COM7038M Cyber Security Assignment Sample
Security Governance
(a). CIA triad basically refers to “Confidentiality”, “Integrity”, and “Availability”. This is mainly designed to maintain several policies for various information securities in a particular organization. This particular model can also be defined as the “AIC triad”, which is “Availability”, “Integrity”, and “Confidentiality”, which helps to restrict confusion and issues with the CIA known as “Central Intelligence Agency”. This kind of triad always needs to be updated to be efficient. “Confidentiality” is a rule in the information system which limits the information’s access. “Integrity” is basically the assurance which tells the information is accurate. “Availability” is related to provide authentic access of information in a particular time as per user requirement.
(b) The implementation of the classical scheme is to ensure that the data that are sensitive are properly handled or not (Ula et al. 2017). The major steps or phases in the implementation of a classification scheme are as follows.
- The risk assessment of sensitive data should be completed. This basically needs a better understanding of contractual, privacy, confidential and regulatory requirements of the particular organization. The classification of the data should be defined in such a way which will involve stakeholders consisting of business, legal and compliance unit leaders.
- The classification policy which will be developed should be formalized. This is done to avoid confusion which quite sometimes becomes unmanageable. The classification of data can be public, restricted, confidential and internal. In the various types of data classification, the subcategories should be present like PCI data, financial data which is not published, GDPR-relevant and HIPAA-relevant.
- The data types should be categorized. This includes the types of customer the organization collects. The data created for the stakeholders and the customers. The transactional data to deal with the stakeholders and the customers. And lastly, in the above parts, which is the most confidential information required to give attention.
- The data location should be discovered. After the data has been established in the organization and then the data is electronically stored. There are some “data discovery tools”, which helps to find the location of the stored data irrespective of the data format.
- The data should be identified and classified. After the data is electronically stored, then the location is detected using some tools. Then the data are firstly identified, and then it is classified into their respective groups. This is basically done with the help of analysis engines with user input.
- The controls should be enabled. The security controls should be implemented. This is mainly done to determine the controlled data is sensitive or not. If it is sensitive, then it will be the various processes to protect the data.
- The data should be monitored and maintained. After the data is classified into different clusters, then the data is controlled and protected. After the data protection, the data are being monitored and maintained to meet business needs.
(c) The term “Administrative controls” are the basic procedures which basically guides all the employees and employers to deal with the information of the organization, which are highly sensitive. It basically restricts access in a working area. The six different administrative controls which are used by security personnel in a particular organization are as follows:
- The various procedures and policies of an organization.
- The hiring practices which are effective.
- The background check of the employees before joining who are recently hired by the organization.
- The process of termination is controlled.
- The classification of data and labeling is necessary.
- Security Awareness is necessary.
(d) The term “Quantitative Risk Assessment” is a particular method that provides the risk estimates and the specific parameters which describe them. This is mainly used in various sectors like industrial sectors, financial sectors and so on (Zou et al. 2018). In this, firstly, the risk is identified and analysed. Then after analysing, the risks are evaluated, and the ranks are provided. “Quantitative Risk Assessment” is basically calculated using some formulas described below.
“SLE = AV * EF” (1)
Where SLE is “Single Loss Expectancy”, AV is “Asset Value” and “EF” is “Exposure Factor”.
Now, “ALE = SLE * ARO” (2)
Where ALE is “Annualized Loss Expectancy”, SLE is “Single Loss Expectancy”, and ARO is “Annualized Rate of Occurrence”.
From equation (1), it can be said that
“ALE = SLE * ARO”
Or, “ALE = AV * EF * ARO”
So, the “Quantitative Risk Assessment” is calculated using the following formula.
“Annualized Loss Expectancy = Asset Value * Exposure Factor * Annualized Rate of Occurrence”.
(e) The fundamental principles provided in ISO/27001 for the design and implementation of an ISMS are as follows:
- Evaluation: Firstly, the information of the system are being diagnosed and evaluated.
- Planning: Then, the planning needs to be done on how the data and information should be managed to avoid the data breach. This can be done by Self-management and by hiring a particular consultant.
- Documentation: According to the planning done, the data and information should be properly documented.
- Organization: The data and information should be the organized form and well managed by a particular organization. For this, good leadership qualities are required.
- Presentation: After the documentation and the management of data and information, the final project should be presented perfectly.
- Deployment: Then, after the presentation, the project needs to be approved.
Cyber Security Incident
Introduction
The term data breach can be defined as the incident in which various pieces of information are being taken from the system without the permission and authorization of the owner of the system. The data breach is mainly faced by large organizations. The data which are stolen from the system includes sensitive and confidential information like customer data, details of the credit card and trade secrets. The various data breach methods which are observed in various kinds of industries are hacking, insider leak, physical loss, portable loss of devices and so on. In this report, an incident of cyber security will be described. The organization that is taken into account which faced a data breach is “Canva”.
Data Breach Incident
Canva is a platform for graphic designing which is used to create the graphics of social media, posters, presentations, documents and so on. The application provides templates to the user, which helps the user to design and do other things at ease. This platform also provides some paid features and subscriptions like “Canva Pro” and “Canva Enterprise”. The organization Canva was founded in 2012 by “Melanie Perkins”, “Clifford Obrecht” and “Cameron Adams”. There are around 1500 employees in the company.
The organization faced a data and security breach, which affected the user accounts of over 139 million. The particular organization faced an attack on 24th May 2019. In the attack, about 139 million profiles of the user were accessed, which include emails, usernames and other profile ids. Passwords were decrypted by the hackers using “bcrypt hashing algorithm”, and it is considered the most secured algorithm. The user who logged in the Google was claiming access to the “OAuth Login Tokens”. The hackers were able to take various information from the account, like the account number and the credit card numbers.
Technical description of the data breach
The organization faced a data and security breach which affected the user accounts of over 139 million, but the hacker could not do much. The organization “Canva” faced an attack on 24th May 2019. The hacker generally tried phishing to leak the data of the users and other important sensitive and confidential data from the organization. There was a huge loss in the organization due to the data breach. It started from around 70 million dollars which rose to more than 2.5 billion US dollars. The hacker who breached the application contacted “ZDNet” and told about the last hacking done on the other organization, which the hacker breached a few hours ago. The data that is stolen includes real names, username, address, email and so on. The hacker mentioned, “I download everything upto May 17. They detected my breach and closed their database server”. Due to some advanced security measures, the organization managed to save itself from more breaches (Schinagl et al. 2020). About 139 million profiles of the user were accessed, which include emails, usernames and other profile ids. Passwords were also encrypted by the organization using the “bcrypt hashing algorithm”, and it is considered the most secured algorithm which can avoid data losses and hacking.
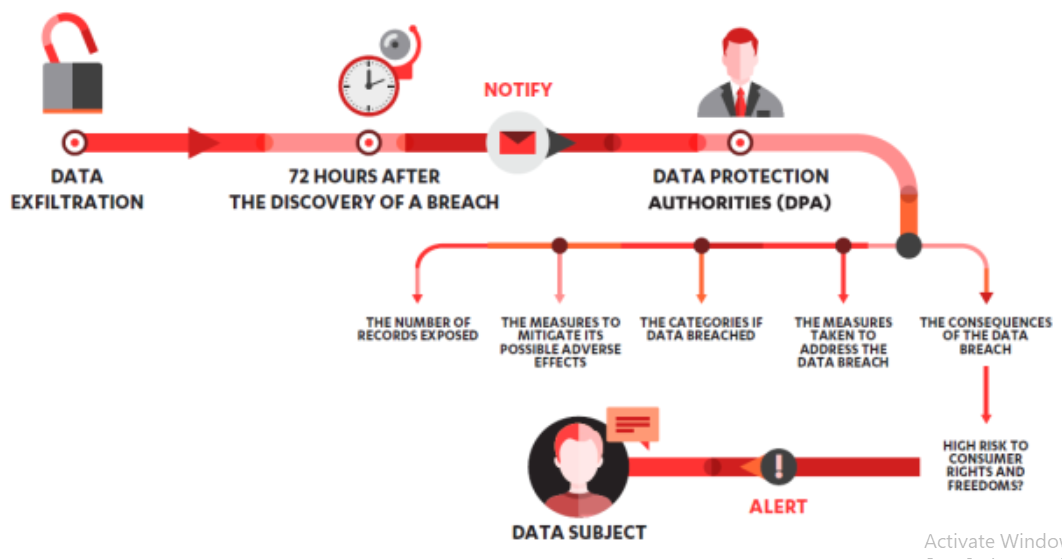
Figure 1: Data breach notification procedure
(Source: https://i.pinimg.com/originals/38/3d/fc/383dfc6503c0e2245f86a07dad83e01b.png)
The user who logged in the Google was claiming access to the “OAuth Login Tokens”, which makes the profile and the account of the user more secure and hard to crack. Each and every organization should follow the data breach laws to beware of the attacks, which can result in huge losses. There are various weaknesses or vulnerabilities that the hackers exploited for breaching the particular company. They basically took the zero-day advantage. In this, the hackers took various steps. Firstly a “Zero-day” exploit had been discovered by the hackers, and then they found a specific way to use it. The hackers found a flaw and then caused the software to crash or misbehave. Then the software is reversed engineered by having the source code or binary code or by the approach of the black box. In this way, the hacker breached the organization and which resulted in a huge loss of the company.
ISO/IEC 27001
The clauses in the ISO/IEC 27001 that the company did not follow, which could have contributed to the data breach, are as follows.
Scope: This is based on the characteristics of business, location and technology.
The approach of the Risk Assessment: This includes the method of the risk assessment, regulatory and legal requirements. This also includes the criteria and risks of acceptance.
Risk identification: This includes various threats, vulnerabilities, availability and integrity. In addition to that, it identifies the asset and its owner.
Risk analysis: This is basically the analysis of the risk in the organization.
Risk evaluation: This refers to the estimation of the risk levels.
Risk treatment: This refers to risk avoidance and the transfer of risks to various parties.
Control objectives: This refers to the various implementation and selection of the controls based on risk assessment and the process of treatment. The controls that the companies should take in order to avoid such breaching in the future are as follows.
The organization should consult with the legal counsel. This should be followed in every organization if they faced a recent data breach. The organization should follow the data breach laws to beware of the attacks, which can result in huge losses.
The systems and data should be more secured. After the company faced the breach, the company should hire more experts who will determine the accessed data and the way it was being accessed and the thing that was most and least effected in the particular data breach. The data and information should be the organized form and well managed by a particular organization. The part that was more attacked need to be more secured.
The relevant parties should be notified. The parties that are linked with the organization should be informed (Cheng et al. 2017). Along with this, the user of the applications should be informed so that they maintain security among themselves. The organization should follow the data breach laws to beware of the attacks, which can result in huge losses. So this should be done in order to be more protective.
Correct vulnerabilities must be used to prevent the breaches further. The hacker basically took the zero-day advantage. In this, the hackers took various steps. Firstly a “Zero-day” exploit had been discovered by the hackers, and then they found a specific way to use it. This should be noticed, and the securities must be improved. Access to various critical data should be reduced and audited. The sensitive data should be encrypted, and the authentication security should be improved.
The management should be strengthened. The data and information should be the organized form and well managed by a particular organization. For this, good leadership qualities are required.
Conclusion
From the report, it is concluded that the company need to follow the clauses that will reduce the chance of data breach. The various data breach methods which are observed in various kind of industries are hacking, insider leak, physical loss and portable loss of devices. The organization should follow the data breach laws to reduce the attacks. The risk assessment of sensitive data should be completed, and this needs a better understanding of contractual, privacy, confidential and regulatory requirements of the particular organization. The classification of the data should be defined in such a way which will involve stakeholders consisting of business, legal and compliance unit leaders. In order to make it more secure, the best algorithm should be used.
Reference List
Journal
Cadwalladr, C. and Graham-Harrison, E., 2018. Revealed: 50 million Facebook profiles harvested for Cambridge Analytica in major data breach. The guardian, 17, p.22.
Cheng, L., Liu, F. and Yao, D., 2017. Enterprise data breach: causes, challenges, prevention, and future directions. Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery, 7(5), p.e1211.
Gashgari, G., Walters, R.J. and Wills, G., 2017, April. A Proposed Best-practice Framework for Information Security Governance. In IoTBDS (pp. 295-301).
Gehred, A.P., 2020. Canva. Journal of the Medical Library Association: JMLA, 108(2), p.338.
Ibrahim, A., Thiruvady, D., Schneider, J. and Abdelrazek, M., 2020. The Challenges of Leveraging Threat Intelligence to Stop Data Breaches. Front. Comput. Sci. 2: 36. doi: 10.3389/fcomp.
Petrova, M.H., 2018. Weapons prohibitions through immanent critique: NGOs as emancipatory and (de) securitising actors in security governance. Review of International Studies, 44(4), pp.619-653.
Schinagl, S., 2020. What do we know about information security governance?‘From the basement to the boardroom’: Towards digital security governance. Res. IT-Auditing Multidisciplinary View Ed., p.135.
Shu, X., Tian, K., Ciambrone, A. and Yao, D., 2017. Breaking the target: An analysis of target data breach and lessons learned. arXiv preprint arXiv:1701.04940.
Sunandi, S.D. and Koesrindartoto, D.P., SBM ITB Proceedings.
Sunandi, S.D. and Koesrindartoto, D.P., USER’S ACCEPTANCE OF BIOMETRIC AUTHENTICATION SYSTEM.
Ula, M. and Fuadi, W., 2017, February. A method for evaluating information security governance (ISG) components in banking environment. In Journal of Physics: Conference Series (Vol. 812, No. 1, p. 012031). IOP Publishing.
Zou, Y., Mhaidli, A.H., McCall, A. and Schaub, F., 2018. ” I’ve Got Nothing to Lose”: Consumers’ Risk Perceptions and Protective Actions after the Equifax Data Breach. In Fourteenth Symposium on Usable Privacy and Security ({SOUPS} 2018) (pp. 197-216).
Know more about UniqueSubmission’s other writing services:

