COM00094M MSc in Cyber Security Degree Examination Assignment Sample
IDENTITY, TRUST, REPUTATION, AND THEIR APPLICATIONS
Abstract
This report contains four questions in which first question shows how the system of “Identification, Authentication & Authorization” system can be developed for the advantage of police service. The second question explains how customer feedback can be beneficial for the betterment of the organization. The third question explains about BAN logic and the fourth question shown spoofing and its effect on UAVs.
Keyword:
BAN logic, UAV, Cyber security, IAA System, Spoofing
Question 1
“South Hallamshire Police Service” has brought modifications in their digital services. They tend to develop the kiosks to the different locations of the country for maintaining authenticity. Kiosks are present within the premises of the police station to ensure that no authorized people can enter the premises.
The authorized officers are only able to access the system only for a particular period of time. The officers who would be requiring the authorization to access the essential information in Kiosks would be required to take the permission from the supervisor.
- The first criteria are cost effectiveness. The system is required to be built in a way that requires minimal investment. The system is required to be cost effective so that it can be used by all people. The IAA system is required to be one of the most essential systems which are beneficial for maintaining security within the premises of the police service station. Secondly the system is required to be designed in a way that it can only be authorized by the people who have the access to the system.
All the officers should be provided with QR code which can be scanned to get the access to the system. This would be helping in maintaining the security of the system and would also ensure that only the authorized people would be able to access the system [1]. The system is required to be user friendly so that it can be used by all the users. It is very necessary to ensure that all the users are capable of using the system.
A proper threat model is also required to be prepared to ensure that all the sensitive information stored in kiosks are stored securely. The kiosks are also used by the police officers to get connected with the mobile phones of the suspects. This would be enabling the officers to identify the presence of any suspecting items within the mobile of the suspects.
Hence the officers are required to be provided with proper training to ensure that they can help in maintaining the kiosks. If they are not trained properly they would be unable to efficiently operate the kiosk thus resulting in poor “Identification, Authentication & Authorization (IAA)” practice.
- Identification happens when a user claims or proclaims a personality. This can also be performed with a login, a procedure ID, a digital certificate, etc that can identify a particular topic. This identifier is used by system security to determine whether or not a subject has access to an item.
Authentication or Validation is the process of verifying an identity, and it occurs when individuals offer adequate qualifications to establish their personality. For contrast, when a user enters the user credentials with an identity, the username demonstrates that perhaps the user is really the author of both the screen name. In a nutshell, identification gives confirmation of a biometric template.
Once a user has been recognized and validated, they can indeed be allowed authorization predicated on their proved identities. It is critical to emphasize that distinct authorization cannot exist without identity and validation. In other words, if everybody just signs together with the same username, you may allow or deny someone access to information.
Users can’t distinguish amongst users when everybody employs the same username. Users who have now been validated with distinct usernames and passwords, on the other hand, might be provided access to external accounts according to their identification [2].The Identifying, Security, and Activation platform supports the safe enterprise applications at UW-System universities by objective of this section governance and access control activities.
Access to data in the IAA registration for user and customer support, a secure authentication service, a centralized certification service, and UW platform password protection are all part of the IAA identity management managed services for authorized applications. A server provides verification when people want to know who’s really browsing their material or site.
That whenever a customer wants to know that perhaps the service is the system it purports to be, it uses authenticate. The customer or machine must confirm its authenticity to the local server during certification. Typically, server verification requires the usage of a pass code. Tickets, retinal scanners, voice search, and signatures are among more methods of authentication.
Verification by a browser often entails the service providing the client with a credential in which an intermediary, such as Certificate authority or Thawed, certifies that the service represents to the business that the viewer believes it to. Authentication does not define which operations someone may do or which files an organization can access.
Authentication automatically detects and confirms the character of the participants or machine. Authentication is the act through which a server assesses whether or not a client is permitted to utilize a commodity or retrieve a file. Permissions is typically used with validation such that the website has to have some idea of who the customer has equal rights and access to [3].
The sort of authorization demanded may differ; usernames may well be requested in certain circumstances but not in all. In certain circumstances, no clearance is required; any customer may utilize a commodity or download a file just by requesting it. The majority of blogs on the internet do not require a password or authorization.
Figure 1: “Identification, Authentication & Authorization (IAA)” System
(Source: www.researchgate.net)
- The IAA system developed would help in recognizing the authorized people. The system would only allow the authorized people to access the system. The system can be developed in a way that only the identified users would be able to access the system. In the first step the user is required to access the system through any smart cards or qr codes.
The user is able to access the system and the system asks for its login ID and passwords. Hence the users have to provide their passwords for accessing the system further. The user first gets access to the system either through any kinds of cards or passwords.
The system then generates an OTP which is then sent to the mobile phone of the user. After the OTP sent to the mobile phone gets matched the mobile and the system gets connected [4]. Then all the information of the mobile phones can be accessed through the system. The police officers thus use this concept to get access to the mobile phone of the suspect. This would be helping the police to prevent any kinds of crimes.
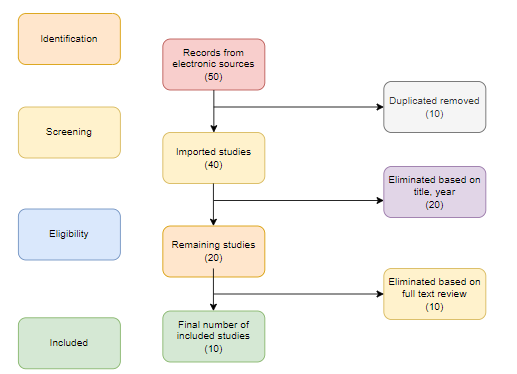
Figure 2: Login process of the “Identification, Authentication & Authorisation (IAA)” System
(Source: online.visual-paradigm.net)
Question 2
- “Ruritanian Brewing Co.” has been successful in trading at food fairs for about three years. This has been helping them to set up a successful business and enhance customer loyalty to a large extent. The company is soon going to adapt the concept of online shopping. Hence the company knows that achievement of the customer’s feedback can be immensely beneficial for improving the quality of their business.
Hence it is very essential for the company to build a system which can be beneficial for collecting and storing the information regarding the responses of the customers. Hence a system can be developed in a way that all the customers can be able to provide their feedback regarding the services provided by the company. The system should be user friendly and can be used by both physical and online customers.
The system should have a facility so that the customers can submit their ratings and reviews. This would be helping the company to identify the needs of the customers which would later help them to gain customer satisfaction and loyalty [5]. This in turn would be helping the company to enhance their overall sales and thus improving their organizational development process.
Hence the “Ruritanian Brewing Co.” is required to develop a system in a way so that the customers can find it easy to provide their feedback regarding the service provided by the customers. There are many options for obtaining the feedback of the customers. But among them all, only the most appropriate one can be chosen.
First of all a proper website can be designed regarding the business, where the customers can be able to provide their valuable feedback. The website is required to be designed in a way so that it is user friendly. The website is required to have proper web contents and should also be provided with proper navigation. This is very essential to be done to ensure that users can easily use the website properly and thus can submit their valuable feedback.
The website can contain the rating system which would help the customers to rate the service from 1 to 5. For obtaining the feedback of the customers who are physically buying the items from the mentioned company at the fairs, the concept of physical forms can be adapted. The customers can submit their feedback by filling up those forms.
The company can also send emails to the clients asking for their feedback. The customers can thus provide their feedback via emails to the company [6]. Among all the website development is the best option for getting the response of the customers. Websites with proper design would also be helping the company to attract a large number of customers.
It is also required to ensure that customers find it very easy and convenient to provide their feedback. It would also be helping the organizations in turn to gain customer loyalty and thus improving their overall business.
- Cyber Crime is one of the most major issues faced by most of the organizations these days. Hence it is very essential to maintain cyber security to ensure that all the essential business information is not hampered due to any kind of cyber crime. Data collection and analysis regarding the responses of the customers are very essential to be performed for the organizational betterment.
Thus it is very necessary to ensure that all these sensitive data regarding the customers’ feedback is collected and stored securely. Unknown hackers or intruders would generally try to interfere with the system so that they can make unnecessary changes in the data regarding the responses of the customers. This would be very harmful for the organization as it would hamper the relation between the customers and the organization.
This in turn would also be hampering the business quality of the organization. Hence to prevent the sensitive customer’s feedback from getting hacked a proper threat model can be developed properly to ensure that all the information is secured [7]. The company should be hiring highly skilled experts who can identify the possible cyber attacks and can develop the system properly.
All the employees within the company are required to be aware of the possible threats and should be following the possible measures to prevent the essential information from getting hacked.
The following measures that can be implemented for preventing cyber crimes are establishment of controls regarding network access, implementation of appropriate antivirus software and firewalls, continuous monitoring of network traffic, conduction of a risk assessment for determining vulnerability. Hence all the above mentioned steps are required to be followed by the organization to ensure that the feedback of the customers can be collected and stored properly.
This would thus help the organization to satisfy the needs of the customers as per their preferences.
Question 3
- “Burrows–Abadi–Needham logic” (or BAN logic) is a collection of principles for creating and analyzing data communication methods. BAN logic assists its consumers in determining if the knowledge being transferred is reputable, safe against surveillance, or both.
- The basis of BAN reasoning is the idea that all communication systems take place on mediums that are subject to manipulation and public surveillance. BAN semantics is mainly concerned with primary concepts. The real intricacies of the reasoning are very uninteresting, and researchers don’t think they’re necessary to master since you’re trying to develop an encryption algorithm.
- BAN logic could really establish a program’s trustworthiness; it can only detect some types of minor mistakes, assist us in reasoning about the standard, and help locate and codify our hypotheses and analyses. Many additional companies, such as GNY logic, were influenced by BAN logic [8].
In the 1990s, crypto algorithms were evaluated in frameworks with modeling analyzers, and various errors were discovered in protocols “confirmed” with BAN logic and similar mathematical abstractions. In certain circumstances, the BAN analysis also showed that a procedure was secure when it was, in reality, dangerous. As a result, BAN-family algorithms have been abandoned in favor of demonstration approaches based on the fundamental invariance arguments.
- The BAN evaluation can be problematic since it permits protocols that are unsafe to be explained as secured. They demonstrate this by demonstrating that such technique modifications are difficult to identify in underlying BAN conceptual implementations, however these variances are crucial in determining is not whether the communication is private.
Question 4
- “Unmanned Aerial Vehicle (UAV) is a vehicle that can be guided by using remote control or other devices that has sensors, transmitters, designators etc for interfering or destroying the target enemy. These vehicles, if designed properly, can operate very efficiently and can cover a large range of areas. The consent of UAV has failed due to the invention of drones and other remote controlled vehicles that are generally used by the defense or military forces in several countries after the occurrence of “World War II”.
UAVs are very essential these days for many purposes such as monitoring wildlife, delivering minimal items, surveying dangerous locations, for filming movies or any kinds of commercials, capturing live happenings etc [9]. Spoofing attack is basically defined as a situation when an unknown attacker illegally enters into an authorized device with the motive of stealing sensitive data, spreading malwares and bypassing “access control systems”.
The spoofing attack that can mainly attack the “unmanned Aerial Vehicle” is GPS spoofing. GPS spoofing generally occurs when an sender tries to send a signal through a radio transmitter to the antenna at receiver side for countering a lawful GPS signal. Attackers generally tend to block the signal in the path and make unnecessary modifications.
The receiver often receives a noise signal which can often confuse the receiver or deviates them. Spoofing attack basically occurs when the attacker is successful in breaking through an authorized system. Hence the utilization of smart security techniques is required to be used for preventing the spoofing attack.
Radio interference generally overpowers the weak “GNSS” signals and thus causes the satellite signals to get lost and thus occurs the positioning loss [10]. Hence the attacker generally tends to share fake signals to the receiver so as to deviate them with the false location.
UAV- UAV is basically a vehicle that is operated by the operator by using remote control for identifying and destroying the enemy.
Spoofing- Spoofing is basically a process of disguising the communication coming from an unknown or unauthorized source to be a trusted or authorized one.
GPS- GPS or Global positioning system helps the civil or the military users to obtain the most accurate geographical location.
GPS Spoofing- GPS spoofing generally occurs when an unlawful signal interferes with the signal in the path of transmission between the sender and the receiver.
Cyber Threats- Cyber threats are explained to be the malicious acts that tend to steal or damage information and thus hampering the digital era.
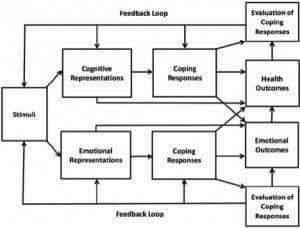
Figure 3: Flowchart for spoofing detection
(Source: www.mdpi.net)
- The spoofery accepts the genuine signal and estimates the geolocation data and sampling interval from the first stage. Then it duplicates the original signal and sends it in low voltage to obtain accuracy. The destination transmitter would not identify this operation since the only difference, in its opinion, is a little improvement in signal strength.
The spoofer then progressively increases the capacity of its replicated signal until it outweighs the genuine signal, allowing it to seize power of the transmitter. The duration of the duplicated signal is then gradually shifted [11]. In this case, the information has now become the impersonating signal but is interpreted as the “genuine” transmission by the obtaining accuracy, while the true signal is viewed as noise.
As a result, the receiver’s power source would be adjusted to coincide with the impersonating broadcast, which differs significantly in phase from the genuine bit stream. Spoofing will disrupt the reliable communication between of transmitter and network time by sporadically altering the amplitude of the GPS signal, which is crucial for calculating the propagation characteristics and hence the time delay.
Cyber threats are one of the most important aspects that affect the efficiency of the operation of UAV to a large extent [12]. Thus the use of appropriate routers, firewalls and other network gateway can be used for testing the incoming information packets. The defense mechanism that can be used in this case is the Router defense mechanism.
Hence the spoofing prevention method can be used for protecting the influence of GPS spoofing. The SPM preventive approach certifies procedures with the use of an integrated encryption key. A base station constructs a master password before delivering an IP packet. When a packet reaches its target node, routers within the networks examine the source network and validate the key.
A legitimate packet is one that has legitimate private keys, whereas a counterfeit transmission is one that does not contain cryptographic keys nor has erroneous cryptographic keys. The SPM approach distinguishes itself by marking and authenticating packets that originate from just an ASES operated with SPM [13].
As a result, if an ISP senses an assault into itself with one of its consumers, it safeguards itself from faked packets by permitting only transmissions from SPM members to get through. “Quality of experience” is defined as the acceptability of a service received by the user. “Quality of Experience” is very essential for providing the users with the desired satisfaction and loyalty. Hence it ensures that the user is receiving ultimate satisfaction from the service provided to them.
Figure 4: Flowchart for measuring GPS spoofing attack
(Source: www.researchgate.net)
Reference list
Journal
[1] Arthur, M.P., 2019, August. Detecting signal spoofing and jamming attacks in UAV networks using a lightweight IDS. In 2019 international conference on computer, information and telecommunication systems (CITS) (pp. 1-5). IEEE.
[2] Ghani, A., Mansoor, K., Mehmood, S., Chaudhry, S.A., Rahman, A.U. and Najmus Saqib, M., 2019. Security and key management in IoT‐based wireless sensor networks: An authentication protocol using symmetric key. International Journal of Communication Systems, 32(16), p.e4139.
[3] Han, R., Bai, L., Liu, J. and Chen, P., 2019. Blockchain-based GNSS spoofing detection for multiple UAV systems. Journal of Communications and Information Networks, 4(2), pp.81-88.
[4] Haque, M.S. and Chowdhury, M.U., 2017, October. A new cyber security framework towards secure data communication for unmanned aerial vehicle (uav). In International Conference on Security and Privacy in Communication Systems (pp. 113-122). Springer, Cham.
[5] Iqbal, F., Yankson, B., AlYammahi, M.A., AlMansoori, N., Qayed, S.M., Shah, B. and Baker, T., 2019. Drone forensics: examination and analysis. International Journal of Electronic Security and Digital Forensics, 11(3), pp.245-264.
[6] Jafary, B., Bhattacharya, S., Nafreen, M., Yuan, S., Zhou, J., Wu, L., Manjunath, P., Chigan, T. and Fiondella, L., 2019. The Application of Unmanned Aerial Systems In Surface Transportation–Volume II-F: Drone Cyber Security: Assurance Methods and Standards (No. 19-010). University of Massachusetts Dartmouth.
[7] Jeler, G.E. and Alexandrescu, G., 2020. ANALYSIS OF THE VULNERABILITIES OF UNMANNED AERIAL VEHICLES TO CYBER ATTACKS. Review of the Air Force Academy, (2), pp.17-26.
[8] Kabbur, M. and Kumar, A., 2021. MAR_Spoof: Securing VANET against Spoofing and Tunneling attack with cooperative assistance from RSU.
[9] Konstantinov, I.S., Lazarev, S.A., Kiselev, V.E. and Demidov, A.V., 2019. Approaches to the security analysis of authentication and authorization protocols in distributed systems.
[10] Liu, B., Yang, B. and Su, X., 2018. An improved two-way security authentication protocol for RFID system. Information, 9(4), p.86.
[11] Liu, B., Yang, B. and Su, X., 2018. An improved two-way security authentication protocol for RFID system. Information, 9(4), p.86.
[12] Liu, Y.C., Bianchin, G. and Pasqualetti, F., 2020. Secure trajectory planning against undetectable spoofing attacks. Automatica, 112, p.108655.
[12] Lykou, G., Moustakas, D. and Gritzalis, D., 2020. Defending airports from UAS: A survey on cyber-attacks and counter-drone sensing technologies. Sensors, 20(12), p.3537.
[13] Mahmood, K., Naqvi, H., Alzahrani, B.A., Mehmood, Z., Irshad, A. and Chaudhry, S.A., 2018. An ameliorated two‐factor anonymous key exchange authentication protocol for mobile client‐server environment. International Journal of Communication Systems, 31(18), p.e3814.
[14] McCoy, J. and Rawat, D.B., 2019. Software-defined networking for unmanned aerial vehicular networking and security: A survey. Electronics, 8(12), p.1468.
[15] Mridha, M.F., Al Imran, M., Wadud, M., Hussen, A. and Abdul Hamid, M., 2020. An Improved User Anonymous Secure Authentication Protocol for Healthcare System Using Wireless Medical Sensor Network. International Journal of Computing and Digital Systems, 10, pp.2-12.
[16] Sandoval, S., 2018. Cyber security testing of the robot operating system in unmanned aerial systems. Naval Postgraduate School Monterey United States.
[17] Sedjelmaci, H., Senouci, S.M. and Ansari, N., 2017. A hierarchical detection and response system to enhance security against lethal cyber-attacks in UAV networks. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 48(9), pp.1594-1606.
[18] Siu, K., Moitra, A., Li, M., Durling, M., Herencia-Zapana, H., Interrante, J., Meng, B., Tinelli, C., Chowdhury, O., Larraz, D. and Yahyazadeh, M., 2019, September. Architectural and behavioral analysis for cyber security. In 2019 IEEE/AIAA 38th Digital Avionics Systems Conference (DASC) (pp. 1-10). IEEE.
Know more about UniqueSubmission’s other writing services:

