CN7026 INDIVIDUAL CW REPORT CLOUD COMPUTING PET SECURITY AND SERVICES
ABSTRACT
Pet security and services are very much needed for emergency situations. When the pet caretaker went out of the station, pet security can be provided by various pet security services. Emergency care is also provided by these pet security services. Here, a system for pet security service has been proposed and some part of the system is implemented.
This system acts as the bridge between the pet care taker and the pet security services to communicate during the emergencies. The care taker can get recommendations and advices to take care the pets using this system. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Cloud computing refers to the information managed where personal data processing is apprehensive the users can access the cloud service without any knowledge of technology. It reduces the cost with an on-demand mechanism providing pay–on the business model. Privacy refers to the cloud as self-autonomy as it consists of responsiveness on how to store information and communicate the information with a control flow and avoid its abuse. The information has to be protected with self-autonomy which derives from the right of privacy. The individual user can control the data whether it may a private data or public.
The end-user devours the cloud service without knowledge of physical location how the data is the processing of personal user data and is arranged. The important issue considered increasingly is privacy where the data administration and individual information of a person in a cloud consider the main challenge between both authorized and business-related. The confront to alleviate risk in the cloud has a role included by PET clinic to stay healthier with care plan can deploy using privacy-enhancing technologies to secure a data in a cloud environment.
The on-demand network access with a collective pool of the whole resources is to enable the process with minimal effort on service in the cloud computing paradigm. The five characteristics that enable the process of clouds such as network access everywhere, self-service with the on-demand process, resource pooling with location-independent, fast elasticity and deliberate service.
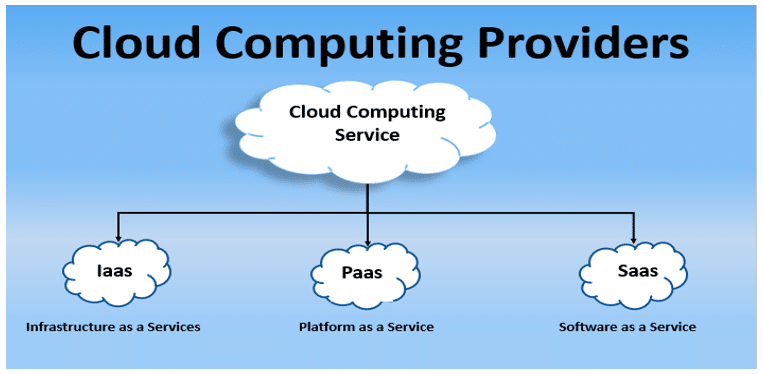
The fast elasticity consists of extent up resources where deliberate service provides the business model with the use of resources with computing allowance, load consideration and metering tools. The cloud services provide the three delivery models such as software/application/platform as a service. It has three responsibilities with individual data protection.
Software as a service in a cloud is used to represent various applications to access from various consumer devices through a web browser. The client has no authority over data processed
But have the confidence in providing the cloud source how to give information in service of software.
The platform service provides to deploy applications with user-friendly tools is a big responsibility of developers where the attacker might access the text because he can direct the implementation environment.
CHOICE OF CLOUD SERVICE PROVIDER
Infrastructure service providers run software with compute resources and it takes responsibility for providing to secure data, set up connections in a system and perform the applicable law and regulation. It is a model for providing execution and guarantees with technical security of flexibility process. The client in an infrastructure surrounding provides to communicate the privacy safety measures needs.
CLOUD CONCEPTUAL MODEL PARADIGM
ESSENTIAL PRIVACY PRINCIPLES IN CLOUD FOR PET
The essential principle of individual data includes correctness and equality, proportionality, purpose arrangement, data eminence, directness and responsibility. This is common in different countries with legal relevance surroundings. The privacy Enhancing technologies consist of;
- Minimize the risk of a breach in principles and legislation.
- Individual data amounts can be minimized.
- Control of information can be preserved to allow a person to themselves at all times.
The implementation of privacy-enhancing technologies can be represented through the proactive-measures requirements which can be used to preserve the data with confidentiality and rights to protect data from unnecessary processing. The Privacy-enhancing technologies and tools consist of providing to secure the data in a globalized world.
CLOUDINESS TOOLS/TECHNIQUES IN PET CLINIC
Privacy-enhancing technologies consist of providing the tools and technologies for PET clinic using opacity which attempt for performing to minimize the data such as encryption technique, data management to secure data, information sanitization which helps to enhance technologies to provide policies with online access of personal data in a secured way.
Legality and equality principle: The data must be processed with the appropriate nationwide legislation with the freedom of principles with human rights to secure personal data with public and supporting rights.
Quality principle: The individual data of a person should process according to its sufficient and not unnecessary relation for which it was projected.
Function requirement Principle: The data to be fulfilled according to the purposes for which it was collected.
Information eminence principle: The individual data should be kept accurate with the correct date and it should not be taken the period which it was planned.
Directness principle: The controller of maintaining data should have obvious policies for processing the individual data.
Liability principle: The organizer of maintaining data should consist of an internal mechanism that leads to making obvious observations of data subjects with a narrow establishment.
IMPEDIMENTS OF PRIVACY IN CLOUD COMPUTING
The personal data can be represented to achieve the quality to expand the quantity with work out delivers for a client to the emergence of new business with models for the contributor. The most important confidentiality challenge in cloud computing are
- Risk estimation of complexity in a cloud environment
- New business model and inference of customer confidentiality
- Authoritarian conformity to achieve
PRIVACY-ENHANCING TECHNOLOGIES TO SECURE PET CLINIC IN CLOUD
The confidentiality to secure data with a PET clinic enables to provide and execute the providers securely even if the customer does not have confidence in the contributor. It is helpful to move with cloud technology for pet’s health care. The cloud environment helps to secure the pet data with a set of tools and method which is used to keep their privacy data by get rid of and diminish personal data without any loss of functionality of information system.
It allows performing working out with cryptographic concepts to protect data. The encryption of homomorphism is used to secure the data with preserve protocols. The asymmetric technique is used to perform the algebraic procedure straight on cypher text which represents the original plain text.
Pet clinic benefit in cloud
A pet clinic care is used to detect disease in the early stage of disease and normal check-up help start action in the right way. The treatment can be given according to the disease and help to reap subsequent benefits.
Health care in the cloud
Preventive health care for pets can be a help to stay longer with the help of pet doctors in a cloud environment
SIGNIFICANCE ROLE FOR PET CLINIC TO MOVING CLOUD
The significant role of moving cloud for pet clinic has many benefits such as
- Hardware expenditure is less
- Reliability
- position self-determining device
- Back up data in the cloud
- The overall cost can be minimized
Hardware Expenditure is less
In a cloud-based, the server space does not waste and hence it is very reasonable and adaptable. It does not require any installation charges.
Reliability
In a cloud, it doesn’t matter what the size of a pet clinic is. The main advantage to moving a pet clinic in a cloud can be achieved using the particular service and no issues of upgrade and downgrade of subscription in prospect.
Backup data in a cloud
The data can be backup using a cloud-based software service and no need to worry about data loss about pet clinics in a cloud environment. The data will be secure and safe with the requesting provider.
The overall cost can be reduced
The overall cost can be reduced in a cloud environment of choosing the application for the PET clinic.
REIMBURSEMENT OF CLOUD PET CLINIC SOFTWARE
The software application without moving to the cloud need an upgrade. In a cloud-based environment the updating of the application by the trader at the server-side. The cloud application in a PET clinic has many advantages such as
- Free promotion
- Move towards easily in the cloud
- Augment teamwork and file sharing apps
- Security in cloud servers
The AWS structural design is used to handle high traffic for storing a huge quantity of information which is used in a variety of virtual machines with different requirements of an assortment of mapping individual servers. The AWS planning consist of an expandable computes cloud which is used to represent formation as well as entity mapping which is used to simply regain and accumulate data with various application programming frame calls. The AWS structural design has five supports and it consists of:
- implementation dissimilarity
- safety and protection measures
- reliability
- proficiency of arrangement
- Overheads optimization for customers.
It provides a reliable approach and development in the way of procedure to a client and correlates to work out the implement plan with structural design in AWS.
STRUCTURAL DESIGN OF AWS
- LOAD EVALUATION IN AWS
It corresponds to the h/w and s/w which is used to progress the competence of an application of a server.
- ELASTIC LOAD EVALUATION IN AWS
It is used to adjust the traffic difficulty and deal with the direction-finding needs.
- SECURITY METHOD IN AWS
The inbound set of connections is used to specify to transmit with appropriate passage instance.
- STORAGE SPACE AND ENDORSEMENT IN AWS
It stores the substance with a resource called buckets which are used to read, mark and remove the objects from the bucket.
SOLUTION REFLECTION OF AWS
The significant network such as route and firewall is not necessary because it gives protected depiction with a host in structural design which allows to admittance among host in the fewest amount way as per prerequisite. The model in AWS provides to deploy the application which is used across data centres for both high convenience and consistency. The PET clinic of moving data in a cloud using AWS has more security with diverse protection services available based on a customer in a cloud.
AWS CLOUD PRICING CALCULATION
IMPLEMENTATION OF PET RESULTS IN AWS
The AWS instance is used to set up and configure the application in a virtual environment that runs on an instance. The instance is used to indicate the private key when connect to it through Amazon EC2.
The volume storage consists of frequent updates with an occurrence or storage for a database application. A mass storage device can be attached with an instance or multiple instances at a time. It is durable and is connected with an instance like any other physical hard drive and uses o dynamically change and resize the provisioned capability with production volume storage.
The Privacy-enhancing technology using AWS provides to protect data and workloads from unauthorized users. It provides the encryption scheme to detect and check continuously with the factors including the private data with laws and regulations in the pet clinic cloud environment.
RESULTS
The PET clinic moving to the cloud has many benefits which have to watch the health care effectively day by day and this host by cloud environment can access by any device.
CONCLUSION
The PET clinic in a cloud environment can be accessed through the internet and it provides many advantages with the representation of installation fee, server space can be utilized. A PET clinic is used to develop with a cloud environment to make the functionalities of the core with user-responsive nature the function were included with cloud architecture of using AWS. It helps pet’s clinictomove on a cloud without software installation in order to stand alone with cloud-based VET support effectively.
REFERENCES
1.G W Van Blarkom, J J Borking, and JGE Olk,2015.Handbook of privacy and privacy-enhancing technologies. Privacy Incorporated Software Agent(PISA) Consortium, The Hague.
- Keith Frikken and Mikhail Atallah,2017. Privacy-PreservingCryptographic Protocols. In Digital Privacy, pages 47–69. Auerbach Publications.
- Shafi Goldwasser and Silvio Micali.,2015. Probabilistic encryption and how to play mental poker keeping secret all partial information. In Proceedings of the fourteenth annual ACM symposium on Theory of Computing, pages 365-377, New York, NY, USA, 1982. ACM.
- Craig Gentry.,2014. A full homomorphism encryption scheme.PhD thesis, Stanford University.
- Qin Liu, Guojun Wang, and Jie Wu.,2016. An EfficientPrivacy Preserving Keyword Search Scheme in CloudComputing. Computational Science and Engineering,2016. CSE ’09. International Conference on, 2:715-720.
- Karthick Ramachandran, Hanan Lutfiyya, and MarkPerry,2015. Chaavi: A Privacy-Preserving architecture for webmail Systems. In Cloud Computing 2011, TheSecond International Conference on Cloud Computing, GRIDs, and Virtualization, page 133 to 140
- Daniele Micciancio.,2015. The first glimpse of cryptography’sHoly Grail. Communications of the ACM, 53(3):96–96.
- Morrie Gasser, Andy Goldstein, Charlie Kaufman, andButler Lampson.,2016. The Digital distributed system security architecture. In Proceedings of the 1989 NationalComputer Security Conference, pages 305-319.
- S Bajikar.,2016. Trusted platform module (tpm) based security on notebook pcs-white paper. White Paper, Mobile Platforms Group-Intel Corporation.
-
B Bertholon, S Varrette, and P Bouvry.,2014. Certicloud: A novel TPM-based approach to ensure cloud iaas security cloud Computing (CLOUD).


