Penetration Testing The Cloud
Security of the data stored in the cloud is one of essential and most emerging need in cloud computing to ensure that the data and the application of web are secure. Different types of attackers try to hack systems in the network or any individual users.
Hackers try to infiltrate the web application and the underlying software. With the help of penetration testing the security strategy of your web application can be evaluated and monitored when any data which are most sensitive are monitored using the penetration testing.
Penetration testing is done as a core part web application security to find out the vulnerabilities in the applications. Penetration testing made on the web application helps to examine the overall security risk and the potential risks that are involved in the web application which may include errors in the coding, breaking of authentication and injecting vulnerabilities inside the application or in the stored data.
Penetration testing is done on computer system, system connected through network or on the application that are hosted. Its main use is to find out the vulnerabilities which are open for hackers to breaches the security of the system is one of the important feature today.
Hackers hacks the data of the company or even prevent the authorized person to access the data and ask for a huge amount so that they will allow accessing the data stored in the cloud. Penetration testing helps the security team to find out the arising issues. It is one of the cheapest tests and helps to identify the vulnerabilities as soon as possible.
Pen testing and its different usage and implementation are identified due to the growth of cloud environment. Pen tests are to be conducted for all cloud-based application as a counterpart of on-premises testing. While the penetration test is run in a public cloud may complexities arise which include technical and legal hindrance.
Approach on cloud based pen testing
The first and foremost step is to understand the policies that are given by the cloud provider. There are many cloud providers in the market today due to increased use of cloud environment. Many providers have restrictions on the doing pen test about what type of test they can actually do while testing it with pen-testing.
For example let us consider one application is running on the cloud which you try to pen test it for any vulnerability in the cloud. Before executing the test we should do some research and find out the recommendation of the cloud provider for different process they use. It the recommendations of the cloud provider is not followed it may cause some errors.
Pen test looks like a DDoS attack and it cause the system to shutdown or restart your account. Infrastructures in the cloud are monitored by all the cloud providers to find out the anomalies. When running the penetration testing then the user can inform the system operators or user about the unwanted happening in the cloud.
There are even some automated procedures that are implemented. If any attack is detected in the cloud environment it may stop the running application or even shut down the system without any warning message it looks like a DDoS attack. All the cloud providers will monitor their infrastructure to find out the anomalies in the cloud.
Since we have taken the public cloud for testing. Public clouds are noisy since it is a multitenant and should manage the requirement between the available resources. Some of the cloud providers will shut down the system automatically. Since the applications are shutdown by the providers when the user try to login to the system they can find that the cloud application, database and storage are offline.
If you want to login to the cloud database or cloud application by providing the current credential, A clear explanation about how the username is blocked should be given to the cloud provider. When we implement the penetration test in the public cloud there are certain rules to be followed by the public component. Before doing the pen test the legal policies and procedures should be well known.
The following are the points that should be covered by all the people who try to implement it.
- Application
- Data access
- Network access
- Virtualization
- Compliance
- Automation and
- Approach
Application is to identify the needs of APIs and user interface. Next they should identify how the data should be pen tested whether with application or directly to the database in the cloud. Network access is used to check whether the application and the data stored in the cloud are protected. Then to find out the workload based on the isolation of the virtual machine and its workload.
Laws and regulations in the database should be known before the testing the data is termed as compliance. Many automated tools are available to test the application based on cloud. Identification of one such automated pen testing tools is more important. Then identification of the approach that should be followed while testing the application like including or excluding them in pen test.
It explains the reaction of admin thinking that a real attack has happened. The test to be conducted should be agreed by all the members in the pen testing team and should be followed as per the plan. Any exceptions raised by the application helps us to identify the reaction of the admin who is seeing the pen test occurring and killing the access.
Selection of pen-testing tools
Many pen-testing tools are available now among which on-premises cloud-based application is a popular approach. Many cost effective pen-testing tools are also available in the market. While selecting the pen testing tool it is important that it should simulate the actual attack.
Hackers commonly use to guess password or look the APIs that provide direct access to the data that is stored in the computer the tools that we select should simulate procedures that hackers can try to hack the system. Pen-testing tools can’t meet the requirements which should be avoided since it increases the cost of leverage an existing tool.
While executing the pen test the following things should be observed
- Human Response
- Automate Response
Human response is based on the reaction of the application admin team and the users about the pen test. The get a correct result the test should not be disclosed. Many users may shutdown the system while some will try to identify the problem first, before identifying and uplifting the threat.
It also takes the response of the client providers which one of the important aspect of the responders. In automated response system the system will automatically find out the threat. Based upon the identified threat the system can simply block the IP address or shutdown the application by the generated pen test.
Whatever action it takes should be intimated to the application admin along with a description that says the action taken to correct the issues. Documentation of both human and automated response is important. With the help of the documentation we can find out the difference in the responds of the system and human on the threat and identify the security level of the system.
Elimination of vulnerabilities
The main outcome of this testing process is to find out all the vulnerabilities in the system and to discover it with the help of pen test. The list may contain any number of issues it may be one or two or even hundreds.
If no issues are found it means that the pen test created is not effective and it indicates that a re-evaluation of the test should be conducted to find out the vulnerabilities in the system. Some of the vulnerabilities found by the simulation of pen testing in the cloud-based applications are
- Application data can be accessed by using **** API
- Access to the API will be granted after a maximum number of attempts
- Isolation of workload is not properly done by the VM
- DNS is disabled and the VPN will allow outside user to access the data
- New regulations are not followed while encrypting the data
- Other problems related to the security of the data
Depending upon the type of application that we run the types of issues may vary depending upon the pen test run on it. The different layers like application, network, database, storage system etc should also be tested and reported separately. The interoperability of the layers should also be tested. Output of the test made on each layers should be produced as a report. It is one of the best practice to be followed in pen testing.
The recommendations of the cloud provider regarding the pen test should also be followed to test the applications in the cloud. The get the best result the process flow should be followed by putting all the efforts we can get a best result.
Suggestions on final pen-testing
The pen testing results also depend upon the who’s doing the test and if the testing is done at home then some issues will not be answered. Even good internal testing teams will miss some things. The team members are familiar with all the application and can identify the causes and lead to omission.
White-hat hackers can be used as an alternative to run the cloud-based application for their money. Researchers are going on to find out the types of applications. The pen testing approach and its tools should be customized as per the specific requirements.
OpenStack Cloud Management Software
OpenStack provides an integrated cloud management with four core services which include Compute, Storage, Networking and Dashboard along with a set of ancillary service Identity and Image. The below image shows the block diagram of the software.
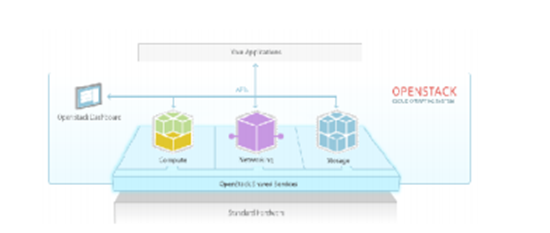
It is used to manage virtual machines with huge networks. The openstack compute use cases are extended from public cloud that offers IaaS service, Private clouds which offers service within an organization, applications of big data and for application of high-performance computing. Features of openstack is to manage the virtualized server resources like memory space, CPU, network interfaces etc.
It manages Flat, Flat DHCP, IPv4, IPv6, etc of the local area network. It also manages to store the data that are imported, shared and helps to query the virtual images. It can also assign or reassign the IP address of the virtual machines in the cloud. Security is provided to the users, project and roles with the Role Based Access Control (RBAC). Faster provisioning is provided for caching VM image on the nodes.
Both object and block storage are provided by the openstack storage to use it along with server applications. A distributed storage system for virtual machine images, backups and archives are a static storage which is considered as object storage.
To provide scalability and redundancy objects and files that are written using multiple disk drives help them to spread throughout the openstack cloud. A persistent block level storage is provided by openstack which can be used by high performance data storage with compute instance and expand the file system or for the server to access the raw block level storage.
Features of openstack storage (Swift & Cinder) are usage of commodity hard drives which will reduce the storage cost per byte. To make the storage highly redundant and reliable self-healing is done by coping data to several different places all over the cloud. Data storage is unlimited for both horizontal and vertical scaling.
Can provide storage for very large scale objects with multiple petabytes of data along with billion of objects. Elastic Block Storage of Amazon S3 support API. It has many build in management utilities like account management, storage monitoring and container management.
OpenStack Networking is used for managing API-driven system network and its IP addresses. A feature of openstack networking (Quantum) is to manage the IP address by allowing static IP address, DHCP. It provides various networking models which also include VLANs. Users can create their own network and manage them. Various devices canbe integrated in the cloud with the help of network framework which include firewalls, intrusion detection system, load balance etc.
OpenStack Dashboard is provided for the cloud administrator and also for the users to manage the resources in the cloud and to control the compute and storage in the cloud. Administrators can create users and assign project to the user along with a limited set of resource that are required for the project. Dashboard can also used by the user to control the resource that are allocated to them for their project. It is an extensible web based application.
OpenStack Identity is used to maintain the user’s database and to map the users to the OpenStack service which they can access. A common authentication is provided by openstack identity (Keystone) which can integrate third party backend directory services.
It supports standard authentication of providing username and password credentials, token based system etc., along with other multiple forms of authenticate. Cloud administrators can set up common policy for all the users and system in the cloud and can specify the permissions of computation, storage and network of resources.
OpenStack Image is a service which helps to discover, register and service for disk and server image. Image templates can be created by the cloud administrators with the help of the template cloud users can instantly create new image. It helps to create and store the snapshots of the created image. It supports different types of image formats which include VHD (Hywhich include VHD (Hyper-V), Virtual Box(VDI), qcow2, VMDK and OVF.
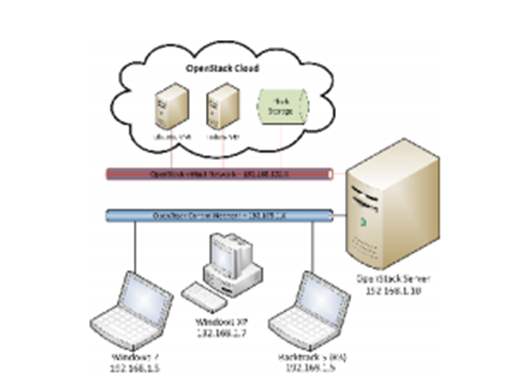
Open Stack penetration test are built and configured. For the purpose of implementation four computers are configured to support the penetration testing. To connect the OpenStack dashboard a laptop with window 7 is used.
Along with this a window XP system is configured with network interface card, wireshark etc are used to analyze network traffic to and from the open stack server. The implementation setup and the output that are received are demonstrated in the output section. The image shown below depicts the OpenStack Test Cloud Implementation.
Before implementing the penetration test a scan of the openstack server is executed using Zenmap program which is a GUI for the nmap program which is called as Network Mapper. The result of the scan indicates the no of ports on the openstack server which can be used as an attack vectors.
Setup of server:
Packet trace
Backend trace:
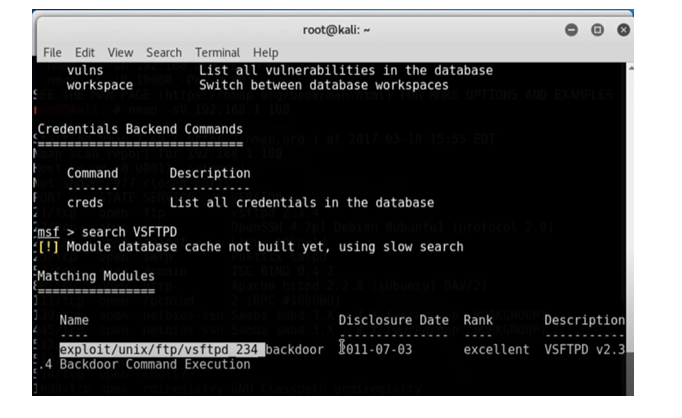
Module selection:
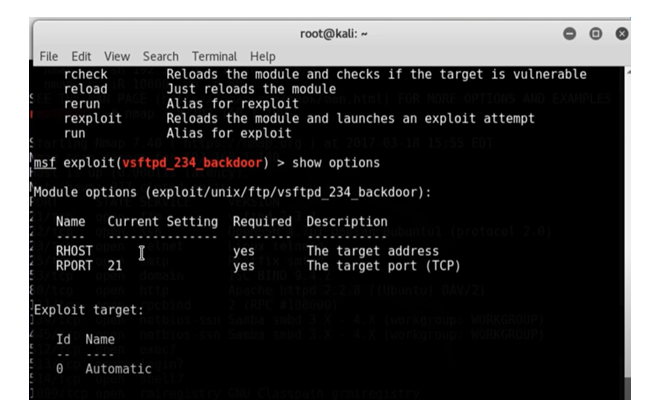
Host setup:
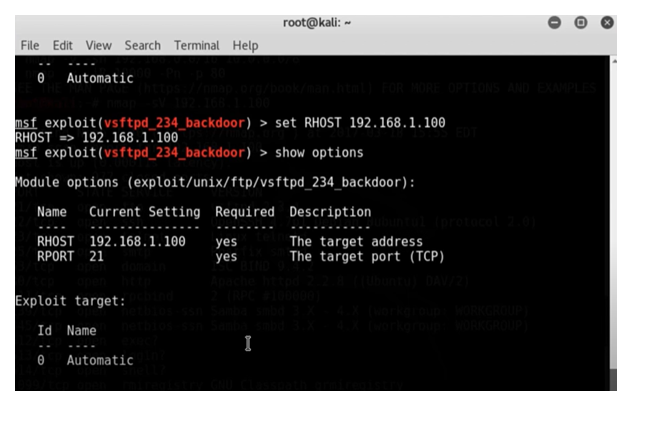
IP tracing:
Number of penetration test is performed in OpenStack cloud management server during the implementation of this research. Among which the HTTP Fuzzing dashboard does not reveal any vulnerabilities. It uses two test programs BED and sfuzz used in HTTP fuzzing attackes in the distributed penetration. Packet tracing test is also executed. Different types of theft attacks were implemented to gain the administrative access.
In an unencrypted network the login credentials are acquired easily using Wireshark this is done by locating unencrypted files on the openstack server which contains information that are more sensitive. The vulnerabilities that are developed during this research can be prevented using the HTTPS for communication between the cloud management software and the cloud users. By encrypting the credential the openstack files that contain sensitive information can be prevented.
Performance of penetration test is an important task that should be continued on the OpenStack cloud management software. Many large scale companies use openstack to test their private and public clouds to protect their data by improving the overall security. Many of the users are moving all their application and data in the cloud to OpenStack user because of testing and its worthy effort.
Penetration test ensure the security of web applications and provides a core security by identifying the vulnerable applications that are running. A report of Forrester have said that nearly 60 percent of the companies in North America depend on the cloud computing.
- B. Mohata, D. M. Dakhane, and R. L. Pardhi,2013. ‘‘Cloud based testing: Need of testing in cloud platforms,’’ Int. J. Appl. Innov. Eng. Manage, vol. 2, pp. 369–373.
- Raengkla and T. Suwannasart,2013. ‘‘A test case selection from using use case description changes,’’ in Proc. Int. Multi Conf. Eng. Comput. Scientists, Hong Kong, pp. 13–15
- Singh, A. Kaur, B. Suri, and S. Singhal,2012. ‘‘Systematic literature review on regression test prioritization techniques,’’ Informatica, vol. 36, no. 4, pp. 379–408.
- Kumar and S. Rao,2014. ‘‘A latest approach to cyber security analysis using vulnerability assessment and penetration testing,’’ Int. J. Emerg. Res. Manage. Technol., vol. 3, no. 4, p. 21.
- Jones,2013. ‘‘Penetrating the cloud,’’ Netw. Secur., vol. 2013, no. 2, pp. 5–7.
H.-C. Li, P.-H. Liang, J.-M. Yang, and S.-J. Chen,2010. ‘‘Analysis on cloudbased security vulnerability assessment,’’ in Proc. IEEE Int. Conf. E-Bus. Eng. (ICEBE), Shanghai, China, , pp. 490–494
- N. Goel and B. M. Mehtre,2015. ‘‘Vulnerability assessment penetration testing as a Cyber defence technology,’’ Procedia Comput. Sci., vol. 57, pp. 710–715.
- Denis, C. Zena, and T. Hayajneh,2016.‘‘Penetration testing: Concepts, attack methods, and defense strategies,’’ in Proc. IEEE Long Island Syst., Appl. Technol. Conf. (LISAT), pp. 1–6.
- I. Sahu and U. Pandey, “Mobile cloud computing: Issues and challenges”, Proc. Int. Conf. Adv. Comput. Commun. Control Netw. (ICACCCN), pp. 247-250, Oct. 2018.
- Akherfi, M. Gerndt and H. Harroud, “Mobile cloud computing for computation offloading: Issues and challenges”, Appl. Comput. Informat., vol. 14, pp. 1-16, 2018.
SFUZZ (Simple Fuzzer), available from http://SFUZZ.git.sourceforge.net/git/gitweb.cgi?p= SFUZZ, December 2012.
Quick Start All-in-One OpenStack Shell Script, available from http://devstack.org
National Vulnerability Database CVE-2012-2144, http://web.nvd.nist.gov/view/vuln/detail? vulnId= CVE-2012-2144
Wireshark is available from http://www.Wireshark.org
Zenmap and nmap are available from http://nmap.org
OpenStack Documentation is available from http://docs.openstack.org


