TASK 1 : PENTEST PORTFOLIO
Introduction
In the 21st Century, there is no risk in the digital world as genuine as digital wrongdoing. Novel and one of a kind method for digital wrongdoings have come up as AI has attacked the worldwide tech space.
One of the manners by which the defenselessness of an association can be tried is Penetration trying. In this examination, the various techniques of entrance testing have been talked about and a relative investigation of the equivalent has been given. The legal rules just as the administrative structures that have been upheld by the UK enactment in such manner have additionally been featured.
Besides, the investigation incorporates a definite standard working methodology (SoP). A dynamic tree has likewise been incorporated.
PenTest Methodology Comparison
The fundamental and essential point of pentesting is to survey the safety efforts of data security. This is done from the point of view of an aggressor.
It serves a few purposed, the essential among them being to find out the effect of security controls. As remarked in the investigations of Lechner (2017), there are different techniques for pentesting.
They can be recognized with respect to the strategies they follow.
Here is a comparison of four major pentesting methods.
| Goals | Scope | Assessment | Pre-engagement guidelines | |
| ISSAF | ISSAF targets incorporating each and every chance of a penetration test from its beginning to the wrapping up.
|
ISSAF is viewed as a structure and it remembers different methodologies for draft 0.2.1B.
|
The methodology has been created in three distinct stages which are: orchestrating and status, assessment, and, enumerating and cleaning up. One significant bit of leeway offered by ISSAF is that the specific association between the tasks and other related hardware are given | It is viewed as simpler to decimate information than to restart it.
|
| OSSTMM | OSSTMM (v3) is a technique that embodies various modules and channels that manage distinctive space districts
|
It was made under the benefits from open source allowing | OSSTMM is basically a technique for assessment. In this way, it isn’t as broad as ISSAF. It is progressively valuable and favored as an exploring instrument and authoritative necessities. The analysts of security have more than the necessary fitness.
|
The most recent adaptation requires paid interest |
| OWASP | OWASP includes different hardware and testing frameworks. These are principally for advanced security under open source licenses.
|
OTG is predominantly for three unique regions that include: the testing structure for development of various web applications, systems for the testing of these applications, and reporting the arrival of the previously mentioned applications | It is allowed to use so as to assemble a web application that can give security significantly after such a test has occurred. Thusly, OTG is progressively centered around the security encompassing the different web applications instead of the ISSAF and OSSTMM, which center for the most part around the testing of security execution | OTG is centered around just a single one of a kind element of the web: web applications |
| BSIMM | BSIMM contains 112 activities that have been arranged into 12 woks. Instances of these incorporate SSDL contact and sending
|
It was made by watching the security in more than 63 associations
|
BSIMM doesn’t demonstrate the instruments to be utilized or the system of utilizing them
|
Pentesting is just one of the few highlights offered by BSIMM.
|
Table 1: Comparison of pentesting methods
(Source: Shanley and Johnstone, 2015)
Statutory and legal consideration of a penetration tester
The United Kingdom has various enactments and declarations that should be clung to while directing a pentest so as to shield the enthusiasm of the association. These incorporate,
- UK Computer Misuse Act 1990
- UK Data protection Act 1998
- Police and Justice Act 2006
- Human Rights Act 1998 (Legislation.gov.uk 2020)
To ensure that the structure is being followed and the result is sure, an instrument that encourages the arrangement of agree should be implemented. This component characterizes the degree of the test and furthermore guarantees that the strategy and system of the tests doesn’t damage any of the authoritative standards.
It has been seen in the investigations of Lechner (2017) that this structure ought to be endorsed and approved by a court. It is urgent that the extent of previously mentioned agree be stretched out to incorporate specialist co-ops and other outsiders.
No type of testing ought to be led before a reasonable assent has been gotten. It has been expressed by Radanliev et al. (2019), this system will make it sure that no laws will be broken, even unexpectedly. It likewise guarantees that no data has been covered up by the association that is doing the testing.
As an addendum, since this assent may contain subtleties that are delicate in nature, it is essential that these subtleties are managed utilizing total tact.
SOP for Task 2
Phase 1: Pre-engagement interactions
1.1.Metrics for time estimation:
To the total time that has been calculated, an additional 20% must be added as a buffer in case of emergencies and unforeseen occurrences.
1.2. General questions:
Questions should be asked from every aspects of the security system of the organization.
1.2.1. Test for the Penetration of Networks
1.2.2. Test for Web Applications
1.2.3. Test for the Penetration of Wireless Networks
1.2.4. Test of Physical Penetration
1.2.5. Societal Engineering
1.2.6. Interview with Managers of Business Units
1.2.7. Interview with the Administrators of the System
1.3.Scope creep:
If the work provided increases, then the payment should also increase proportionately.
1.4.Specify IP ranges and domains:
Whether or not the testing includes systems like the firewalls and the IPS/IDS should be clarified in the beginning of the test.
1.4.1. Validate ranges:
It is important to ascertain which systems belong to the client. Penetrating any other system would constitute a breach of the law and open the tester up to prosecution.
1.5.Third parties:
To maximize the results and the effectiveness, any third party organizations associated with the business must be aligned with the testing.
1.5.1 Cloud services
1.5.2 ISP
1.5.3 MSSPs
1.5.4 Servers being hosted by different Countries
1.6. Definition of acceptable social engineering pretexts:
It is also paramount to understand the type of attacks that the client is currently facing so that solutions can be found accordingly.
1.7.DoS testing:
Denial of Service (DoS) testing should be considered to ease any apprehensions that the client may have about the conduct of the test.
1.8. Goals:
While it is unadvisable to establish the primary goals on the basis of compliance, the secondary goals could be compliance-based.
1.8.1 Primary
1.8.2 Secondary
1.8.3 Analysis of the Business
1.9. Mechanism for Contact in Case of Emergencies:
Emergency contact mechanism must be predetermined to avoid losing valuable time in case of any such occurrences.
1.9.1. Process of Incident Reporting
1.9.2. Process of Defining the Incident
1.9.3. Frequency of Status Reports
1.9.4. PGP
1.10. Rules of engagement:
This decides the length and duration of the testing process.
1.10.1. Timeline
1.10.2. Locations
1.10.3. Handling of evidence
1.10.4. Regularity of meetings to discuss Status
Phase 2: Intelligence gathering:
This phase aims at gathering requisite information and intelligence so that the target can be reset and redefined accordingly.
2.1 Selection of the Target:
There is a wide plethora of factors to be considered for selecting a target
2.2.1. Identifying the Target
2.2.2. Rules of Engagement for the Target
2.2.3. Test Duration
2.2.4. Test Goal
2.2 OSINT
2.2.1. Passive accumulation of information
2.2.2. Semi-passive accumulation of information
2.2.3. Active accumulation of information
2.3 Covert gathering
2.3.1. Corporate
2.3.2. HUMINT
2.4 Footprinting
2.4.1. Footprinting from external sources
2.4.2. Footprinting from internal sources
2.5 Identify protection mechanisms
2.5.1. Protection based on Network
2.5.2. Protection Based on Hosts
2.5.3. Protection Based on Applications
2.5.4. Protection for Storage
2.5.5. Protection for Users
Phase 3: Modeling of Threats
3.1 Analysis of Business Assets
3.1.1. Data from the Organization
3.1.2. Human Capital
3.2 Analysis of the Business Process
3.2.1. Process favoring technical infrastructure
3.2.2. Process favoring informational assets
3.2.3. Process favoring human capital and employees
3.2.4. Integration of Third Party Software
3.3 Analysis of Threats
3.3.1. Possible Threats to Employees
3.3.2. Possible Threats to Management
3.4 Analysis of the Capability of Threats
3.4.1. Tool Analysis
3.4.2. Exploit availability analysis
3.4.3. Channels of communication
3.4.4. Ease of Access
3.5 Model for Motivation
Phase 4: Analysis for the Testing of Vulnerabilities
4.1 Testing:
Various assessments need to be conducted to understand the vulnerabilities of the system and how they can be exploited.
4.2 Active:
This means coming into direct contact with the equipment being tested.
4.3 Passive:
This involves mere monitoring and analysis from afar.
4.4 Data Confirmation
4.4.1. Relationship between the tools Used
4.4.2. Manual testing
4.4.3. Attack avenues
4.5 Research:
Once probable issues have been identified, research needs to be done to check for the validity and accuracy of these issues.
Phase 5: Exploitation
5.1 Purpose:
This process involves bypassing the system security to gain access to the system. It uses specialized methods to do so.
5.2 Preventive Measures:
These are methods which are developed to prohibit this bypass.
5.2.1. Anti virus
5.2.2. Human measures
5.2.3. Prevention in the execution of Data
5.2.4. Randomization of the Layout for the Address Space
5.2.5. Firewalls for Web Applications
5.3 Evasion:
This is a technique used to escape and bypass the security measures enabled by the organization.
5.4 Precision strike:
This process use simulation software as a substitute for simulated attacks that have been occurring.
5.5 Customized Exploitation Avenue:
As all the attacks are not the same, some degree of customization is also needed.
5.6 Tailored exploits:
Available exploits are customized and tailor-made to the specifications of the attack.
5.7 Zero-Day angle:
This is a form of corporate espionage representing large firms who may mount such attacks against major competitors or threats.
5.7.1. Fuzzing
5.7.2. Analysis of the Source Codes
5.7.3. Types of exploits
5.7.3.1. Buffer overflows
5.7.3.2. SEH overwrites
5.7.3.3. Returned orientation programming
5.7.4.Analysis of the Traffic
5.7.5. Physical access to the system
5.7.6. Proximity access to the system
5.8 Possible avenues of attack: It is essential to identify various avenues through which an attack may occur. This is done to avoid surprises in the form of an attack from a yet unidentified zone.
5.9 Overall objective: The overall objective needs to be decided and agreed upon before the test so that the procedures can be set accordingly.
Phase 6: Post exploitation
6.1 Reason
6.2 Rules of engagement
6.3 Analysis of Supporting Structures
6.4 Pilaging
6.5 Targets of High Profile
6.6 Exfiltration of information
6.7 Persistence
6.8 Further penetration into infrastructure
6.9 Cleaning up
Phase 7: Reporting: The findings of the test need to be communicated to the client. The client needs to be informed of the various threats and how to go about mitigating them. They might also need assistance with the existing security mechanism to prevent further breaches.
7.1 Brief Summary
7.2 Structure of the Report
7.3 Executive summary
7.4 Technical report
Decision Making Tree for Task 2
A dynamic tree helps in shaping a plan of the potential activities. It incorporates all the means that should be taken to upgrade efficiency and get the most ideal result.
It has been confirm in the investigations of Said et al. (2015), that a choice tree shows the means just as the interrelationships and the relationship between’s these means. This will empower better and complete comprehension of the venture, and give an essential diagram of the outcome that is being normal.
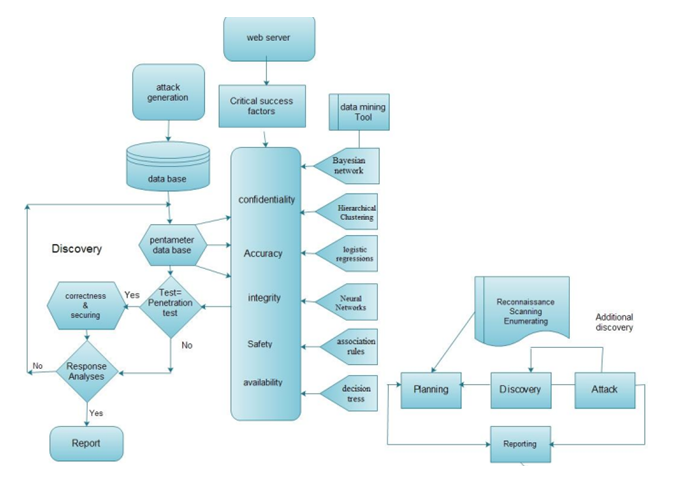
Figure 1: Decision making tree
(Source: Saidet al. 2015)
Conclusion
Digital wrongdoing is perhaps the greatest risk to organizations in the 21st Century. These might be led by both individual programmers or by rival organizations.
To forestall them, it is critical to build up a safeguard instrument that reviews the brain research of the aggressors and protects itself as needs be. One such technique is called Penetration testing.
This examination clarifies the different types of entrance testing as to their extension and evaluation. Through this, it very well may be comprehended that most extreme consideration and precautionary measure is required when utilizing such programming.
There are certain and negative components for all the strategies, in this manner each issue will have an alternate strategy that is best for illuminating it. The examination has likewise given a rundown of parliamentary enactments that should be clung to.
Notwithstanding that, there is a blueprint of a straightforward infiltration test that gives a brief look into the fundamental configuration by which these tests are led. A dynamic tree has additionally been remembered for this investigation.
.
Reference list
Shanley, A. and Johnstone, M.N., (2015). Selection of penetration testing methodologies: A comparison and evaluation.
Legislation.gov.uk (2020), UK Cyber Laws. Accessed on: 12.04.2020, accessed from: https://www.legislation.gov.uk/
Said, H.M., Hamdy, M., El Gohary, R. and Salem, A.B.M., (2015). An integrated approach towards a penetration testing for cyberspaces. European Journal of Computer Science and Information Technology, 3(1), pp.108-128.
Lechner, N.H., (2017). An Overview of Cybersecurity Regulations and Standards for Medical Device Software. In Central European Conference on Information and Intelligent Systems (pp. 237-249). Faculty of Organization and Informatics Varazdin.
Radanliev, P., De Roure, D.C., Nurse, J.R., Burnap, P., Anthi, E., Ani, U., Maddox, L.T., Santos, O. and Montalvo, R.M., (2019). Definition of Internet of Things (IoT) Cyber Risk Discussion on a Transformation Roadmap for Standardisation of Regulations Risk Maturity Strategy Design and Impact Assessment. arXiv preprint arXiv:1903.12084.


Thanks-a-mundo for the post.Really thank you! Awesome.
https://guidemysocial.com/story2136612/valve-manufacturers-in-india-list-an-overview
I really enjoy the article post.Really looking forward to read more. Great.
https://bookmarkspring.com/story11436823/helping-the-others-realize-the-advantages-of-canada-family-visa-requirements
Very informative article post.Really looking forward to read more. Really Cool.
https://inspro2.com/
Muchos Gracias for your post.Really thank you!
https://saxenda-kopen78900.blogdomago.com/24907228/finding-excellence-in-pulmonology-your-guide-to-pulmonologists-in-madurai
Enjoyed every bit of your article post. Great.
https://troyeyhpx.daneblogger.com/25480342/indicators-on-fresh-vegetables-in-raj-nagar-extension-you-should-know
I think this is a real great blog post.Really thank you! Fantastic.
https://hi-8891235.actoblog.com/26210113/unraveling-the-majesty-of-markha-valley-trek-a-solo-adventurer-s-guide
Really enjoyed this blog.Thanks Again. Really Cool.
https://www.hkcashwebsite.com
Major thankies for the blog article.
https://www.hommar.com/
I am so grateful for your post.Much thanks again. Really Great.
https://blog.huddles.app
Great, thanks for sharing this blog.Much thanks again. Keep writing.
https://blog.huddles.app
Muchos Gracias for your article.Really thank you! Fantastic.
https://crushon.ai/
Fantastic blog post.Much thanks again. Will read on…
https://crushon.ai/character/7573a4cc-a7fc-4c3b-9b11-0f296d2bde95/details?not-for-all-audiences=true&utm_medium=home
Thanks for the blog.Really looking forward to read more. Awesome.
https://ai-sexting.top/
I truly appreciate this blog post.Really thank you!
https://www.yinraohair.com/wigs/shop-by-style/short-curly-wigs
Fantastic blog.
https://www.yinraohair.com/cosplay/shop-by-color/other-color
Great, thanks for sharing this blog post. Great.
https://www.piaproxy.com
Thanks a lot for the article.Much thanks again. Fantastic.
https://telcgrnm.org/
Im obliged for the post. Fantastic.
https://cncmachining-custom.com