Security Algorithms in Cloud Computing
Abstract
Cloud computing is the next level of the internet usage. Nowadays most of the organizations are moving towards the cloud computing because we can share the storage, hardware, software, databases and other processors.
For utilizing these services we can pay reasonable amount to the infrastructure who owns. So there is no proper security in storing the data. The data stored in cloud can be accessed by the third party.
There are different types of algorithms which help to secure the data. In this paper we will see the different types of approaches that help to secure the data. Many cryptographic algorithms can be used to secure the data.
The cloud computing provides the effective service to the users in terms of low cost, very flexible, and reliability etc. The organization no need to pay any services for the maintenance cost. So there is no need to maintain the hardware, software and other storage devices.
Keywords: DES, RSA, security
- Introduction
The cloud computing is the delivery of computing service through internet. It is highly effective and it also allows business people to use the hardware and software through internet. The peoples can utilize the cloud service from anywhere.
This is the main advantage of using the cloud. The resources of cloud can be accessed from anywhere if there is internet connection. Examples for cloud service are webmail, social networking sites, online file storage etc. We need to achieve three things in cloud computing.
They are confidentiality, integrity and availability. To achieve confidentiality the cryptographic algorithms can be used. There are different types of cryptographic algorithms. The data is stored in the common place where we need to provide some security. The types of algorithms are symmetric algorithm, asymmetric algorithm and hash functions.
Cryptography is the secured form of writing. The original data is scrambled under some image, audio, video files. The data is changed from readable form to non-readable form is known as encryption.
The receiver can change the non-readable form to readable form is known as decryption. The performance of asymmetric algorithm is slower than symmetric algorithm. It is an on demand network services. The user can use servers, databases remotely.
The symmetric algorithm has only one key. That is only one public key for both encryption and decryption. The asymmetric key has two keys that is public and private keys one for encryption and another for decryption.
Data Encryption Standard (DES)
It is symmetric key block cipher it takes 64 bit plain text and creates 64 bit cipher text. At the decryption it takes 64 bit cipher text and creates 64 bit plain text. It also uses 56 bit cipher key both for encryption and decryption.
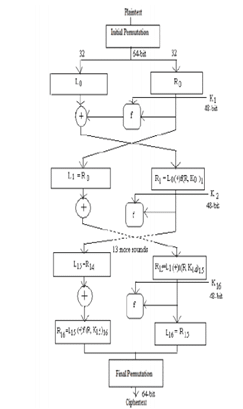
Fig 1: DES
It performs initial permutation on the entire 64 bit block of data. It further splits into two. They 32 bits and further computations are carried out.
RSA Algorithm
It is based on the type of positive integers. It is a public key cryptography. The public key can be known to all and it is used for encrypting the messages. The private key is known only to the receiver to decrypt the message.

Fig 2: RSA
- Literature Review
The authorakshitabhandari et al [1] proposes that cloud provides the various services to the users on demand. The data are stored in cloud at remote areas. There are different types of security issues in storing the data. They are data security, network security and security issues from malicious user attacks.
The author proposes the Hybrid AES algorithm for giving security to the data. The author has compared the original running time of the RSA algorithm and improved algorithm using hybrid encryption algorithm RSA and AES.
Using different keys during the decryption will also enable the people to avoid brute force attack, denial of service etc. The author also suggested that using of multiparty computation also avoids further security concerns.
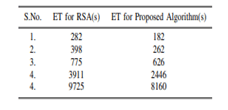
Fig 3: Total execution time
This is the total execution time for the existing and the proposed algorithm. The author also suggested that the time of retrieval of data is also more important. The cloud has to response in a good way to the user. If the waiting time is more the user will be affected in working with the cloud. So there should be good load balancing technique.
Now a day many load balancing algorithms are used to provide effective service to the cloud users. The challenge that comes should be managed with the effective security management. The security management will manage the attacks and secures the data from being attacked and breached. It will provide the data security and the data integrity. There are many controls in the security system like,
- Deterrent Controls
- Preventive Controls
- Detective Controls
- Corrective Controls
These different types of controls will secure the data from different types of attacks.
Plaintext is the real information or data which will be given as an input for the algorithms and the cipher text is the output that comes after the cryptography process.
There are different types of cloud models like deployment models, delivery model and service model. Deployment model is dependent on the types of cloud like private cloud, public cloud, and Hybrid cloud. The private cloud will be taken care by the organisation and the individuals.
Public cloud is the cloud system which is used by the public and it is a self service model. But this public cloud is very minimal secured and attacks might happen easily and no protection for the data. Hybrid cloud is the cloud system that uses the some of the properties of the organisation and ensures the data protection. Delivery models are the different the different form which will make the service in different models.
Service models are of three types like infrastructure as a service, platform as a service and Software as a service. Software as a service is a top layer among the service models. Platform as a service is to oversee the testing process in the cloud environment.
Infrastructure as a service is a service which is used to provide the management and also the availability of the frameworks or other applications which will make sure that the applications are running without delay.

Fig 4: Graph for existing and proposed algorithm
In the above graph the execution time comparison of two algorithms is shown. The proposed algorithm shows the less execution than the existing time. So the response time will also decrease. The cloud environment should be very effective and good response time should be there. The effective load balancing mechanism should be there to deliver good service.
The author prabukanna et al [2] states that many data of the business environment are outsourced and stored in the cloud. Many business people are moving towards cloud due to low cost of service. The business people can remotely they can store the data and utilise the other resources like software, processor, storage and other data servers.
There is no maintenance cost for using this service. This paved the way for many business people to utilise this resources. However the security is the main issue in using this facility. The author uses the hybrid encryption RSA algorithm for providing security.
The author proposes identity based hybrid encryption method. This is achieved by hybrid encryption and proxy re-encryption techniques.
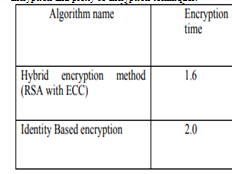
Fig 5: Proposed Encryption time
The author finally concludes that the data should be with high security. The data stored on cloud should be secured using the hybrid encryption and proxy re-encryption mechanisms.
The data is stored in the cloud with receiver identifier which is encrypted. So the receiver can access the information by matching the identifier. Using this method the data is secured properly.
The author vishal R. pancholi et al [3] states that the cloud computing is used by the entire business environment because of low cost. The user is expecting high level of security. In cloud all the data are stored remotely. There is a chance to steal the information.
The high level of security can be achieved by using AES algorithm. The AES algorithm undergoes so much of substitutions, permutations and transformation. The author proposes the AES algorithm provides only less execution time than blowfish method.
It is an iterative method. It undergoes so much of substitution and permutation network. In this the decryption of the encrypted data is possible only with the correct password.
The use of cloud services has increased the business growth at 41%. The author concludes that the AES algorithm is the best security algorithm which offers more flexibility and efficiency.
The author Naveen N.K Thippeswamy et al [4] states that the cloud computing is the multifaceted technique which helps to share the resources in the internet. Many business men are moving towards this technique to use the resources at the low cost. The drawback in using this architecture is lack of privacy and security. The author uses RSA and AES algorithm to provide the security.
The author proposes multilayer encryption approach in his work to reduce the execution time of the algorithm. The diagram above shows the execution time of different types of approach.
Finally the author suggests that use of multilayer encryption approach along with RSA and AES algorithm which helps to provide maximum security and integrity to the data. Thus the data can be secured properly.
The author Qimingzheng et al [5] states that the approach novel discrete chaotic S- Box coupled map lattice is used to provide security in railways. The railway system uses the cloud computing to store the data.
There is no proper security and privacy for the stored data. So this approach is used to provide the data to be secured and allow only authenticated persons to view the data. Finally the author concludes that use of this S-Box technique will provide security and it is very efficient.
A light weight authenticated scheme helps a user lot by avoiding unauthorized to see the data. It provides the balance information security and data transmission.
The author Aized Amin Soofi et al [6] proposed that the cloud computing is the major sources for the business to provide various services at low cost. But there is no proper security provided to the users and there is lack of confidentiality.
The people use the cloud to store their data but there is no control over the data that is stored at the remote areas. There author has reviewed all the research papers which helps to find the different types of approaches and validations that researcher has performed.
The views all the cloud computing papers and finds the validation results. Some of the researcher has proposed but there is no proper validation. The author concludes that the many researchers should validate their works.
The author DhurateHyseniet al [7] states that the cloud computing is used by many business to store the data. There is a big question about the security for high confidential data. The author uses the technique called IT security specialist which helps to secure the data.
There are different types of steps like file encryption, partitioning and distribution of the data. By using this we can provide high level of security to the data. Different types of algorithms are used to provide the security. Thus the author concludes that different types of approaches are used to provide high level of security.
Blowfish is an algorithm that uses 64 bit of cipher and it is useful for the calculation for the power and the throughput. The attacks of malwares and the DDoS were increased and the providers of the cloud are providing more focus on the data security.
As the data security is the major aspect required by most of the organisations and these security algorithms can provide that requirements and satisfies their expectation. Most of the security algorithm will use the cryptography process which involves both encoding and decoding techniques to protect the data from the attacks as well as the attackers.
As many organisations contain sensitive data, the data security or the secure algorithm is very much required in all the organisations that will provide the confidentiality.
- Proposed Work
There are different types of cryptographic algorithm which helps to provide security to the user. We will use the DES and RSA algorithm to provide multiple level of security to the data. First the file is uploaded.
The DES algorithm is implemented and first level of encryption is performed and RSA algorithm is implemented and second level of encryption is performed. Finally the cipher text is stored in the database. While in decryption the process is again reversed.
The stored cipher text is first decrypted into plain text. RSA provides the first level of decryption and again the DES algorithm is implemented to provide the second level of decryption. Finally the plain text is viewed in the screen.
- Conclusion
The cloud is the faster growing environment which helps all business people. We have seen different types of reviews which have shown that many research paper has find only the solutions and only 41% of papers has performed the validation. In this two different types of algorithms are combined to give higher level of security to the highly confidential data.
The multiple level of encryption and decryption techniques helps to provide the high security. The cloud provides the services at low cost. There is no maintenance cost for the services. This made attracted by the many business people and it reached its peak.
This is the one of the booming environment in the internet. The cloud computing is the fats process and it is open and the many organisations are utilizing the cloud for data security and privacy as it provides high confidentiality as it is the important factor which is required by many organisations.
Cloud computing provides the best quality and it the security algorithm provided will give more security to the systems. So it is required in many organisations because of its many number of features.
- Future Enhancement
In future different types of approach are used to provide high level of security. In this we have not concentrated on the execution time of the algorithm. In these areas we have to concentrate more to provide maximum flexibility and minimum response time. New combined hybrid approaches can be used. So the data stored in cloud should be very confidential and highly secured.
References
[1] AkshitaBhandari, Ashutosh Gupta, Debasis Das, Secure Algorithm for Cloud Computing and its Applications, IEEE 2016.
[2] G. PrabuKanna, V.Vasudevan, Enhancing the Security of User Data Using the Keyword Encryption and Hybrid Cryptographic Algorithm in Cloud, International Conference on Electrical , Electronics and Optimization Techniques, 2016.
[3] Vishal R. Pancholi, Dr.Bhadresh P. Patel, Enhancement of Cloud Computing Security with Secure Data Storage using AES, International Journal for Innovative Research in Science & Technology , Volume 2, Issue 09, 2016.
[4] Naveen N.K Thippeswamy, Security and Privacy Challenges Using Multilayer Encryption Approaches in Cloud Computing Environments, International Journal of Innovative Technology and Exploring Engineering, Volume 8,Issue 8, 2019.
[5] QimingZheng, Xiaomin Wang, Muhammad Khurram Khan, WenfangZhang, B.B Gupta and weiGuo, A Light weight authenticated Encryption Scheme Based on Chaotic SCML for Railway Cloud Service,IEEE Access 2017.
[6] DhurateHyseni, ArtanLuma, BesnikSelimi, BetimCico, The Proposed model to Increase Security of Sensitive Data in Cloud Computing, International Journal of Advanced Computer Science And Applications, volume 9, 2018.
[7] Bhardwaj, A., Subrahmanyam, G.V.B., Avasthi, V. and Sastry, H., 2016. Security algorithms for cloud computing. Procedia Computer Science, 85, pp.535-542.
[8] Bhardwaj, A., Subrahmanyam, G.V.B., Avasthi, V. and Sastry, H., 2016. Security algorithms for cloud computing. Procedia Computer Science, 85, pp.535-542.
[9] Ramaporkalai, T., 2017. Security algorithms in cloud computing. Int J Comput Sci Trends Technol (IJCST-2017).
[10] Agrawal, T. and Singh, S.K., 2016, March. Analysis of security algorithms in cloud computing. In 2016 3rd International Conference on Computing for Sustainable Global Development (INDIACom) (pp. 106-108). IEEE.
[11] Deepa, M., 2017. SECURITY ALGORITHMS IN CLOUD COMPUTING: A REVIEW. International Journal of Pure and Applied Mathematics, 117(7), pp.85-92.
[12] Masdari, M., Salehi, F., Jalali, M. and Bidaki, M., 2017. A survey of PSO-based scheduling algorithms in cloud computing. Journal of Network and Systems Management, 25(1), pp.122-158.
[13] Sasikala, M. and Anuratha, V., 2017. ANALYSIS ON CLOUD COMPUTING SECURITY ISSUES AND ALGORITHMS. International Journal for Research in Science Engineering & Technology, 4(1), pp.34-40.
[14] Tan, Y., Qin, J., Tan, L., Tang, H. and Xiang, X., 2018, June. A survey on the new development of medical image security algorithms. In International Conference on Cloud Computing and Security (pp. 458-467). Springer, Cham.
[15] Potluri, S. and Rao, K.S., 2017. Quality of service based task scheduling algorithms in cloud computing. International Journal of Electrical and Computer Engineering, 7(2), p.1088.
[16] Yassein, M.B., Aljawarneh, S., Qawasmeh, E., Mardini, W. and Khamayseh, Y., 2017, August. Comprehensive study of symmetric key and asymmetric key encryption algorithms. In 2017 international conference on engineering and technology (ICET) (pp. 1-7). IEEE.
[17] Arunadevi, M. and Sathya, V., 2018. ANALYSIS ON CLOUD COMPUTING SECURITY ALGORITHMS AND ITS SECURITY CHALLENGES. International Journal of Computer Science Engineering and Technology, 4(4), pp.26-34.
[18] Ashalatha, R., Agarkhed, J. and Patil, S., 2016, February. Data storage security algorithms for multi cloud environment. In 2016 2nd International Conference on Advances in Electrical, Electronics, Information, Communication and Bio-Informatics (AEEICB) (pp. 686-690). IEEE.


