Data Communications Programming Assignment
Tutorial Review on Data Communication
Introduction
In this study we are going to see an overview of Digital communication and the evaluation of digital communication through the past years. How the growth of digital communication paved the way for TCP/IP protocols and the need for security protocols. A small implementation is made using _ to show the packet sent through the TCP/IP protocol and the packets that are receive by the receiver the overhead involved in the transmission of the packets, the delay incurred in the transmission of packets along with packet drop ration of TCP/IP and TCP/IP with IPSec are shown in the appendix. Different network security protocols that are used in different layers are overviewed in this paper.
Digital Communication
The data transmission is growing rapidly which made the digital communication systems more attractive. Due to COVID-19 all the schools and college are locked down and digital communication has paved the wave for teachers to teach students with the help of digital communication. Many people are working from their home this is possible due to the flexible options available in the digital communication. The main reason for the growth of digital communication is due to VoIP (Voice over Internet Protocol), Data transmission and internet connections. Development of hardware and software for digital message is one of the emerging areas in the world of digital communication. In today’s digital world most of the communications made are in the form of digital communication through analog mode. While transmitting the data through the digital mode it is robust to vulnerability due to noise and other distortion in the communication channel. Since the communication needs travel a long distance a regenerative repeaters are used along the transmission path which detect the digital signals and increase the potency of the gesture and transmit the signal through the path by retransmitting it in a new noise-free signal. Digital communication is widely used since it can produce codes with low error rate and high fidelity. Digital communication involves how the data send by the source machine reaches the destination machine. To understand the modern-day communication technology the basic rules about the process of digital message is an essential feature.
History of Digital Communication: Telegraph was the first digital communication in which few words are spread by Morse’s through telegraph in the year 1844 when the first real-time long distance communication started. Telegraph used a manual keying to indicate the digital communication. It used the Morse Code which is a variable-length code technique which used an alphabet of four symbols a dot, a dash, a letter space and a word space; the short sequences represent frequent letters while the long sequences are infrequent letters.(Viterbi et al, 2013).
Telephone invented by Alexander Graham Bell in the year 1875 was used to transmit speech by programming the voice into electrical sign and duplication of sound. It was first used to talk over a short distances since the original version was simple and weak. In the year 1897 A.B. Strowger and his team invented the switch which is an automatic step-by-step switch. In 1928 Harry Nyquist theory on signal transmission in telegraphy established an accurate reception of telegraph signals. In the transmission of digital data Nyquist’s work is most commonly used over dispersive channels. After the invention of Pulse-Code Modulation (PCM) technique in the year 1937 which was used to encode digital speech signals made the encryption of speech signal possible. After the invention of the transistor and large scale integrated circuits PCM technique had some qualitative changes. The foundation for digital communication was started in the year 1948 after the publication of the paper ‘A Mathematical Theory of Communication’ by Claude E. Shannon. (Shannon C.E., 2001).
Error protection: In digital message system the data transmitted are in the form of binary bits, which are modulated to analog signal and transmitted in through the communication channel. There is a chance to corruption of these bits while traveling due to the noisy channel. Once the receiver receives the analog signal will demodulate them into binary bits. Since the bits are traveled through a noisy channel there is possibility for errors to occur depending upon the noise in the channel the error bit ration may vary. Error control coding techniques are used to process the error recognition and rectification of the errors which take place through the transmission. Most of the digital announcement systems are applying the fault control code to provide a powerful code for optimal performance.
Digital communication devices are more popular after the popularization of computer and internet there is a great shift in the communication field. The digital revolution has erased the communication gap among the people. Today people in any corner of the world can communicate with each other due to the development in digital communication technology. The social networking with the help of three significant relevance of the digital world the World Wide Web (WWW), Mobile communication and the Satellite communication have changed the way of communication technology.
Social networking is one of the advancement in the digital communication technology which allows people to share their profiles, pictures, video etc with their friends, family and other persons all over the world. This makes the interaction among the people with the social networking sites. But the usage of these sites has both positive and negative impacts. The main aim of these social networks is to help people who are staying away from their friends and family to keep in touch with their friends and family members. It also helps to find friends who have common interest and share their knowledge. Social network helps to connect people and to deliver their products. The news spreads quickly with the help of the social networking sites. But now a day’s many of them are using these social networking sites to make false and unreliable information. It is created to find new friends but many of them are using this friendship in a negative way and that leads to many problems in the family. Cyber bullying is one of the growing problems in the social networking sites. Many people are addicted to social networking sites which is one of the emerging problems since many of them are wasting their time in social media. Smart phones had made the growth of this digital communication and social media network more accessible. People are posting their photos and video to get likes in the social media without knowing the problems behind that. Digital communication technology made the communication among people much faster but the use of technology should be in the right way. Orthogonal frequency division multiplexing (OFDM) is most commonly used modulation technique in digital communication which provides a secured performance. Packets are send using the OFDM based system and simulations are done using MATLAB the results produced are given below
Figure 1 shows the transmission of packets among the nodes in the network.
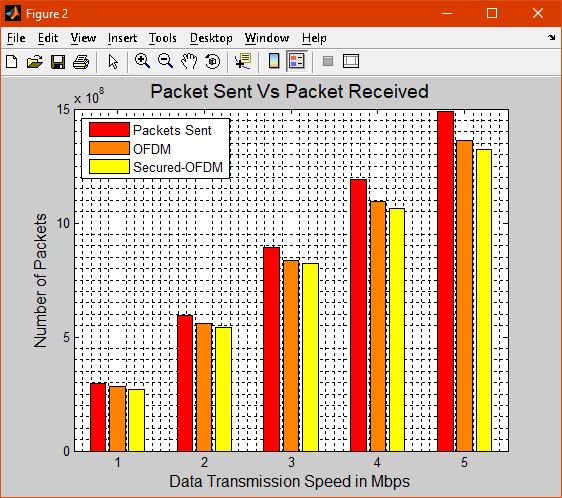
Figure 2 shows the packets sent using OFDM and Secured OFDM
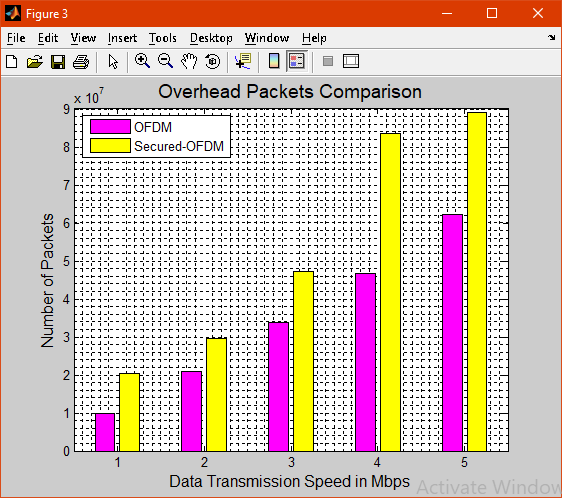
Figure 3 shows the overhead of packets
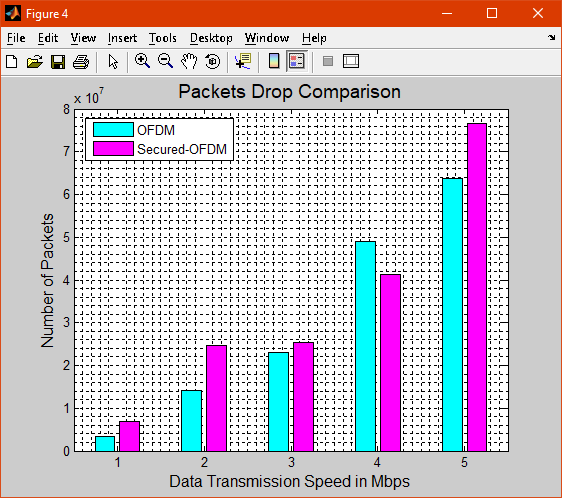
Figure 4 shows the packet drop ration of OFDM and secured OFDM
TCP/IP
The main drawback of TCP/IP protocol is lack of authenticity and privacy of data. Due to the increased use of internet and its application security enhancement should be implemented with the TCP/IP to provide a secure protocol IPSec was developed. TCP/IP protocol was developed for a small number of users and for static web pages. But in the today in the world of digital communication the usage of these protocols are increased and the security issues arise while transmitting the data. A numerous methods have evolved to address the security problems but most of it focuses on the OSI protocol stack to compensate the lack of IP security. The SSL protocol was created to be implementing with application like World Wide Web access, FTP etc many of the application never work with this protocol. IPSec is single protocols that provide a complete solution for the security issues in the IP network. It provides various types of protections for any higher-layers of TCP/IP application protocol without any addition security measures. IPSec includes encryption of the user data, provide authentication and integrity to the message, it protect the message from certain attacks like replay attacks. It can negotiate the security algorithm keys. It supports two types of security modes tunnel and transport. The IPSec standard is defined in RFC 2401, RFC 2402, RFC 2403, RFC 2404, RFC2406, RFC 2408, RFC 2409 and RFC 2412 since it is a combination of techniques and protocols it is not defined in a single standard. IPSec provides security service for the protocols and applications in the IP layer. So it acts as a tool for secure communication among the devices by establishing a secure path. To establish a secure path the sender and receiver must agree with a set of protocols to be used to send and receive the data and the encryption algorithms they are going to use in the data encoding. They also exchange keys to unlock the encrypted data. To perform all the actions IPSec use different components and are made as a package which is also called as the core protocols of IPsec.
IPSec Authentication Header (AH) is used to provide authentication service. It checks whether the message that was received is supposed to be originated for the one who sent it and also verify the intermediated devices have changed the data while the data is transmitted through the transmission channel. It protect the data from the reply attack where an intruder capture the original message send by the sender and resend a new message as if it is send by the original sender. Encapsulation Security Payload (ESP) ensures the privacy of the data. It protects the data by encrypting the payload of the IP datagram.
The components of IPSec AH and ESP are known as protocols even though they are not a distinct protocol they are used as a header of the IP datagram. IPSec provide authentication and privacy to the data send in the communication channel. For proper functioning of the IPSec it needs the support of several other protocols and services.
IPSec has two basic modes of operation transport mode and tunnel mode. In transport mode it use AH and ESP header to the original IP datagram packets with integrate IPSec architecture. But in tunnel mode the IP datagram is created normally and the entire datagram is encapsulated using AH/ESP headers.
With the help of MATLAB packets are sent from servers to the different client nodes using TCP/IP protocol and TCP/IPSec protocol and a comparison is made among these protocols. The numerical results of the implementation of these protocols shows that while packets are sent using TCP/IP the packet received rate is high when compared with packets send using TCP/IP with IPSec. The overhead involved in TCP/IP with IPsec is high while that of TCP/IP is low. The delay caused in sending the packet to the destination is high in TCP/IP with IPSec when compared with TCP/IP this is due to the security checks made in the TCP/IP with IPSec. The packet drop ratio is also high in TCP/IP with IPSec since it will not allow the message that are hacked by the intruder and drop those packets so the packet drop ratio is also high in TCP/IP with IPSec. The numerical results of the implementation are shown in the below table.
Numerical Results
| Packets Sent | Packet Received | Overhead | Delay | Packets Drop | ||||
| TCP/IP | TCP/IP with IPSec | TCP/IP | TCP/IP with IPSec | TCP/IP | TCP/IP with IPSec | TCP/IP | TCP/IP with IPSec | |
| 297619000 | 284345193 | 270327338 | 9851189 | 20357140 | 105.78 | 169.01 | 3422619 | 6934523 |
| 595238000 | 560357053 | 540952294 | 20833330 | 29642852 | 166.18 | 399.58 | 14047617 | 24642853 |
| 892857000 | 835982009 | 820267726 | 33839280 | 47142850 | 194.82 | 405.95 | 23035711 | 25446425 |
| 1190476000 | 1094880777 | 1065714115 | 46666659 | 83452368 | 262.24 | 571.29 | 48928564 | 41309517 |
| 1488095000 | 1361904544 | 1322321217 | 62351181 | 89136891 | 276.18 | 603.38 | 63839276 | 76636893 |
The graphical results of the implementation are shown below
Figure 1 shows the configuration of server and other nodes that are involved in sending and receiving the packets send using the TCP/IP and TCP/IP with IPSec.
Figure 2 shows the transmission of packets among the nodes
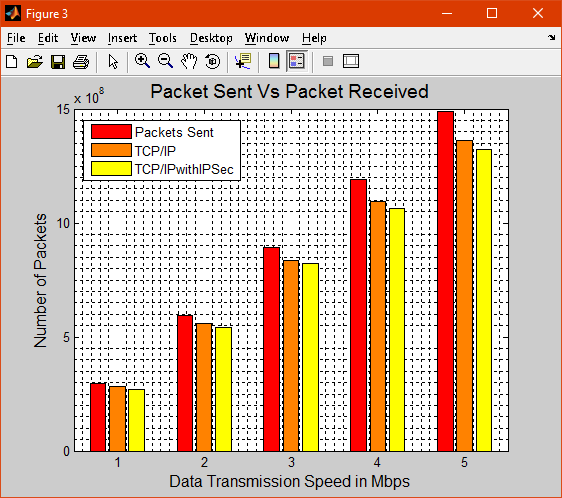
Figure 3 shows a comparison of packet sent and packet received using TCP/IP and TCP/IP with IPSec it shows that the packet received is less in TCP/IP with IPSec when compared with TCP/IP.
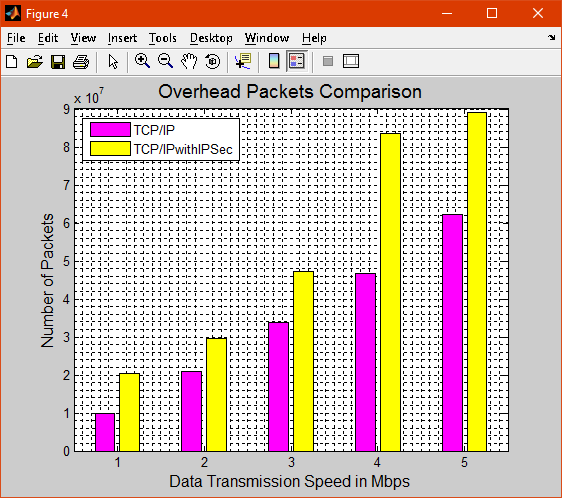
Figure 4 shows the overhead packets while transmitting the data and the overhead of packet is high in TCP/IP with IPSec when compared with TCP/IP.
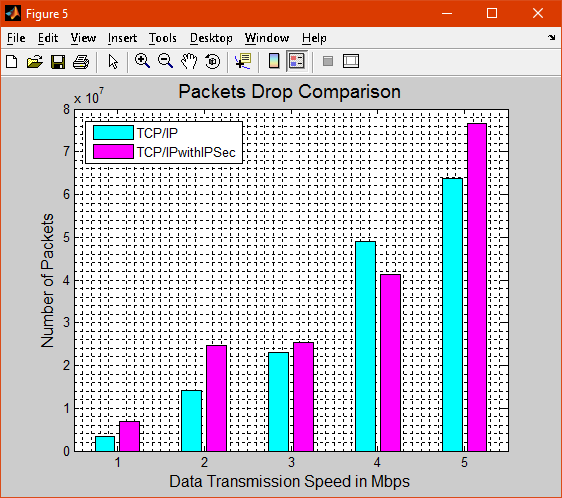
Figure 5 shows the packet drop ratio of TCP/IP and TCP/IP with IPSec from the graph it is clear that the packet drop ratio is high in TCP/IP with IPSec.
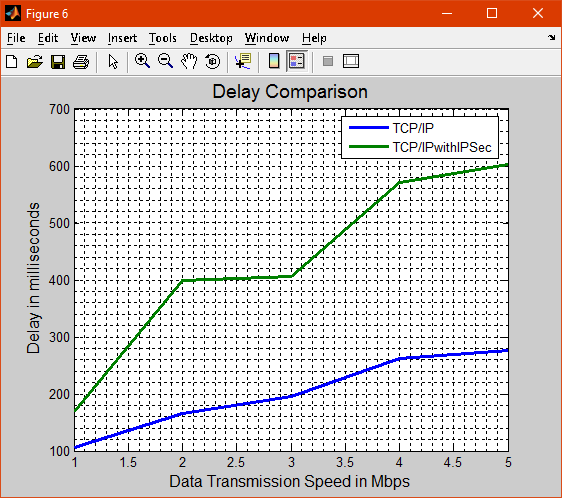
Fig 6
Figure 6 shows the delay in transmission and it shows that TCP/IP with IPSec has a huge delay while TCP/IP has a relatively small delay.
Network Security Protocols
Due to the hasty increase of digital communication there was a emergent insist for security and privacy of the data that are broadcast through the digital message channels. Network safety protocols are considered to prevent the unconstitutional access of the data from the network. Most of the safety protocols use the encryption and cryptography practice for the secure transmission of data through the digital channel. Some of the most commonly used safety protocols are Secure File Transfer Protocol (SFTP), Secure Hypertext Transfer Protocol (HTTPS) and Secure Socket Layer (SSL). The main objectives of these protocols are to protect the data from malicious users in the network. As the growth of digital communication increase the growth of attacks also increases equally so the need for security protocols are also increasing day by day which is a difficult and challenging task. Safety and privacy policies are necessary for message through the digital media.
PGP (Pretty Good Privacy) is one of the most common and important protocol use to protect information by encrypting the e-mails and additional forms of message for the security and privacy of the messages sent. It was created by Phil Zimmermann uses a public-key cryptosystem. It works by generate a belief between its users and create a circle. The users in this circle create public key and using these key they encrypt the message. It is used to sign communication in the digital signature it is used to validate the genuineness of the file received. It is mainly used in email message to check the files downloaded from the internet are secure.
S/MIME (Secure/Multipurpose Internet Mail Extension) protocol is an expansion of MIME. A digital signature is used to encrypt the message. MIME protocol specifies how the messages, pictures, video files, and audio files are transferred through the digital media. This protocol was described in RFC 1521. When a client request for a web certificate the web server send the demand file to the client along with a MIME header. Every message send as an email will consist of the two parts they are MIME header and the body. S/MIME supports three public key algorithms to encrypt the broadcast of message. The three encryption algorithms used in S/MIME are Diffie-Hellman, RSA and triple DES.
Secure HTTP (S-HTTP) is an extension of Hypertext transfer protocol. HTTP protocol was developed to handle static web pages. But now the web pages are dynamic have lots of graphics. So protocols with cryptographic and realistic improvements were created to enable e-commerce. Each files sent through S-HTTP is encrypted or it enclose a digital certificate some files may contain both encryption and digital certificate. S-HTTP provides a secure communication mainly for commercial transaction among the HTTP client and the server. It follows various mechanisms to endow with privacy, substantiation and truthfulness of the message send. Usually all the messages send through HTTP has two components a header and the body. The header part contains information to the recipient’s browser how to process the received message body. While transferring the message’s both the client and the server utilize the message provided by the HTTP header for negotiation of the file. The S-HTTP protocols extend this negotiation for security purpose by using an additional header showing the message encryption and digital certificate in the HTTP format along with the information to decrypt the message.
Kerberos is a network substantiation protocol to authenticate the users, clients and servers. It uses a secret key for authentication. To make the communication secure between the client and server using Kerberos they identify each other after the identification process the announcement between the client and server are encrypted to guarantee the confidentiality and data honesty of the message send.
Secure Socket Layer (SSL) is a common purpose cryptographic system mainly used in Netscape navigator and internet explorer. This provides an encrypted end-to-end path among the client and the server. It provides a secured authentication service by encrypting the data, authenticate the server and message integration along with a client substantiation for TCP connection. It uses HTTP, LDAP or POP3 application layers. It is same as S-HTTP but there are many difference in the design and implementation of these protocols. S-HTTP was designed for web protocol while SSL is used in network protocol. SSL is implemented at minor level while S-HTTP has replaced the socket API in the application layer.
Transport Layer Security (TLS) is a standardization of secure method for web communication. TLS charged for on condition that safety and data reliability at transport layer. The new standard is SSL/TLS. The ability for interoperability and to exchange the TLS parameter among the sender and receiver without a need of a third party makes the TLS implementation. HTTPS is a combination of HTTP and SSL for safe announcement among the web browser and web server. SSH are used for secure distant logon. It runs on the top of the transport layer protocol.
IPSec (Internet Protocol Security) is a protocol developed by the Internet Engineering Task Force (IETF) is a substantiation and encryption protocol mainly developed to address the security of IP base networks. It has a very multifaceted protocols included in RFC2401 and 2411. It was designed for IPv6 but implemented successfully in IPV4. It offers services like access control, connectionless truthfulness, secrecy, verification, Replay protection. These objectives of IPSec protocol was obtained by isolating the protocol into two Authentication Header (AH) and Encapsulation Security Payload (ESP) protocols. AH protocol looks after the substantiation and data reliability while the ESP provides substantiation, data reliability and confidentiality. A packets send from a source should contain either AH or ESP
VPN (Virtual Private Networks) construct use of the public telecommunication infrastructure by including safety procedures in the communication channels. Tunneling is used for encryption. The two types of VPN are remote access and site-to-site. In remote access it supports only user to connect to the protected network of the company while the site-to-site supports two protected company networks. It grants expensive leased lines and lower cost by sharing the public infrastructure. The two components of VPN are terminators and tunnel. Terminators are either software or hardware used for encryption, decryption and authentication. Tunnel connects end-points for safe communication between the end points in the network. Tunnels are virtually created end-points.
Conclusion
In this study an understanding about digital communication and how data are transferred in the digital communication is reviewed. Different protocols used for secure transmission of data over the channel is reviewed and a simulation of TCP/IP and TCP/IP with IPSec is done using the MATLAB and the results are discussed which shows that TCP/IP with IPSec has more delay, more packet drop, move overhead when compared with TCP/IP since it uses many security mechanism the message with security issues are dropped.
References
Viterbi, A. J., & Omura, J. K. ,2013. Principles of digital communication and coding. Courier Corporation.
Shannon, C. E. ,2001. A mathematical theory of communication. ACM SIGMOBILE Mobile Computing and Communications Review, 5(1), 3-55
Mohammad Tanveer Khan, ,2017. Review: Network Security Mechanisms and Cryptography, International Journal of Computer Science and Mobile Computing, Vol. 6, Issue 7 July 2017.
Somya Khidir Mohmmed Ataelmanan, Mostafa Ahmed Hassan AI ,2019. A review of threats, protocols and solutions to enhance the security of wireless networks, International Journal of Computer Science and Network Security, Vol.10 No.4 April 2019.
Pareek, Shilpa & Gautam, Ashutosh & Dey, Ratul. ,2017. Different Type Network Security Threats and Solutions, A Review. IPASJ International Journal of Computer Science (IIJCS) ISSN 2321-5992. 5. 001-010.
Pravin D. Hatwar,2019. A Review on Network Security Protocols, Journal of Analysis and Computation, International conference on Knowledge Discovery in Science and Technology 2019.
Know more about UniqueSubmission’s other writing services:

