SECURITY ASSESSMENT OF HOME WIRELESS NETWORK
Author Name
Author I
Abstract-Wireless network is used to connect residence as a group of devices such as gadgets, computers and mobile devices access network from wherever in the home.
The wireless network in home used to access files, and folders on devices using Internet as Wi-Fi. It is easy for new devices to connect a network and no access point is needed. The wireless networking company has progressively enhanced on this heritage making consumer-friendly and easier to integrate in a home. It signifies the 802.11[1].
Standards and popular wireless networks are 82.11ac,802.11b/g/n, and 802.11a for significance standards. In home, devices may synchronize in very short range to other devices using wireless local area technologies and increase the quality of life inside the home and enhanced home security which helps to easily access.
Keywords: Wireless network, IEEE standards, Wireless technologies.
I INTRODUCTION
The people taking place to use wireless access at home. In the commencement of internet in 1990s the personal computer is the only network device and only few people started to use internet at home.
The optical broadband network and penetrate the entire country and various devices such as tablets, smart phones, and secondary devices are used at home.
People using home networks in various ways such as data communiqué using the internet, wireless microphone and message with sense devices. The three major wireless access systems are wireless local area networks (WLAN), Bluetooth used for wireless networks [2].
In home network it is mainly used for data communiqué. Wireless become widespread after the standard of IEEE 802.11ac.A machine to machine network is a rational network which is used to connect only prominent–end smart devices but also anything in a home network. Wireless network consist of function in two ways [3].
II LITERATURE SURVEY
The consumer connects to an access point in an ad-hoc peer to peer mode. Access point broadcast service set identifier (SSID) is used by consumer to connect the wireless network.
The consumer select from the register of Access point [4]. The wireless networks are cheaper and easier to set up because there is no cable to run. It is easy to join and leave the network whenever they don’t have to position the substantial access point.
So Wi-Fi device used in home networks effectively. To improve the security in a home wireless network have to update software and remove service to attack a network and devices, change username and password frequently, built strong password, anti-virus software to be updated, install firewall, backup data regularly, increase security and alleviate email threats.
The malicious intruders are continuously threatening the networks for the misconfiguration of access points, weak security controls, and vulnerabilities for compromising the defence of network.
The growth of the remote access of network through the technologies of wireless allow the intruders in a large range and it became risk for the organizations.
So, as a result the vallant is used to help the clients for the identification of access points and analysing the configurations of security and rogue devices, vulnerabilities are tested and the security policies are implemented for the risk minimization.
Setup of home network enables to secure the network device in one place to access a network [5]. The following steps is use to create a home network securely:
- Router plays an entryway between internet and home network.
- Right of entry routers boundary and lock it down in a network.
- Organize security and IP addressing.
- Sharing and control set up to be represented.
- User account to be setup.
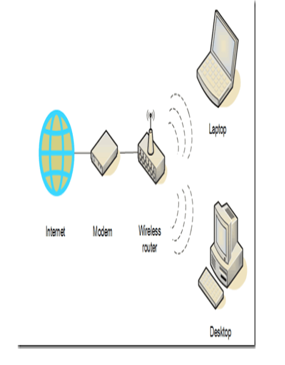
Fig1: Home wireless network
III CONNECTION IN WIRELESS NETWORKS
The connection modes in wireless network are:
- Network adapters in wireless
- Routers
- Access point as wireless
- Wireless antennas
- Signal Boosters in wireless
Network adapters in wireless
It is most common network which is used to connect adapter and it is called as network interface card. In laptop it is used as a small chip which is used inside handheld computers.
The network adapters have a radio transmitter and receiver [6]. The wireless transceivers send and accept message which is used to interpret, arrangement, and organize the data between the system and network. The network adapter increase now a days and use in lap tops and handheld systems.

Fig2: Network adapter in wireless
Routers in Wireless
It is a wirelessrouter which is used to support connection sharing for improved network security with access points. Wireless access point has a benefit of scalability where transceivers spread throughout home through wireless access point [7].
The wireless LAN has a router or access point and run a network adapter using Infrastructure mode else it will run in Adhoc mode. The predictable mode of Infrastructure has an access point to communicate in wireless networks. In an Ad-hoc network it can communicate without access point [8].
Access Point in Wireless
It is used to connect wireless LAN communication station and it is called as base station. The access point are lightweight with a LED light which has to join a wireless LAN with an own broadband router with a wireless computer [9].
Wireless Antennas
In a wireless network adapters, access point, routers use antenna for receiving signal in LAN network. It is shipped to provide sufficient reception to finish the basic network setup.
Signal Boosters in Wireless
A small piece of equipment in wireless access point and routers is known as signal booster. Signal booster which help to increase the base station transmitter strength to improve wireless network communication and response simultaneously [11].
IV PROBLEMS IN WIRELESS HOME NETWORKS(WHN)
A home network it consist of five key issues
- No internet access in wireless network but connected.
- Changeability in network connection.
- Wi-Fi networks are not find out properly
- Numerous devices are connected
- Not able to connect with correctpassword [12].
No internet access in wireless network but connected
The wireless standard has been processed for a particular purpose. It is enhance with incorporating of modern technologies. There are too many wireless network standards and have to check network address in assigned range.
If it shows the exclamation point it is difficult to choose particular wireless system in a Wi-Fi [13]. A wireless home network has access without permission. The firewalls which is used to accept or reject access.
The connection have to check various standard platform which allow client to access without disquieting about connectivity in their own network in home.
Changeability in network connection
In home network client use a network and have experience difference of router distance, congested network and base station connection is wrong where rate of recurrence bands and numerous wireless system may coexist.
It is very difficult to represent an erratic broadband connection to low deployment rate the possibility of coexistence in wireless system has low. The propagation of wireless system increased which will increase the rate of intrusion within same or different system.
Intrusion actually degrades the system throughput in large population such as railway station or common place. Use of 5GHz is a successful solution for diminish the authority of intrusion become most popular wireless system use 2.4GHz band. And the channel 149 use to explore where networks use around the home.
Wi-Fi networks are not find out properly
In a home network people use to communicate with devices and numerous devices will increase considerably. The procedure of setting is very complex because users differ in home wireless network [14].
It is necessary to create a protocol or mechanism that user does not need to implement any procedure settings in home network. In wireless system the procedure has to be followed for both settings and certificate in future to be simplified.
The first thing have to check whether device is airplane mode which able to not connecting Wi-Fi. The devices which connect to 2.4 GHz band [15].
Numerous devices connected in wireless network
The n number of devices which connected to a network is difficult to handle. Many Wi-Fi networks has huge capacities and does not support more device connect on it due to performance go down.
Not able to connect with correct password
The correct username and password have to give in Wi-Fi which is use to get connected in a right network. The wireless connection get load or break down it reject new connections in a network [16].
Wireless home network advantages (WHNA)
The wireless LAN network allows a client to use any relevance and devices without disquiet for connectivity in wireless. The user can enable to use necessary LAN technology:
- Ease of use
- Mobility of wireless networks
- Efficiency of wireless network
- Deployment of wireless Networ
- 5.Expandability of wireless Networks.
Wireless devices connectivity as an Ease of use.
It is used to deploy arbitrary wireless network system for various purposes. These are enabled to use of software representation which is used to process radio signals and access point (AP) which is used for a variety of wireless system in home network [17].
It allows user to access network with any opportune location with increasing saturation of hand held computers in a particular wireless network. Client can access wireless devices without tormenting the connectivity process.
Mobility of wireless network
Public wireless network the client from outsiders can access the internet environment where multiple access point are humiliated over the network [18].
Effectiveness of Wireless network
It is a client centric wireless network connected to maintain constant affiliation network move from one point to another point. This represent the network terminals in wireless system that an employee potentially do her work from any location point.
Deployment of wireless network
The infrastructure in wireless network is based on a single access point where the networks in wired have cables to run more no of locations in use.
Expandability of Wireless network
It has a number of clients to be extremely expanded with an existing equipment. In a wired it requires additional wiring for connecting a network.
Cost of Wireless network
The hardware in wireless networking has a modest increase in wired representation which has potentially increase a cost always outweighed in associate with running physical cables which act as inherent technology of a wireless network in home.
V SECURITY OF HOME WIRELESS NETWORK
The security of home network make easy to pick up signals from a wireless home network. The important feature of wireless network is WEP to improve security. WEP encrypts the traffic network mathematically which help us to understand by computers but human not able to read it. WEP become outdated and WPA replace with security options.
WPA helps to protect from wireless LAN and ensure it to organize properly when set up a network. The wireless network in IEEE standards802.11ac,802.11b/g/n,802.11a provides a network to build effectively.
VI VALIANT APPROACH FOR WIRELESS SECURITY ASSESSMENT
The identification and mapping of the wireless networks which is active, the valiant consultants determine the vulnerabilities of our network, to the attacker with the help of radio access in the space of wireless network.
The consultants of valiant will attempt for the detection of the wireless network in a particular place which includes identifying the ad-hoc networks, and determining the ranges and location of the wireless network, also evaluating the wireless access area range and also determining the information of network configuration, the entry points for the identification of the system information or the parameters for access [19].
The implementation of wireless access for the vallant, vulnerabilities will evaluate the measures taken for security in order to the infrastructure security. Considering the SSID, the strength and the usage of the WEP network, encryption, access control devices and segmentation.
Exploitation of vulnerabilities and the other network access, the consultants of the vallant can make use of it with the already identified vulnerabilities for attaining the access of the segments of other networks.
The success of the team is because they tested with various methods for the exploitation of access. This method will determine the segments of the systems and the network infrastructure which can be accessed, the security controls will divide the wireless network from the segments of other network and also the wireless network can be make use of a launching point for attacking some other systems.
The benefits of key business is as follows:
- The wireless network security is enhanced
- Finding and decreasing the vulnerabilities and security risks
- Preventing unintended or malicious activities
- Trying to avoid the situations which makes the organizations reputation and goodwill at stake
- The regulatory compliance is met.
VII CONCLUSION
A wireless network in a home network helps to connect multiple computers to form a local area network. It is used to access files and folders in all devices associated to a network from multiple computers to single printer.
The Mobile IP has its enduring IP address which is use to assign enduring IP address to allow devices in a home network. It directs security for all network devices from one location.
Devices can join and leave a network and participate whenever in a network such as laptop, gadgets enhance to interact with other devices easily. It is used to improve the quality of task, personal information sharing and increase security in a wireless home network connected to each other in an internet without cables like e-readers and tablets.
REFERENCES
1.Kahina Chelli, “Security Issues in Wireless Sensor Networks: Attacks and Countermeasures”, Proceedings of the World Congress on Engineering, London, U.K. (Vol. 1, pp. 1-3, 2015
- J. Loft, M. Hosseinzadeh, R. M. Alguliev, “Hierarchical routing in wireless sensor networks: a survey”, ICCET ‘2, pp. 650-654, 2015.
- R. Rajeswari, V. Seenivasagam, “Comparative Study on Various Authentication Protocols in Wireless Sensor Networks”, the Scientific World Journal, vol. 2016, pp. 16, 2016.
- M. U. Aftab, O. Ashraf, M. Irfan, M. Majid, A. Nisar and M. A. Habib, “A Review Study of Wireless Sensor Networks and Its Security”, Communications and Network, Vol. 7, No.4, pp.172-179, 2015
- Murat Dener, “Security Analysis in Wireless Sensor Networks”, Hindawi Publishing Corporation, International Journal of Distributed Sensor Networks, Vol.10, No.10, pp.303501, 2016
6.M. Revathi and Dr. B. Amutha, “A Survey on Security Protocols in Wireless Sensor Network”, International Journal of Pure and Applied Mathematics, 2017
7.Y. Bazband and K. Fahimi, “Performance Comparison Wireless Sensor Network Security Protocols: LLSP and Tiny SEC”, International Journal of Engineering Sciences and Research Technology, 2014
- A. S. Ahmed, “An Evaluation of Security Protocols on Wireless Sensor Network”, TKK –T Seminar of Internetworking, 2015
- L. E. Lighfoot, J. Ren and T. Li, “An Energy Efficient Link- Layer Security Protocol for Wireless Sensor Networks”, IEEE EIT 2007 proceedings, pp. 233-238, 2016
- J. Ren, T. Li and D. Aslam, “A Power Efficient Link-Layer Security Protocol LLSP for Wireless Sensor Networks”, Military Communications Conference, pp. 1002-1007, 2015
- C. Karloff, N. Sastry and D. Wagner, “Tiny Sec: A Link Layer Security Architecture for Wireless Sensor Networks”, Baltimore, Maryland, USA, pp. 162-175, 2014
- L. Tobarra, D. Cazorla, F. Cuartero, G. Diaz and E. Cambronero, “Model Checking Wireless Sensor Network Security Protocols: Tiny Sec + LEAP”, in wireless sensor and actor networks, Springer, Boston, MA, pp.95-106, 2013
- L. Krontiris, T. Dimitriou, H. Soroush and M. Salajegheh, “WSN Link-Layer Security Frameworks”, wireless sensor network security, Athens Information Technology, Greece, pp. 142, 2015
- A. Perris, R. Szewczyk, J. D. Tygar, V.Wen and D. E. Culler, “SPINS: Security Protocols for Sensor Networks”, Kluwer Academic Publishers. Manufactured in Netherlands, Vol.8 No.5 pp.521-534, 2014
- K. M Pattani and P. J Chauhan, “SPIN Protocol for Wireless Sensor Network”, International Journal of Advance Research in Engineering, Science and Technology, 2015
- S. Zhu, S. Setia and S. Jajodia, “LEAP: Efficient Security Mechanisms for Large Scale Distributed Sensor Networks”, Proceedings of the 10th ACM conference on Computer and communications security, Washington D.C., USA, Vol. 2, No.4, pp.500-528, 2014
- D. Alsoufi, K. Elleithy, T. Abuzaghleh and A. Nasser, “Security in Wireless Sensor Networks-Improving the LEAP Protocol”, International Journal of Computer Science and Engineering Survey, 2015
- A. A. Andhale and Prof. B. N. Jagdale, “Light Weight Security Protocol for Wireless Sensor Networks (WSN)”, International Journal of Engineering Research and Technology, 2014
- K. Ren, W. Lou and Y. Zhang, “LEDS: Providing Location- Aware End-to-End Data Security in Wireless Sensor Networks”, IEEE Transactions on Mobile Computing, Vol. 7, No.5, pp.585-598. 2015.


