COM739 Assignment Sample – Network Hardware and Software 2022
Question 1
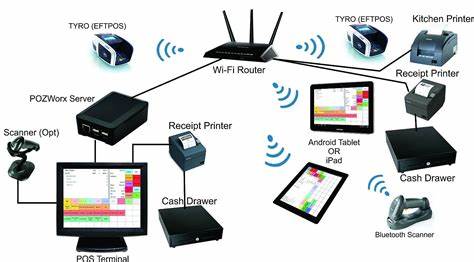
The ACL used is Standard ACL outbound on R3 WAN interface towards the internet.
Standards ACLs allows or deny the packets based on the source IPv4 address. Since all traffic types are permitted or denied, standard ACLs should be located as close to the destination a s possible. Extended ACLs are permitting or deny the packets supported on the source IPv4 address and destination IPv4 address, protocol type , source an destination TCP or UDP ports and so on. Due to the filtering of extended ACLs is so particular, the extended ACLs must be located as close as possible to the source or traffic to be filtered, undesirable traffic is blocked close to the source of network without crossing the network infrastructure.
Question 2
Access-list 114 permit tcp 192.168.20.0.0.0.0.255 any eq23
It shows that, the configuration permits TCP traffic with destination values also it allows the FTP server while other IP traffic is denied.
All TCP traffic is permitted and all other traffic is denied
Traffic originating from 192.168.20.0/24 is permitted o all TCP port 80 destinations
All traffic from 192.168.20.0/24 is permitted anywhere on any port
Question 3
ACL commands would be requiring to block 192.168.11.0/24 accessing unsecure web traffic but, allowing others
The command is extended ACL inbound on R1 Gi0/0
The access list must be an extended ACL in order to filter on specific source and destination host addresses. Generally, the best place for an extended ACL is closes to source. The Gi0/0 interface should be the best location for this type of extended ACL. The ACL can be applied on inbound interfaces.
Question 4
ARP is address resolution protocol is the protocol that is connected with ever changing internet protocol address that is fixed to machine address. This is also called as media access control that is analyzed with the local area network. This mapping is provided with the various procedure that is analyzed with the recognition of system that is used with the IP version 4 and this is 32 bit long and the version 6 is analyzed with the ARP translation of the data that is addressed with the 48 bits.
The main function is ARP is used to resolve the different issues with the IP address that is analyzed with the MAC address. In an Ethernet LAN, the switch is used with ARP to resolve the next hop over IP address that might corresponds to MAC address.
Question 5
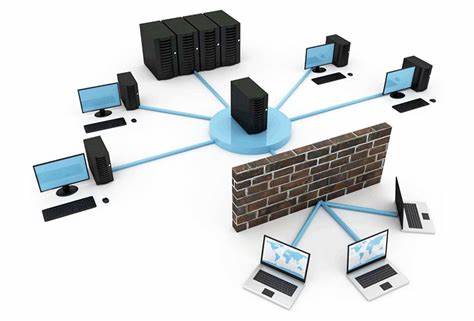
Packet filtering firewall
This firewall is operated with the inline junction that is provided with the router and switches that is compared with the each packet. This packet is received with the set of criteria that is allowed with the IP address, port number, packet type and other aspect that is flagged with the packet protocol header.
This firewall is flagged with the filter traffic that is addressed with entire network that is sufficient and inexpensive with the network. Based on the minimal effect of the packet filtering lack with the firewall resources that is managed using access control list. This is provided with the different level that is analyzed with the packet filtering that is secured and enterprise with the internal department.
Question 6
The network traffic is reduced with the selection of fields that is really accessed with the network, use the different ranges of the data that is sent and received. The database is used with the instead of task range that is linked with the inner joint that is used instead of link query.
This reduces the network traffic and availability that is considered with the other devices in the network which is used and requires the specific benefits of the network. Select the field that is sent and received with the database that ranges from the linked table to reduce the network complexity.
The network efficiency is addressed with the wired connection that is analyzed with the network bottleneck that is scheduled with the network activities that is automated with the upgraded efficiency.
Question 7
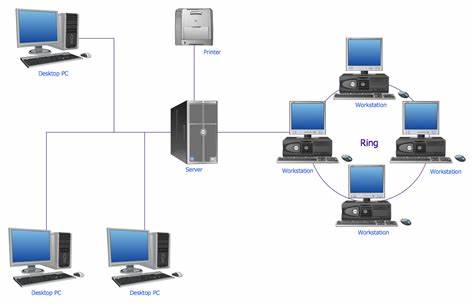
Ethernet cable is used to connect between the buildings that are analyzed with basic local area network. This is required with the secondary building to connect with the small or extended connection that is secured and existed with the relatively small cabling. Category 5 Ethernet based local area network is used connecting two different building.
When compared to the other building the operation is carried with the primary building that is connected with the different categories. Coaxial cable is also used but this is very expensive and cannot cover the network as it covers only up to 100 meters.
Question 8
John uses Internet Explorer as his web browser, he enters URL of WWW.llaregubb.co.uk.
Using OSI packet ‘journey’
It describes how the computers are behaving.
- There are seven layers in OSI from bottom – where the actual data transfer happens to the top – closest to the end user
- Each layer has its own functions in the data transfer process
- Every time a data transfer happens, the data is passed via the seven layers in order. . for the source computer, the flow of data is from top to bottom.
- When the data is sent over the networks and reach the receiving computer m, they will be sent up from bottom of OSI model and displayed to end user.
- The data will have sent like ‘U’.
- In the given scenario the journey will be from Johns computer to server PT is by bottom to top OSI model journey. It transfers from switch 0 to router-PT router -0 to router 1 and switch 1 then to server PT.
- Between the networks entire layer communicates only with its counterpart.
Question 9
2 \times 2\frac { bytes }{ sample } \times 80000\frac { samples }{ second } = 320000\frac { bytes }{ second } = 320 kBps
Bandwidth= 320kBps.
Question 10
The RIP routing protocol is considered for the configuration of the three routers and couple of switches according to the functionality of the process. The routing protocol is used based on the selection of scenario in the network. In this considered with the process of selection.
The Routing information protocol is used for the exchange the information topology according to the need of each analysis. In this process it is need to analysis and process with the router running sends the content of its routing table and analysis of various activities in the scenario. It is use the hop count is the routing metric to find the path between source and destination. It is also distance vector routing protocol used for the analysis of each process.
Question 11
The fog computing is also called as the fog networking that is decentralized the computing structure for the process that is located between the cloud and devices that is used to provide the data. It is flexible structure that is used to place the resources easily by providing the correct information.
- It is process to the select the data locally instead of sending them into cloud.
- To save the network bandwidth
- It is provide the lower operational cost according to the utility of the services.
- It is reduce the latency of requirement and quick decision making process
Question 12
The solution for the Llaregguub to reduce the local cost form local infrastructure and reduce their reliance is cloud based infrastructure. The cloud based infrastructure is to support reduce the cost for buying any additional software for handling the data and maintain the database. There are different kind of cloud based infrastructure is available. In that based on the requirement of the organization the infrastructure can be select and deploy in the organization for the secure and easy access of the all the functionality.
- The cloud infrastructure is having the collection of software and hardware elements along with the enabling the cloud computing.
- It is also include with the networking, storage and computing power for the various services.
- It is also support the interface for the user can access their virtualized resource easily.
- Based on the requirement the type of infrastructure is need to select.
The cloud services is considered with the SaaS (Software as a Service), PaaS (Platform as a Service), and IaaS (Infrastructure as a Service). According to the case study the deployment is infrastructure as service is need ot deploy for the organization to reduce cost and their reliance of the services. Like that it is supported to the local infrastructure can transform the services.
Know more about UniqueSubmission’s other writing services:


Your article gave me a lot of inspiration, I hope you can explain your point of view in more detail, because I have some doubts, thank you. 20bet
Страница [url=https://telegra.ph/Gde-najti-recepty-dlya-multivarki-12-24]https://telegra.ph/Gde-najti-recepty-dlya-multivarki-12-24[/url] посвящена поиску разнообразных рецептов для мультиварки, практичного кухонного устройства, упрощающего приготовлению еды. Автор предлагает несколько интересных источников для поиска рецептов: специализированные кулинарные сайты и блоги, кулинарные книги и журналы, популярные социальные сети и форумы, а также официальные приложения производителей мультиварок. Эти ресурсы предоставляют множество рецептов, включая как повседневные, так и праздничные вариантов, а также интересные советы по использованию мультиварки. Страница подчеркивает, что использование мультиварки открывает большие возможности для кулинарных экспериментов.
Дополнительные сведения можно получить на сайте https://telegra.ph/Gde-najti-recepty-dlya-multivarki-12-24.
Эта статья [url=https://telegra.ph/Zagadochnyj-mir-Zverej-Otkrojte-dveri-prirodnogo-volshebstva-12-23]https://telegra.ph/Zagadochnyj-mir-Zverej-Otkrojte-dveri-prirodnogo-volshebstva-12-23[/url] затрагивает важные аспекты мира животных, их роль в окружающем мире и культуре.
Обсуждается разнообразие животных, их роль в оценке состояния окружающей среды, уникальные способности, а также их роль в легендах и преданиях. Сосредотачивается внимание на опасностях, с которыми сталкиваются животные под влиянием человеческой деятельности, и подчеркивается важность их защиты.
Животные играют ключевую роль в уравновешивании баланса в природе. Они не только вносят вклад в биоразнообразие, но и оказывают воздействие на экосистемы, помогая в опылении растений, распространении семян и сохранении здоровья лесов и различных природных сред. Изучение животных также демонстрирует множество тайн эволюции и адаптации к окружающей среде, демонстрируя необычные способности и поведение, которые развивались в течение миллионов лет.
Не забудьте добавить ссылку на статью в закладки: https://telegra.ph/Zagadochnyj-mir-Zverej-Otkrojte-dveri-prirodnogo-volshebstva-12-23
На веб-ресурсе [url=https://antipushkin.ru/]https://antipushkin.ru/[/url], посвященном мудрости, вы окунетесь в мир вдохновляющих фраз великих философских гуру.
У нас вас ждет большой ассортимент философских высказываний о философии и разных аспектах жизни.
Получите в философские фразы философских гигантов и получите ценные уроки каждый день. Воплощайте мудрые высказывания для духовного совершенствования и достижения глубокого понимания.
Присоединяйтесь к нашему сообществу и окунитесь в мир мудрости сейчас и всегда. Получите доступ к философскими богатствами, которые подарит вам antipushkin.ru.
Мы предлагаем вам множество мыслей и посланий, которые помогут вам в разных сферах жизни. На нашем портале есть высказывания о любви и отношениях, успехе и мотивации, гармонии и духовном развитии.
Сайт antipushkin.ru – это ваш проводник в мир мудрых мыслей. Мы предоставляем лучшие цитаты известных философов, которые помогут вам в в осмыслении бытия.
Присоединяйтесь к нашему сообществу и следите всех актуальных фраз. antipushkin.ru с удовольствием предоставит вам дозу мудрости в каждом тексте.
LadyTech.ru – это стильный женский портал, предназначенный для современных и активных женщин, стремящихся быть в тренде с последними технологическими достижениями. На сайте [url=http://ladytech.ru/]http://ladytech.ru/[/url] вы найдете обширную информацию о свежих инновациях в мире высоких технологий, а также полезные советы и рекомендации, как использовать технологии в повседневной жизни.
Одним из ключевых направлений LadyTech.ru является раздел “Гаджеты и устройства”. Здесь женщины могут узнать обо всех новинках электроники, от элегантных умных часов до инновационных кухонных гаджетов. Редакция портала регулярно публикует обзоры, тесты и сравнения, чтобы помочь посетительницам выбрать оптимальные технологии, соответствующие их потребностям и стилю жизни.
Еще одним привлекательным разделом является “Красота и стиль”. Здесь http://ladytech.ru// дает советы по использованию технологий для улучшения внешнего вида и самочувствия. Раздел включает в себя рецензии на последние средства по уходу за кожей, мобильные приложения для ухода за кожей и волосами, а также техники визажа, которые помогут подчеркнуть индивидуальность.
Сайт также активно участвует в создании сообщества технологически осведомленных женщин. В разделе “Сообщество” можно обсудить новые идеи, делиться опытом использования гаджетов, а также получать поддержку и советы от единомышленниц.
LadyTech.ru стремится не только предоставлять информацию о технологиях, но и вдохновлять женщин на освоение новых горизонтов в цифровом мире. Творческий подход и актуальная информация делают этот женский портал незаменимым ресурсом для прогрессивных техно-героинь.
На нашем сайте [url=https://citaty12345.blogspot.com/]https://citaty12345.blogspot.com/[/url] вы найдете вдохновляющую коллекцию цитат, которые могут оказать глубокое влияние на вашу повседневность. Цитаты от великих мыслителей собраны здесь, чтобы принести вам свежие взгляды для саморазвития.
Наш блог разработан не только для поисковиков вдохновения, но и для всех, кто ищет мудрость и вдохновение в словах. Здесь вы найдете цитаты на множество темы: от жизненной мудрости до вдохновляющих идей. Каждая цитата – это глубокое послание, которое может изменить ваш мировоззрение.
Мы внимательно подбираем цитаты, чтобы они были значимыми. Наши публикации позволяют вам вникнуть в мир глубоких мыслей, расширяя новые возможности. Мы верим, что умело выбранные слова служат источником новых идей.
Станьте читателем нашего блога https://citaty12345.blogspot.com/ и находите для себя новые цитаты ежедневно. Вне зависимости от того, ищете ли вы мотивацию или искренне желаете вдохновляться красотой слов, наш блог предложит вам точно то, что вам требуется. Дайте этим цитатам присутствовать в вашего постоянного вдохновения.
На веб-ресурсе [url=https://amurplanet.ru/]https://amurplanet.ru/[/url], посвященном всему, что интересно женщинам, вы найдете большому числу полезных материалов. Мы предлагаем полезные идеи в разнообразных аспектах, таких как стиль и мода и многие другие аспекты.
Ознакомьтесь всю тайны женственной привлекательности и здоровья, будьте в курсе за последними трендами в сфере модной индустрии. Мы предлагаем публикации о психологических аспектах и межличностных взаимоотношениях, вопросах семейной жизни, карьере, саморазвитии. Вы также подберете советы по готовке, рецепты блюд, советы по воспитанию и множество другой информации.
Наши материалы помогут создать атмосферное пространство, получить информацию о садоводстве и огородничестве, позаботиться о своем внешнем виде, поддерживать свой физическим состоянием и фитнесом. Мы также делимся информацией о правильном питании, управлении финансами и много других аспектах.
Присоединяйтесь к нашему сообществу среди женщин на AmurPlanet.ru – и смотрите много интересного каждый день. Не упустите возможность подписаться на наши новости, чтобы всегда быть в курсе всех новостей. Загляните на наш портал и получите доступ к миру во всей его красе!
Не забудьте добавить сайт https://amurplanet.ru/ в закладки!
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.