MN502 Lightweight Cryptography Assignment Sample
Here’s the best sample of MN502 Lightweight Cryptography Assignment, written by the expert.
Introduction
Conventional Cryptographic technologies are advanced technologies that have improved the technological aspects as well as also increase their security level. But at the same time, the shift from desktop to small devices has brought several security and privacy concerns. It is difficult to implement the conventional cryptographic standards to small devices due to constrained environments. In such conditions, the performance of these technologies is not acceptable. The “Lightweight Cryptography (LWC)” is also based on the cryptographic algorithm or protocol that is designed for executing in restricted environments including countless smart cards, the Internet of Things (IoT), cyber-physical systems, and the smart grid, health-care devices, sensors, industrial controllers, and RFID tags (Bilgin et al., 2013). It is because the majority of the current cryptographic algorithms are designed for the desktop or server environments, but they are not suitable into the constrained resources. This has specific lightweight properties that are based on the chip size and energy consumption. It is superior to the conventional cryptographic ones that are used for the internet security protocols. This technology has the goal to provide adequate security and does not exploit the security-efficiency trade-offs. It provides the cryptographic solutions that need to maintain the resource vs. security constraint. It is also efficient of end-to-end communication for providing the end-to-end security without consuming more energy. It requires low energy for the end devices (Andrés et al., 2016). The goal of lightweight cryptography is to provide security to smart objects networks due to its smaller footprint and efficiency. This technology is based on the conventional cryptography standards that are applied to the constrained resource devices and fulfill the limitations of the target devices.
Another goal of lightweight cryptography is to trade-off between lightweightness and security as it allows for achieving a high level of security by using only small computing power. Some examples of this technology are lightweight stream ciphers, block ciphers, hashfunction and one-pass authenticated encryption. All these technologies are effective to trade off the execution cost, speed, security, performance, and energy consumption on resource-limited devices (Kumar et al., 2012). It is because these technologies utilize less memory, fewer resources, and less power supply to achieve high security over the resource-limited devices.
The potential security threats in systems using low-power devices
The system using low-power devices cause the potential security threats as they are based on limited energy, memory and processing resources that raise the need for security services during the design phase. These systems with low energy devices have several constraints related to energy availability like RFID tags, NFC tags, smart cards, wireless sensors, etc. However, these devices need to be secured by the cryptography by achieving fast identification, authentication and data protection. However, these devices provide advantages in the form of designing and applicability but also create unique security challenges (Yang et al., 2015). These devices have limited energy use and storage capacity as compared to large systems. For instance, a laptop utilizes 60 watts of power whereas Smartphone uses 5-12 watts of power; a wireless sensor requires 1 milliwatt of energy. Apart from this, RFID tags require only 1–10 microwatt of energy. All these low energy devices are constrained to apply the conventional cryptographic technologies to address the power constraints and increase the performance. It is because all these devices are not suitable for real-world activities (Mouha et al., 2015). In addition, limited energy storage in these devices causes a finite amount of runtime available to complete all operations that makes it difficult to utilize the resources for running a protocol. Apart from this, these devices have limited memory in the form of RAM and ROM that may also cause security challenge. Some devices such as fitness trackers, smart lighting, smart watches, etc. are designed to meet the marketing or engineering requirements, but these devices have limited memory that is insufficient for the cryptography causing security issues (McKay et al., 2017). The cryptography technologies are not applicable to these devices due to having limited memory.
The working mechanism of lightweight cryptography
The working mechanism of lightweight cryptography is based on the encryption process. It means this technology works on the application of the encryption to devices by executing the data protection for confidentiality and integrity (See: Figure 1). Such a mechanism is effective to countermeasure the security risk.
Figure 1: Application of lightweight cryptography
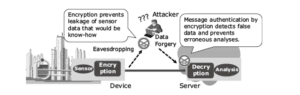
This technology enables the application of secure encryption even for the devices that are with limited resources. Encryption is applicable as standard on the data link layer of systems (Kerckhof et al., 2012). In this, encryption in the application layer is significant to provide end-to-end data protection from the device to the server and offer high security (See: Figure. 2).
Figure 2: the Encryption process
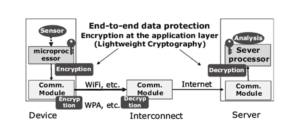
This encryption includes the initial XOR operation and matrix transformations to shuffle the data. The data blocks go through seven rounds of encryption by using a unique 144-bit key for each round. This scheme is effective to protect the data block by consuming less processing power. A device-id and user-supplied password are used to derive the key with the help of unique hardware identification (Manifavas et al., 2014). The use of two sources of input for deriving the key is significant to limit the chance of obtaining the full credentials for decryption of the data and provide security to the collected and stored data.
Performance metrics (Hardware-specific metrics and Software-specific metrics)
Hardware-specific metrics
In the implementation of light-weight cryptography, the hardware design is based on the reduction of the logic gates that are needed to materialize the cipher. This explains the gate area of implementation depending on the technology and standard cell library measured in µm2. This metric is referred as Gate Equivalent (GE). It is the area that is needed by the two-input NAND gate. Small GE indicates the low cost and low consumption of power by the circuit. For the constrained resource devices, 3000 GE is acceptable while for the smaller devices like controllers, 1000GE is sufficient. For instance, a low-cost RFID tag requires 1000 to 10000 gates out of which 200-2000 gates are available for the security aspects (Beaulieu et al., 2015). At the same time, the energy consumption and power constraints are considerable aspects. Energy consumption metric is significant in the device which is operated on batteries while power constraints are considerable for the passive devices like RFID tags that need to be connected to a host device for operation. At the same time, in hardware designing for the lightweight cryptography, the security attacks, and relevant countermeasures are also considered as performance metrics because these measures are associated to the power analysis (Singh et al., 2017). The area need and power consumption are related to each other as the reduction in area may be helpful to minimize the power consumption.
Software-specific metrics
Software requirements need the only microprocessor for operation. So, the design of lightweight cryptography is based on the reduction of memory and processing requirements. In relation to software applications, the number of registers and the number of bytes of RAM and ROM can be used to measure the resource requirements. The small number of registers causes the low overhead. ROM is useful for the storage of the program code while RAM is preferred for the storage of intermediate values used in computations. It provides extra tradeoffs between calculating values. The optimization of software requirements can be possible by using metrics like throughput and power savings (McKay et al., 2017). Throughput is the rate at which new outputs are generated. There is a need to consider low throughput in designing of the lightweight cryptography. However, there is a need to consider moderate throughput in most applications.
Current and Future challenges in lightweight cryptography
However, the lightweight cryptography is valuable in protecting the systems, but at the same time, there are several challenges in its implementation. This technology is not fully developed yet even several studies are being conducted. The standardization of this technology is under research as it is challenging to get full advantages of this technology. Realization of encryption algorithms can be disadvantageous to reveal side-channel information that may cause security issues. At the same time, it is also challenging to develop awareness among the users as there is need to provide training to the users that may increase the cost of implementation of this technology (Buchanan, Li, and Asif, 2017). In addition, encryption-based technology needs an exchange of private keys that need to be completed securely. Besides, it is also challenging to secure the data as the number of participants in a transaction increases; it also causes risks because one extra user adds limitation because an attacker can take advantage of it. Along with this, the standards of the lightweight cryptography are vulnerable to tag and reader impersonation attacks and allows tag traceability. Even, this is also expensive due to the complexity of hardware involved as it is required to conduct research t reduce the cost of the hardware. This technology is faster and cheap, but they can be vulnerable to security problems on incorrect implementation (Usman et al., 2017). In future, it will be challenging for the implementation of this technology because there is a need to make continuous improvement in this technology due to the dynamic nature of security aspects and emergence of new technologies. Further researches can contribute to the development of this technology.
Summary
From the above discussion, it can be concluded that lightweight cryptography is better as compared to Conventional Cryptographic technologies due to the cost-effectiveness, efficiency, and low energy consumption. This technology is useful even for the low energy devices that operate in constrained resource environments. Apart from this, it can also be summarized from this report that system using low-power devices are vulnerable to security issues because of limited energy, memory and processing resources. Limited energy use and storage capacity are major concerns of these systems that make them vulnerable to security issues. These issues create the need for adopting the lightweight cryptography technology that can be significant to address the related issues of these systems. At the same time, lightweight cryptography technology works based on encryption that provides the security to devices with constrained resource environments. From this, it can also be summarized that hardware-specific metrics for the lightweight cryptography is gate area, costs, consumption of power and security attacks; whereas software-specific metrics are memory and processing requirements including the number of registers that are used to measure the performance of the technology. However, this technology is quite useful to provide security, but it also creates challenges in terms of need for continuous improvement, impersonation attacks and revealing side-channel information.
References
Andrés, C., Morales-Sandoval M., and Díaz-Pérez A. “An evaluation of AES and present ciphers for lightweight cryptography on smartphones.” Electronics, Communications, and Computers (CONIELECOMP), 2016 International Conference on. IEEE, 2016.
Beaulieu, R., et al. “The SIMON and SPECK lightweight block ciphers.” Design Automation Conference (DAC), 2015 52nd ACM/EDAC/IEEE. IEEE, 2015.
Bilgin, B. et al. “Fides: Lightweight authenticated cipher with side-channel resistance for constrained hardware.” International Workshop on Cryptographic Hardware and Embedded Systems. Springer, Berlin, Heidelberg, 2013.
Buchanan, W.J., Li, S. and Asif, R., Lightweight cryptography methods. Journal of Cyber Security Technology, 1(3-4), 2017, 187-201.
Kerckhof, S. et al. “Towards green cryptography: a comparison of lightweight ciphers from the energy viewpoint.” International Workshop on Cryptographic Hardware and Embedded Systems. Springer, Berlin, Heidelberg, 2012.
Kumar, A., Krishna G., and Alok A. “A complete, efficient and lightweight cryptography solution for resource constraints Mobile Ad-Hoc Networks.” Parallel Distributed and Grid Computing (PDGC), 2012 2nd IEEE International Conference on. IEEE, 2012.
Manifavas, C. et al. “Lightweight cryptography for embedded systems–A comparative analysis.” Data Privacy Management and Autonomous Spontaneous Security. Springer, Berlin, Heidelberg, 2014, 333-349.
McKay, K. A., et al. Report on lightweight cryptography. US Department of Commerce, National Institute of Standards and Technology, 2017.
McKay, K.A., McKay, K.A., Bassham, L., Turan, M.S. and Mouha, N., Report on lightweight cryptography. US Department of Commerce, National Institute of Standards and Technology, 2017.
Mouha, N. “The design space of lightweight cryptography.” NIST Lightweight Cryptography Workshop 2015. 2015.
Singh, S., Sharma, P.K., Moon, S.Y. and Park, J.H., Advanced lightweight encryption algorithms for IoT devices: survey, challenges, and solutions. Journal of Ambient Intelligence and Humanized Computing, 2017, 1-18.
Yang, Y. et al. “On lightweight security enforcement in cyber-physical systems.” International Workshop on Lightweight Cryptography for Security and Privacy. Springer, Cham, 2015.
________________________________________________________________________________
Know more about UniqueSubmission’s other writing services:

