following organization can be decreased. There can be always a sort of risk of being targetted by any cyber attack. For protecting the following security of the network of the respected organization is to be prepared as well as have a plan in the place of how to tackle with the following attacker if anyone does happen. The patching of the following system as well as retaining the latest updates of the security. The management of the vulnerability is crucial piece of retaining the systems modified.
Question 3
The structure that can be seen in the figure is temporary and reversible. In the case of making the network more secure there are some temporary fittings can be makde with the time. By using inter VLAN protocol in the switches the broadcasting of the all package can be stopped. Itv can be able to make the network more secure.
Only those users can be able to access the database who are in the same VLAN. For securing the ninth floor of the hgead quarter two firewalls can be installed in the night floor of the head quater. One firewall can be implemented outside of the network and one firewall can be implemented in the inside of the office. By implementing those two firewall the overall security of the building can be drastically improved.
There are two routers can be seen in the above figure. For securing the line between those two routers a VPN can be set up. Without the VPN it can be challenging to secure the connection between Eisenburgh floor and headquarters. The separation of those two network can be done for securing the overall network. A layer 3 switch can also be used to secure the network between two building.
While using layer three switch two VLAN can be created accordingly. The layer 3 switch can also be able to perform switching and routing at the same time. That is why it can be very helpful in the case of securing the overall network. There are some wifi that can also be seen in the network. By using complex passwords to the wifi and limiting the overall access the network security can be improved tremendously.
Question 4
A sort of routing protocol can be utilized for discovering the routes between the following nodes to aid the communication within the respective network. The initial goal of this routing protocol for like this network is more accurate as well as more establish of an effective route between the node pairs so that the following messages can be delivered in a timely way.
As per the view of Lezzi et al. (2020), the construction of the route has to be performed with a minimum overload as well as the consumption of the bandwidth. The following protocol of routing is a sort of convention or the standard that can operate how the following nodes have to agree with which of the packets of the route between the respective packets of the route between the computing the respected devices in the following network. In the respected network, the following does not have the idea of the topology of the following network around those, that have to locate.
The basic plan is a new sort of node that can announce as well as can respond to the announcements of the broadcast from its following neighbours of it. As per the view of Corallo et al. (2020), the following node can learn about the new neighbour nodes as well as attain those. The following protocols of routing can be categorized into a) “ Table-driven OR Proactive routing protocols as well as b) “On demand OR Reactive routing Protocols”.
There can be severa1 issues that can be faced in the following routing protocols. The issues in the following “routing Mobility Bandwidth constraint error” that can share broadcast channel of the radio that can be hidden as well as exposed the problems of the following terminal with the resource constraints. The following path that can be “mobility highly dynamic frequent” can break the frequent changes of the following topology.
As per the view of Li et al. (2019), there are several security challenges that can be appeared as the dynamic topology, links that can be wireless and also vulnerable as well as the nomadic environment. The architecture of the security can lead to the problem of the privacy simultaneously. There can be several problems with the following routing protocol they are slow convergence, counting to the infinity, the routing loops as well as the small infinity.
As per the view of Mahdavifar, and Ghorbani (2019), the following OSPF protocol can be defined as the “Open Shortest Path first” is a link-state protocol of the routing that can be developed for the following IP networks as well as can be dependent on the algorithm of the “Shortest Path First” that also can be expressed as the SPF.
This can be classified as the “Interior Gateway Protocol” which also can be expressed as the IGP. this suggests that this can distribute the information of the routing between the following routers that can be belonging to any single “Autonomous System”, a group of the routers that also utilize any usual protocol of the routing.
As per the view of Shaukat et al. (2020), these can be utilized for the routing of the network internally. This can be between the routers as well as the switches in a similar location. There are certain advantages of the following OSPF, some of them are compared with the following routing protocols of the distance vector like the “Routing Information Protocol” or the RIP, this OSPF can be able to serve in a wide way as well as the heterogeneous internetworks. This following OSPF can be able to recalculate the following routes in less amount of time when the
following topology of the network changes. This respected OSPF can provide multipath routing at an equal cost. The following autonomous system can be divided into areas as well as retain the topologies of the area for decreasing the routing traffic off the OSPF as well as the respective size of the “link-state database” for each of the areas.
There can be two different forms of the VPN, they can be “site-to-site VPN” as well as the “remote access VPN”. The following “site-to-site VPN” can be designed for linking multiple distributed sites securely. The respected “Remote Access VPN” is a sort of access of the VPN that can be designed for linking the following remote users safely to any corporate network.
Reference
Sarker, I.H., Kayes, A.S.M., Badsha, S., Alqahtani, H., Watters, P. and Ng, A., 2020. Cybersecurity data science: an overview from machine learning perspective. Journal of Big data, 7(1), pp.1-29.
Lezzi, M., Lazoi, M. and Corallo, A., 2018. Cybersecurity for Industry 4.0 in the current literature: A reference framework. Computers in Industry, 103, pp.97-110.
Corallo, A., Lazoi, M. and Lezzi, M., 2020. Cybersecurity in the context of industry 4.0: A structured classification of critical assets and business impacts. Computers in industry, 114, p.103165.
Li, L., He, W., Xu, L., Ash, I., Anwar, M. and Yuan, X., 2019. Investigating the impact of cybersecurity policy awareness on employees’ cybersecurity behavior. International Journal of Information Management, 45, pp.13-24.
Mahdavifar, S. and Ghorbani, A.A., 2019. Application of deep learning to cybersecurity: A survey. Neurocomputing, 347, pp.149-176.
Shaukat, K., Luo, S., Varadharajan, V., Hameed, I.A., Chen, S., Liu, D. and Li, J., 2020. Performance comparison and current challenges of using machine learning techniques in cybersecurity. Energies, 13(10), p.2509.
Know more about UniqueSubmission’s other writing services:

