CIS102-6 Information Governance and Compliance Assignment
INFORMATION GOVERNANCE FRAMEWORK
1. Introduction
Information governance mainly describes the holistic approach for managing the individual information by executing processes, metrics and roles to transfer information into a business asset. The main purpose of the information governance framework is to establish the organization approach for high-quality corporate governance. This is the structured way to handle the individual information of the organization which helps to keep the confidentiality of the accounting and financial record. In most of the organization, information can be governed with the help of different key principles including integrity, transparency, disposition, retention and availability.
There are several major components of information governance framework such as oversight responsibilities, talent and culture, the infrastructure of the organization. Information governance is the main responsibility of the individual employee of the organization. There is a need to keep the information of the employees secure for maintaining the proper framework. In this study, the famous retail organization Tesco has been selected for analysing the portfolio of information governance framework which will higher the organizational performance. The study aims to portray the different components of the information governance framework and outline the information security management system.
2. Information Governance Framework
2.1 Scope of Governance Framework
The information governance framework will be applied to the whole organization Tesco to manage the information assets in a regulatory, business and legal context. The information governance framework mainly describes the following key aspect of the organization:
- The broad environment of Tesco in where the information is managed and created.
- The business drivers and factors can help to manage the information for the need for compliance, regulations, business needs and legislations (Dong and Keshavjee, 2016)
- An overreaching demonstration of how the information is governed including the assurance of senior management endorsement.
For the implementation of an effective information governance framework, there is a need to elaborate on the concept of 4P’s of governance including people, policies, procedures and processes.
- People: For the execution of the information governance framework, people of the organization come first on the individual side of the business equation. In the opinion of Haynes (2016), people include the founder, the key stakeholders, the existing and potential customers of Tesco. The main key stakeholder of Tesco who will be associated with the execution of the information governance framework comprises BlackRock, Norges Bank Investment, the Vanguard Group.
- Policies: There is a certain policy or purpose for the development of an information governance framework in the business organization Tesco. As per the views of Evans et al, (2019), the main purpose of executing the information governance framework in Tesco for setting proper rules and regulation for managing the important assets of the organization. The policy may include a data privacy policy and the information security policy for the development business.
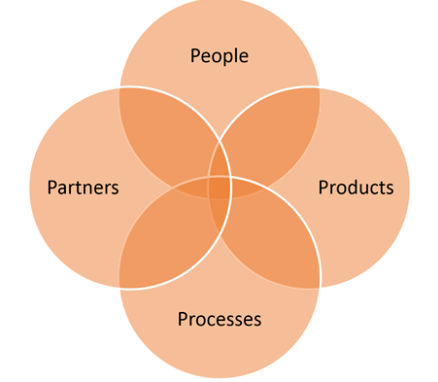
Figure 1: 4P’s of Information Governance
(Source: Evans et al, 2019)
- Procedures: The main procedure for implementing the information governance framework includes defining all the information assets of the organization Tesco, defining the owner of the information asset and also needs to explain the security policy and strategy for information assets. In the views of Shu and Jahankhani, (2017), the procedures include managing the volume of information, creating and receiving information, Storing and archiving information and collaboration and sharing of information.
- Processes: Governance is the standalone process by which the important key stakeholder of the business organization achieves the organizational purpose. The process has been developed by analysing the performance of Tesco. As opined by Olaitan et al, (2016), the processes include mitigating the information risk and the proper development of the security protocol, disaster recovery and contingency and business continuity.
2.2 Outline of the information governance committee
The information governance committee is responsible for all the important matters of information ranging from the strategy, infrastructure, metadata, compliance and the standard privacy of the organization Tesco. As commented by Khalil and Belitski (2020), the committee member must include the senior managers of the organization Tesco those are a responsible legal business, information management, privacy and the implementation of information communication technology development. The higher management of Tesco include head of information compliance, director of IT, head of governance and secretary will be established by a board who will work in a group and responsible for the all the important functionalities of the organization. In the opinion of Khalil and Belitski (2020), the committee members also include the senior officers and the information technologist who directly report to the head of the board for making the strategic planning of managing the information matters in a more holistic approach.
2.3 Responsibility for the information governance team
The information governance team are responsible for mitigating the operational oversight of the framework, review its implementation and ensure all the records are kept properly. The responsibilities of the information governance team are listed below:
- Review the effectiveness and establish the proper information governance framework with maintaining the proper security policies of the business organization Tesco. In the opinion of Merkus et al, (2019), the security policies may include the Tesco CCTV system, the data controller policy, the use of cookie services and the just-in-time mobile applications.
- There is a need to meet the risk of the operation which will be oriented with the implementation of information governance framework related to a data breach, data corruption and data loss of the existing potential customers who are the key stakeholders of business (Moghadam and Colomo-Palacios, 2018).
- The committee team members need to focus on the strategic resource allocation technique for emphasizing information management and also notice the cost and benefit after properly implementing the framework.
- There is a need to ensure for keeping the individual information asset safe and secure with the help of the information management work plan. As argued by Haynes (2016), the technical team and the higher management needs to perform the adoption of information security management systems for higher productivity of the business.
- The committee members need to focus on the coordination of information review which can identify the important business assets of Tesco including the confidential information of their customers, vital information of their business policies, rules and regulations.
- There is a need to monitor the information infrastructure for the development of the business and also focus on the interdepartmental liaisoning which enhances to meet the operational oversight of the framework (Lomas et al, 2019).
- The governance team members need to focus on the implementation of the information standard which may include business system functionality, interoperability capabilities and metadata operation of the business organization Tesco.
- The business committee needs to maintain the organizational trends, norms and guidelines for the development of an information governance framework. In the opinion of Yebenes and Zorrilla (2019), the guidelines can include all the information that has been created by the organization is ready for reuse, and it is interoperable across the commonwealth. The guideline also ensures that all the information is discoverable and supports the accountability, good decision-making approach of the business organization.
2.4 Relevant information policies
Information Security Policy
As per the government of the United Kingdom, there is a need to focus on the following information security policies before the implementation of the information governance framework:
- Data Protection Act: The government of the UK has been focused on the data protection act (2018) for keeping the information more integrated and authenticated for the business organization. As per the data protection act, the business organization is advised not to send important information via e-mail unless the internet connection is secure or encrypted (uk, 2020). The data protection act also stated to keep the banking details and the social security number of the individual secure for reducing the incident or occurrence of a data breach or data loss. The business needs to focus on the business asset clarification schemas.
- DMCA Policy: Digital millennium copyright act of the UK of 1998 helps to protect the software, individual business program of the business organization Tesco. This law has been integrated by the DMCA violation where the organization has taken the prior action for facilitating the information and security (uk, 2020). The DMCA policy is going to be invoked in the information governance framework to process the actual knowledge of the business.
Record Management Policy
The record management policy of the United Kingdom mainly establishes a framework for the implementation of the business and ensures the full accurate record of the business. As mentioned by Adams and Bennett, (2018), the record management policy can be defined to maintain the system more effectively and clarified. There is a need to demonstrate the structure and movement of the information asset of the organization for the specific elaboration of the governance. As per the record management policy of the United Kingdom, there is a need to follow the steps as per the government of the United Kingdom,
- A complete inventory of all the records: The information governance team needs to complete inventory for all of the records of the information asset and process the business and data management in a proper way (Silva and Soares, 2018).
- Responsible person for managing the Record: The committee team members need to focus on the processing and managing of the information for achieving the organizational goal and objectives.
- Develop record retention and destruction schedule: The record retention program helps to review, destroy, retention of the records for maintaining the regular business activities. This guideline helps to maintain, authenticate and integrate records and eliminate the overall business risk (Nicho, 2018).
- Best Way to manage records: The best way to maintain the information management system is the implementation of a proper strategic approach of business and also ensures secure off-site records storage to manage the important business papers.
- Create and document proper procedures: The record management policy also ensures the documentation of the effective and authentic business procedures which helps to deliver an activated information governance framework. In the opinion of Gashgari et al, (2017), this also enhances the organization to eliminate the management mistakes for effective record management.
- Training and Implementation: After the implementation of the innovative information governance framework there will be a need to train the employees for giving their proper knowledge and wisdom about the business activities.
- Managing and auditing the Program: In this section, the implementation of an information governance framework encourages to audit and manage programs which influences the high scalability of the business organization Tesco (Mantra, 2016).
2.5 Overview of information procedures
Legal Compliance: Legal compliance is the procedures to ensure the organizational laws, business regulations and business rules. The organization Tesco has maintained all the necessary legal compliance that may encourage the organization for making an effective information governance framework. In the opinion of Asadi et al, (2019), the organization has implemented effective policies of using the intranet for the specific use of the employees. The employees of Tesco need to maintain proprietary and confidential information for the specific business purpose. The organization has also maintained fair dealing, business and gratuities courtesies and fair business trading. As per antitrust law, 2015, the organization violates the practice of price-fixing, bid-rigging, group boycotts and market allocation of customers. In the opinion of Zaydi, M. and Nassereddine (2018), according to the Foreign Public Officials Act, 2019, the business organization Tesco needs to highlight on diminishing the activities of corruption and anti-bribery facilitation. This framework aims to furnish Anti-Money Laundering Policy and product integrity to assure reliability, safety and quality.
Regulatory Compliance: The regulatory compliance mainly describes the organizational goal and to ensure the efforts for compiling the relevant policies, laws and regulations. This compliance mainly follows the state, international, federal laws that are relevant to the business organizations Tesco. As mentioned by Bennett (2019), the executive management team of Tesco is going to facilitate the business code of ethics around the world which encourages to protect employee’s personal information with the application of UK data protection act, 2018. The audit committee of the organization Tesco will monitor the governance framework for the enforcement of whistleblowing activity in the organization itself. The organization Tesco must follow all the important business implications and the regulatory compliance for the successful development of an information governance framework.
2.6 Overview of how the third party will be managed
The third-party management in information governance framework mainly refers to the process where the organization manages and monitors all the business interaction with all the internal and external parties. In the opinion of Dong and Keshavjee (2016), this includes both the non-contractual and contractual parties of Tesco who are responsible for the development of an information governance framework. The third-party management needs to undergo the following steps:
- Manage and assess third-party risk.
- Conduct Third-party screening, due diligence and on boarding.
- Focus on the information technology vendor risk.
- Ensure appropriate staffing and investment (Haynes, 2016).
- Leverage technology implementation.
2.7 Risk assessment technique for information governance and security
| Type of Risk | Likelihood | Impact on the Governance Framework | Mitigation Strategies |
| Information Management | High | Severe | Effective implementation of enterprise content management systems. |
| eDiscovery | Medium | Moderate | Strategic execution of information governance framework. |
| Regulatory Compliance | High | Severe | The electronic communication system to archive the enterprise information solution. |
| Security and Privacy | High | Severe | The implementation of SOX, FINRA, HIPAA regulation for making important data more authentic and confidential. |
| Storage Management | Low | Minimum | The development of information management automation helps to reduce the volume and storage cost of the data. |
| Defensible Disposition | Medium | Moderate | There is a need to up-to-date the document and effectively implement the defensible disposal of information for reducing the overall business risk. |
| Productivity | Medium | Moderate | Good practice of information governance for increasing business productivity. |
Table 1: Risk Assessment Policy
(Source: Haynes 2016)
2.8 Business continuity plan
A business continuity plan is a structured process of creating an individual system and processes for recovery and prevention to deal with the possible and potential business threats. The continuity plan forecast on the five individual key components which are discussed below:
- Analysis: The business continuity plan needs to analyse the unforeseen circumstances of business which may disrupt the overall growth and productivity. In the opinion of Evans et al, (2019), the risk may include financial, resource capabilities, security and fraud risk, operational risk, compliances risk of Tesco. The individual committee members of information governance framework need to focus on the individual aspect of the risk.
- Solution Design: The committee member needs to mitigate the suitable business risk by effective strategic solutions that help to recover the challenges of the business. The strategic solution may include enterprise content management system implementation, development of security policies (Shu and Jahankhani, 2017).
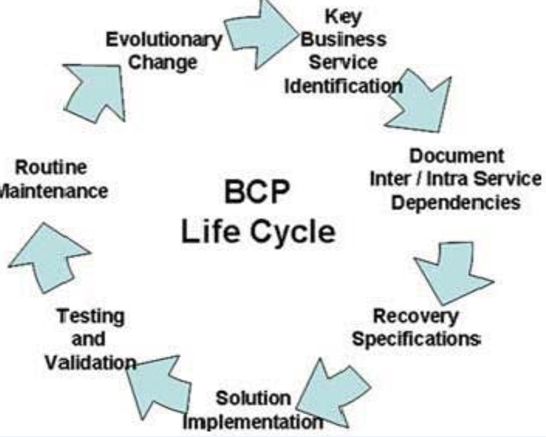
Figure 2: Business Continuity Plan
(Source: Shu and Jahankhani, 2017)
- Testing and acceptance: After the testing of the individual risk and the implementation of the mitigation practice, the broad members of the information governance framework need to accept the business protocols.
- Maintenance: The maintenance of the business risk includes all the affirmative activities where the consistency of the business needs to be maintained and the individual business professionals highlight the business goals.
Key Stakeholder Role
The key stakeholder’s role in the formation of the information governance framework is stated below:
- The individual stakeholder needs to maintain and delegate the task of the implementation of the information governance framework and analyse the risk.
- The stakeholders need to ensure a proper continuity plan and recovery plan for effectively maintaining the framework.
- Stakeholders need to focus on the daily activities and how to maintain the important information asset of business regarding the information governance framework (Olaitan et al, 2016)
2.9 Recovery plan
The disaster recovery business plan includes the four major criteria such as information technology recovery processes, alternative site, data backup and offsite replication and storage facility. In the opinion of Khalil and Belitski, (2020), the technical team of the information governance framework needs to focus on the damage of the system and maintain the proper strategic approach which is discussed below:
- There is a need to secure the hardware of the information system including network, wireless devices and peripherals and also maintain the different software applications including electronic data interchange, enterprise resource management.
- For the data recovery plan, the organization Tesco must focus on the ISO-27000 standard which comprises information security by the joint compilation of International Electro Technical Commission and International Organization for Standardization (Merkus et al, 2019).
- There is a need to focus on the restoration of data which may include the recovery of the authenticate and integrate information on the relevant business activities.
- The internal recovery strategies may include the proper configuration of hardware and software
- The vendor supported recovery strategy helps to assess the business disaster mainly in the IT framework. Moreover, the information governance framework focuses on the data backup plan and utilises the appropriate information management for the technical system (Moghadam and Colomo-Palacios, 2018).
- The IT team needs to be more proficient and competent to manage all the disasters that have been slowing the system and reduce the growth and overall productivity.
3. Outline for an Information Security Management System (ISMS)
The Information Security Management System or ISMS is a standard process for protecting the information assets of an organization and preserving its confidentiality from third parties. In the business world, one of the major issues of corporations is the theft of information or a breach in security. These activities have resulted in the loss of millions of dollars for business enterprises, therefore, strict actions are needed to formulate plans for protecting the information. The information of an organization has four primary pieces of information that include operational value, individual value, value to others, and societal value. Tesco is one of the leading retail firms in the UK and has a gross yearly revenue of 6391.1 crore GBP (Tescoplc.com, 2020). Such a high-level self-sustainable organization is susceptible to inherent risks and breach of security. Therefore, it is highly essential for the management to incorporate the ISMS framework and reduce such risks as much as possible.
Information Security Components
The information security components of the organisation can be assimilated into five principal groups.
- Organization and infrastructural security– Tesco will engage in critical thinking so that the infrastructure of Tesco can be immune from cyber threats and attacks. As mentioned by Al-Dhahri, Al-Sarti and Abdul (2017) third-party screening, due diligence and on boarding teams will be divided so that any targeted attacks on information can be identified and preventive measures can be taken immediately.
- Standards, procedures and policy security– Information security policies of the organisation needs to be high-level planning that can portray the goals of the procedures followed by the company.
- Risk assessment security– Tesco will need to develop a team that spots and identifies the vulnerabilities of the organization within its framework. The aim is to recognize the threats and build up control measures against it.
- Training program and awareness security– This process will help to educate the employees of Tesco about computer threats and risks. As argued by Soomro, Shah and Ahmed (2016) the training regime will teach the employees about the processes that are mandatory when encountering a threat in the system.
- Compliance security– The ISO standard of 27001 provides the best protection against information leakage and thefts. Therefore, Tesco will need to strengthen their barriers to standard’s opinion for enhanced protection and elimination of threats.
Information Security incidents
Vulnerabilities and threats in the system are the two major concepts that align with information security incidents. Tesco has high-security adoption and regulation, yet fell victim to a cyber-attack in 2016. As per Zammani and Razali (2016) the event was observed as a black day for the company as Tesco’s financial information of the debit card holders were targeted by cybercriminals. Above 8261 customer’s information and financial credential was stolen that amounted to about £2.26 million (Tescoplc.com, 2020). Tesco was fined for £16 million by the FCA for the lack of security. The incident shook the very foundation of the organization and influenced the company CEO to adhere to strict principles and policy of ISMS. Therefore, the need for ISMS implementation and business continuity planning for the organization holds profound importance to bounce back in the market. Implementing the vendor-supported recovery strategy will also help the organization to gain back customer trust.
Information Security Management System Components
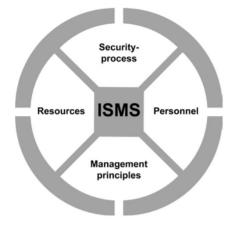
Figure 3: ISMS components
(Source: Haufe et al., 2016)
The components involved in ISMS are:
- Management principles– A breach in an organization can cause millions of money theft and fines. Therefore, as argued by Haufe et al. (2016) it is smart to invest in ISMS to prevent such risks. Tesco, having faced one of the breaches in recent years needs to develop an effective ISMS in the corporate governance framework. Organizations like Tesco can use management tools and techniques are essential components of ISMS to establish a solid viewpoint of process implementation.
- Resources– The human and financial resources play an integral part of security management. The HRM faculties of Tesco should focus on hiring employees for managing the financial resources in a better and secured way.
- Personnel– This involves the audit team, ISN team, employees, third parties, resource planning team, risk management team. As per Cockcroft (2020) the business continuity management plan needs to revolve around these teams to contribute to the success of ISM operations.
- Information security process– IS process is the protection of information from unauthorized access and modification. Organizations such as Tesco must use the IS processes to identify and define the security controls and thereby protect the assets of the organization.
Information Security Management System Domains
The areas of ISMS standard comprises 11 security areas that involve bundles of control objectives in the list. The categorisation of the ISMS domains can be stated as:
| Domains | Objective |
| Security policy | The security domain provides support and backup to reduce risks of information breach |
| Organizational Security | Organizational security is responsible for managing security within the organizational framework. |
| Information System Acquisition | This domain helps to develop and maintain the security of information systems |
| Asset Management | The organizational assets are held in the capable hands of asset management. |
| Access Control | A team is separately allocated to provide access to the piece of information and prevent unauthorized entry. |
| Communications and Operations Management | Handling of operations and creating effective communication channels for sharing information within the organizational framework. |
| Physical and Environmental Security | Makes sure that the legal and environmental standard and regulatory compliance is fulfilled. |
| Information Security Incident Management | Tracks down the incidents and issues occurring in information system securities and prepares action plans to solve it. |
| Human Resources | Training programmes and employee performance appraisal is a necessary task to keep them ready for security incidents. |
| Compliance | Maintain the regulatory standards and avoid violation of rules and regulations to protect information from breaches. |
| Business Continuity Management | Maintenance of major and minor issues within the organizational framework. |
Table 2: Domains of Information Security Management System
ISO/IEC 27001
The ISO standards were first published in the year 1987, after which there were several reforms and amends. According to Logan (2020) the ISO/IEC 27001 standard was established in order to protect the organizations from cyberbullies and thefts. The standard introduced Demming’s PDCA model to plan, implement, control and monitor the effectiveness of ISMS functions in an organization. Big organizations such as Tesco need to adhere to the principles of ISO standard to remain vigilant in the market. The PDCA model established in the ISO/IEC 27001 standard will help to form proper security policies and regulations for improving organizational security and reducing threats and vulnerabilities. As argued by Hasbini, Eldabi and Aldallal (2018) the security policies will be implemented and controlled by the personnel of the organization itself so that continuous improvement of the ISMS process can be acquired.
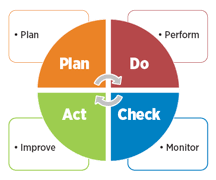
Figure 4: PDCA model
(Source: Logan, 2020)
There is no effective way to grant 100% security from cyber-attacks, however, the ISO 27000 family is certified to enhance the performance of the ISMS framework and reduce possible threats. As commented by Lampe et al. (2020) starting from ISO 27001 and ISO 27002, the published standards will be a great help for Tesco to come back from the security breach incident and operate again.
Benefits of ISO27001
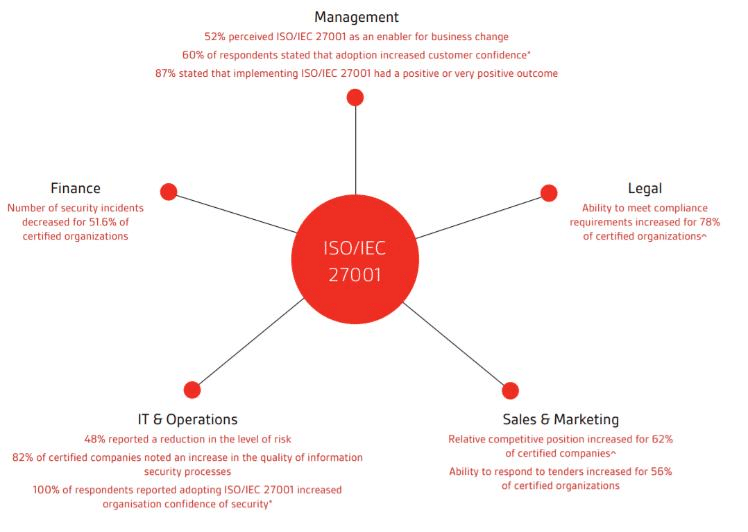
Figure 5: Benefit of ISO27001
(Source: Kauspadiene et al., 2017)
There are cumbersome benefits of ISO27001 standard but the greatest one is maintaining the requirements of ISMS (Kauspadiene et al., 2017). The other importance and benefits of the standard can be grouped as:
- Increase in business efficiency
- Reduction of operational and functional risks
- Assurance to information system security
- Marked certification to organizations following this standard
- Awareness of security threat and vulnerabilities among the members of an organization
- Elimination of risks
- Better decision-making abilities
- Encouragement to carry out business operations smoothly
Information Security Management System Framework
ISMS is an integral part of business management and security systems involving protection against cyber thefts, hacks and breaches. It is necessary for organizations to understand the framework of ISMS before implementing it. Tesco will be able to implement the ISMS framework as business continuity planning is under progress. According to Cockcroft (2020) the security policy, the scope of ISMS, risk management, monitoring and control, risk assessment, and application will be core elements of the framework. Tesco will need to adhere to the guidelines of security policies to resolve the issues of threat and vulnerabilities in their system. Implementing appropriate control methods will encourage the very foundation of the organization to engage in safe information transfer.
Information Security Management System Challenges
Although the ISMS standards introduces several mitigation steps and action plans to prevent risks in the system, still challenges can be present around the corner of ISMS. The main challenges that can be faced by the organization in this respect can be categorized as:
- Structural and boundary challenges– The current business environment is based on volatile and uncertainty factors. The information system and its security faces a lot of new challenges and threats from the environment and society. Moreover, as argued by Zammani and Razali (2016) the topographical and physical entities also possess immeasurable risks to the organization.
- Human challenges– Although Tesco has a reliable field of agents that works hard to maintain security standards, yet it should be noted that cybercriminals spend more time hacking. The difference in experience and skill is a critical factor when countering security breach.
- Organizational challenges– Tesco will need to identify the social and organizational values to enhance the security system.
Recommendation
Tesco will need to invest heavily after their breach to protect the information of the company assets and prevent any leakage. Moreover, the company needs to identify the structural and boundary elements in the organization in order to grasp the knowledge of threats and vulnerabilities. As commented by Haufe et al. (2016) knowing the areas that have weaker security than others can help the teams to identify the location of risk early. Nevertheless, the organization must implement SOX, FINRA, HIPAA regulation for making important data more authentic and confidential. An organizational change is a critical factor to reduce human elements and organizational challenges from affecting Tesco framework.
4. Conclusion
It can be concluded from the study that the main focus is on the implementation of an information governance framework in the business organization Tesco. The study also highlights the different key components of information governance framework including the scope of the governance framework which describes the 4P’s of corporate governance. The study also concerns the committee development for an information governance framework which helps to assess the key responsibilities and mitigating all types of risks. The study also depicts the role and responsibility of the different key stakeholders of Tesco and how they mitigate the operations management of information governance.
The study also forecasts the relevant policy regarding information security and recover management policy which enhances business performance. The study also highlights legal and regulatory compliance for the growth and increasing business opportunities. The main focus is on the third party management and potential risk assessment strategies which mainly influence the organization in a positive direction. The report also ensures the business continuity plan and the disaster recovery plan which mitigate all the technical in capabilities and damages. The implementation of the information management system helps to improve the security policies and the management policies.
Reference list
Adams, M.A. and Bennett, S., 2018. Corporate governance in the digital economy: The critical importance of information governance. Governance Directions, 70(10), p.631.
Al-Dhahri, S., Al-Sarti, M. and Abdul, A., 2017. Information Security Management System. International Journal of Computer Applications, 158(7), pp.29-33.
Asadi, F., Rouzbahani, F., Rabiei, R., Moghaddasi, H. and Emami, H., 2019. Information Governance Program: A Review of Applications in Healthcare. Archives of Advances in Biosciences, 10(1), pp.47-55.
Bennett, S., 2019. Governance in practice: Big data, privacy and information governance-incorporating an ethical-based assessment. Governance Directions, 71(5), p.244.
Cockcroft, S., 2020. Securing the commercial Internet: Lessons learned in developing a postgraduate course in information security management. Journal of Information Systems Education, 13(3), p.7.
Dong, L. and Keshavjee, K., 2016. Why is information governance important for electronic healthcare systems? A Canadian experience. Journal of Advances in Humanities and Social Sciences, 2(5), pp.250-260.
Evans, J., McKemmish, S. and Rolan, G., 2019. Participatory information governance. Records Management Journal.
Gashgari, G., Walters, R.J. and Wills, G., 2017, April. A Proposed Best-practice Framework for Information Security Governance. In IoTBDS (pp. 295-301).
gov.uk, 2020, Regulatory Act, Available at: www.gov.uk [Accessed on: 7th July 2020]
Hasbini, M.A., Eldabi, T. and Aldallal, A., 2018. Investigating the information security management role in smart city organisations. World Journal of Entrepreneurship, Management and Sustainable Development.
Haufe, K., Colomo-Palacios, R., Dzombeta, S., Brandis, K. and Stantchev, V., 2016. Security management standards: a mapping. Procedia Computer Science, 100(100), pp.755-761.
Haynes, D., 2016. Social media, risk and information governance. Business Information Review, 33(2), pp.90-93.
Kauspadiene, L., Cenys, A., Goranin, N., Tjoa, S. and Ramanauskaite, S., 2017. High-level self-sustaining information security management framework. Baltic Journal of Modern Computing, 5(1), p.107.
Khalil, S. and Belitski, M., 2020. Dynamic capabilities for firm performance under the information technology governance framework. European Business Review.
Lampe, G.S., Maftei, M., Surugiu, I. and Ionescu, R.C., 2020. Study on information security management system and business continuity management in the context of the global crisis. New Trends in Sustainable Business and Consumption, p.942.
Logan, P.Y., 2020. Crafting an undergraduate information security emphasis within information technology. Journal of Information Systems Education, 13(3), p.3.
Lomas, E., Makhlouf Shabou, B. and Grazhenskaya, A., 2019. Information governance and ethics–information opportunities and challenges in a shifting world: setting the scene. Records Management Journal, 29(1/2), pp.2-4.
Mantra, I.G.N., 2016. The Modeling of Information Security Classification With Risk Value Assesment Factor to Good Information Governance on The Indonesia Higher Education Sector. JATISI (Jurnal Teknik Informatika dan Sistem Informasi), 3(1), pp.12-22.
Merkus, J., Helms, R. and Kusters, R.J., 2019, May. Data Governance and Information Governance: Set of Definitions in Relation to Data and Information as Part of DIKW. In ICEIS (2) (pp. 143-154).
Moghadam, R.S. and Colomo-Palacios, R., 2018. Information security governance in big data environments: A systematic mapping. Procedia computer science, 138, pp.401-408.
Nicho, M., 2018. A process model for implementing information systems security governance. Information and computer security, 26(1).
Olaitan, O., Herselman, M. and Wayi, N., 2016. Taxonomy of literature to justify data governance as a pre-requisite for information governance.
Shu, I.N. and Jahankhani, H., 2017, November. The Impact of the new European General Data Protection Regulation (GDPR) on the Information Governance Toolkit in Health and Social care with special reference to Primary care in England. In 2017 Cybersecurity and Cyberforensics Conference (CCC) (pp. 31-37). IEEE.
Silva, E. and Soares, B.H., 2018, June. Governance and management of organizations with cloud supported services recommendations for risks of information security. In 2018 13th Iberian Conference on Information Systems and Technologies (CISTI) (pp. 1-8). IEEE.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more holistic approach: A literature review. International Journal of Information Management, 36(2), pp.215-225.
Tescoplc.com, 2020. About us. Available at: https://www.tescoplc.com/ [Accessed on 3rd July 2020]
Yebenes, J. and Zorrilla, M., 2019. Towards a Data Governance Framework for Third Generation Platforms. Procedia Computer Science, 151, pp.614-621.
Zammani, M. and Razali, R., 2016. An empirical study of information security management success factors. International Journal on Advanced Science, Engineering and Information Technology, 6(6), pp.904-913.
Zaydi, M. and Nassereddine, B., 2018. Construction of the First Component of a New Information System Security Governance Framework: 4D-ISS Risk Management Model. In Proceedings of the World Congress on Engineering and Computer Science (Vol. 2).
Know more about UniqueSubmission’s other writing services:

