OVERVIEW OF NETWORK SECURITY ASSIGNMENT 2020
Introduction
Tere is a high use of the mobile comouting and the cloud computing for the firm that help the firms to get the competive advantage and to perform well. But at the same time, there are also different issues that are also faced by the firm.
In this, the threat of the virus and the hacking are the major isue that are also faced by the firms and created the buisness challenges for the firm.
In like manner, ransomware is also one of the major issue that affect the performane of the firm. Ransomware is malicious software that gains unauthorized access to victims that and threatens to publish or block access to that data whatever made victim to pay more ransom.
In general first it blocks the access to the data and then threatens to publish that data if ransomis not paid[1].
Almost all the areas of the society get affected by the Ransomware. In medical data medical data affected by the attack, which makes patients history, schedules of doctors, prescription details, lab order disorders or delayed.
For business, it affects the daily process of the business, threat of business information compromisation. Economical business loss when ransomis paid[2]. General population also not away from paying for Ransomware attacks.
The ransomware attacks the personal computer of the people and whether and gain access to the data, these ransomware makes that data inaccessible to the person or it threatens to dump the data over the warp that may result in the privacy compromise of that person.
This report try to explain some basic mechanism behind the Ransomware attacks, process of the attack and some famousransomware that are present. This report also contains detailed analysis of the recent WannaCry attack that happened in 2017.
Variant of ransomware
Crysis:
Itencrypt files heavily that cannot be decrypted in the reasonable amount of time. It is spread by email attachment, for avoiding detection as executable file it uses double extensions.
CryptoWall:
Itwas first detected in 2014. The most significant feature of this ransomware is to avoid detection. It uses actual digital signature to avoid detection and capable or creating fake explorer.exe and fake svchost.exe that help it in avoidingdetection into the system. the averageransom range of the cryptowall is from $700 to 1400.
It distribute by email attachment and advertising [3].
Locky:
Affectedbelongings to healthcare facilities, it is similar to cryptolocker but more advanced in its behavior, uses complex encryption and server-side key generation.
Because of powerful and complex encryption and server-side keygeneration it is impossible to decrypt the files using manual decryption technics.
It can decrypt all type of files including system drives, removable drives and the network drive.
Petya:
This ransomwarewas first discover in 2016, it uses encryption and fullyblock the user out of the system, affect windows master reboot and encrypt file system table. Petya used email attachment technic to spread.
New improvement in the ransomware called notpetya is capable of using eternalBlue exploit.
WannaCry: this Ransomware attacks the target and encrypts the files. It exploits theeternalBlue exploit in windows. It is the most known ransoware attack in recent time [1]
Working Machanism of ransomeware
Exploit and infection:
Infection and exploit mechanism have to important milestones first is delivery of the malware and the second is gaining execution.
Malwares are delivered to the victim by email or malvertising, other methods of distribution are not so popular. Once the malware is deliveredthe next step is to getting executed for that purpose it used exploit of the system or other programs.
When malware successfully executed it does it work to ensure that the process of exploit doesn’t stops.
Delivery and Execution:
Fileis executed and the persistence mechanism to continue attack is put into the system so that the ransomware can continueattack.to makes sure the that the execution will continue even after reboot of the system.
It puts itself in the startup folder so that when the system is rebooted it automatically starts itself.
in windows system it can modify the registry and can put itself in the scheduled task that automatically startup on system reboot.
Environment mapping – Before performing attack process ransomware map the environment of the system. Environment mapping have different purpose some ransomware use environment mapping to avoid attacking a specific location-based system, or a system using specific language.
Environment mapping is also used to detect the files and folders that should be the target for encryption and also it is used to find possible vulnerabilityinto the system.
that canbe exploited.Ransomware also understand whether it is running in virtual machine or real machine by environment mapping,if it is running in virtual machine it shut down itself so that its behavior cannot be understated[2]
Privilege escalation – To attack and cover its operation ransomware may require higher level privilege, to achieve this goal ransomware use privilege escalation and an administratorprivilege.
Administrator privilege is require to overwrite master reboot record which cannot be achieve by current level of privilege.
Backup solicitation: after completing the process of gaining access and execution and establishing the persistence process ransomware removes the backup file of the system so that backup cannot be restored.
This is process that ransomwarefollow so that unabability of backup can be exploited to get ransom paid.
File encryption:
Once the backup system is removed ransomware encrypt the files of the system and exchange encryption key with command and control center of the system so that encryption key can be used to decrypt files later when ransom is paid.
Ransomwaremove or delete the original files. Ransomware also generally remains the files[3].
Ransom notes –
When encryption is completed ransomware put a note on the user screen notifying that the system has been encrypted and the user need to pay a ransom in order to decrypt the content.
Potential threats
There are different issues that are also faced by the firm due to the ransomware and different related virus.
It is because due to the viruses, file of the systems, data. Etc is hacked by the hackers and after the ransom; they allow the user to access the usable file and the data.
Because of this, it can be determined that there are different potential threats that are posed by ransomware.
Systeme lockup:
Ransomware locks the system and make it inaccessible to the user, so that user cannot access his or her private and important data and he is compile to pay the ransom in order to get data back.
Encrypting and deleting files:
It encrypt the files and alsoremoves the original files so that user cannot find the original file and restore them.
Recent attack
There are various attacks hat are posed due to the posed by ransomware and had been affected the business of the firm.
But at the same time, there are also some recent attacks that are also posed by ransomware.
In this, the most common and recent attack at large scale and well known is wannaCry attack that infected business significantly.
Attack started on the 12th may 2017. It was a global level attack and affected more than 100 countries [3].
It affected more than 200,000 computers worldwide. The ransomware used the exploit named eternalBlue that was exploited was NSA,vulnerability was publically released by shadow broker.
It targets 176 extensions. Which include image, video, document and other important file formats [2] [3].
It encryptfile to get the file back from the encryption it asked about $300 payment in form of bitcoin.
Email phishing was the main method of spreading the virusthrough the globe. Main victims of the attack include window [2]s 8, 2003 and XP users [5].
The vulnerability was possible as latest security update of windows xp was april 2014 based as Microsoft stop supporting these versions. After attack Microsoft release emergency updates to tackle the attack.marcushutchins discovered kill switch accidentally which was a domain [4], he registered the domain which slowed down the virus spread and gave time to come up with some defensive solutions.
Adrian created wannakey based on the flaws in the software, software will not work if the system is rebooted or the decryption key is overridden. ransomeware have a characterstic of fast propagation [1].
User of affected computer were shown a message that there files are encrypted and will be decrypted if ransomeis paid. Many small business of the industriesl were affected by the ransomware , SMEs urged to upgrade the system to avoid possible exposure to the ransomware.
Impact: this ransomware impacted businesses all over the world, some company’s halted business for some time when one or more computers of the company were affected by the ransomware.
SMB protocol disabling was the another way to stop hackers from gaining access. UK,s National Health Service was badly affected.
The reason for the affected NHS was it reliability on the specific version and feature of the windows [4].
In healthcare and businessthousands of the appointment werecanceledand business operations were affected. Taiwan Semiconductor Manufacturing Company.
This firm is also one of the leading firms in the market and has lots of business advantage in the market.
This firm also has the tie up with the business that helps the firm to get the competitive advantage and to handle the all customers also. At the same time, this firm also faced the issue of ramsomware virus and in this; this firm faced the WannaCry virus issue.
In this, iPhone chipmaker blames WannaCry ransomware variant that was the major issue for the firm to manage the business and the customers’ base also.
Because of this, it can be determined that the WannaCry is the major issue that affects the performance and the business of the firm as well.
Following figure shows attack statistics of the wannaCry.
Networks affected by WannaCry
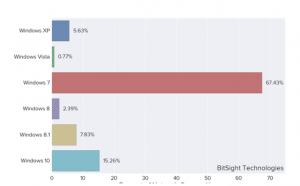
Figure 1 Percentage Of Network Affected by WannaCry
From the above graph, it can be determined that although, there is a huge impact of the WannaCry issue on the all windows such as windows 10, 8, 8.1, vista, XP, 7, etc.
but at the same time, it can also be determined that major impact is on the windows 7.
It is because it is one of the highly used windows across the world and due to lack of security concern; it is easy for the hackers to hack the data from the windows 7.
That is why, the percentage ratio of network affected by WannaCry in on the windows 7 as compared to the others.
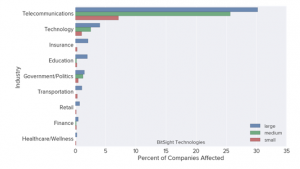
Figure 2 Source BITSIGHT
The above graph represents that there are different industries that are affected due to WannaCry virus but at the same time, it can also be determined that telecommunication industry is highly affected industry due to the WannaCry.
Mitigation Tools
Propcom: it uses honey pot methods and detect if any process trying to change the file. it kills the process if it find any process trying to do so [6].
SSDT: vssadmin.exe toin order toprevent local snapshot from being deleted. Stops the ransomware from deleting the files
Summary:
Ransomeware is malware that affects the system and makes its data inaccessible to its legal and authorised user, in order to gain back the access to the data user need to pay a ransom so that file can be decrypted.
There are many ransomware but the most recent and well know ransomware attack is wanna cry ransomware attack which affected more that 100 countries all over the globe and more that 200,000 devices.
Works Cited
x
x


